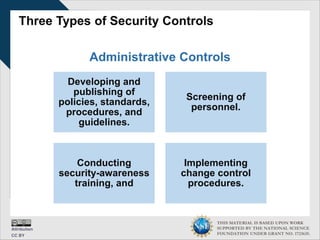
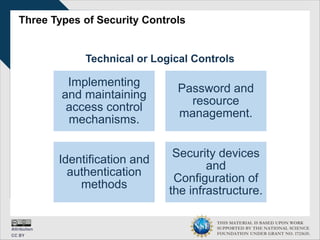
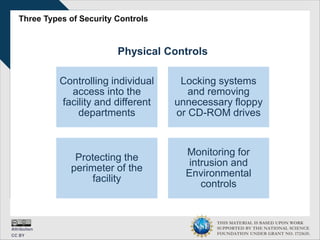
This document discusses cybersecurity and information technology. It is supported by a National Science Foundation grant. It covers topics such as the definition of information technology, information security, security roles and responsibilities, developing security policies and training programs, and effective cybersecurity practices. The goal is to educate about cybersecurity fundamentals and the importance of security awareness training.