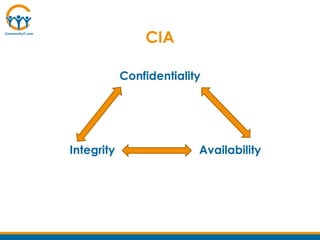
The webinar on IT security best practices, presented by Steve Longenecker and Mark Kraemer, emphasizes the importance of organizational strategies, risk assessment, and user responsibilities in maintaining network security. Various topics such as security culture, policies, and technology solutions like firewalls and antivirus software were discussed, targeting nonprofits' unique challenges. Participants were encouraged to engage actively and share feedback, with an upcoming follow-up webinar scheduled for August 29 on Office 365 for nonprofits.