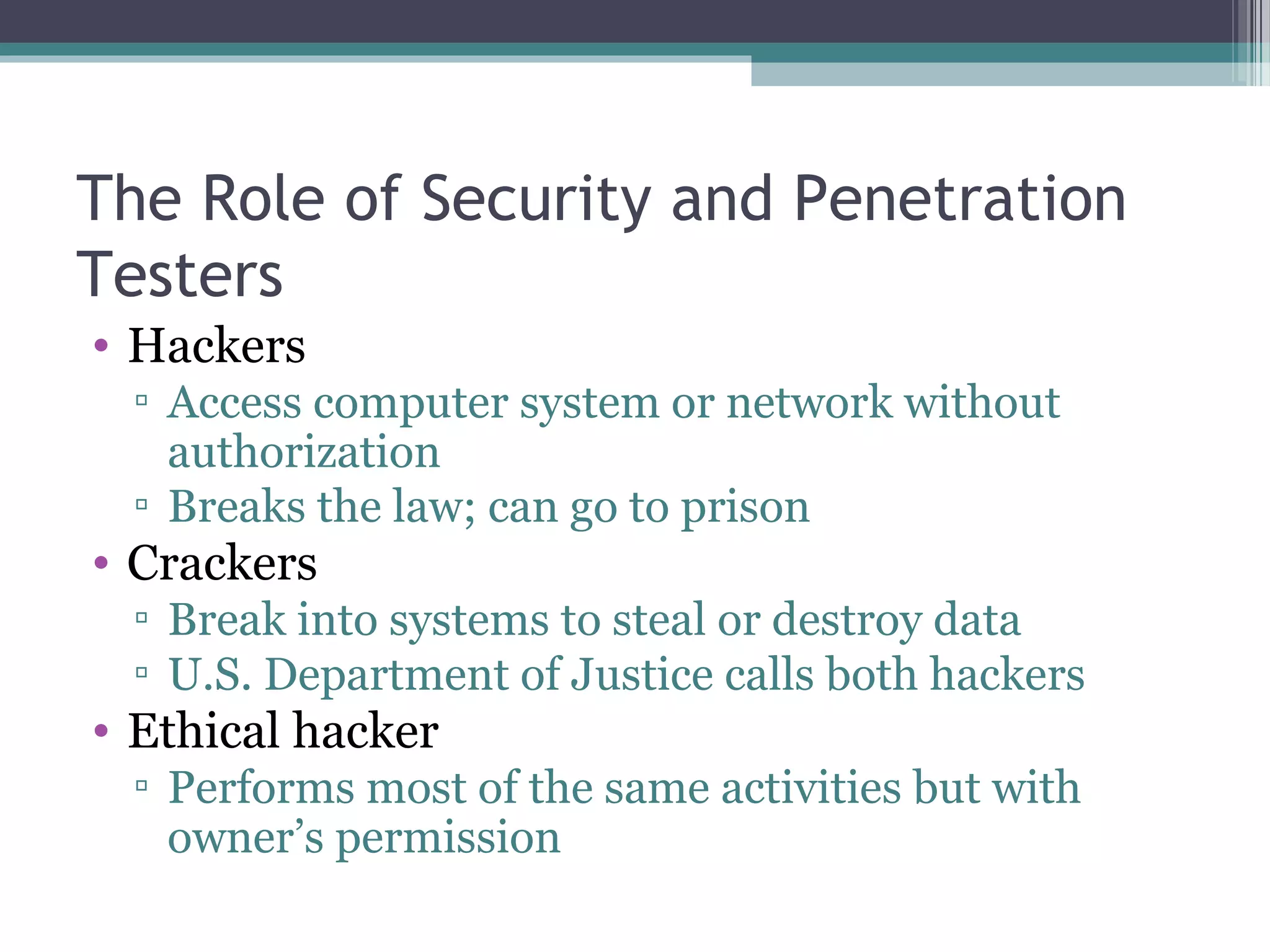
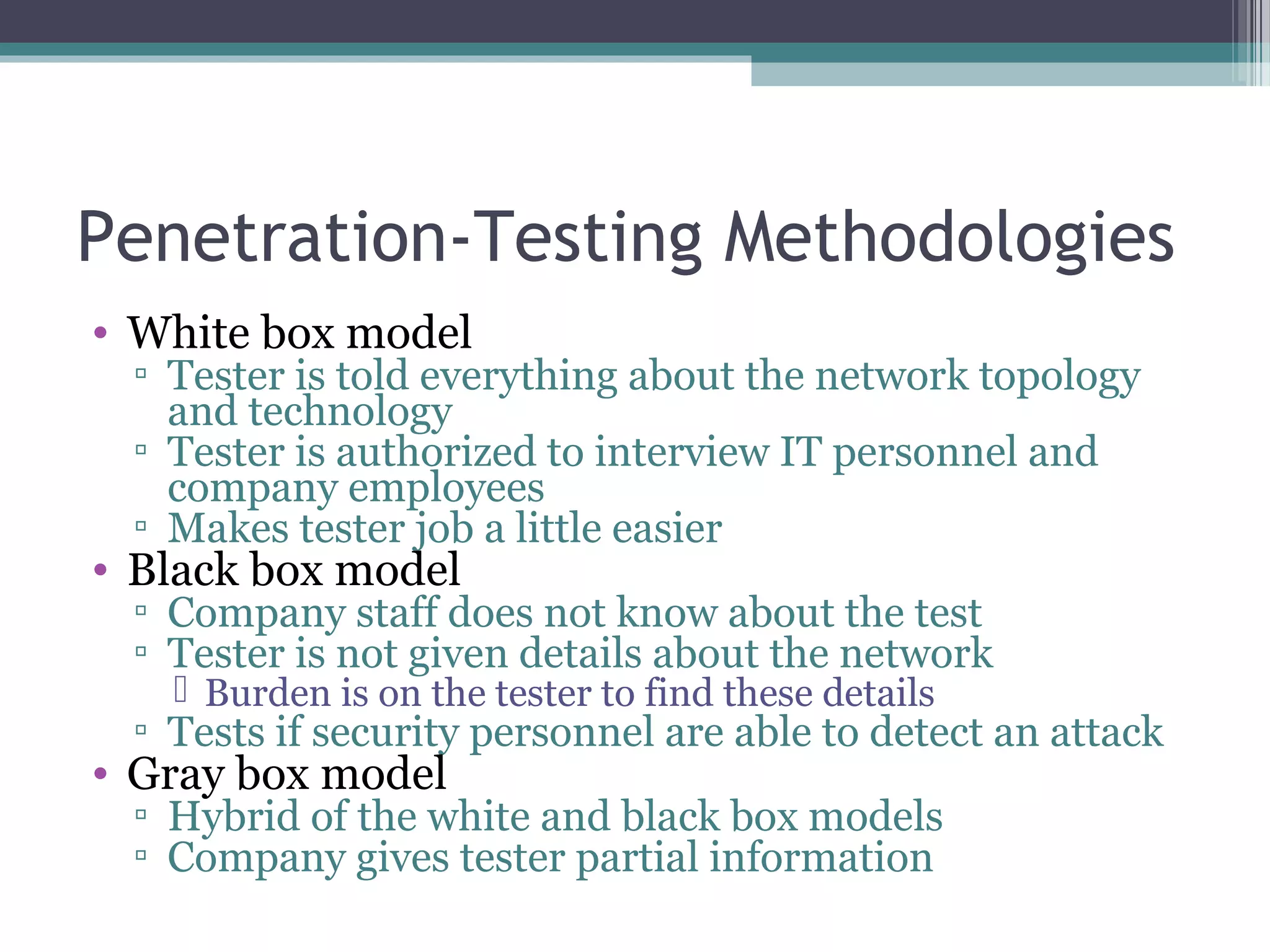
The document provides an overview of ethical hacking and penetration testing, outlining key concepts, methodologies, and certifications in the field. It explains the roles of ethical hackers, the distinctions between various hacker types, and the tools and methodologies used in penetration testing. Additionally, it offers resources for further learning and common questions in the area of security testing.