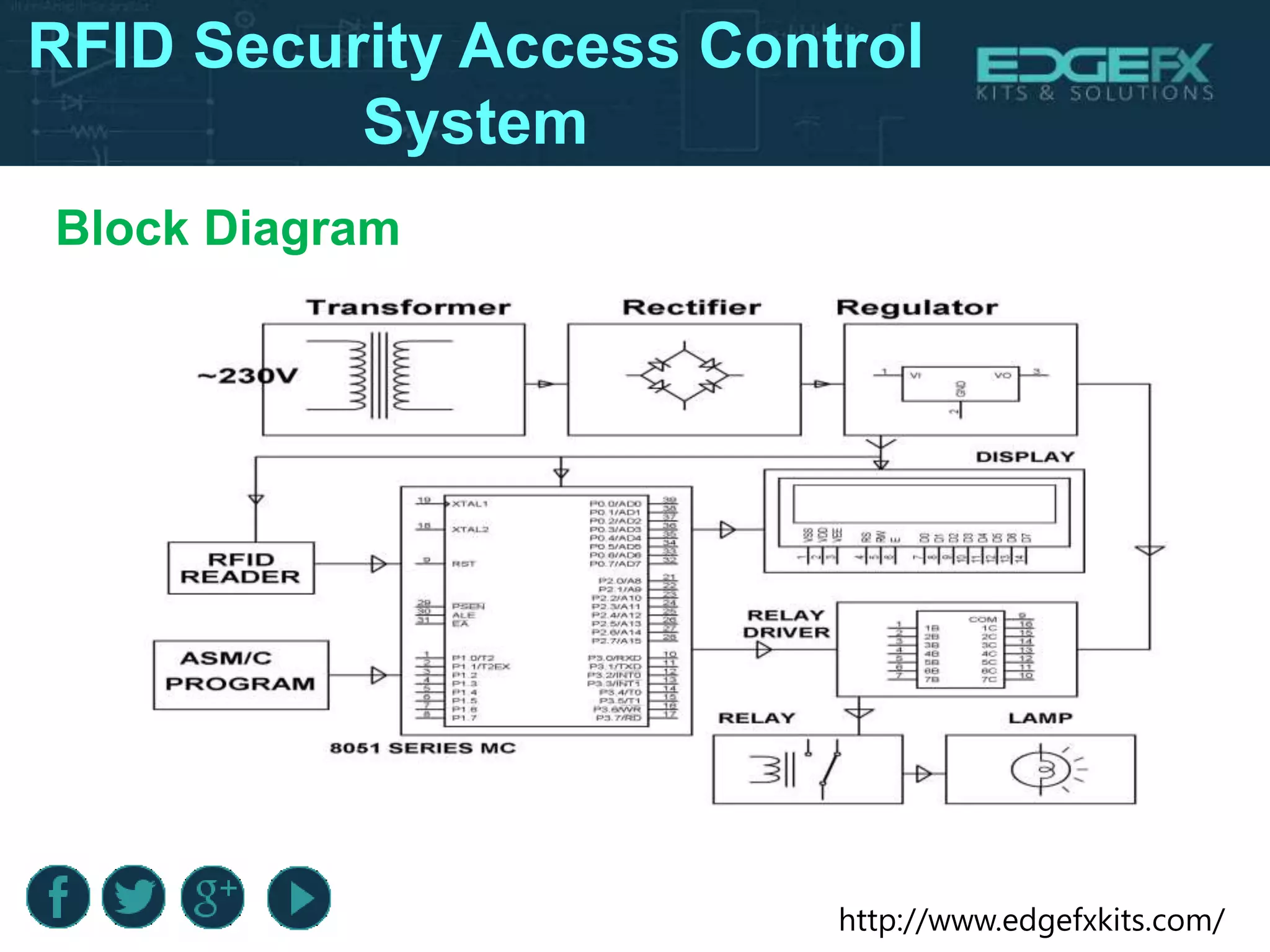
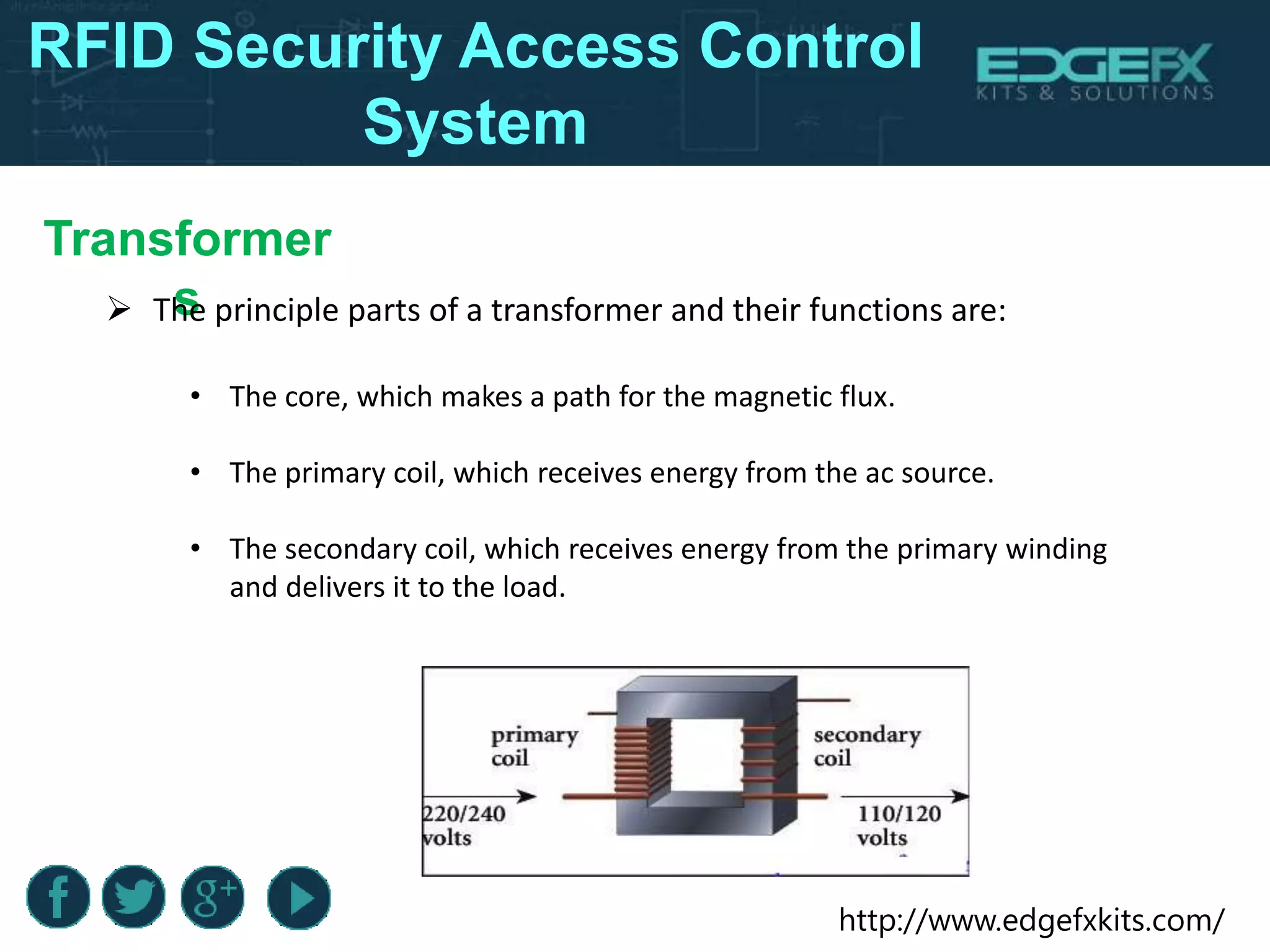
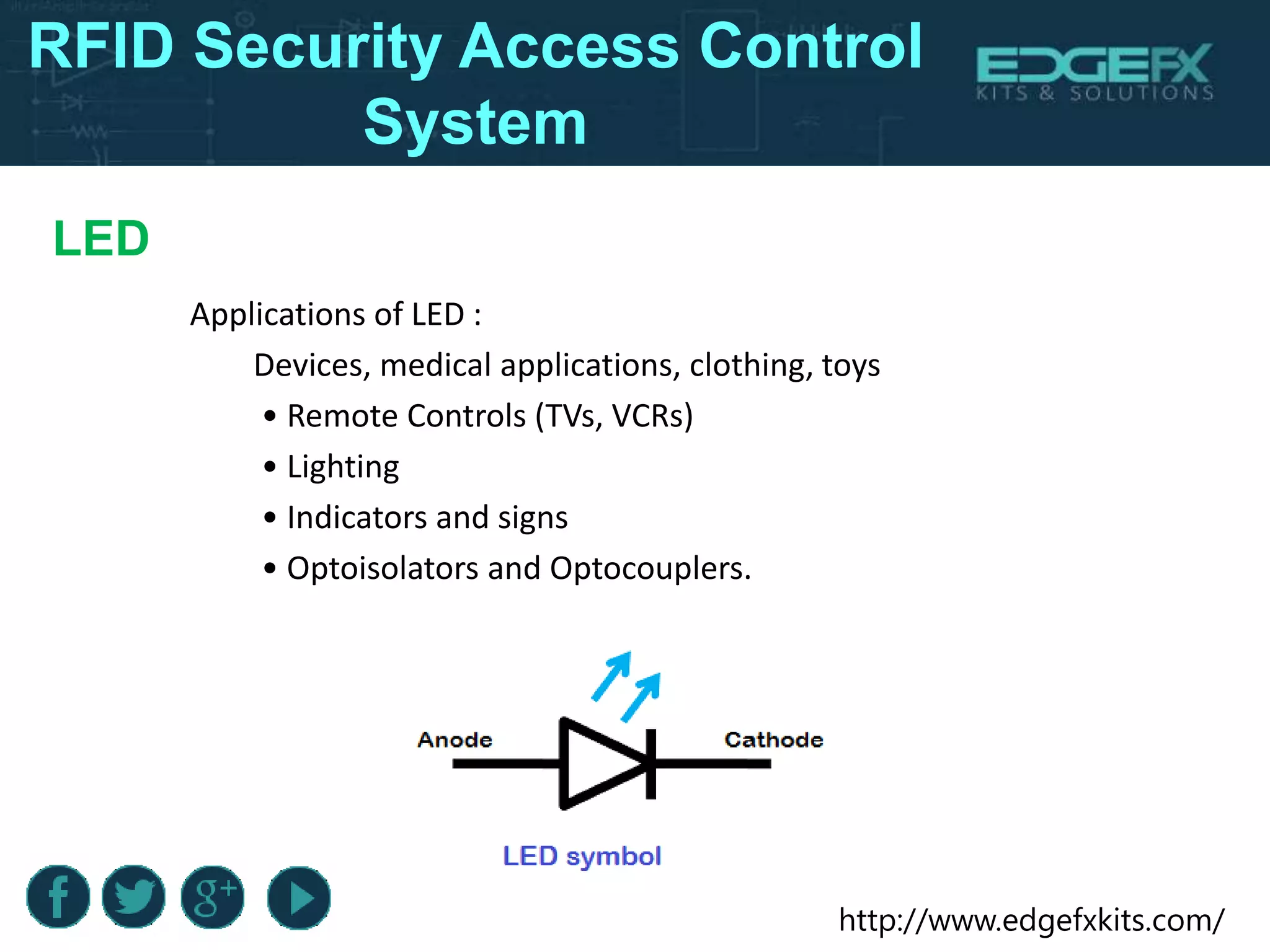
The document outlines the design and functioning of an RFID-based security access control system utilizing an 8051 microcontroller to ensure only authorized personnel gain access to secure areas. It details the hardware components involved, the working principles of RFID technology, including registration and recognition phases, and the associated circuits like relays and voltage regulators. Additionally, it highlights the benefits and limitations of the system, along with its potential applications in various high-security environments.