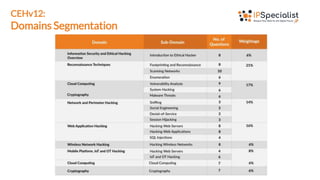
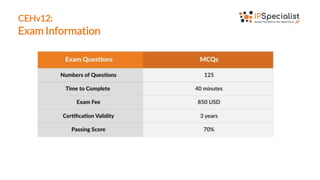
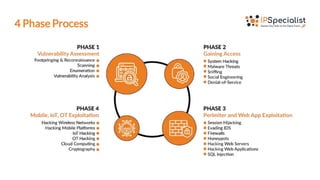
The document outlines the Certified Ethical Hacker v12 (CEH v12) exam, detailing its code (312-50), its relevance to cybersecurity professionals, and the domains covered such as reconnaissance, system and network hacking, cloud computing, and cryptography. It emphasizes the skills validated by the exam, including vulnerability identification and exploitation, understanding of attack types, and legal ethical considerations in hacking. The document also lists the target audience for the exam and highlights key learning topics for candidates.