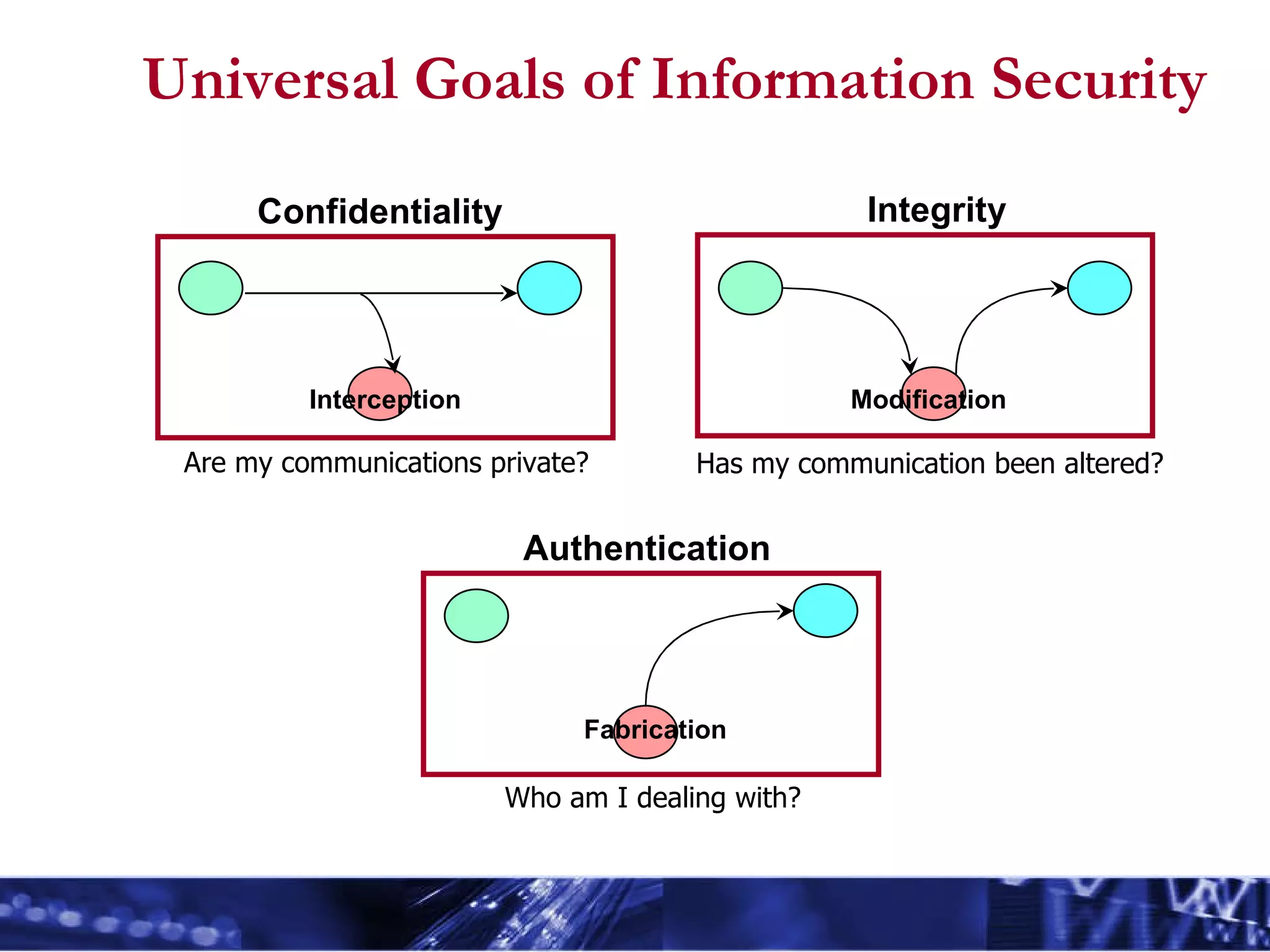
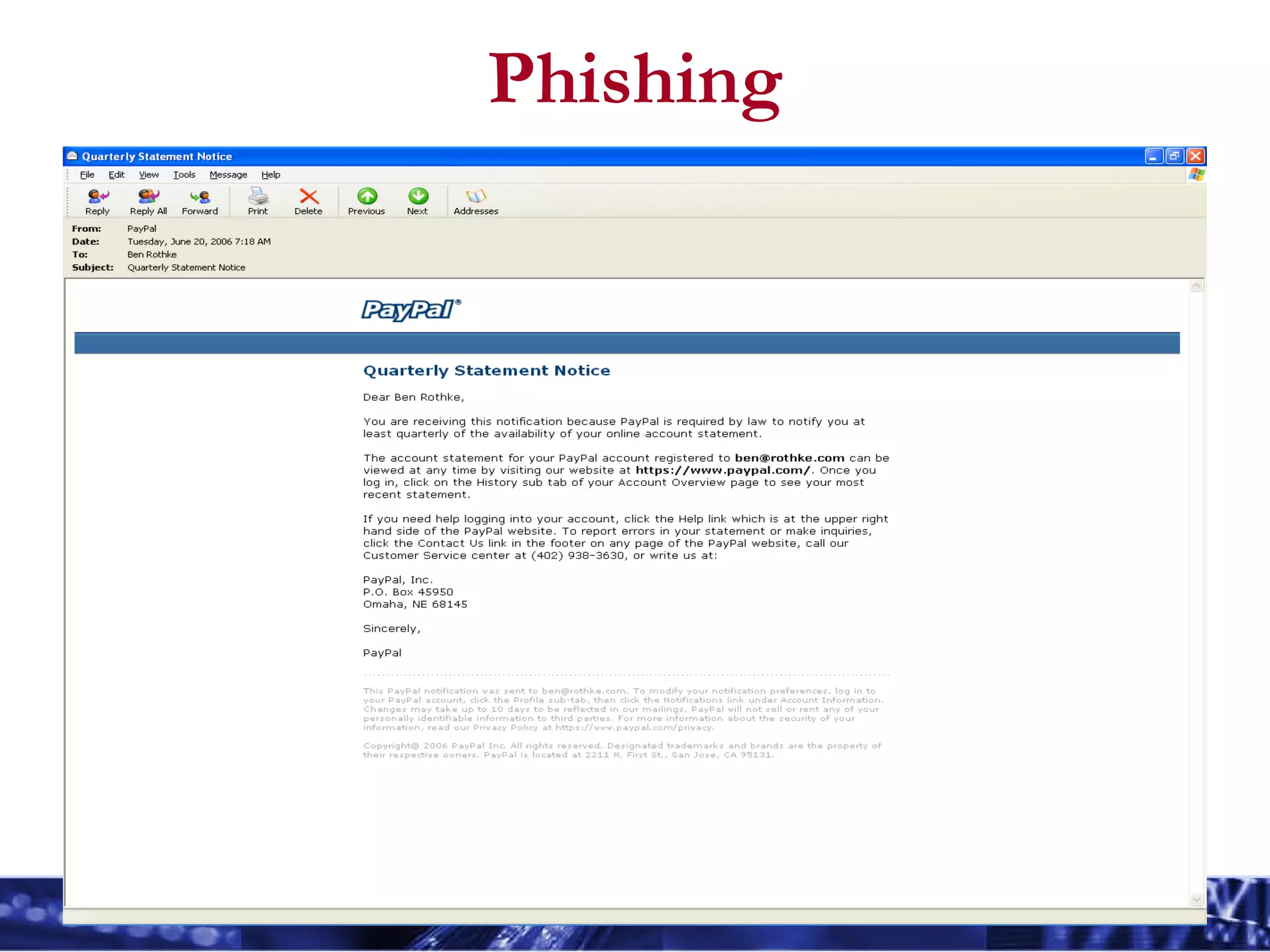
The document outlines essential information security principles and practices for employees, emphasizing the importance of awareness and responsibility in protecting digital assets. It covers various security threats such as hackers, phishing, and social engineering, while encouraging employees to adopt safe practices like using strong passwords and reporting suspicious activities. The document also highlights the need for tailored security awareness programs across different organizational departments to effectively mitigate risks.