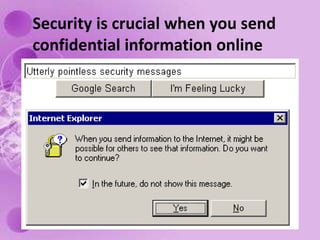
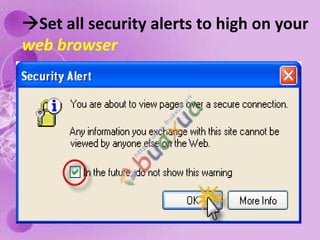
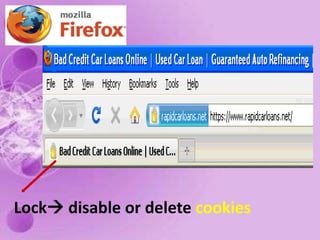
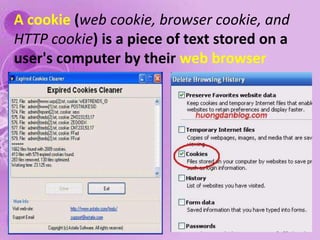
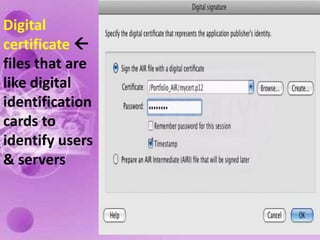
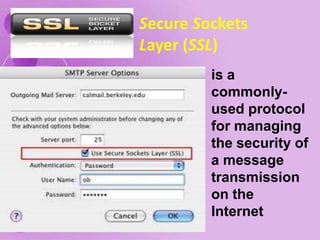
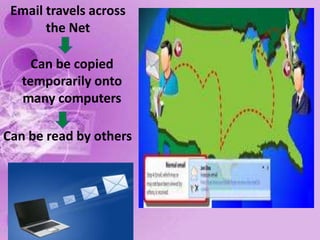
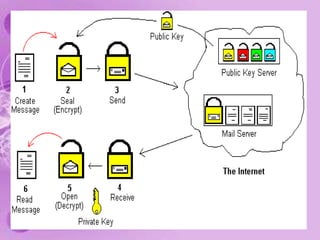
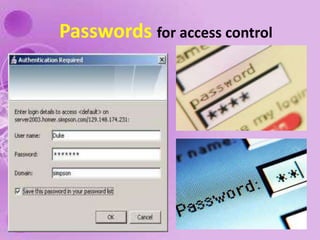
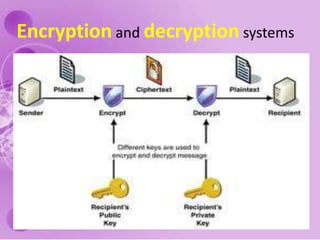
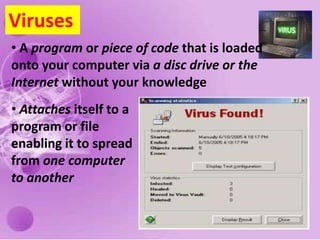
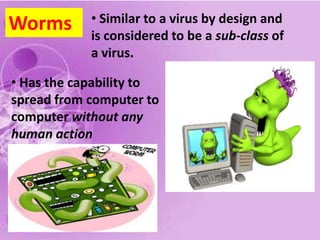
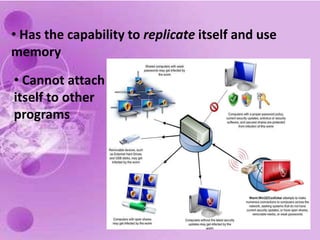
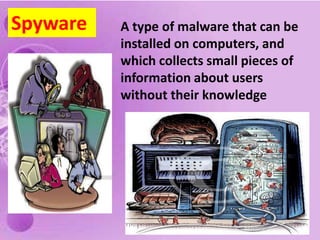
1) The document discusses internet and computer security, including securing web browsers, encrypting emails, using firewalls and passwords, and protecting against malware like viruses, worms, Trojan horses, spyware, and adware.
2) It also covers types of computer crimes such as hacking, phishing, computer viruses, cyberstalking, and identity theft.
3) Some recommended anti-virus software includes BkavPro Internet Security and Kaspersky Internet Security 2011 which provide protection from threats, attacks, and unwanted information.