The document discusses the NIST Cybersecurity Framework. It defines key terms like information security, CIA triad, and cybersecurity. It explains that the NIST CSF provides guidance on cybersecurity risk management principles and best practices. It outlines the Framework Core, Implementation Tiers, and Profiles to help organizations manage cybersecurity risks in a cost-effective manner. The CSF can be used by organizations of any size or sector to understand and apply cybersecurity risk management.
![Cybersecurity Framework
Manajemen Risiko Keamanan Informasi [EL5216 17/18]
Muhammad Akbar Yasin [23216322]](https://image.slidesharecdn.com/cybersecurityframework-180326200630/75/Cybersecurity-Framework-Introduction-1-2048.jpg)
![Terms
• Information Security
• Information security is about the protection of information, regardless of
whether it is stored digitally or not
• CIA Triad
• Cybersecurity
• Is it about securing “cyber”?
• Cyber security is about securing things that are vulnerable through ICT
[1] https://ccis.no/cyber-security-versus-information-security/](https://image.slidesharecdn.com/cybersecurityframework-180326200630/75/Cybersecurity-Framework-Introduction-2-2048.jpg)
![Terms (continued)
• ISACA Glossary
• Information
• An asset that, like other important business assets, is essential to an enterprise’s
business. It can exist in many forms. It can be printed or written on paper, stored
electronically, transmitted by post or by using electronic means, shown on films, or
spoken in conversation.
• Information security
• Ensures that within the enterprise, information is protected against disclosure to
unauthorized users (confidentiality), improper modification (integrity), and non-access
when required (availability).
• Cybersecurity
• The protection of information assets by addressing threats to information processed,
stored, and transported by internetworked information systems
[3] https://www.isaca.org/Pages/Glossary.aspx](https://image.slidesharecdn.com/cybersecurityframework-180326200630/75/Cybersecurity-Framework-Introduction-3-2048.jpg)
![Infosec vs Cybersecurity
[2] http://www.cisoplatform.com/profiles/blogs/understanding-difference-between-cyber-security-information](https://image.slidesharecdn.com/cybersecurityframework-180326200630/75/Cybersecurity-Framework-Introduction-4-2048.jpg)
![NIST Cybersecurity Framework
• Why NIST CSF?
• Provides guidance on risk management principles and best practices,
• Provides common language to address and manage cybersecurity risk
• Outlines a structure for organizations to understand and apply cybersecurity
risk management
• Identifies effective standards, guidelines, and practices to manage
cybersecurity risk in a cost-effective manner based on business needs.
• Who Should Used the Framework?
• for organizations of all sizes, sectors, and maturities. While the Framework
was designed with Critical Infrastructure (CI) in mind, it is extremely versatile
and can be used by organizations regardless of sector or size.
[4] https://www.us-cert.gov/sites/default/files/c3vp/framework_guidance/HPH_Framework_Implementation_Guidance.pdf, page 11](https://image.slidesharecdn.com/cybersecurityframework-180326200630/75/Cybersecurity-Framework-Introduction-5-2048.jpg)
![NIST Cybersecurity Framework
[5] Implementing The Nist Cybersecurity Framework Using Cobit 5: a step-by-step guide for your enterprise](https://image.slidesharecdn.com/cybersecurityframework-180326200630/75/Cybersecurity-Framework-Introduction-6-2048.jpg)
![[6] https://www.orbussoftware.com/governance-risk-and-compliance/nist/benefits/](https://image.slidesharecdn.com/cybersecurityframework-180326200630/75/Cybersecurity-Framework-Introduction-7-2048.jpg)
![Framework Core
Subcategories are the deepest level of
abstraction in the Core. There are 98
Subcategories, which are outcome-
driven statements that provide
considerations for creating or improving
a cybersecurity program.
[7] https://www.nist.gov/cyberframework/online-learning/components-framework](https://image.slidesharecdn.com/cybersecurityframework-180326200630/75/Cybersecurity-Framework-Introduction-8-2048.jpg)
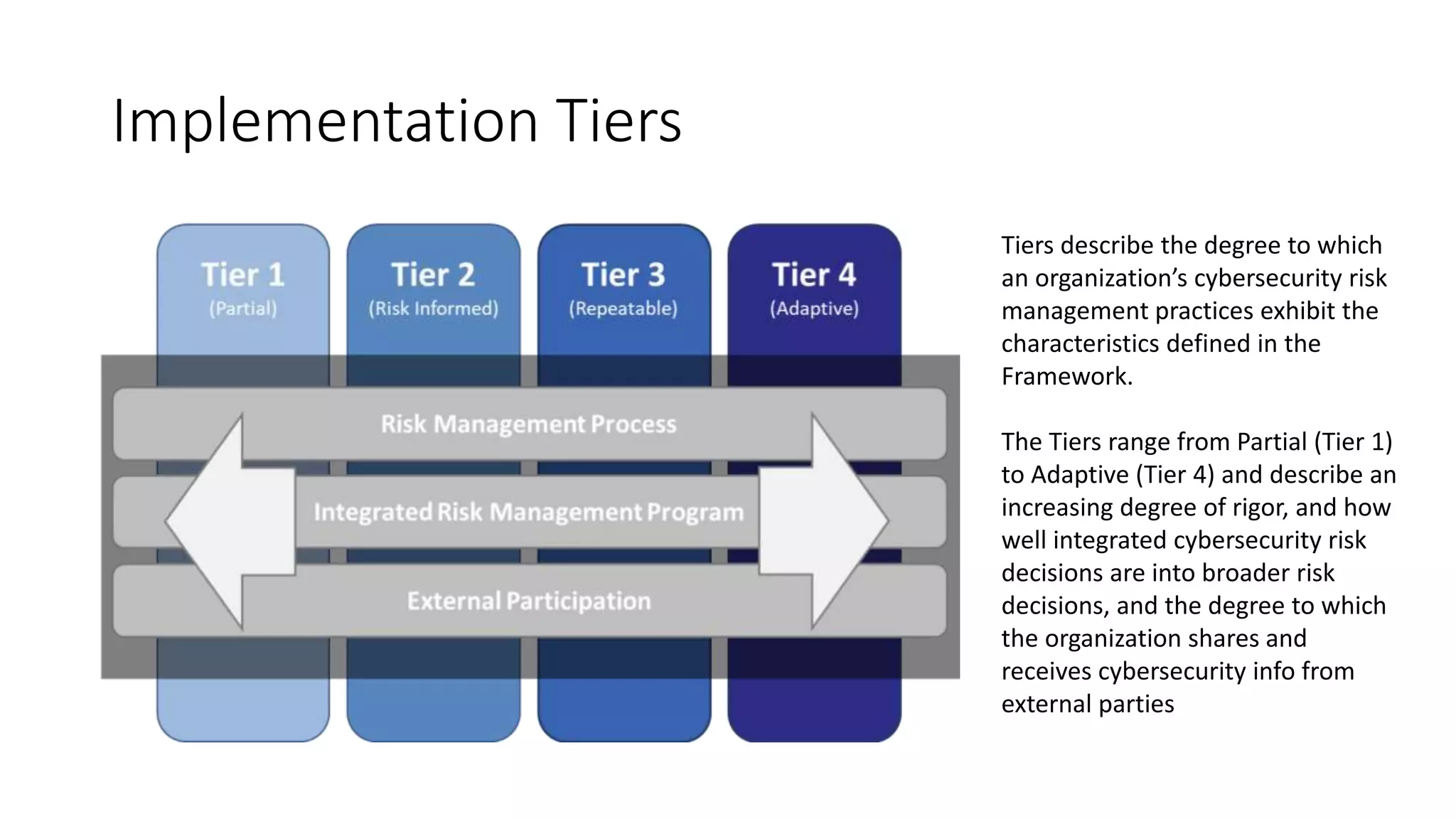
![Implementation Tiers
[8] https://supplier.intel.com/static/governance/documents/The-cybersecurity-framework-in-action-an-intel-use-case-brief.pdf](https://image.slidesharecdn.com/cybersecurityframework-180326200630/75/Cybersecurity-Framework-Introduction-10-2048.jpg)
![Reference
• [1] https://ccis.no/cyber-security-versus-information-security/
• [2] http://www.cisoplatform.com/profiles/blogs/understanding-difference-between-
cyber-security-information
• [3] https://www.isaca.org/Pages/Glossary.aspx
• [4] https://www.us-
cert.gov/sites/default/files/c3vp/framework_guidance/HPH_Framework_Implementatio
n_Guidance.pdf, page 11
• [5] Implementing The Nist Cybersecurity Framework Using Cobit 5: a step-by-step guide
for your enterprise, page 5
• [6] https://www.orbussoftware.com/governance-risk-and-compliance/nist/benefits/
• [7] https://www.nist.gov/cyberframework/online-learning/components-framework
• [8] https://supplier.intel.com/static/governance/documents/The-cybersecurity-
framework-in-action-an-intel-use-case-brief.pdf](https://image.slidesharecdn.com/cybersecurityframework-180326200630/75/Cybersecurity-Framework-Introduction-12-2048.jpg)