Embed presentation
Download to read offline








This document discusses intrusion detection and prevention systems (IDPS). It defines the key concepts of intrusion detection, prevention, reaction, and correction. There are two main types of IDPS: network-based systems which monitor network traffic for attacks, and host-based systems which monitor activity on individual hosts. The document outlines the advantages and disadvantages of both approaches. It also describes different models of network-based IDPS including wireless and network behavior analysis systems.

















Overview of intrusion detection and prevention systems and their importance in protecting assets.
Defines intrusion detection and prevention, emphasizing actions for intrusion detection and reaction.
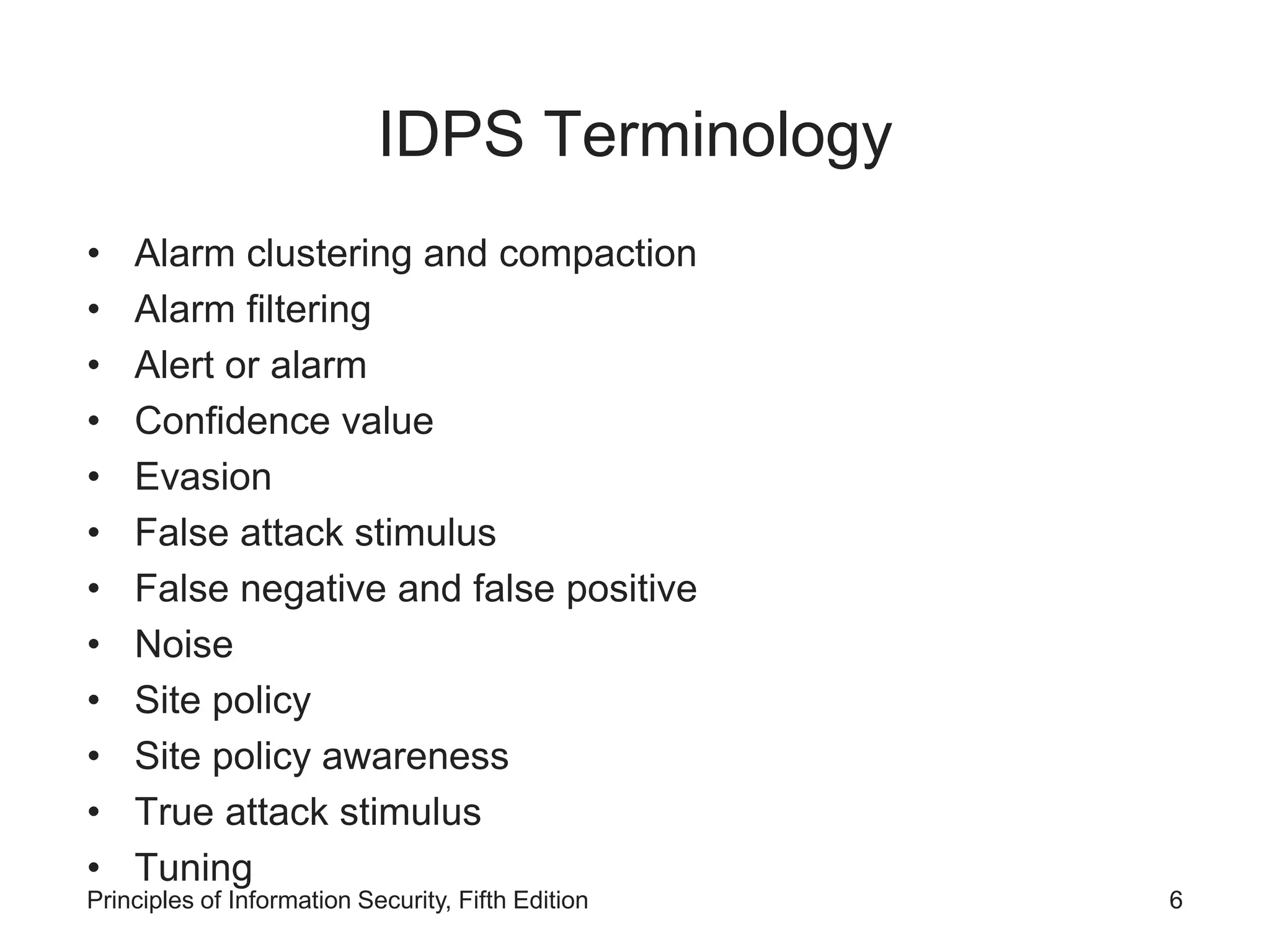
Key terms related to Intrusion Detection and Prevention Systems including alarm filtering and false positives.
Discusses the importance of IDPS for detecting intrusions, data collection post-attack, and enhancing security.
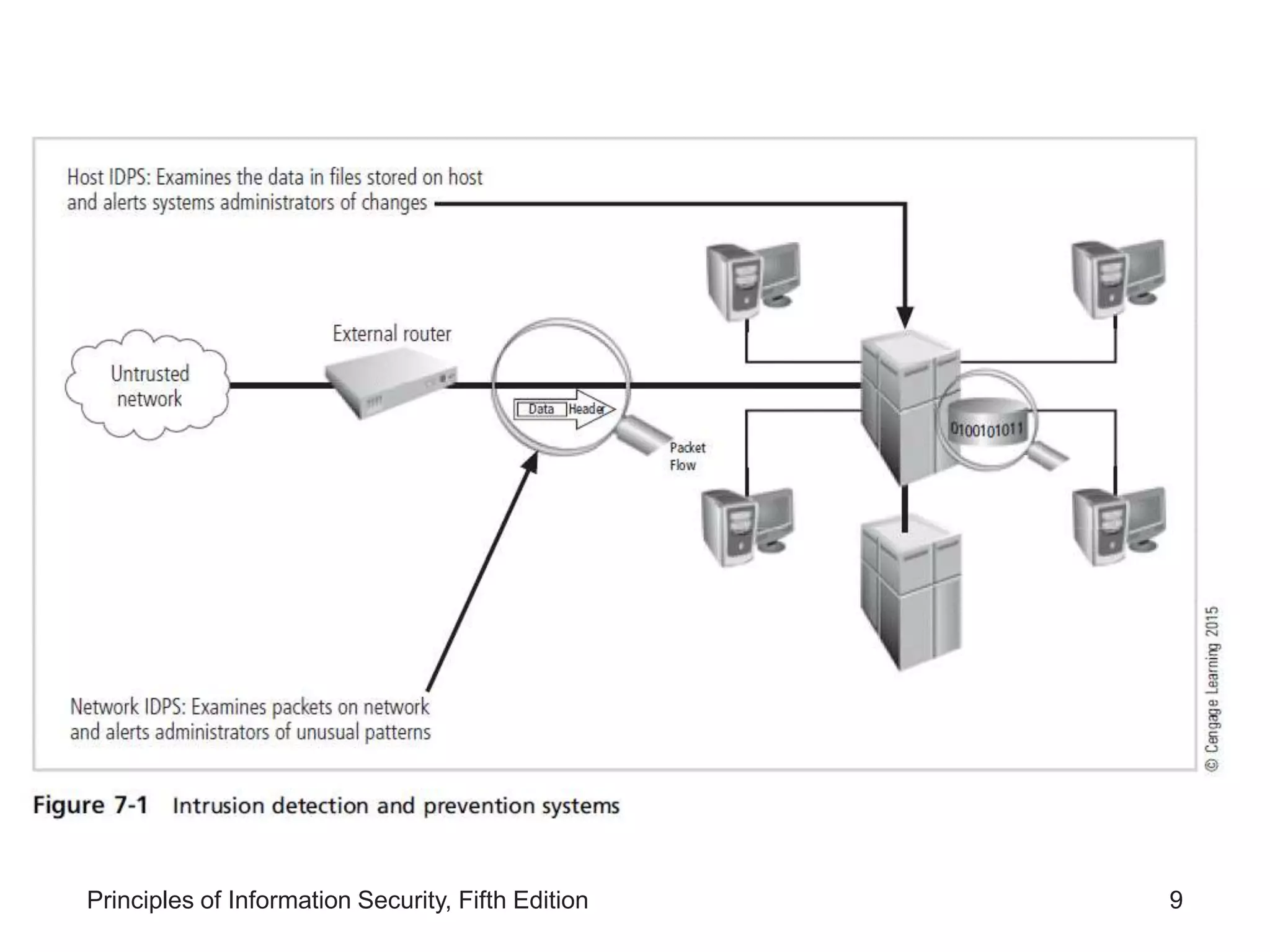
Types of network-based intrusion detection systems and their operational principles and advantages.
Challenges and disadvantages faced by network-based IDPSs, including limitations with encrypted traffic.
Focuses on wireless network security and network behavior analysis systems detecting traffic flow issues.
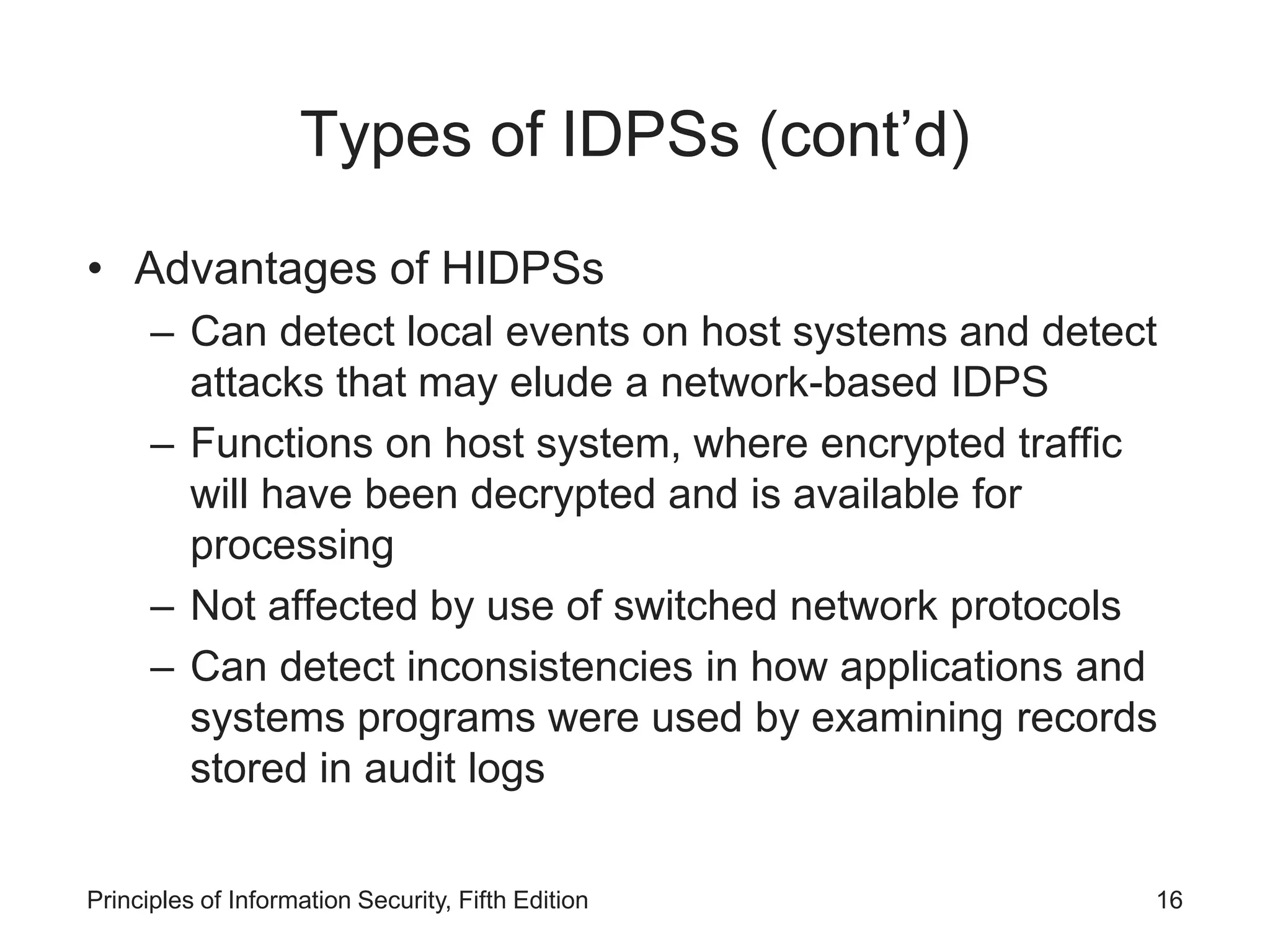
Describes host-based intrusion detection systems, their monitoring capabilities, and advantages over network-based systems.
Explores the disadvantages of host-based detection systems including vulnerability and performance issues.