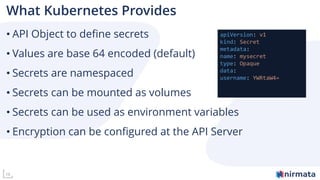
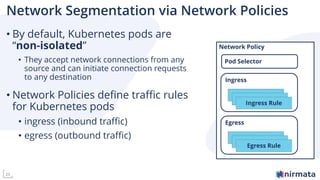
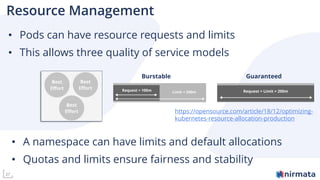
The document outlines best practices for securing Kubernetes workloads, covering key components such as secret management, access controls, and network policies. It emphasizes the importance of using policy engines like Kyverno for managing configurations and suggests utilizing management planes like Nirmata for effective Kubernetes configuration. Overall, it highlights the necessity of implementing robust security measures across different cluster components for optimal protection of workloads.