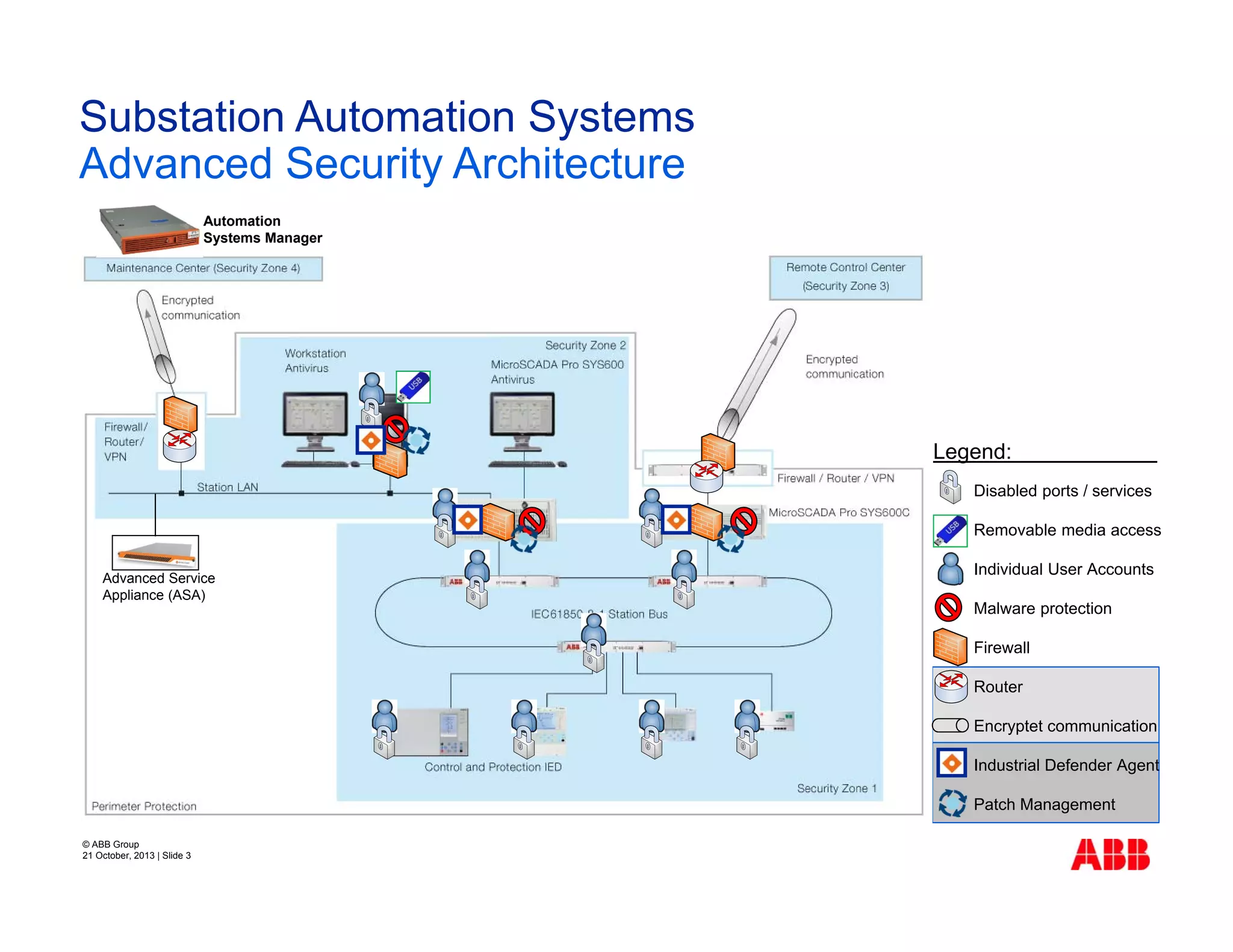
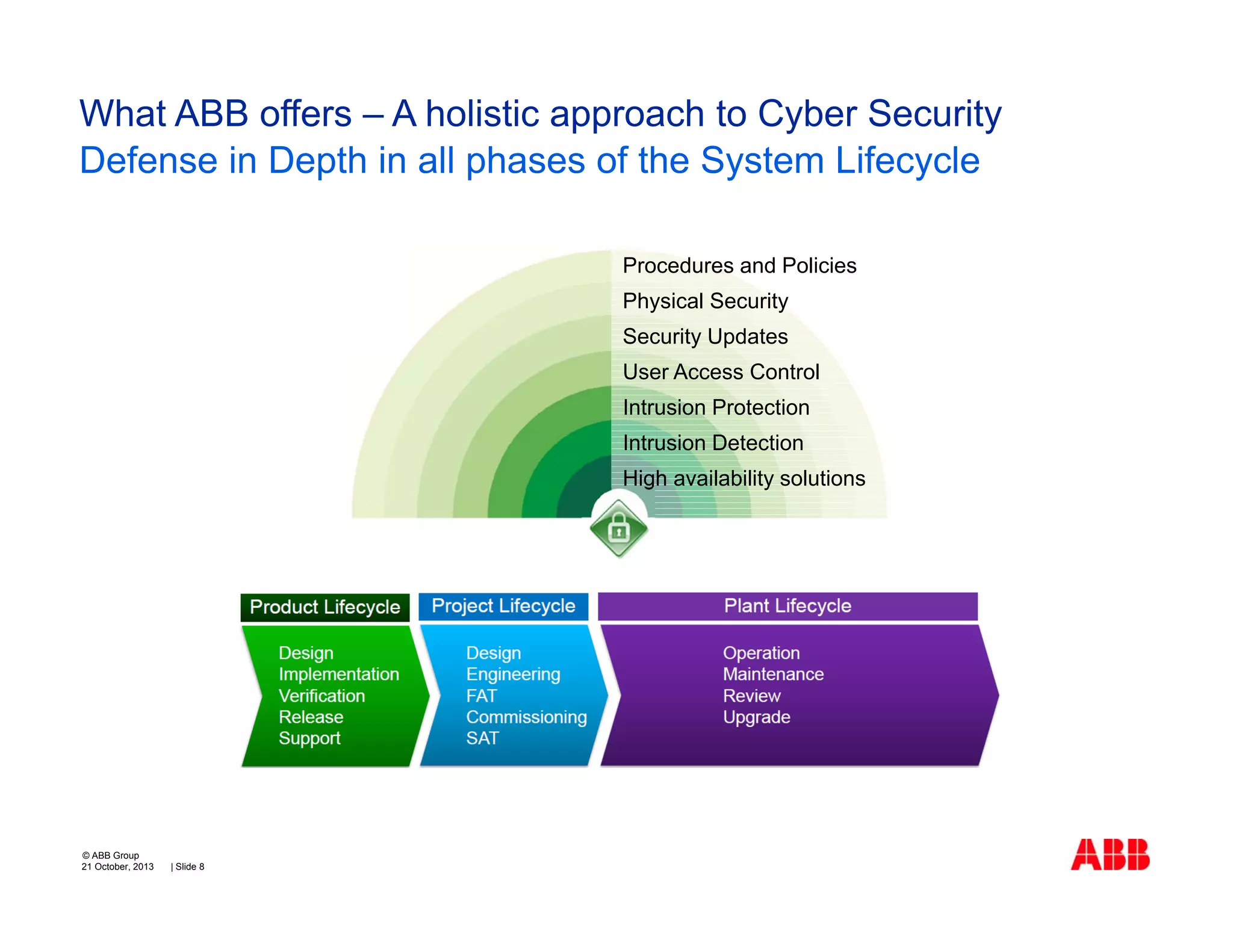
The document discusses cyber security challenges facing industrial control systems and how to address them. It identifies the main challenges as organizational issues like risk management and awareness, technical issues involving installed infrastructure and vulnerabilities, and disruptive changes. The challenges can be addressed through better preparation like inventorying systems, understanding normal behavior to detect anomalies, monitoring for vulnerabilities, and keeping systems patched. The presentation concludes that effective cyber security requires a joint effort across various stakeholders and a holistic, defense-in-depth approach covering the entire system lifecycle.