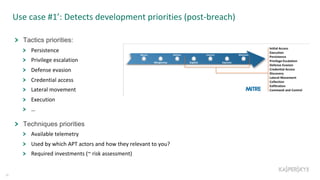
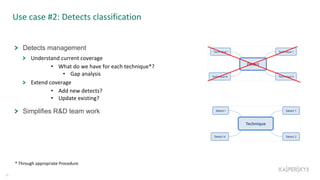
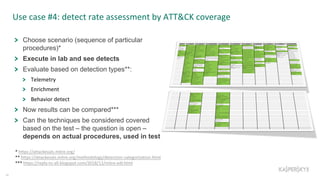
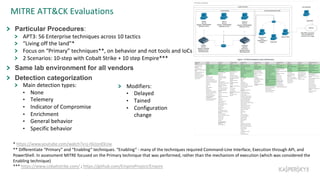
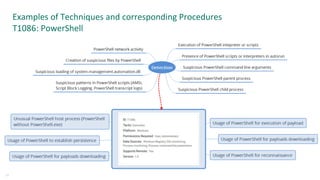
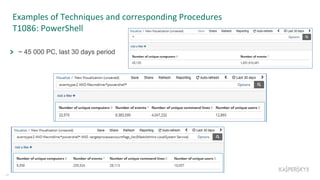
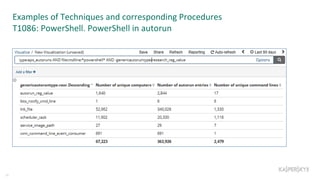
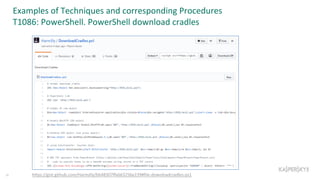
The document outlines the roles and backgrounds of Teymur Kheirkhabarov and Sergey Soldatov in security operations, emphasizing the importance of MITRE ATT&CK in enhancing detection strategies against cyber threats. It discusses various attack tactics, techniques, and procedures, alongside methodologies for evaluating detection capabilities and improving security operations. Several use cases illustrate how to effectively adapt and test detection methods to maintain security against advanced threats.











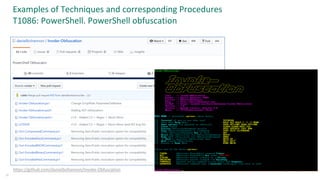

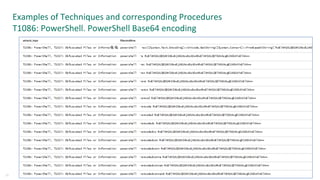
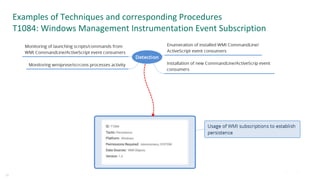
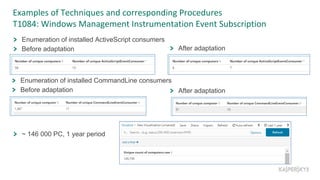

![Other sources of detect ideas – TI from operations
28
Public
Twitter, blogs, talks, etc.
Tests*
Private
Internal threat research
Operations practice
Threat hunting**
DFIRMA***
Security Assessment/Red teaming
* https://attackevals.mitre.org/evaluations.html , for example
** the practice of searching iteratively through data to detect [advanced] threats that evade automatic security solutions
*** Digital forensics, Incident response, Malware analysis](https://image.slidesharecdn.com/mitre-colaboratory-v4-190108111157/85/How-MITRE-ATT-CK-helps-security-operations-28-320.jpg)