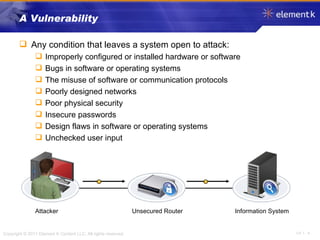
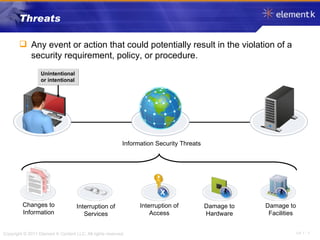
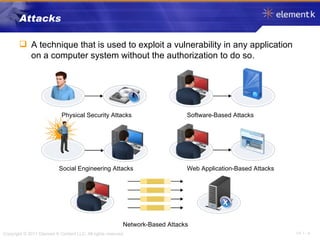
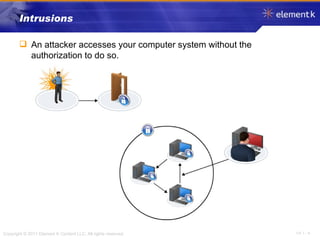
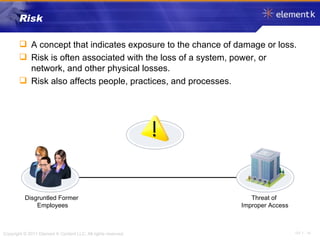
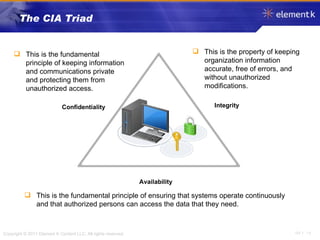
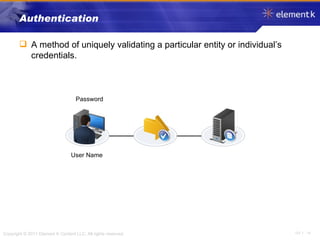
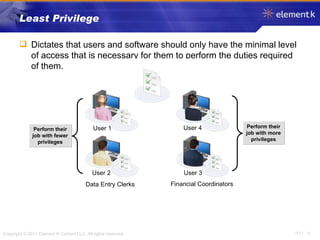
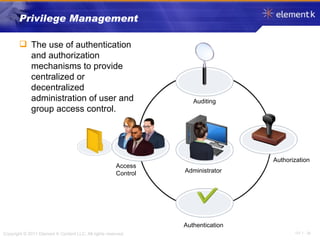
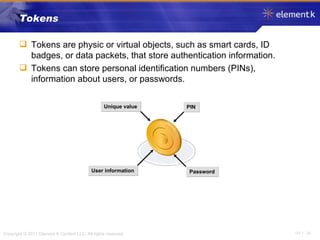
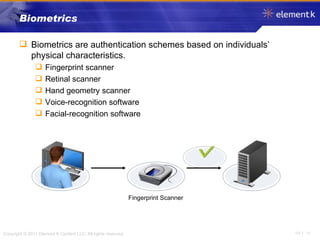
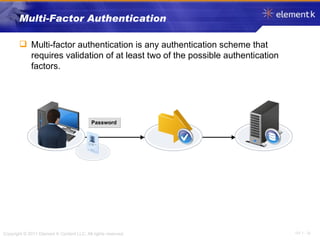
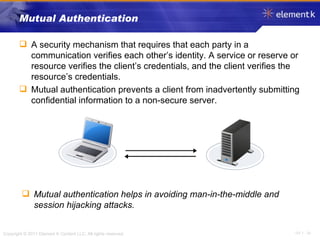
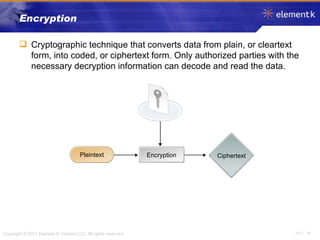
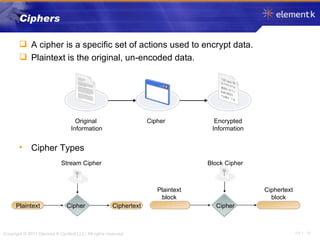
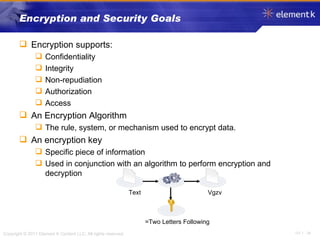
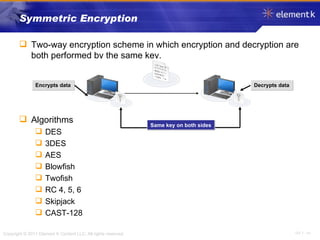
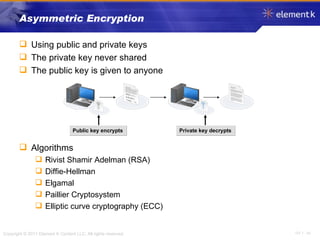
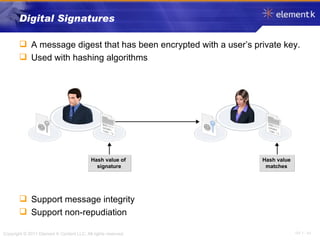
The document discusses several key concepts in information security including the goals of security like prevention, detection and recovery. It covers threats, vulnerabilities, attacks and different types of controls. It also explains authentication methods like passwords, tokens, biometrics and multifactor authentication. Finally, it summarizes cryptography fundamentals including encryption, ciphers, hashing and symmetric/asymmetric encryption algorithms.