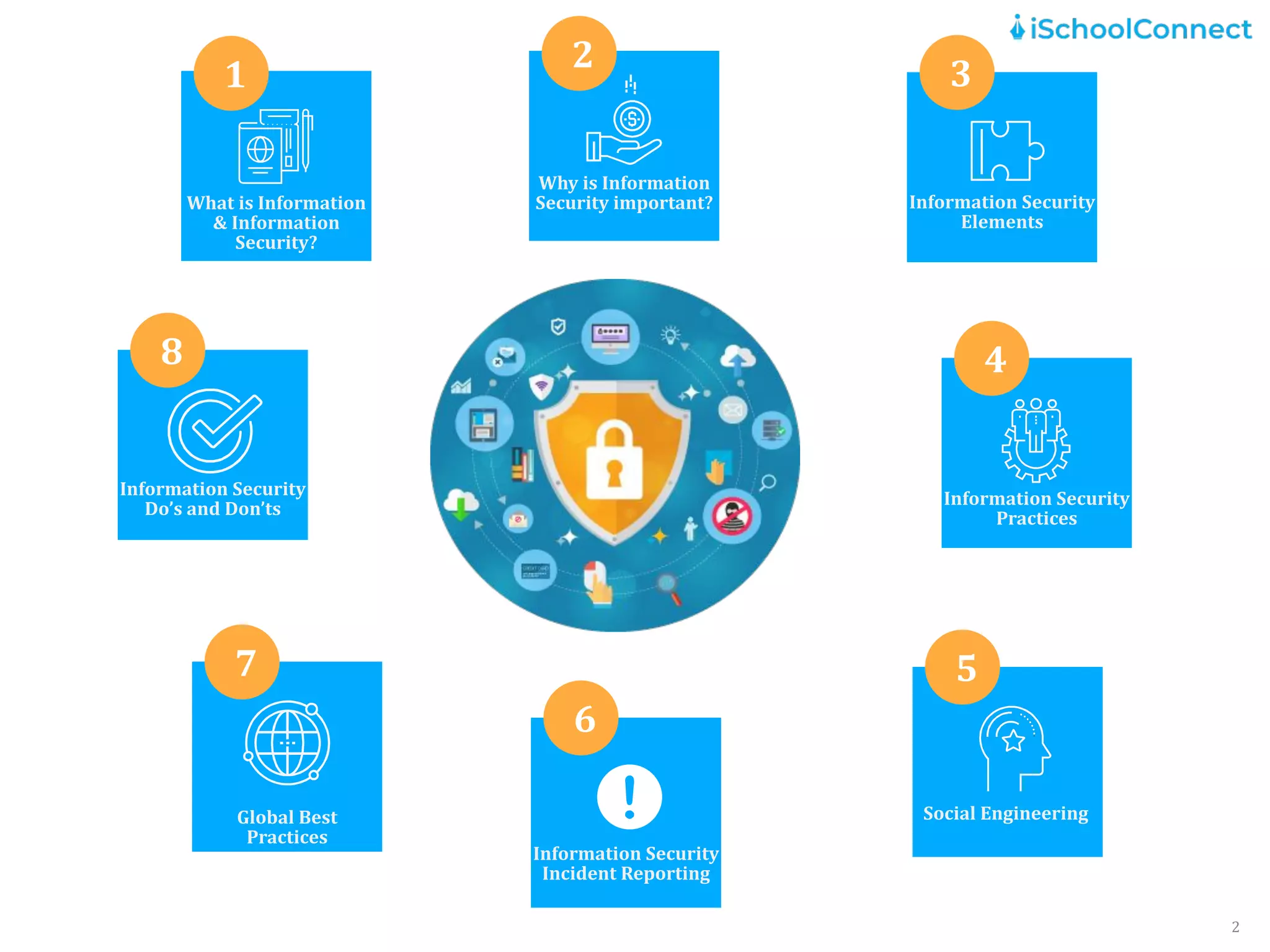
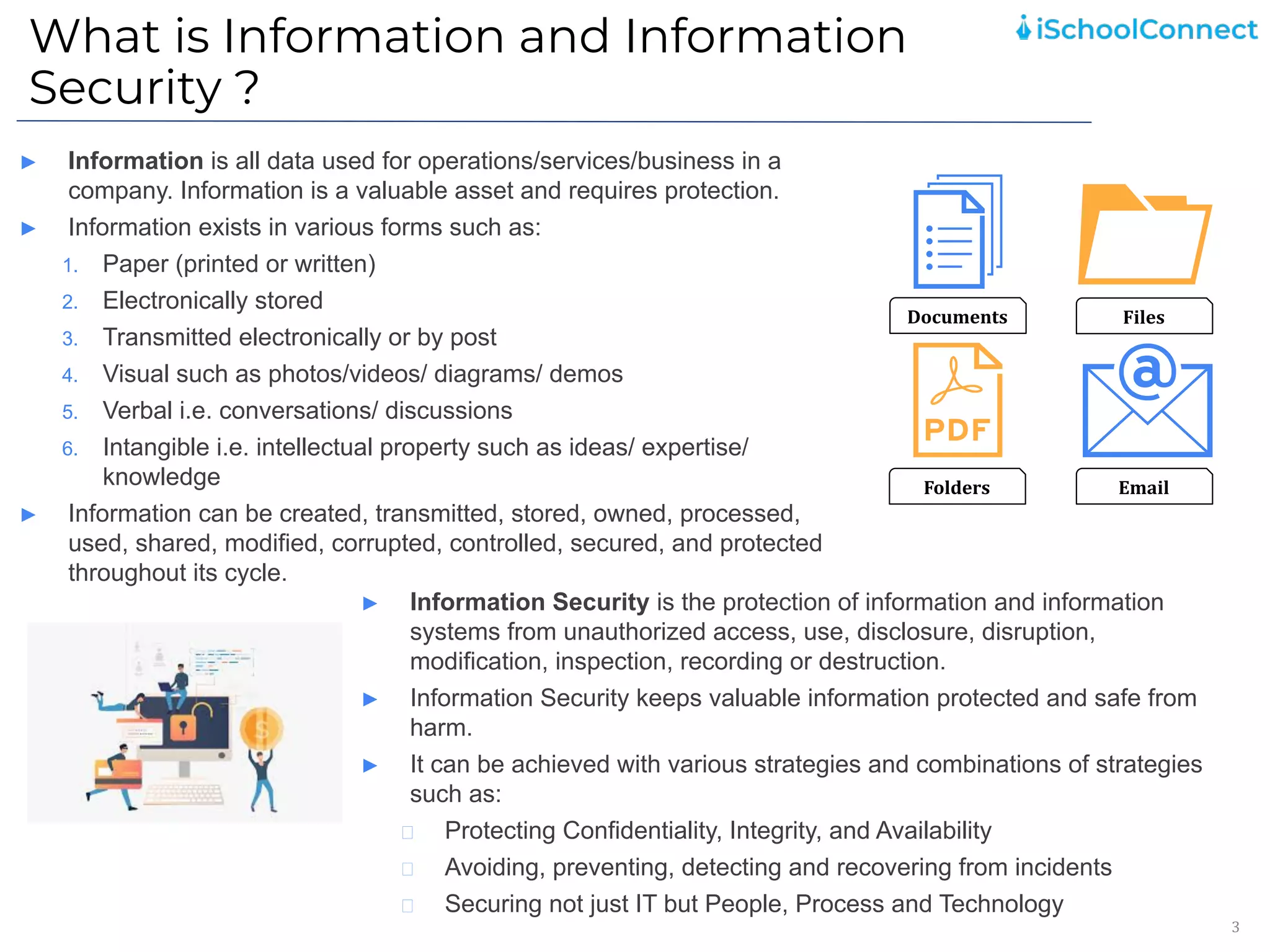
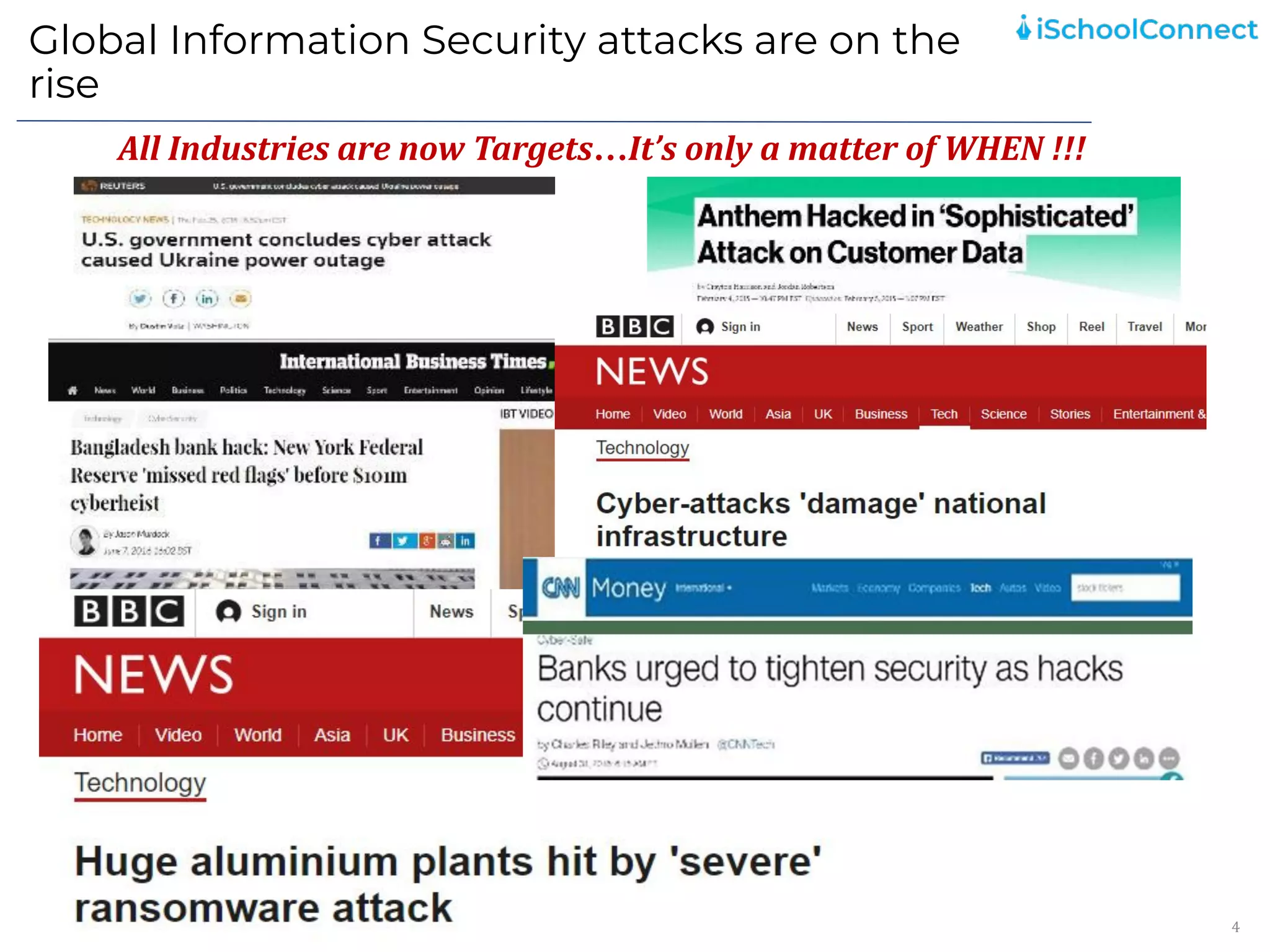
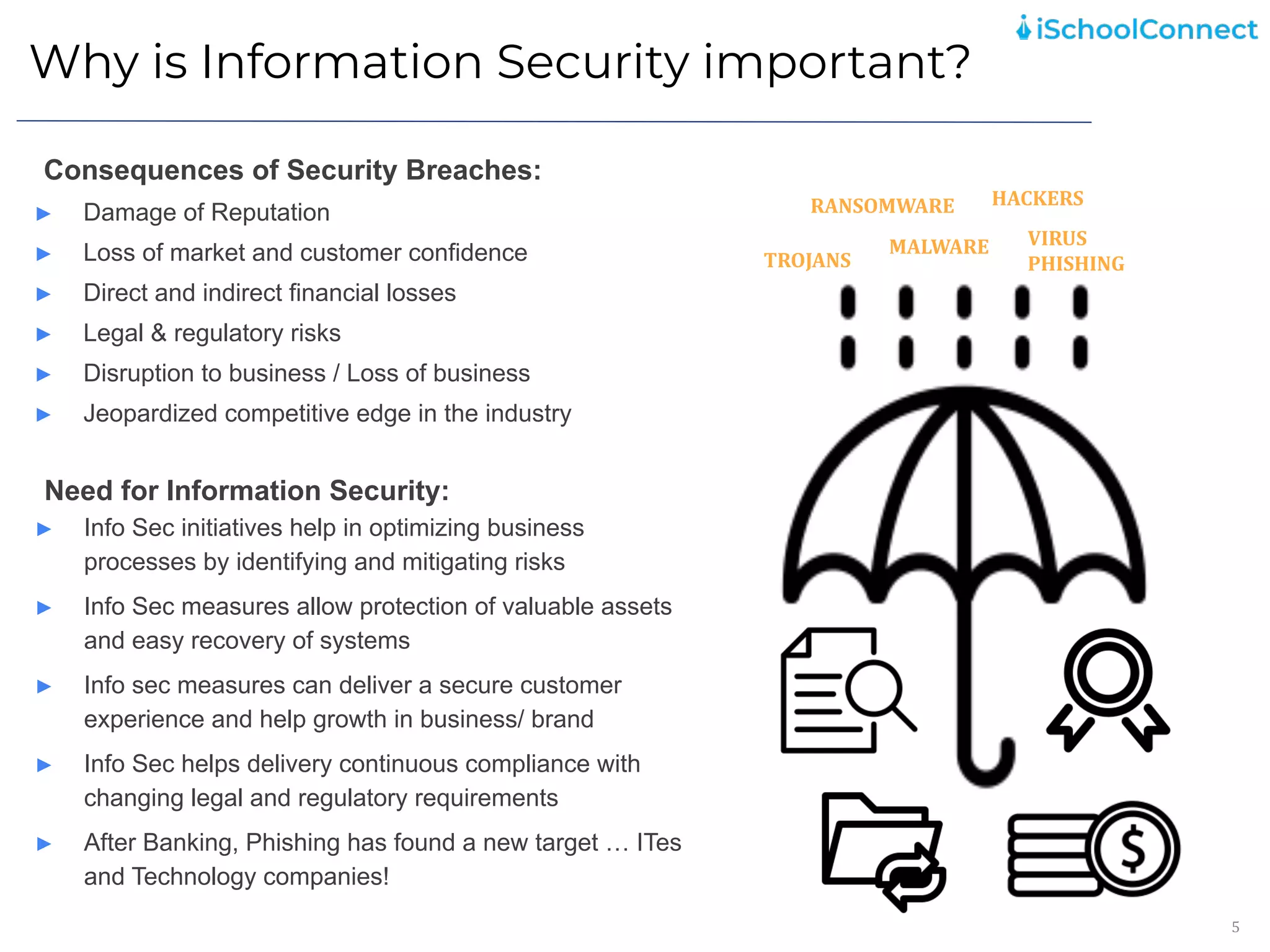
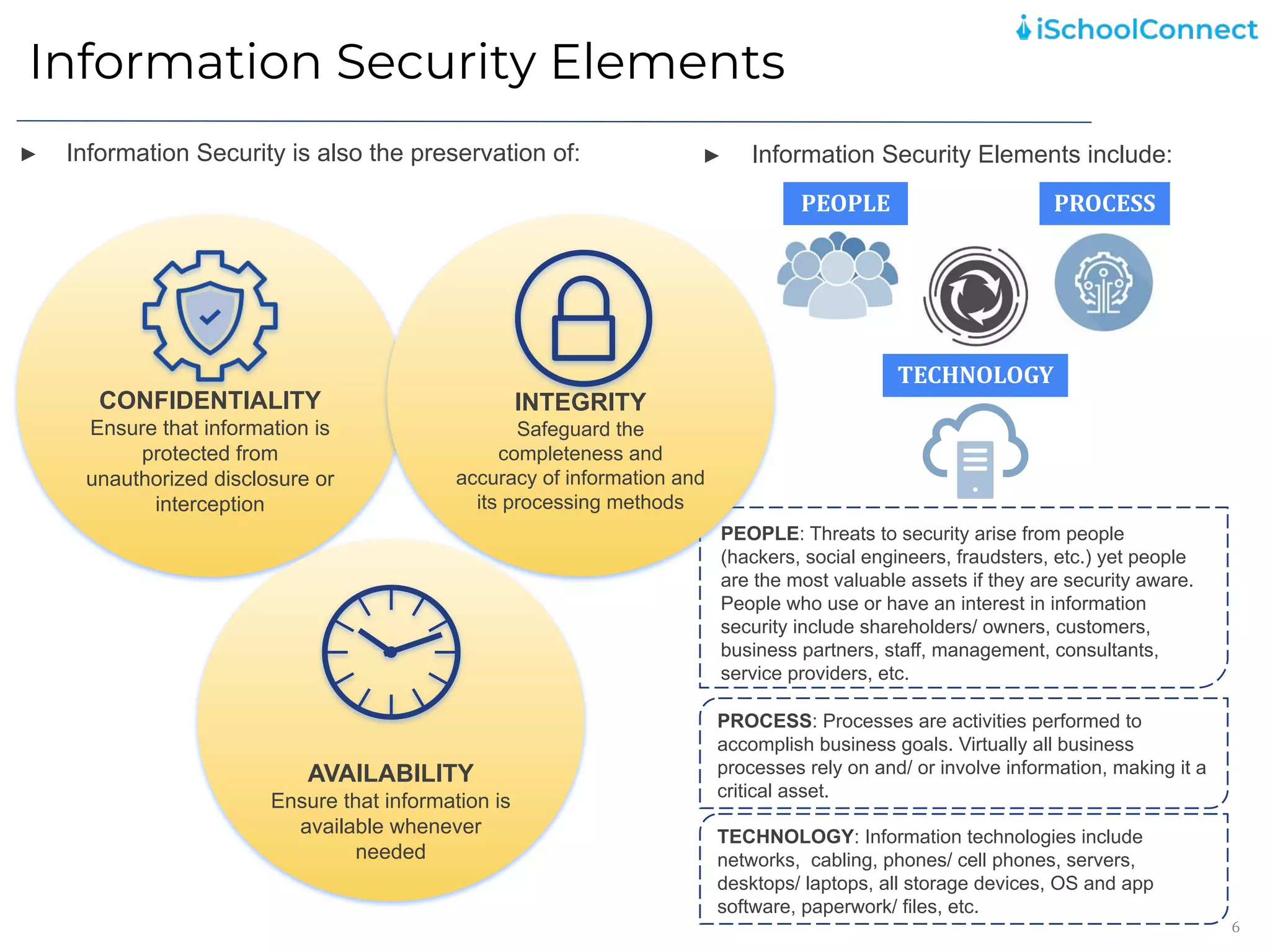
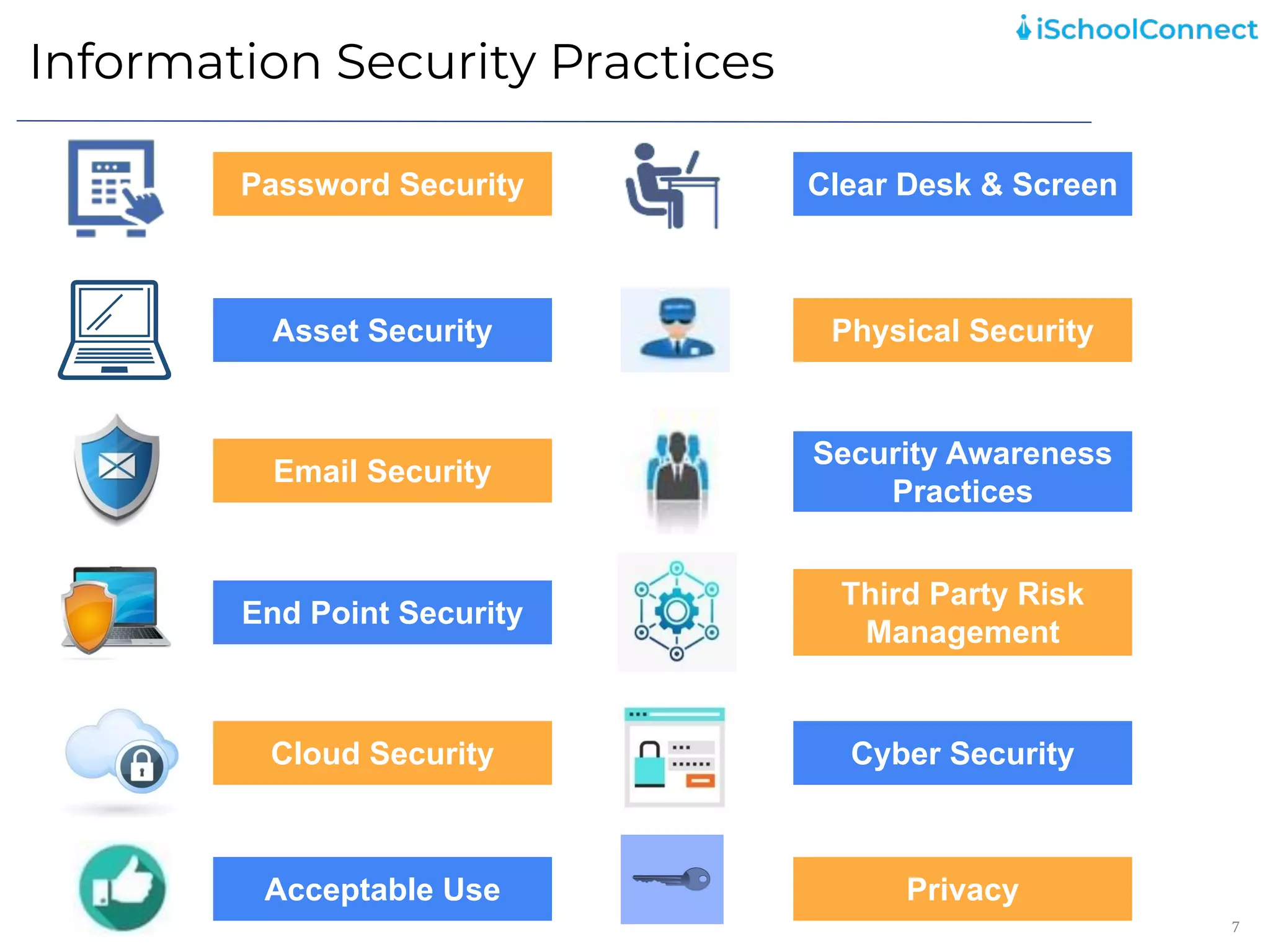
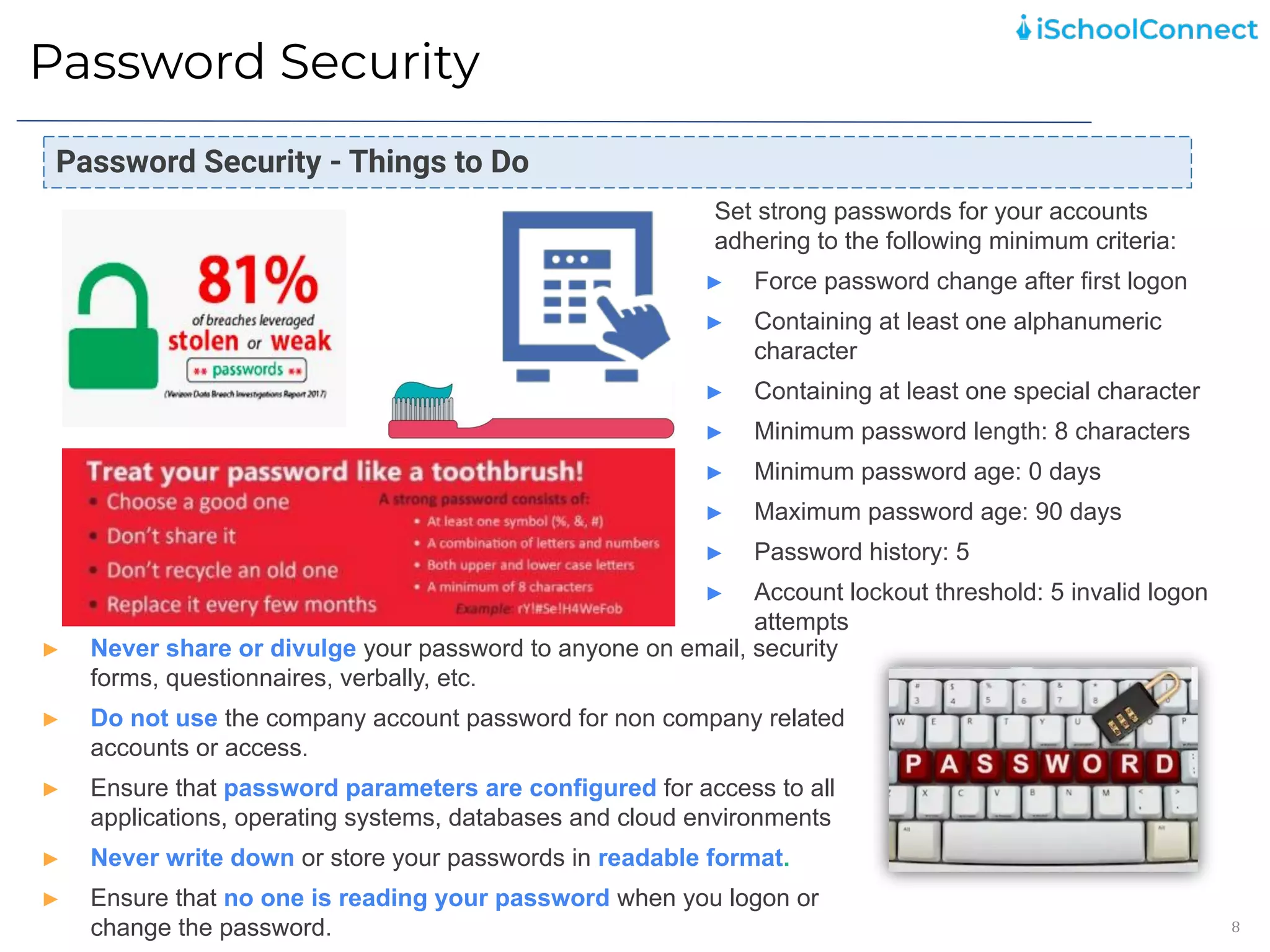
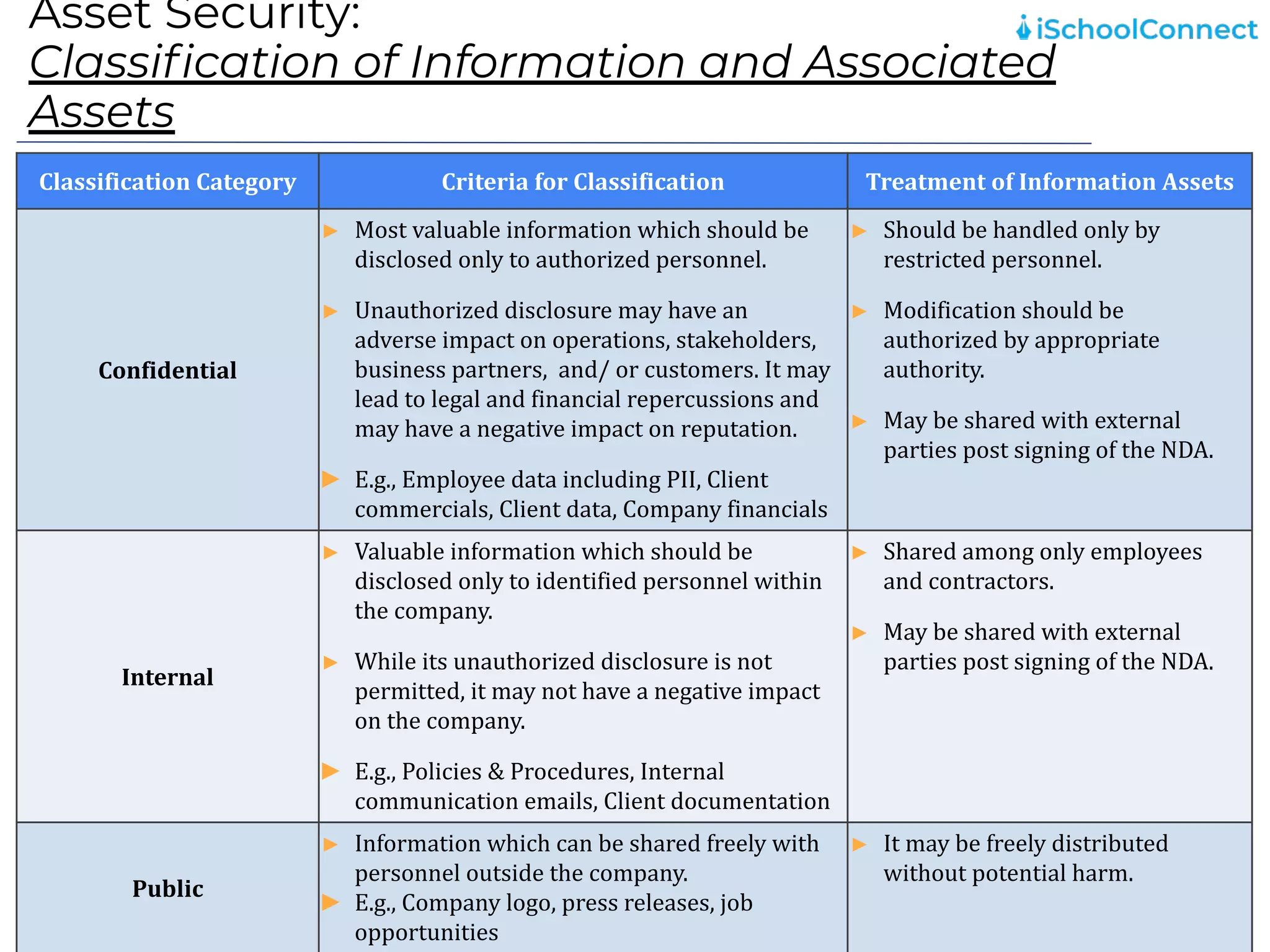
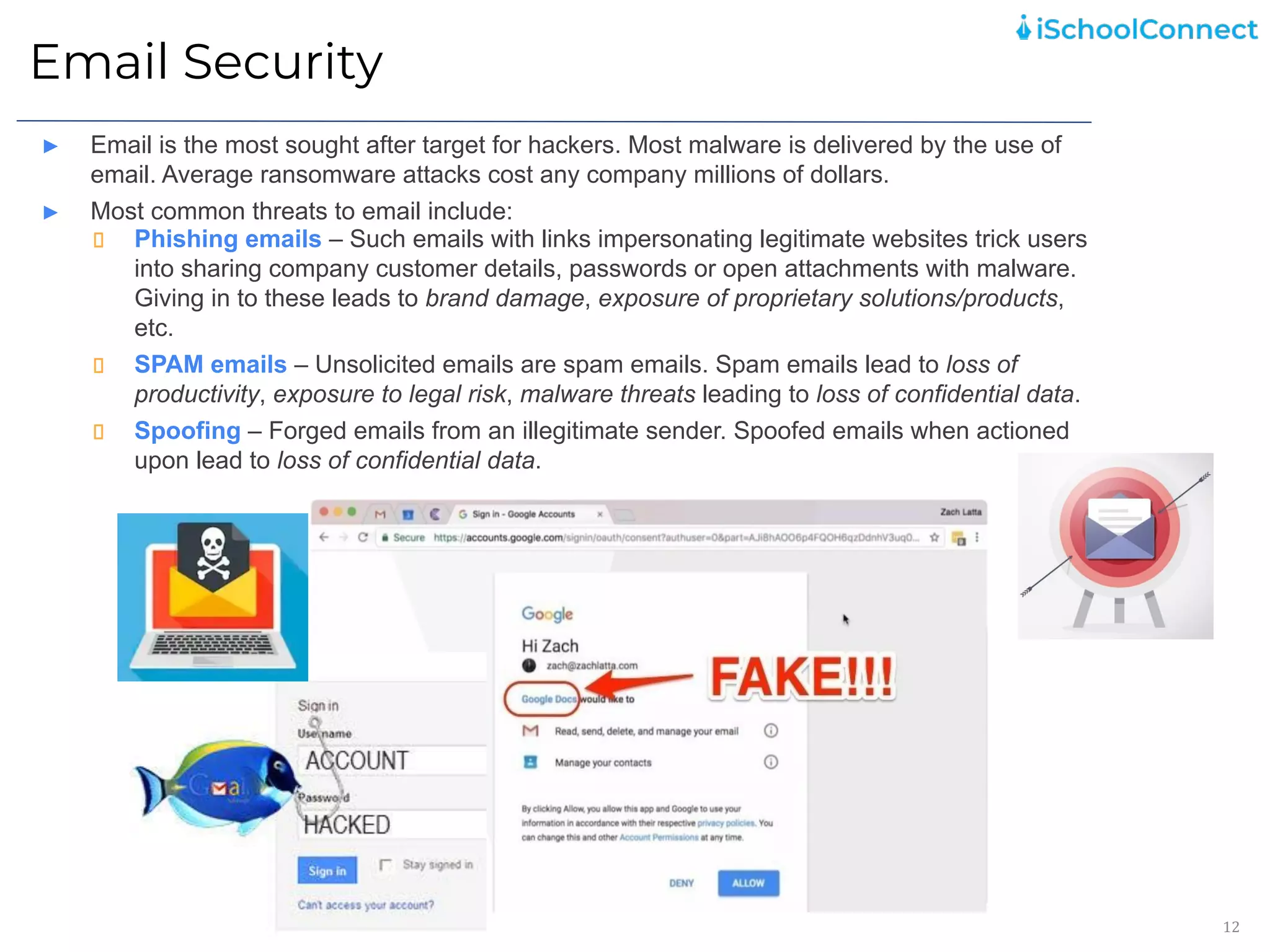
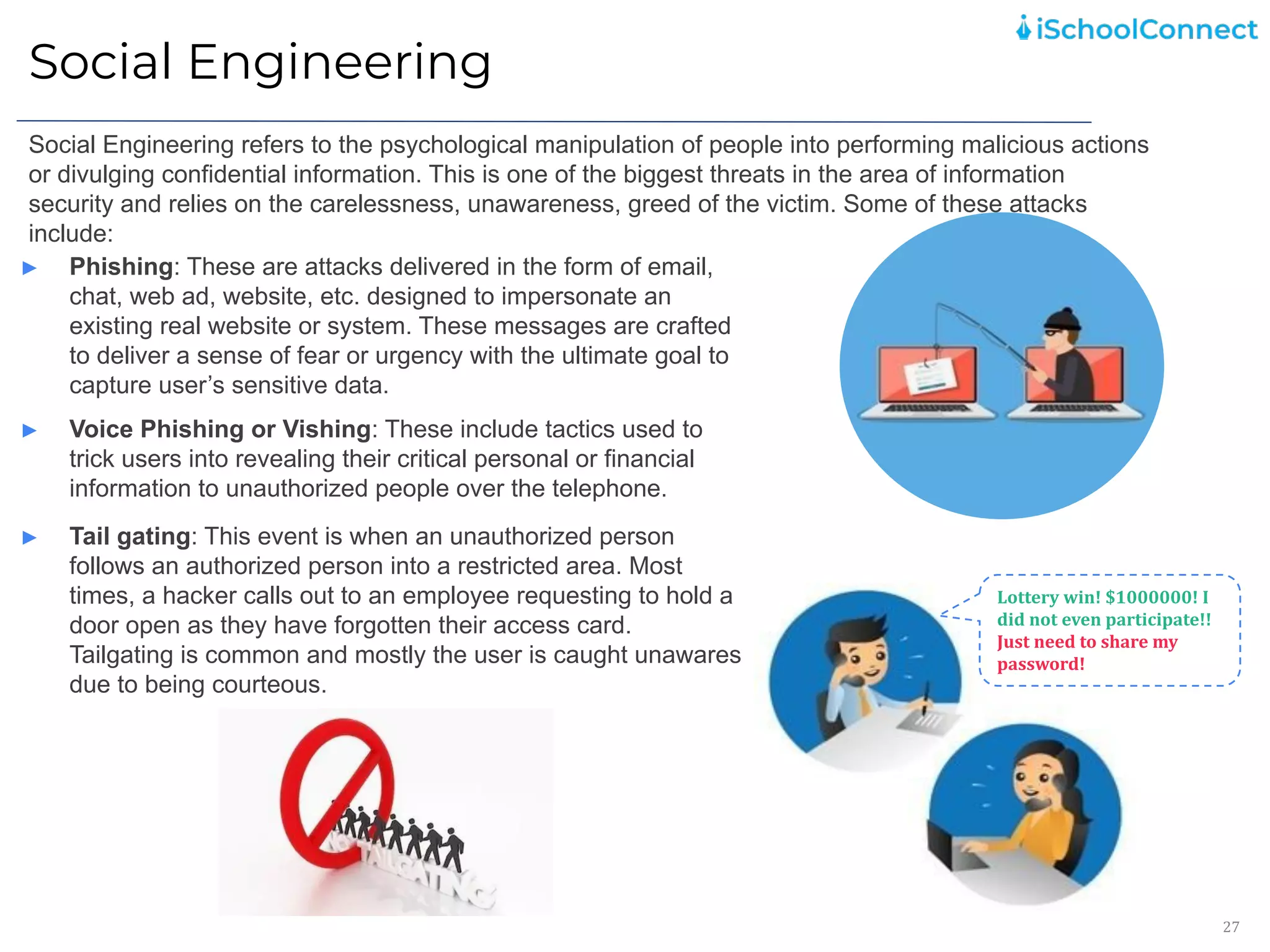
The document outlines an information security user awareness training agenda released in November 2021, focusing on the importance of information security and best practices to protect data within an organization. Key topics include understanding information and security, identifying social engineering threats, incident reporting, and implementing global best practices. It emphasizes the need for robust security measures, asset classification, email security, and employee responsibilities to mitigate risks associated with cybersecurity threats.