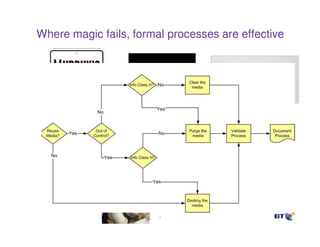
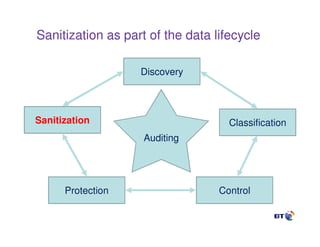
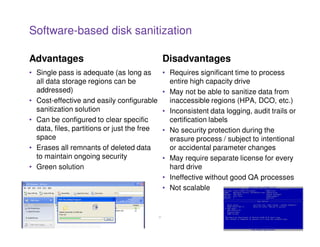
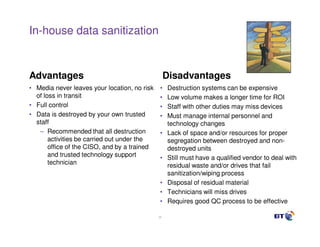
This document discusses effective practices for ensuring data destruction when decommissioning digital media. It emphasizes the importance of having a formal sanitization process and policy to mitigate risks from failed data removal. The types of media sanitization are described as clearing, purging and destroying data, with purging providing protection against laboratory attacks. Both software and hardware-based methods are outlined, including the benefits of secure erase for purging and degaussing for data destruction. Regulations and standards that inform policies are also referenced.