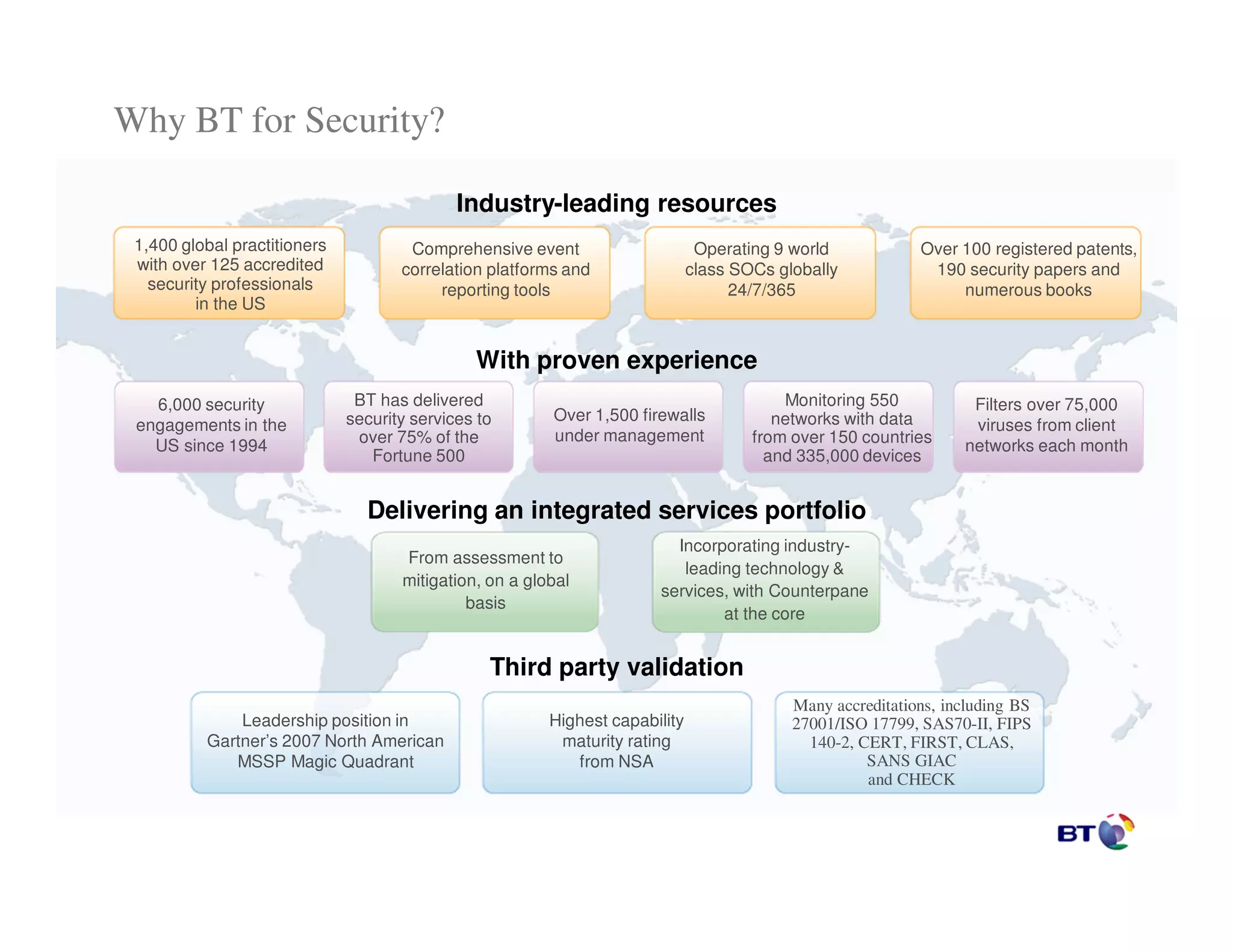
1. BT provides industry-leading cybersecurity resources including over 1,400 practitioners globally, 9 security operations centers, and over 100 patents.
2. They have experience securing over 75% of Fortune 500 companies through 6,000 security engagements since 1994 and monitoring over 550 networks.
3. BT delivers an integrated security portfolio from assessment to mitigation globally, incorporating industry-leading technology and services from Counterpane.