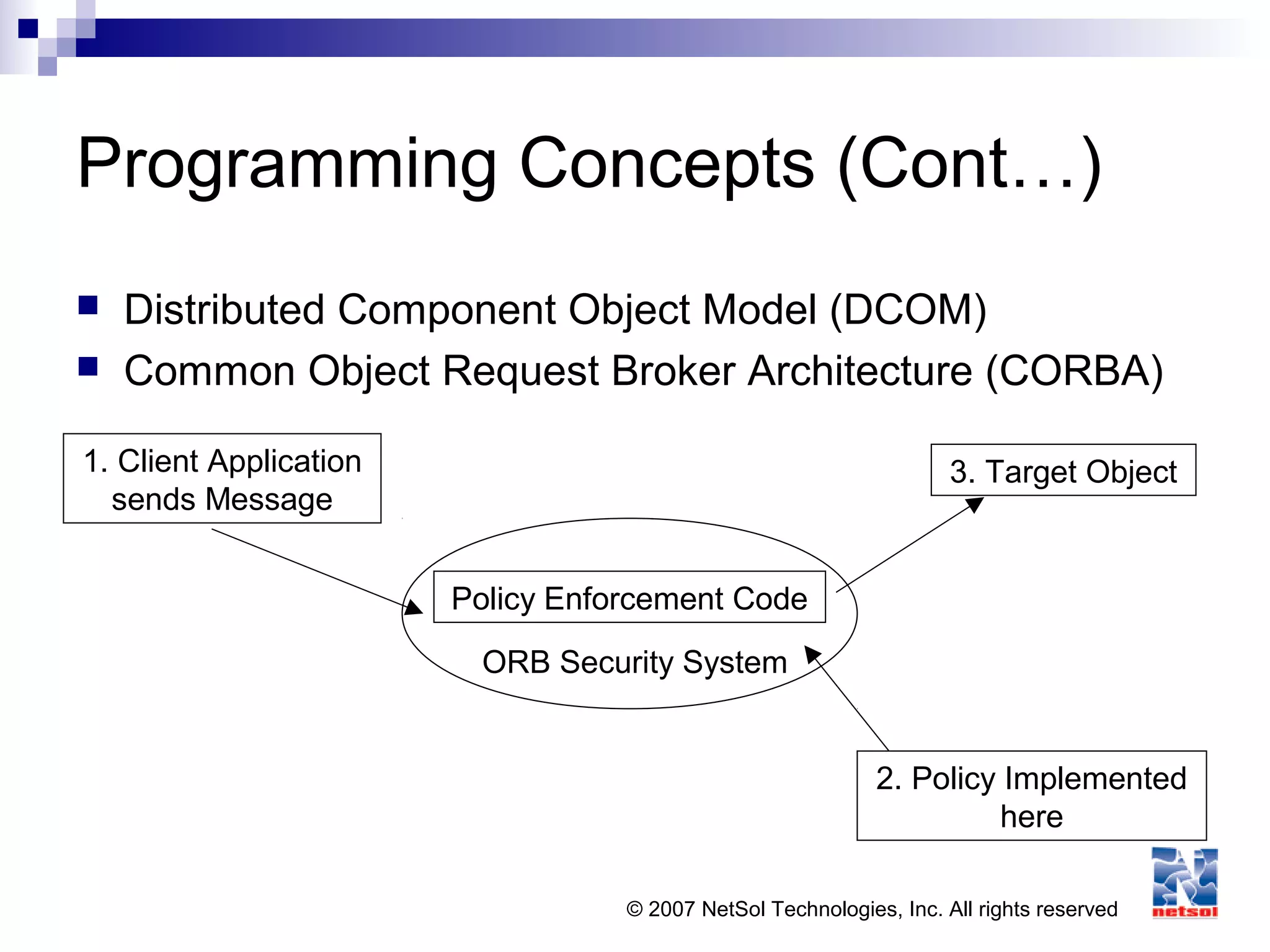
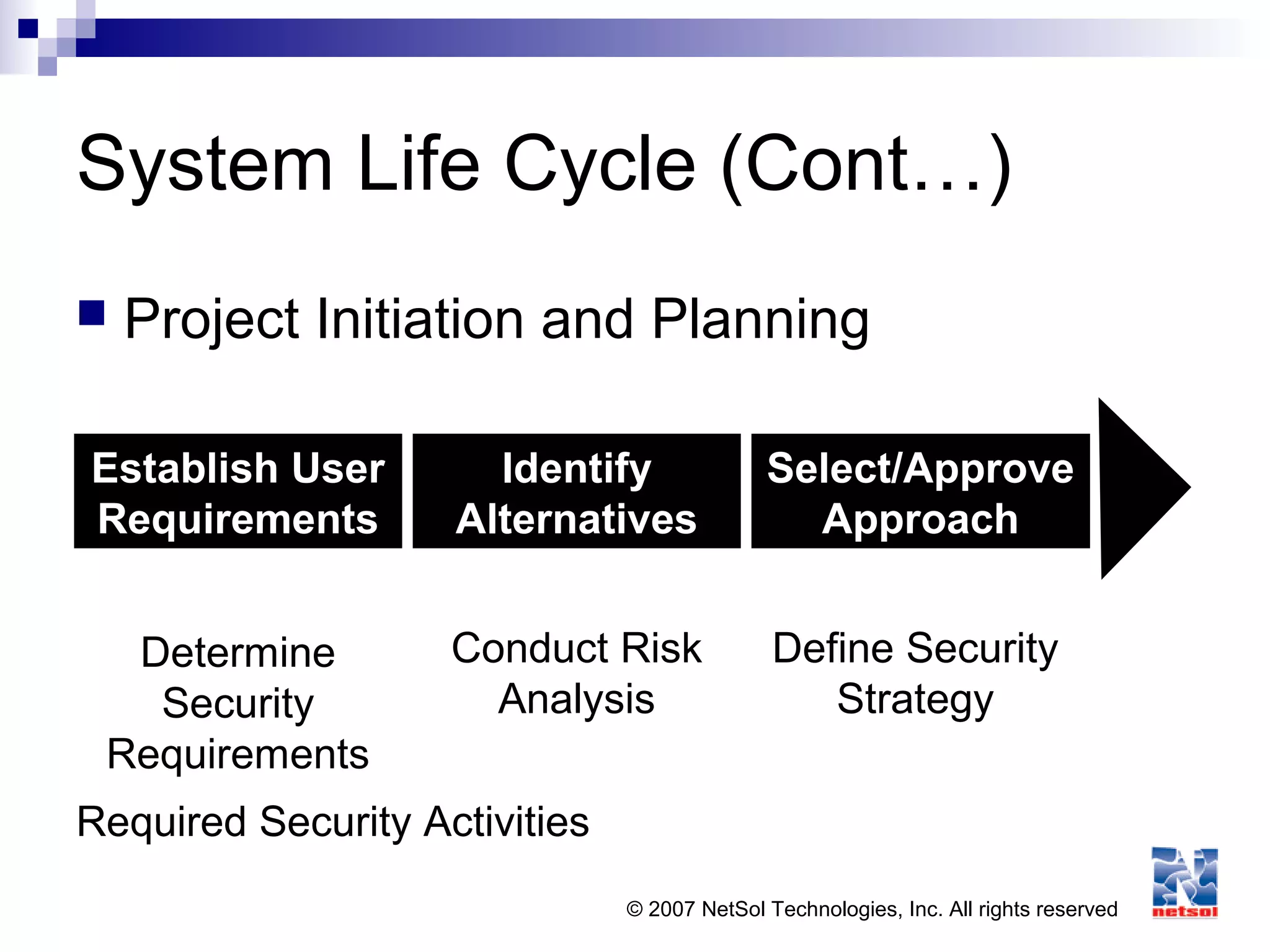
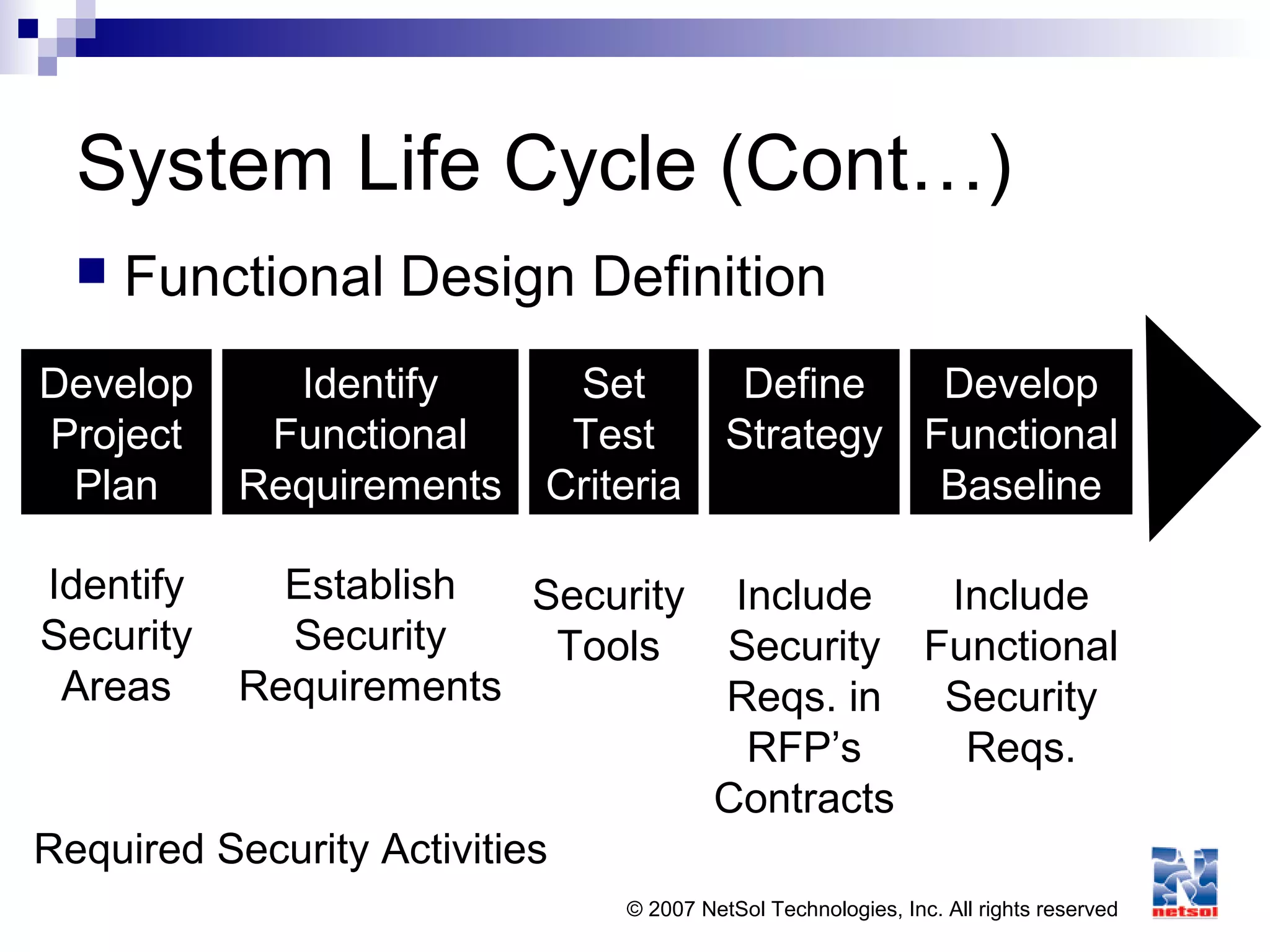
This document provides an overview of application security concepts. It discusses programming concepts, threats and malware, software protection mechanisms, audit and assurance mechanisms for databases and data warehouses, and application security in web environments. Specific topics covered include programming languages, the software development lifecycle, vulnerabilities like buffer overflows, and mitigation techniques like cryptography, access controls, and testing.