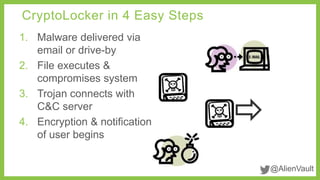
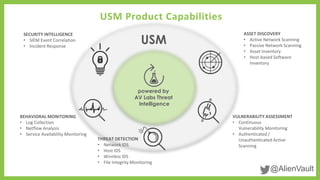
The document outlines how AlienVault's Unified Security Management (USM) platform helps mid-sized businesses detect and respond to ransomware threats, particularly Cryptolocker infections. It emphasizes the need for improved detection and response capabilities, given the increase in high-profile breaches and the evolving threat landscape. The USM integrates various security tools and provides threat intelligence to enhance an organization's security posture.