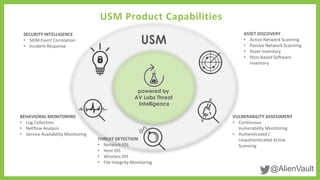
The document outlines a process for executing a watering hole attack, which involves targeting specific websites to exploit vulnerabilities and inject threats. It discusses AlienVault's unified security management (USM) platform that integrates various security capabilities, including threat detection and intelligence. Additionally, it highlights the regular updates provided by AlienVault Labs for actionable security guidance and a call to action for users to try their services.