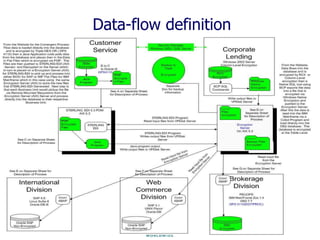
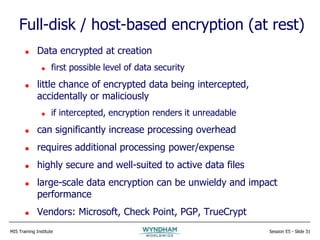
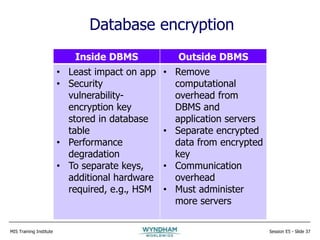
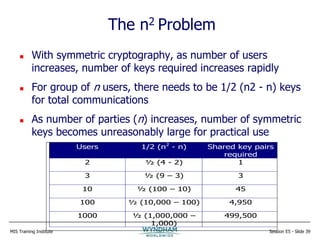
The document discusses strategies for effective encryption deployment. It begins with an overview of encryption and emphasizes that while the mathematics are complex, effective encryption primarily requires attention to detail, good design, and project management skills. The rest of the presentation focuses on developing an encryption strategy, including defining requirements, classifying data, documenting policies and processes, assessing legacy systems, choosing appropriate encryption methods, and properly managing encryption keys. Effective encryption is portrayed as a comprehensive program rather than an isolated technical solution.