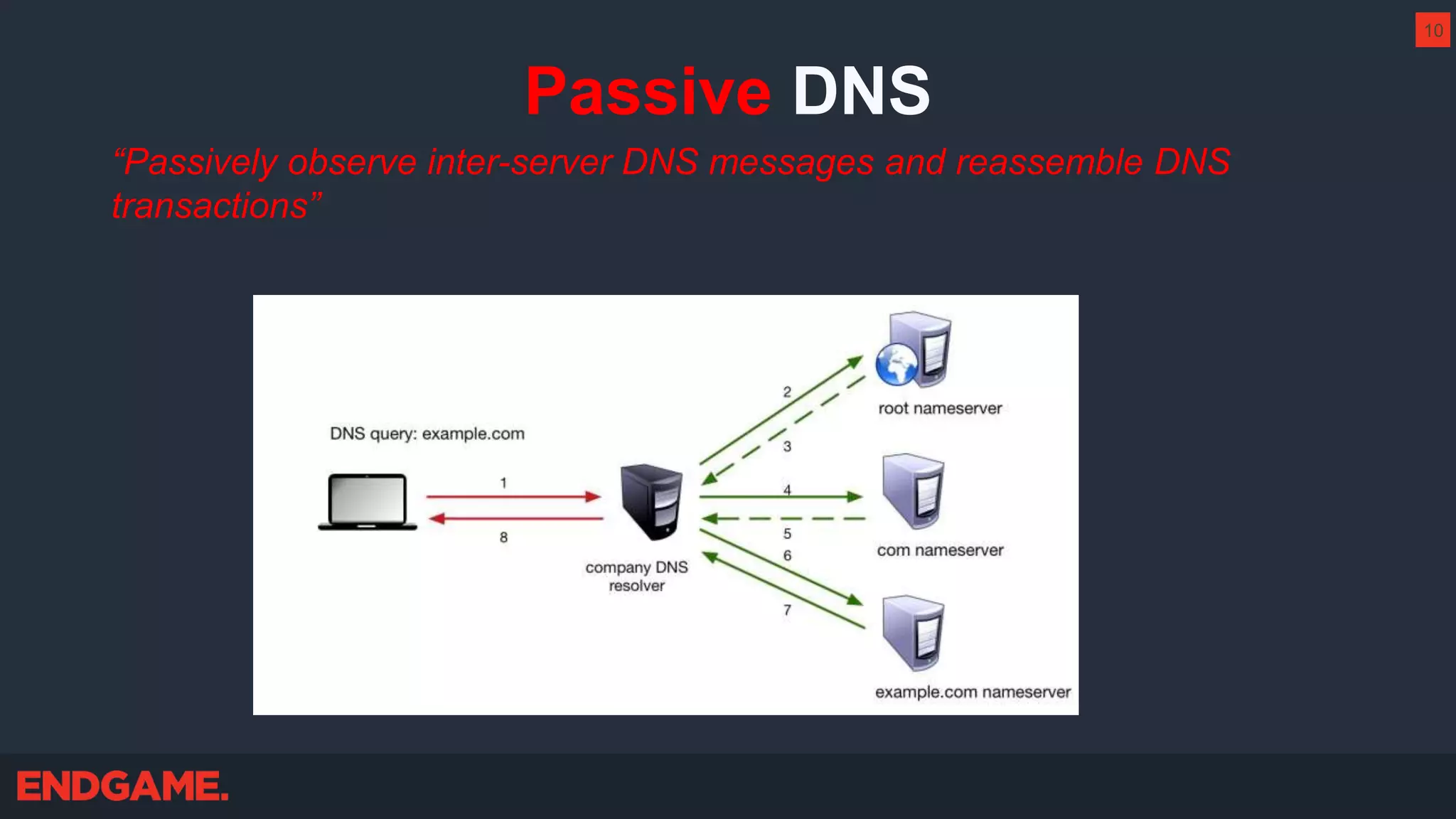
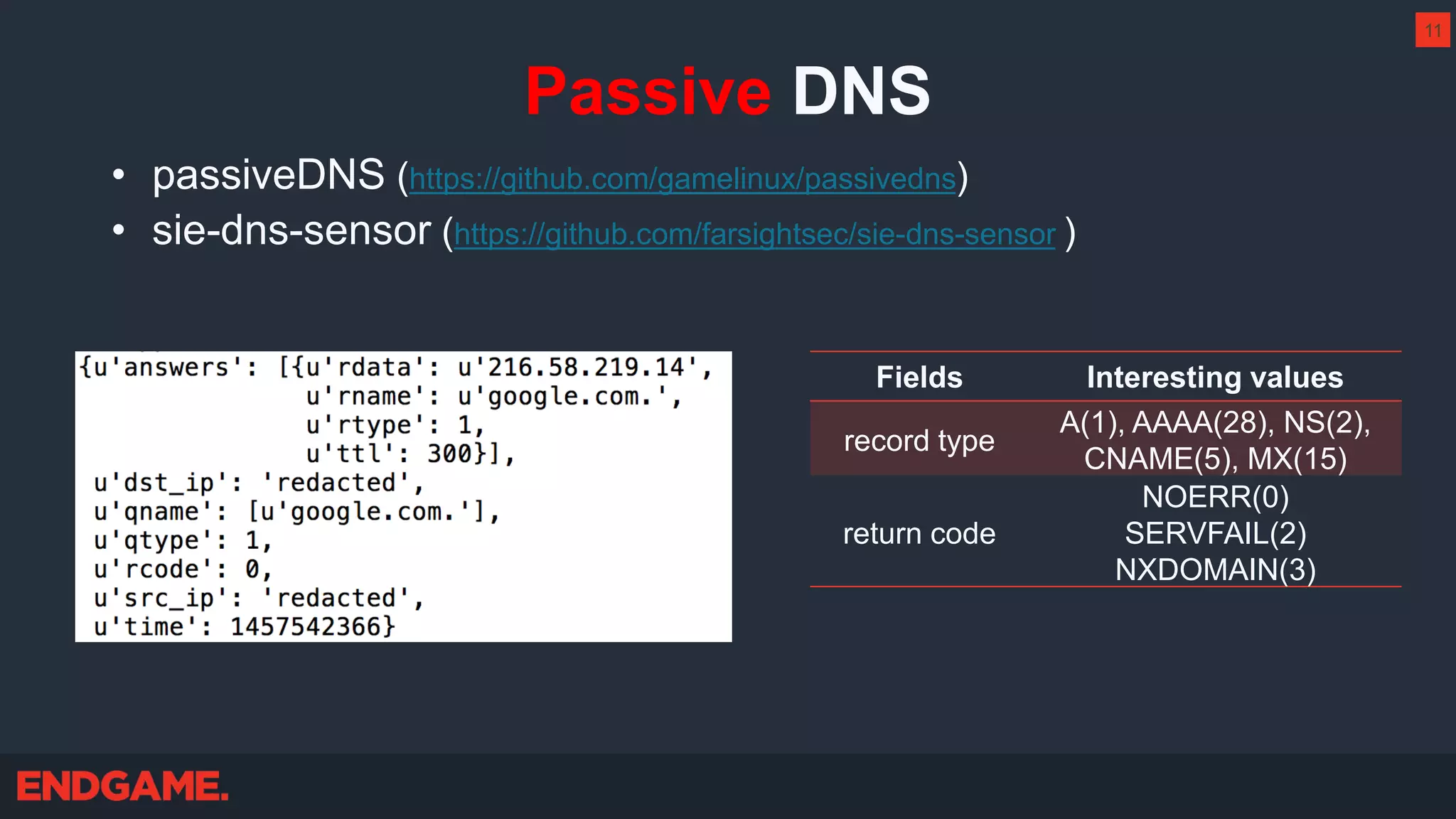
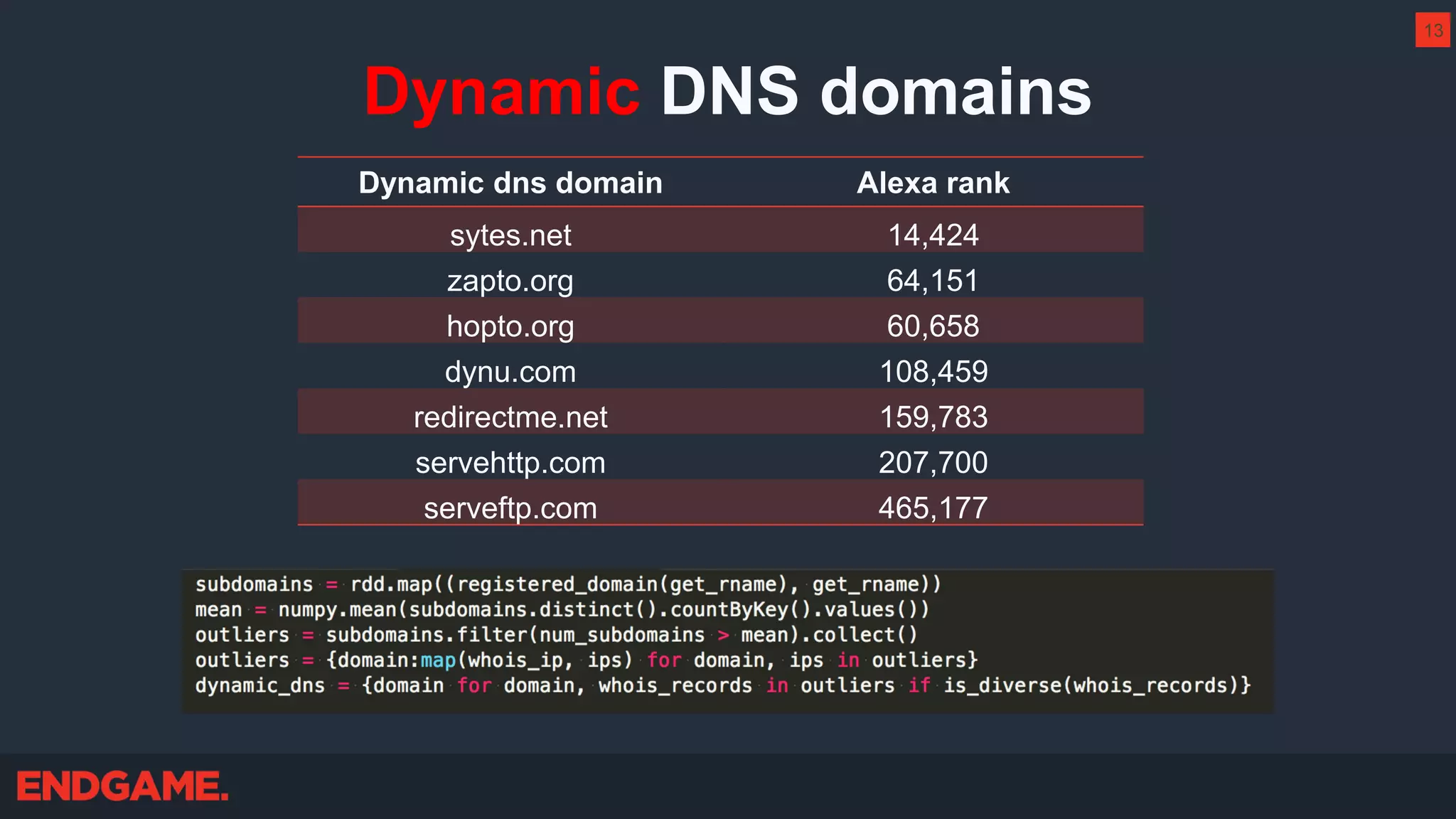
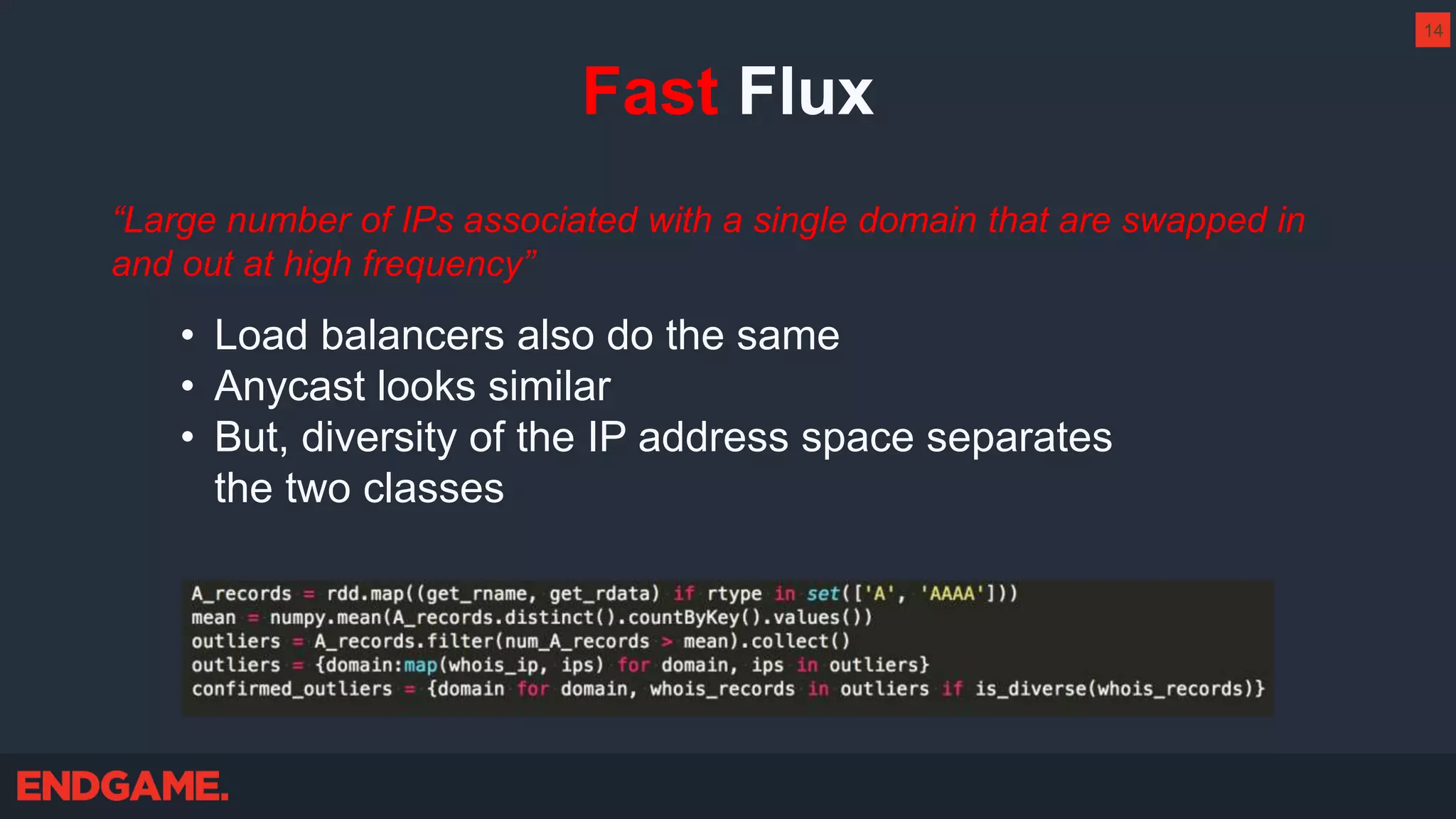
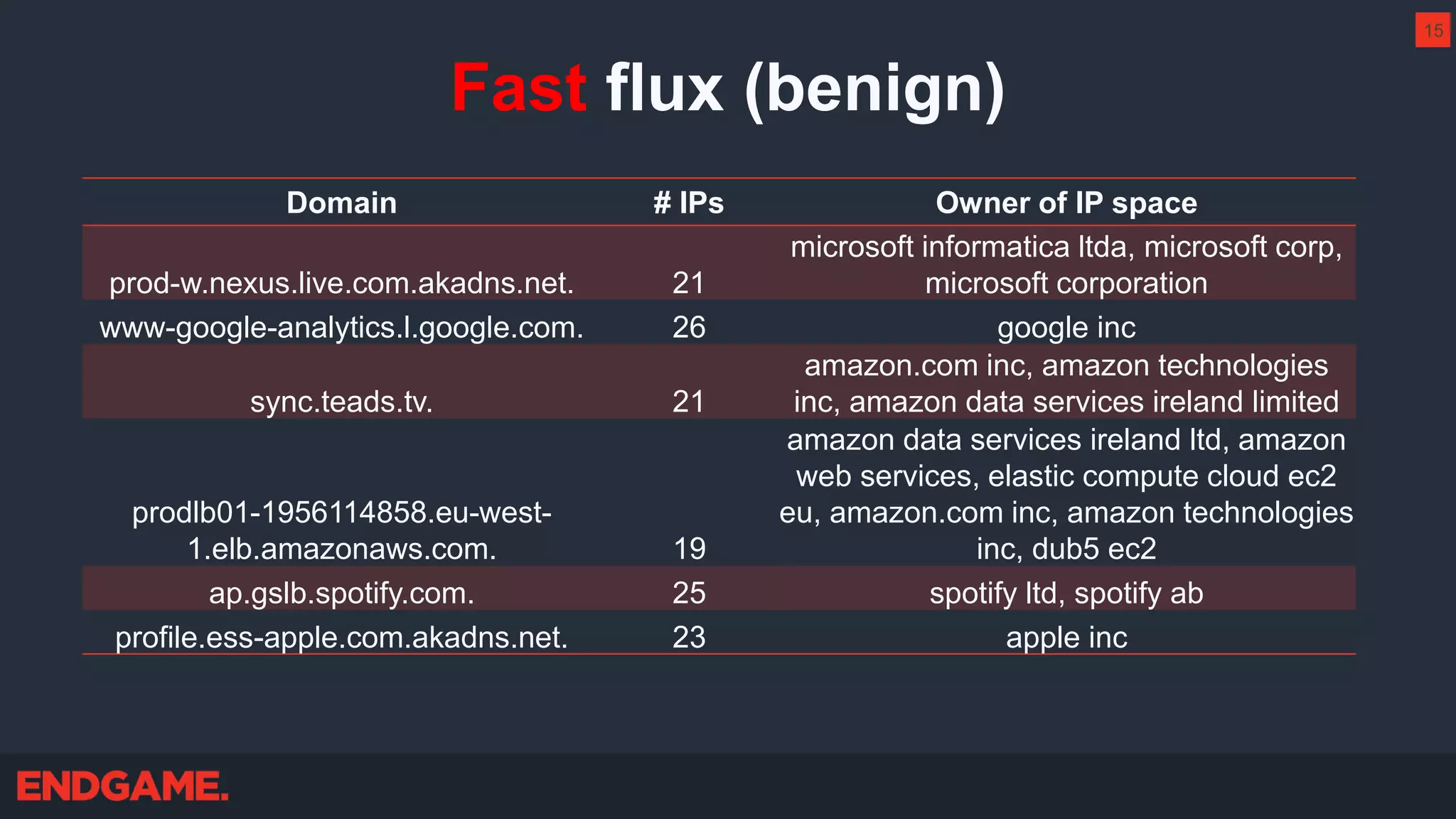
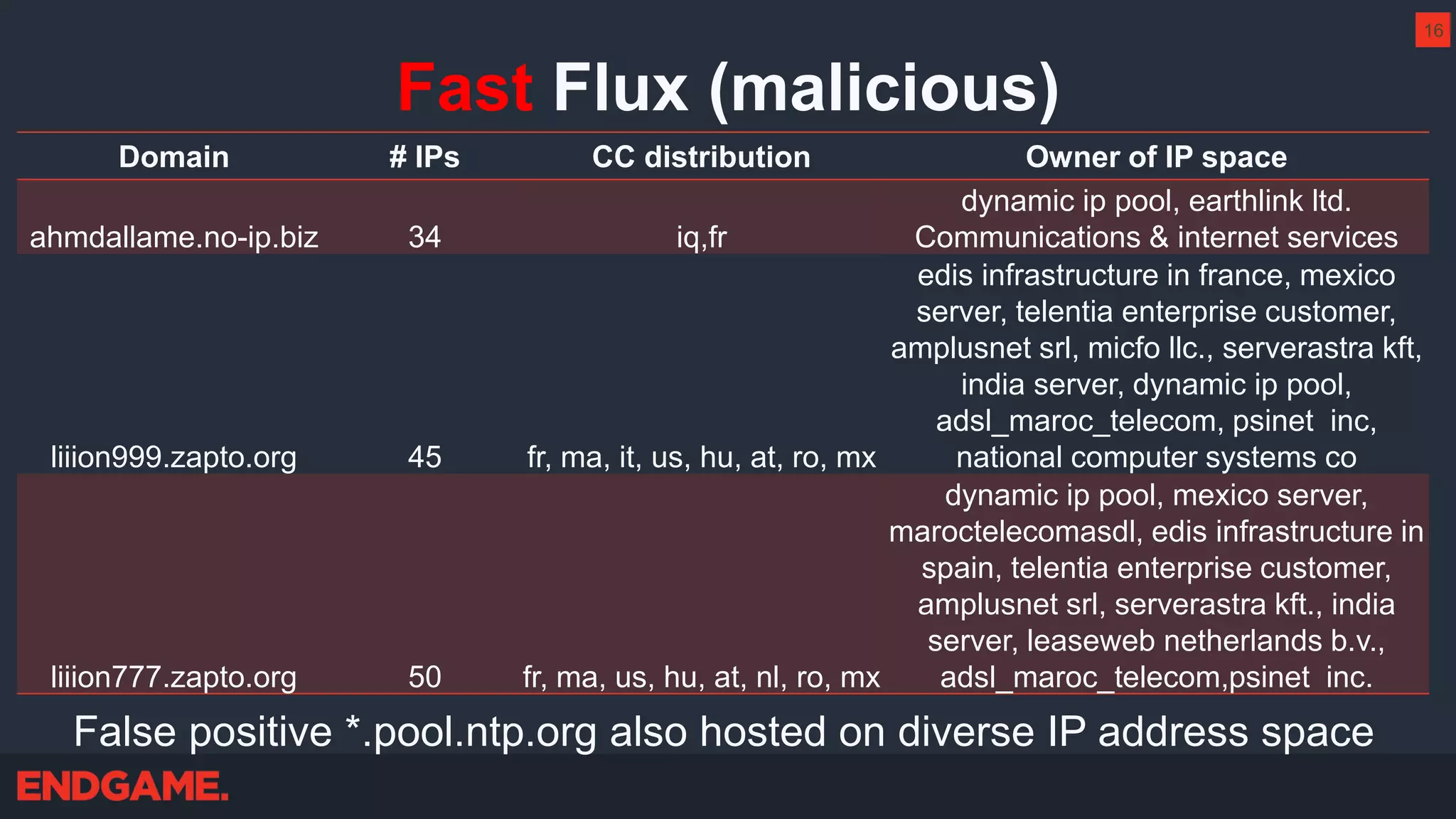
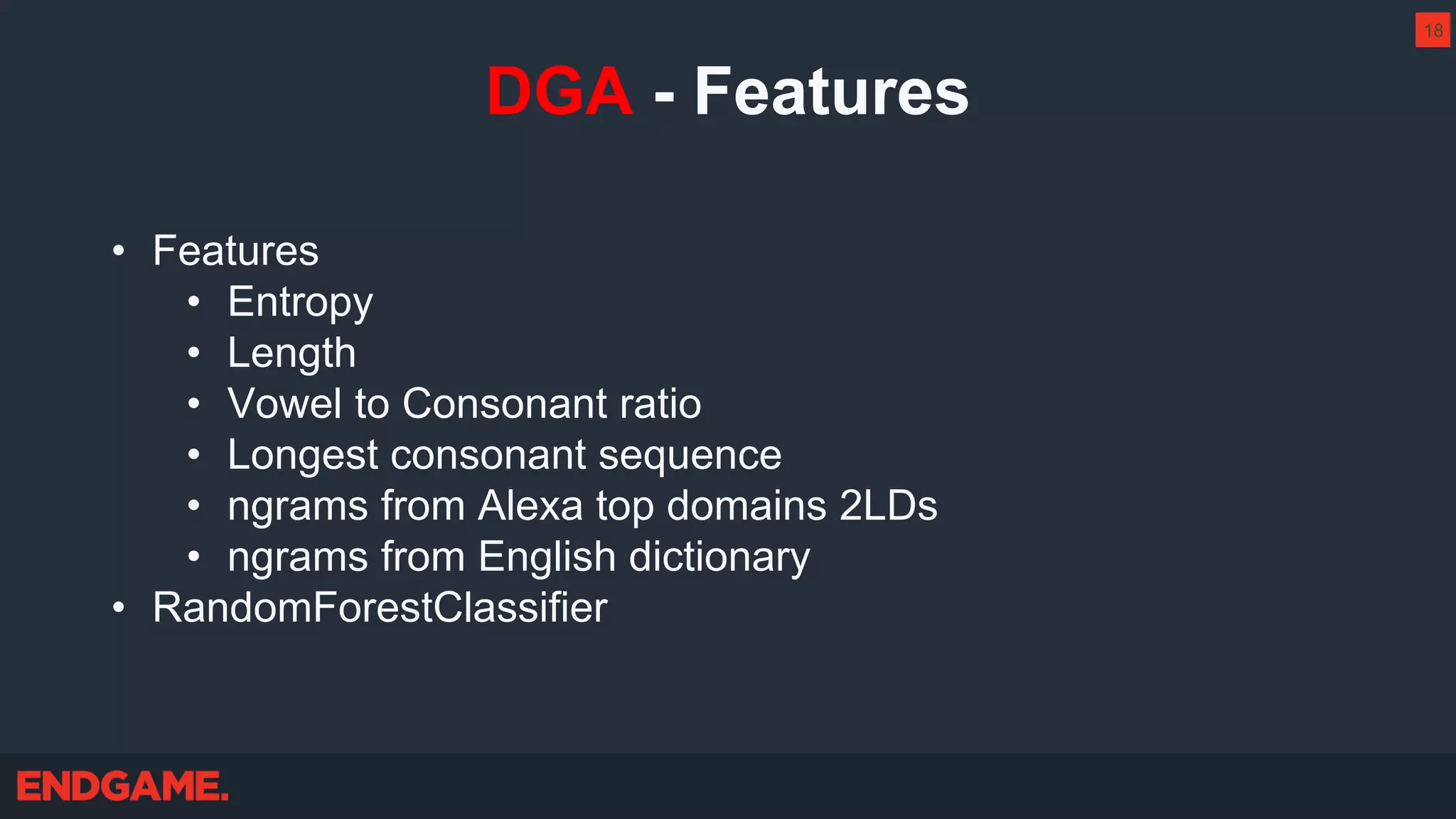
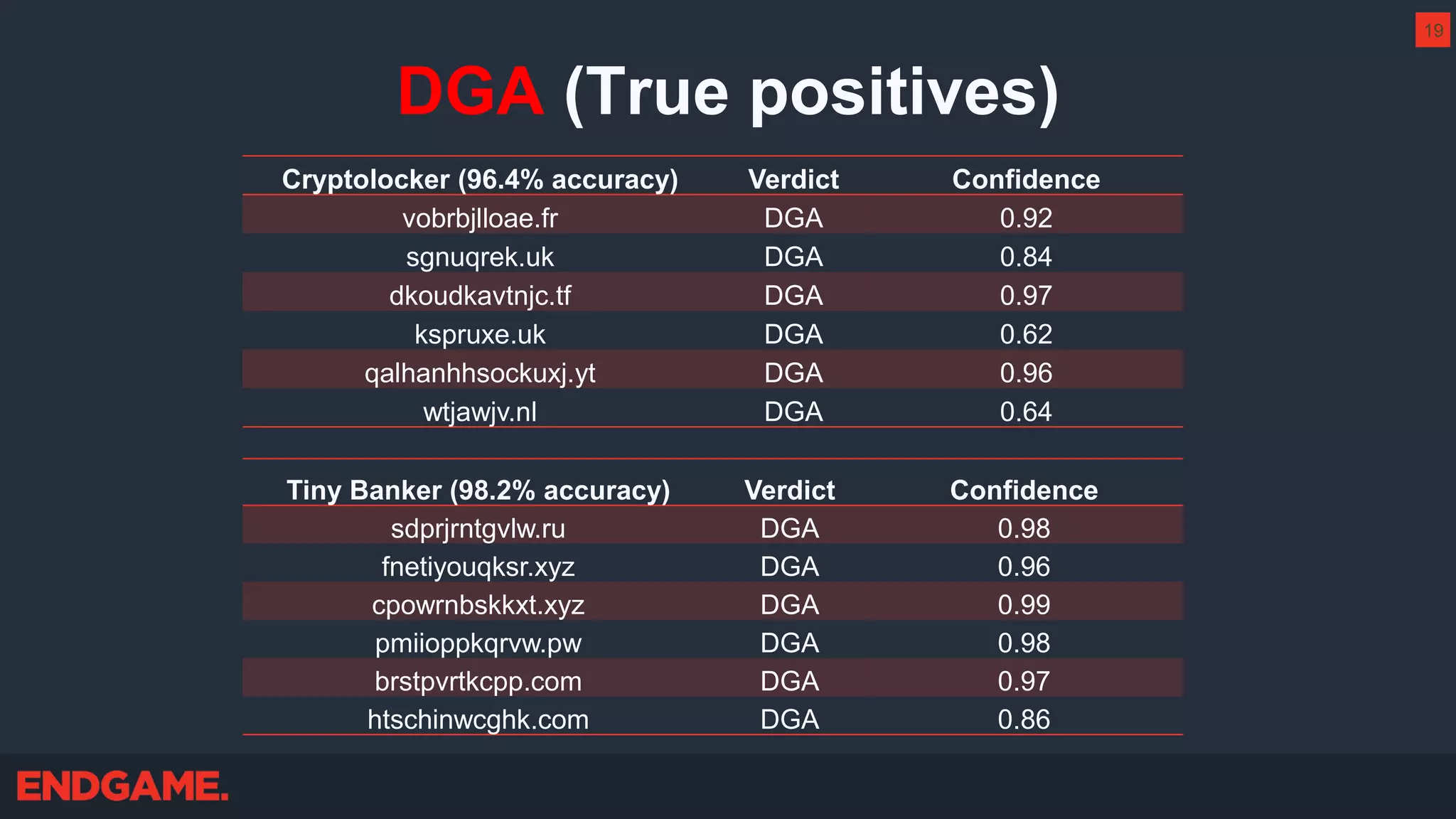
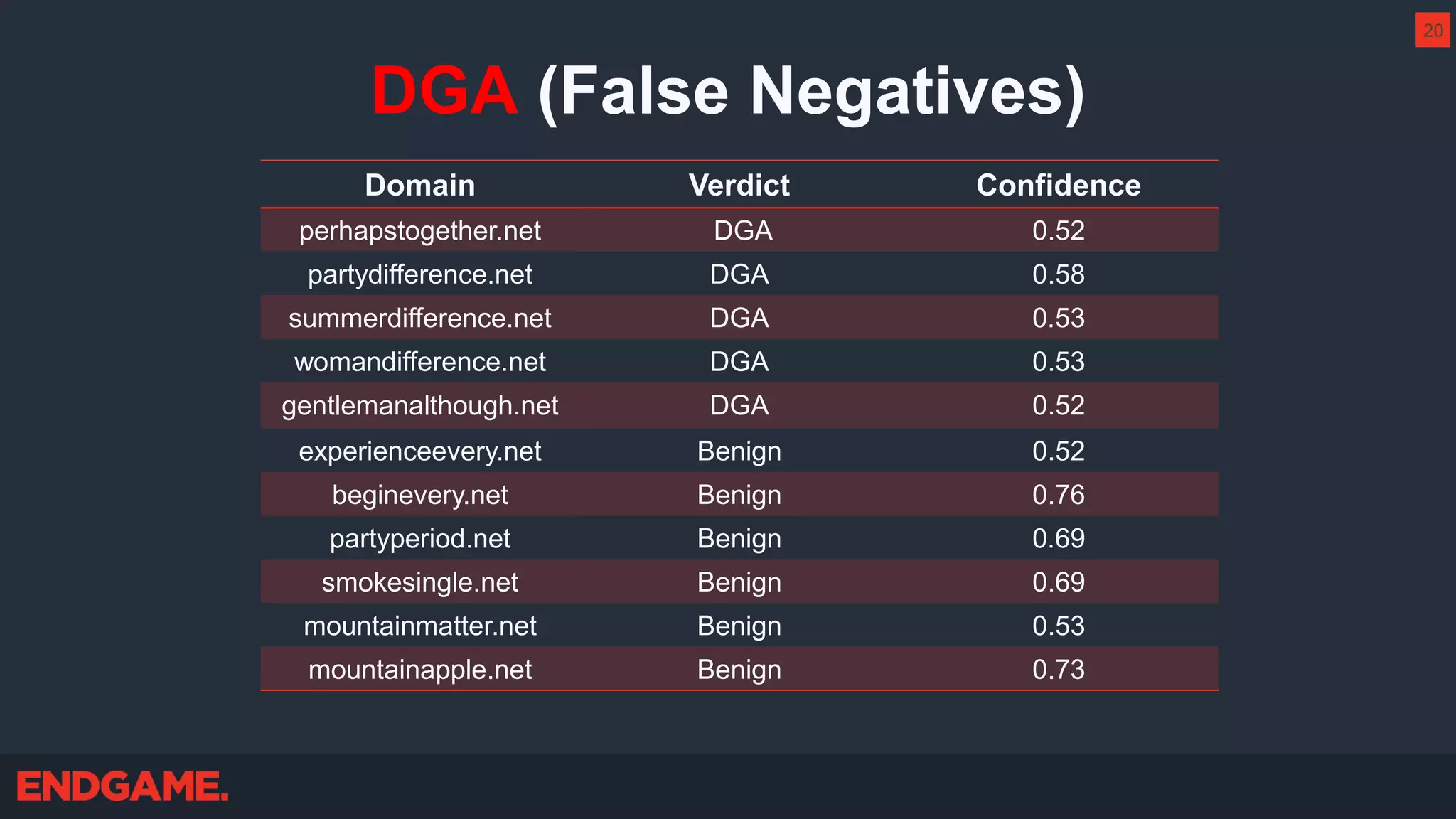
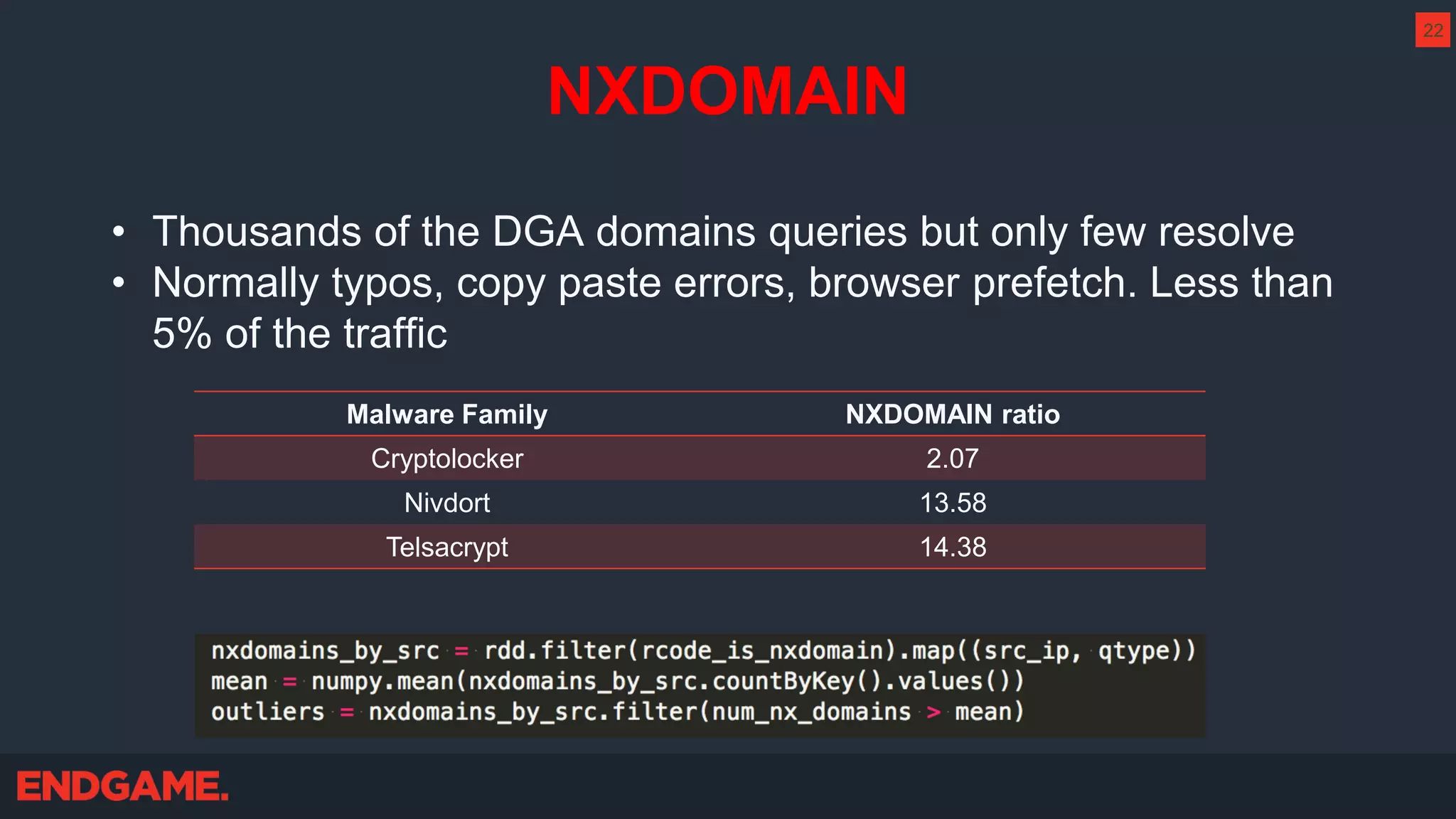
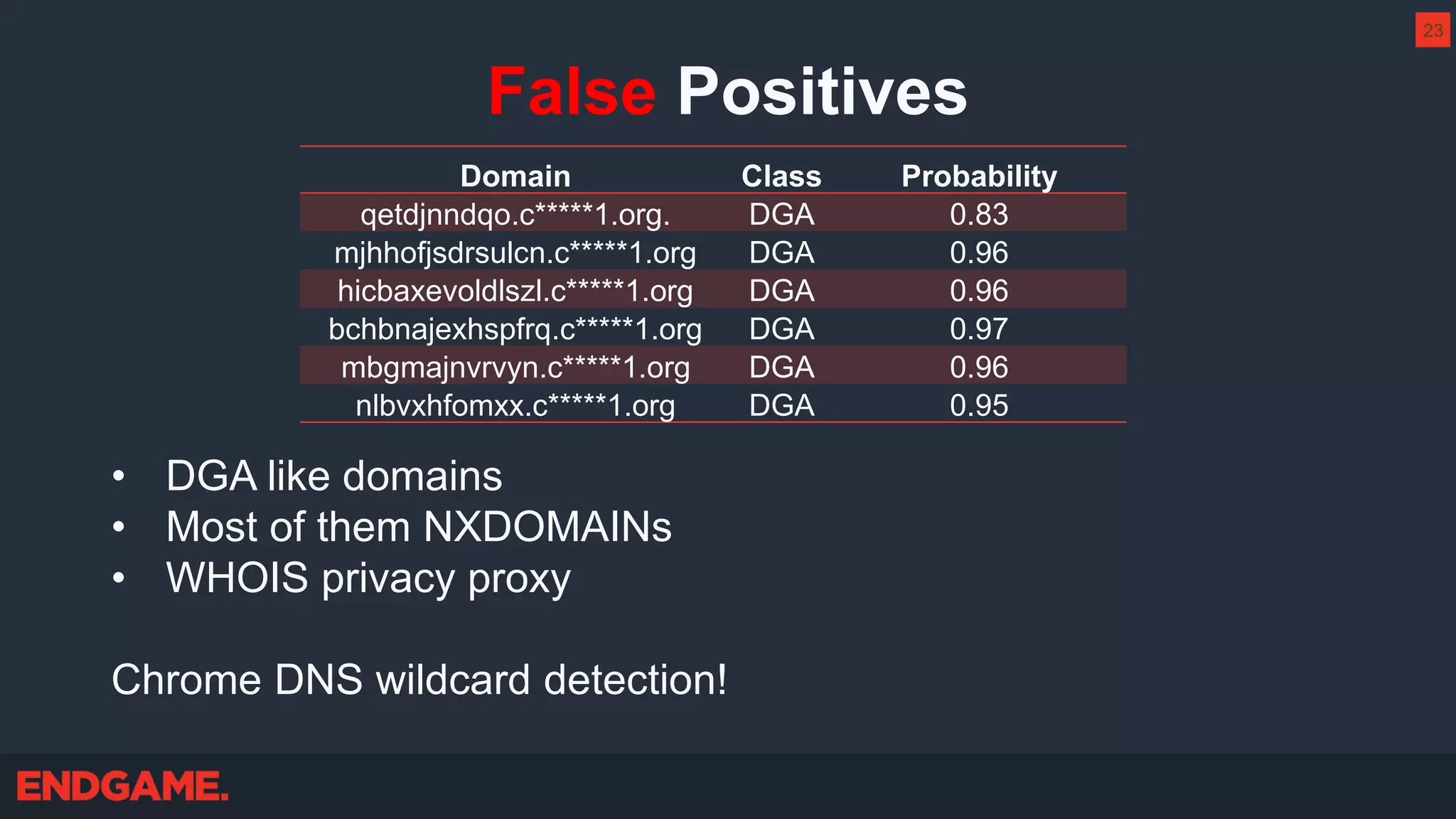
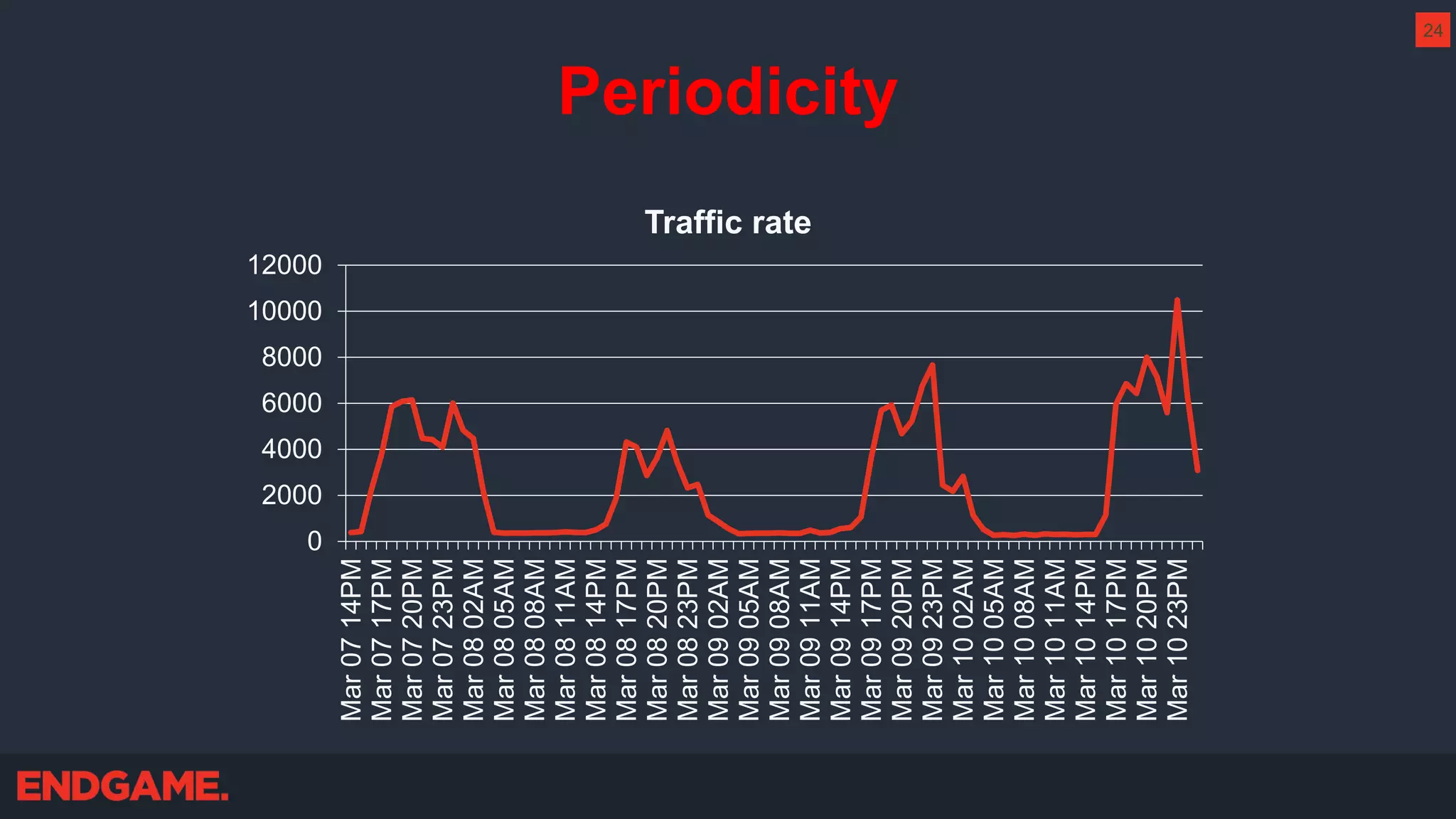
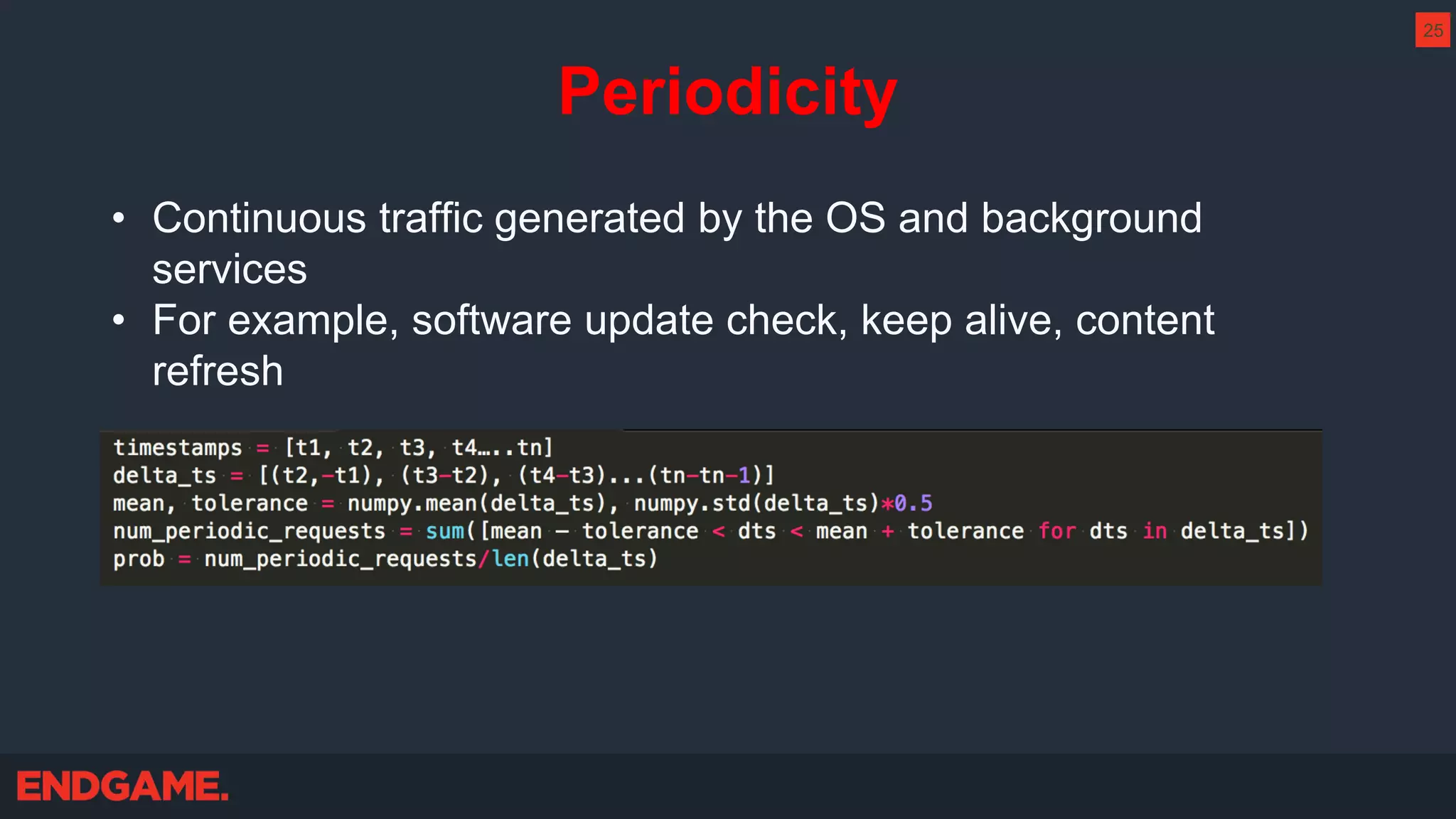
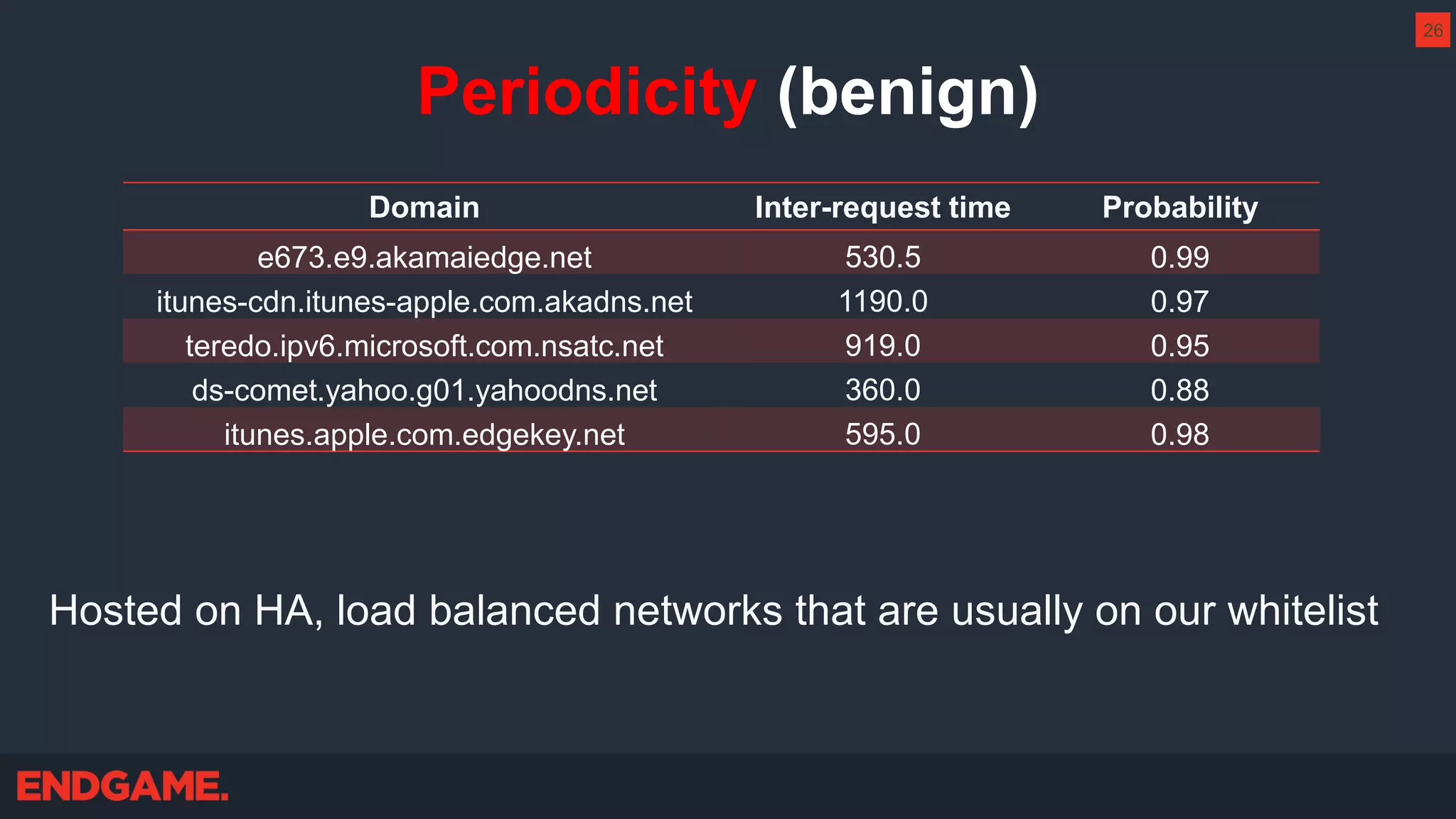
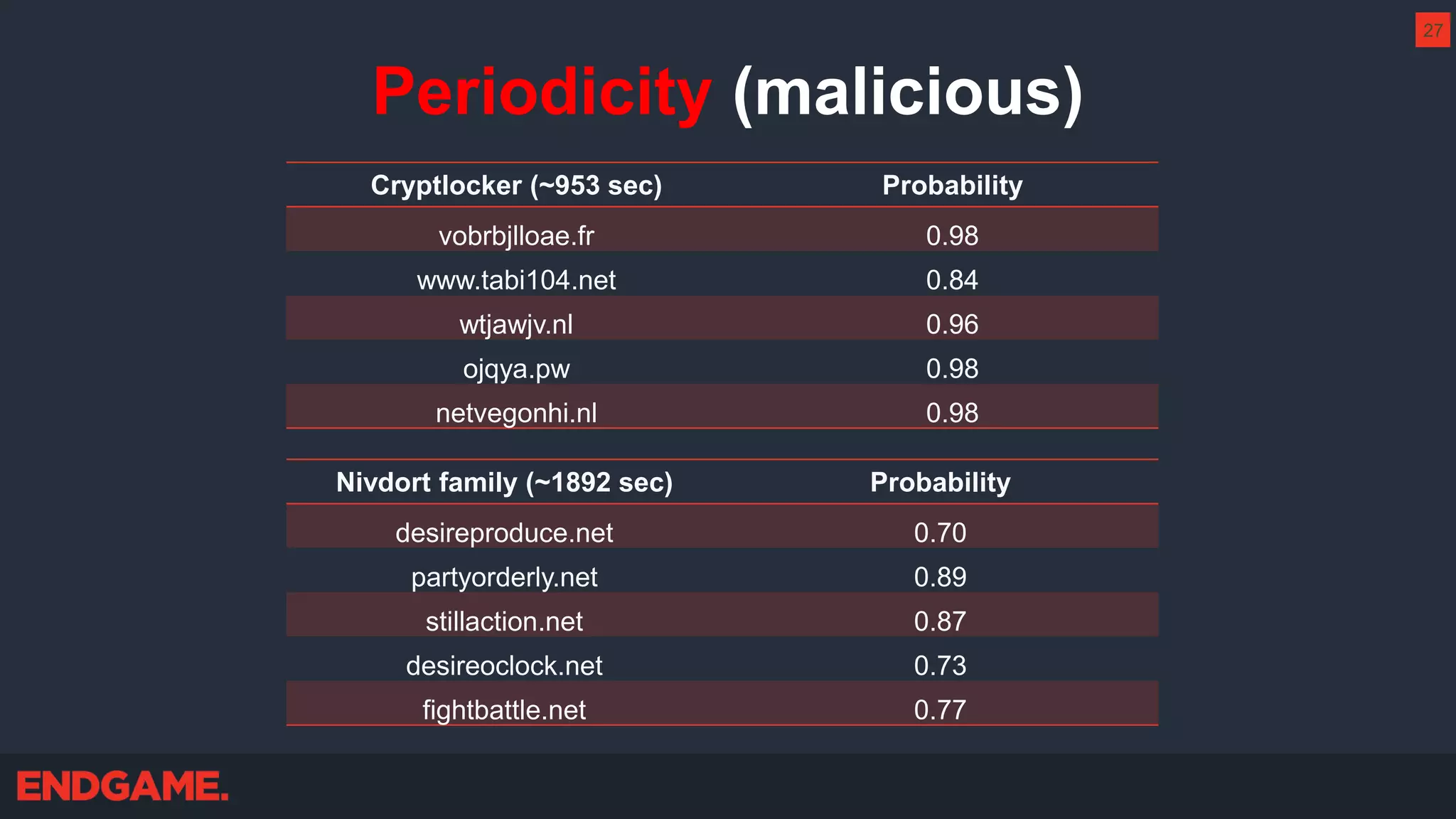
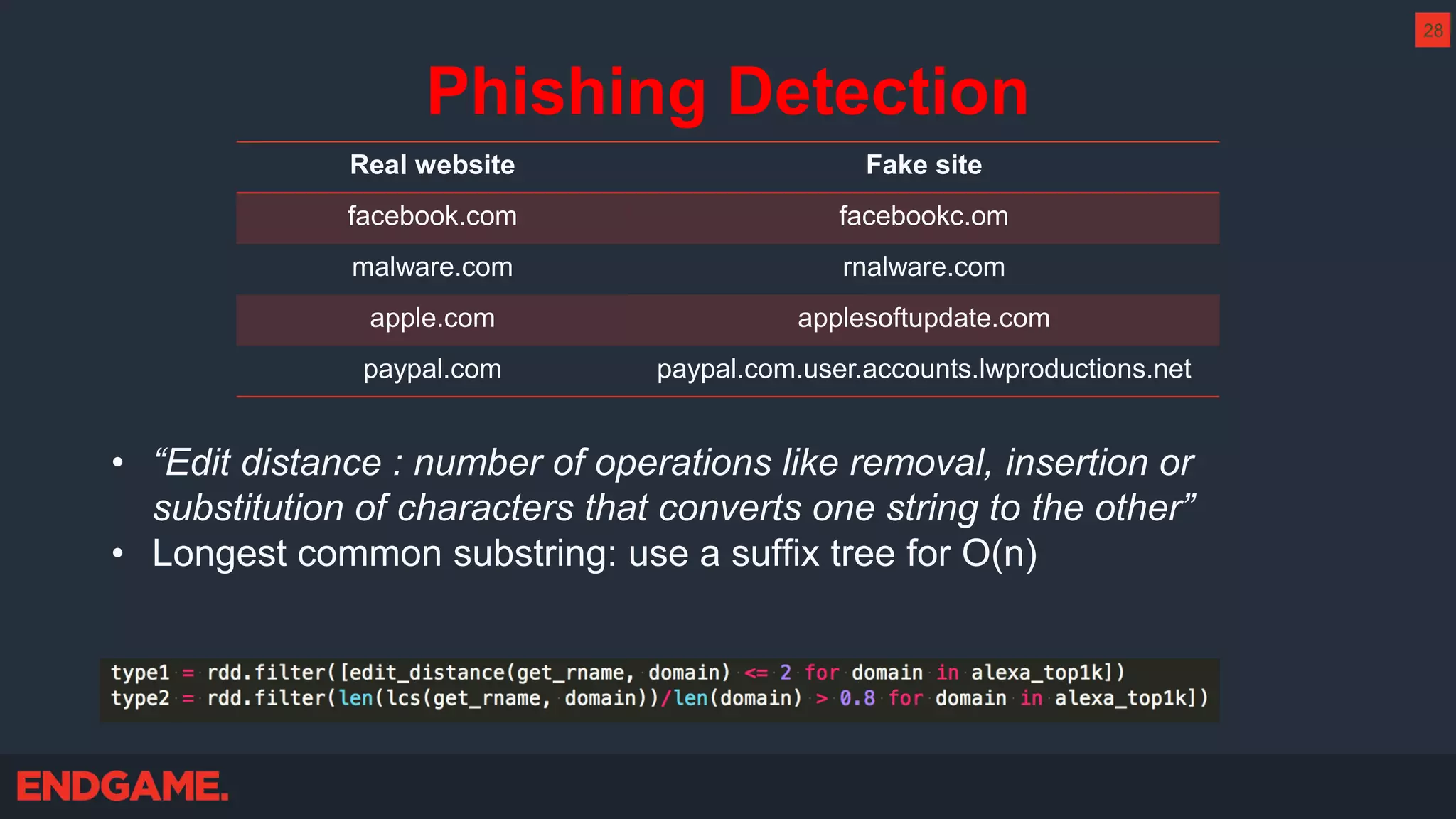
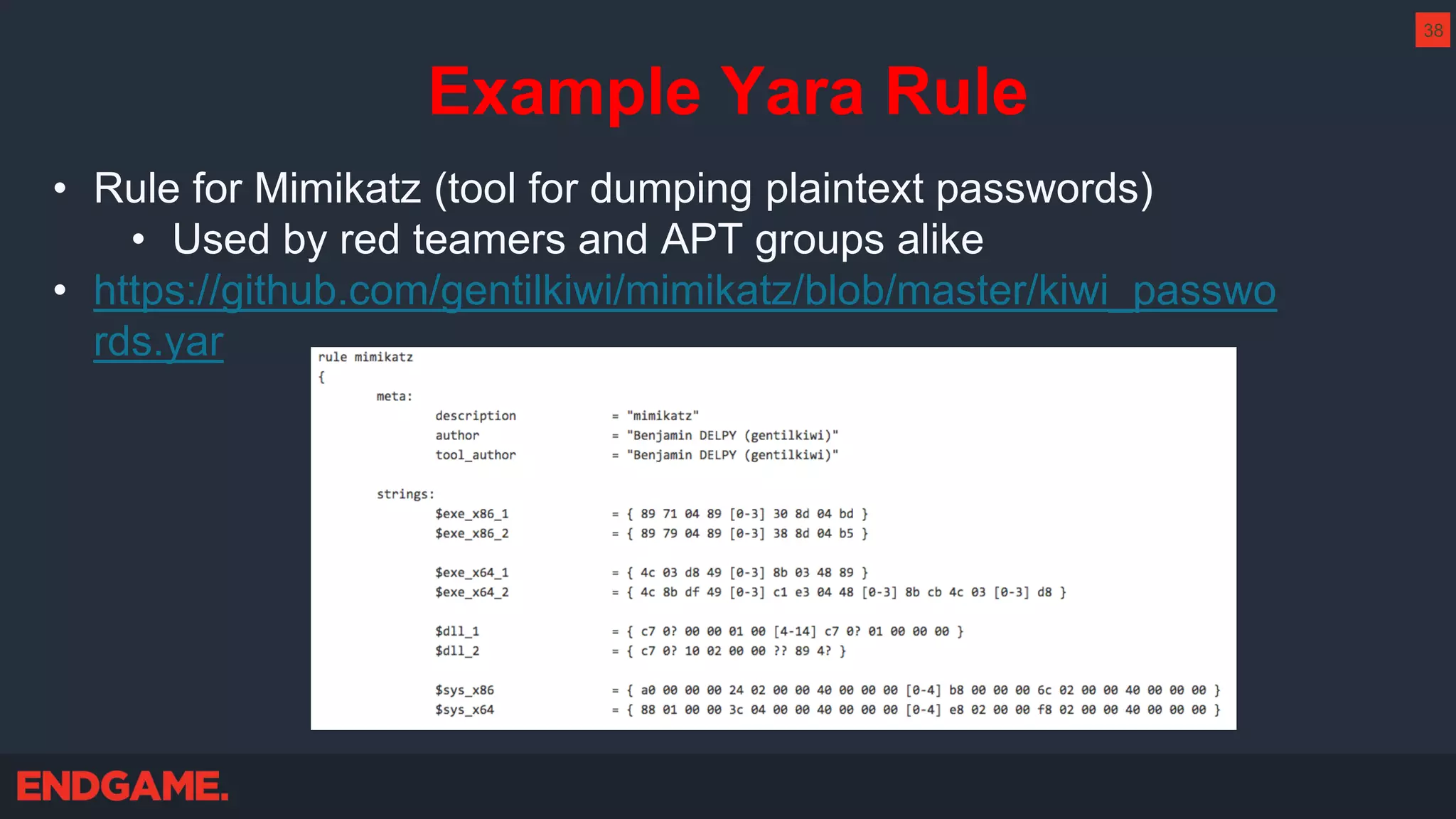
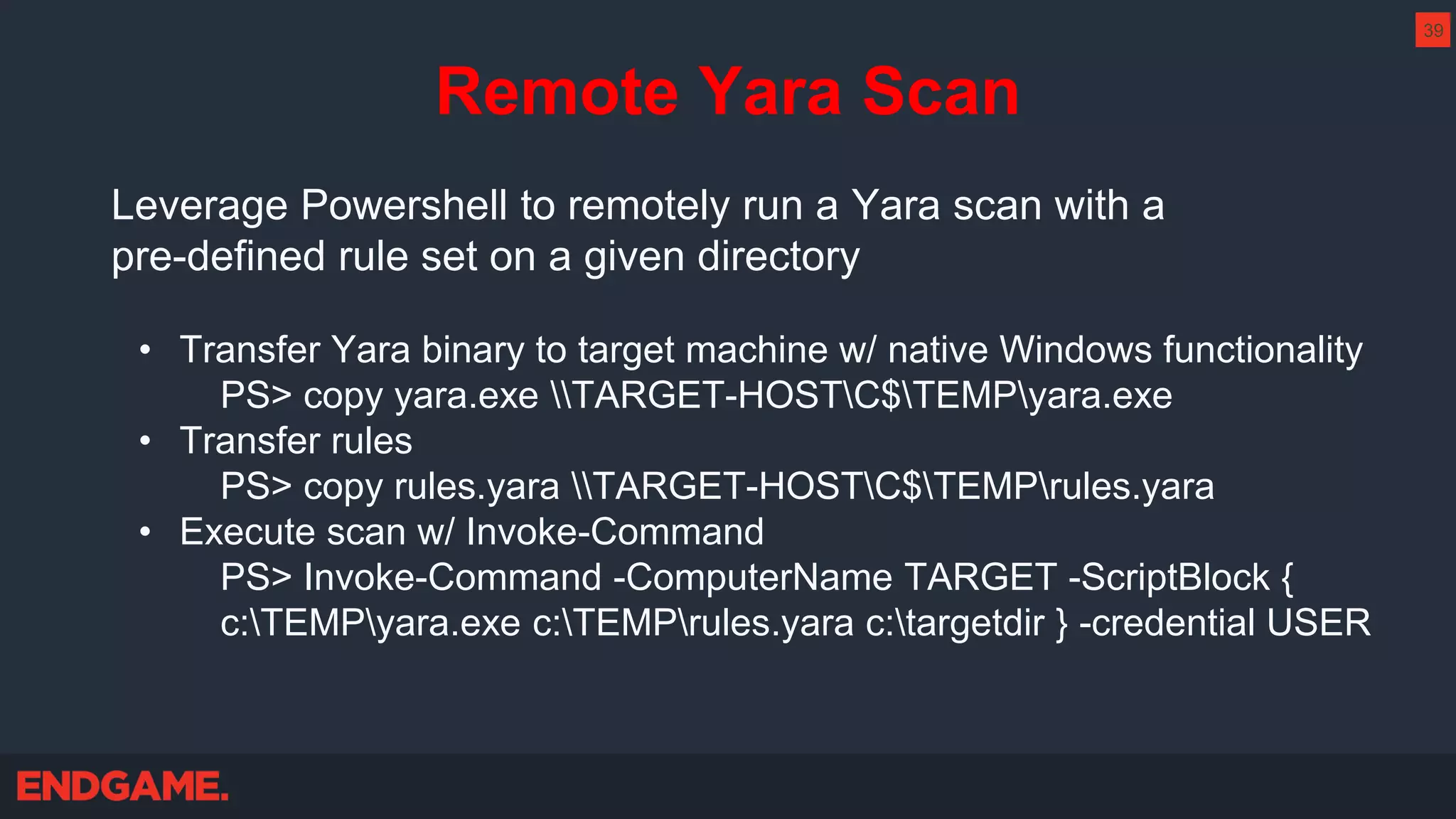
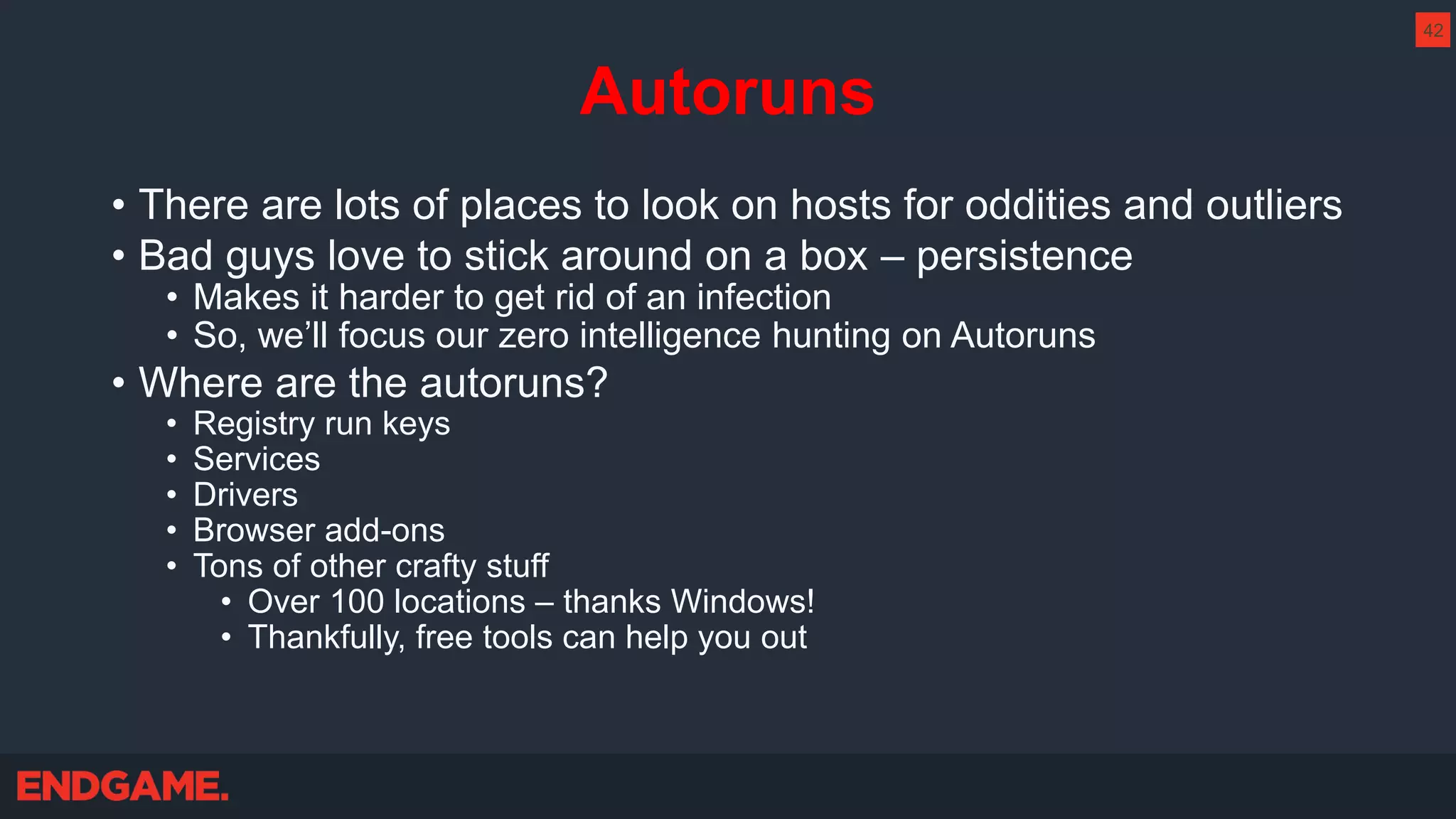
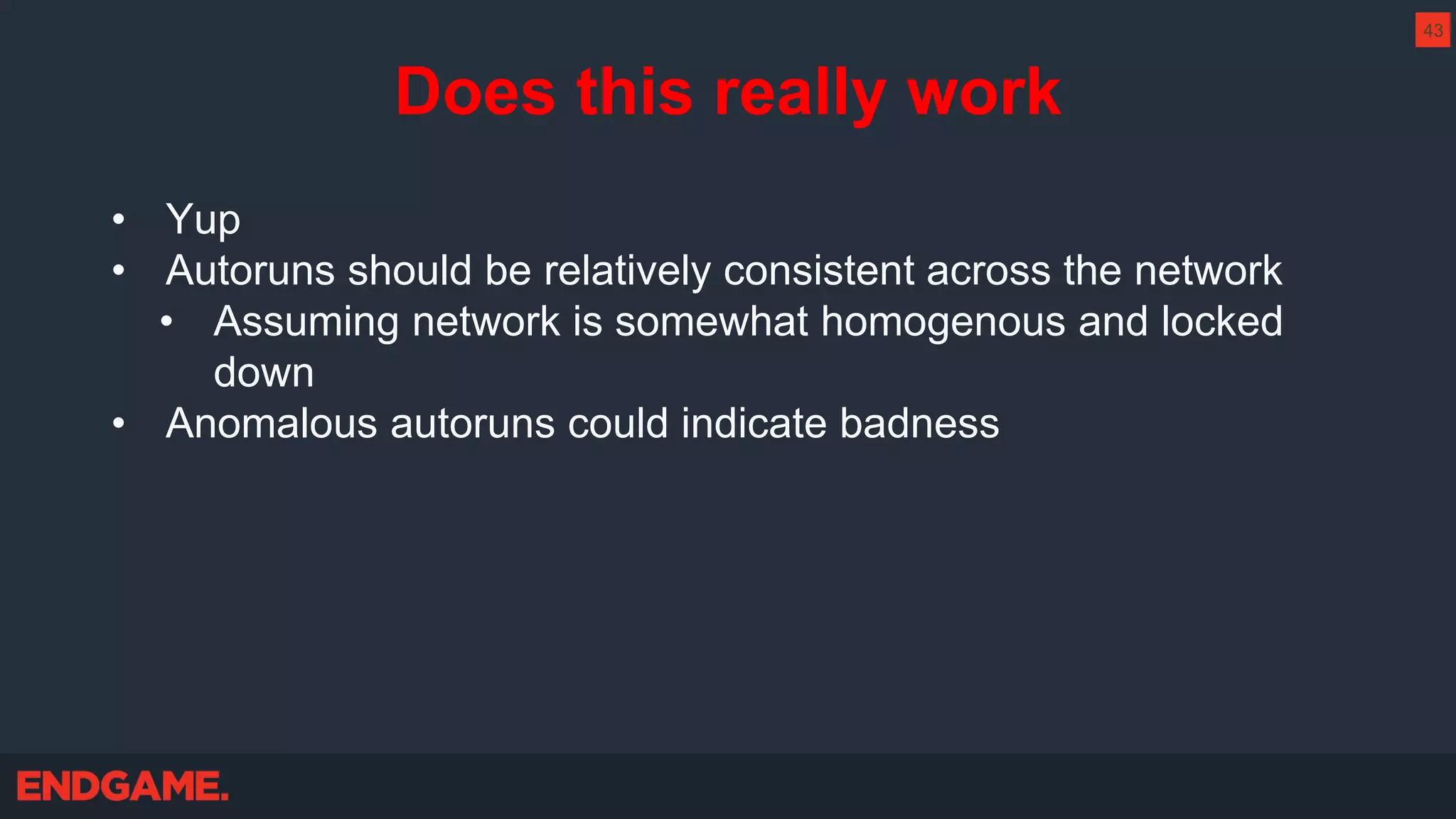
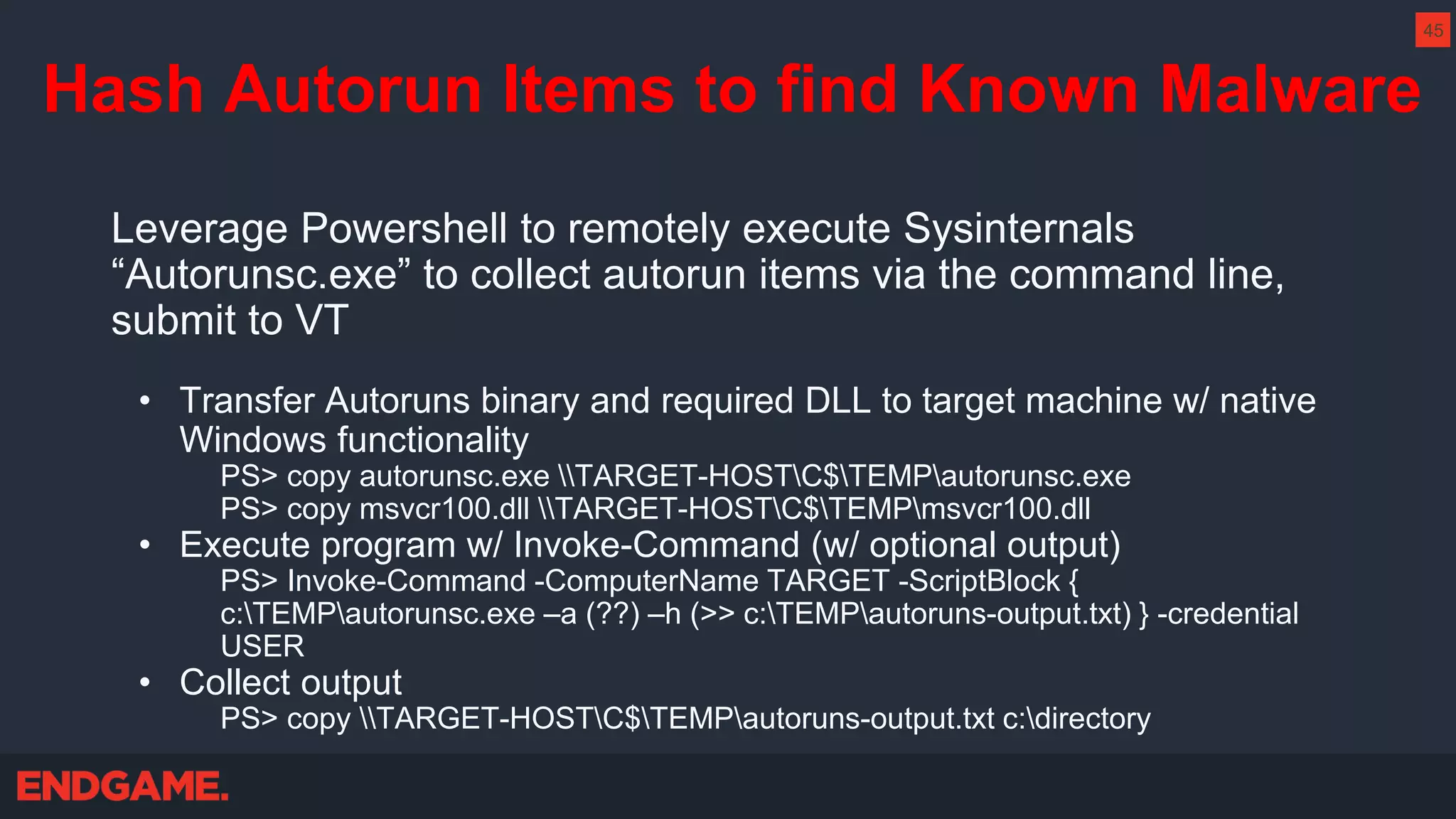
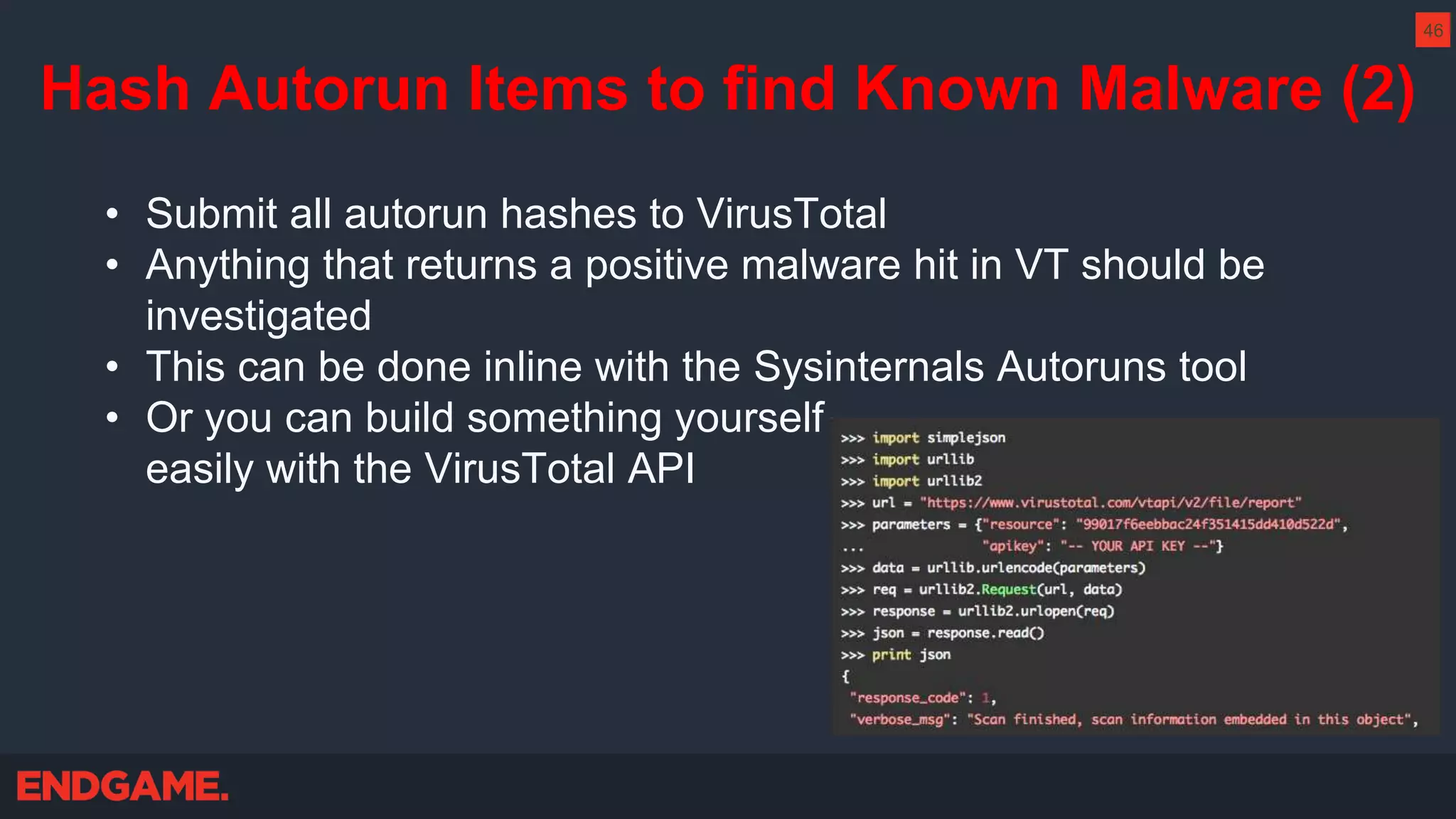
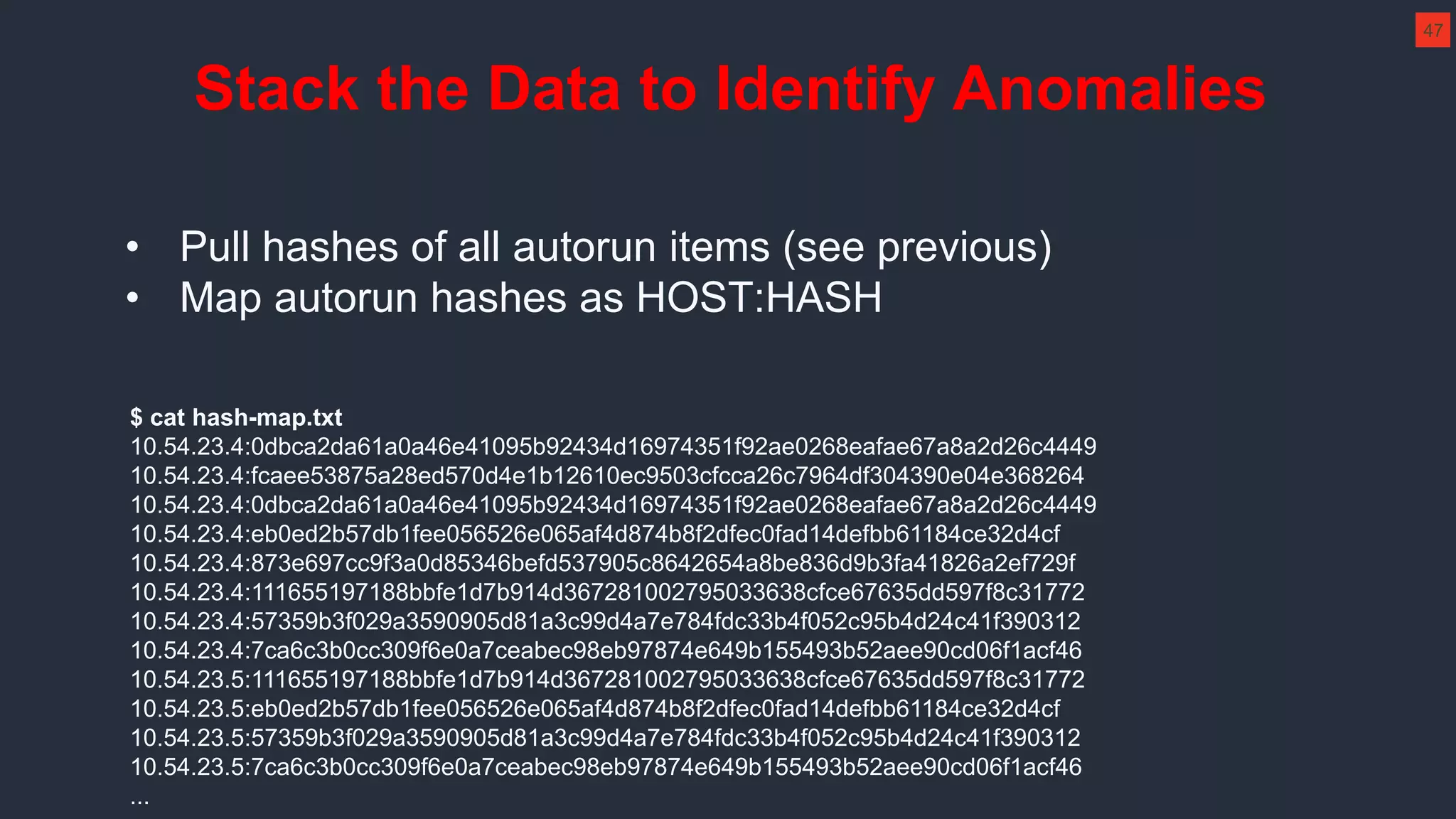
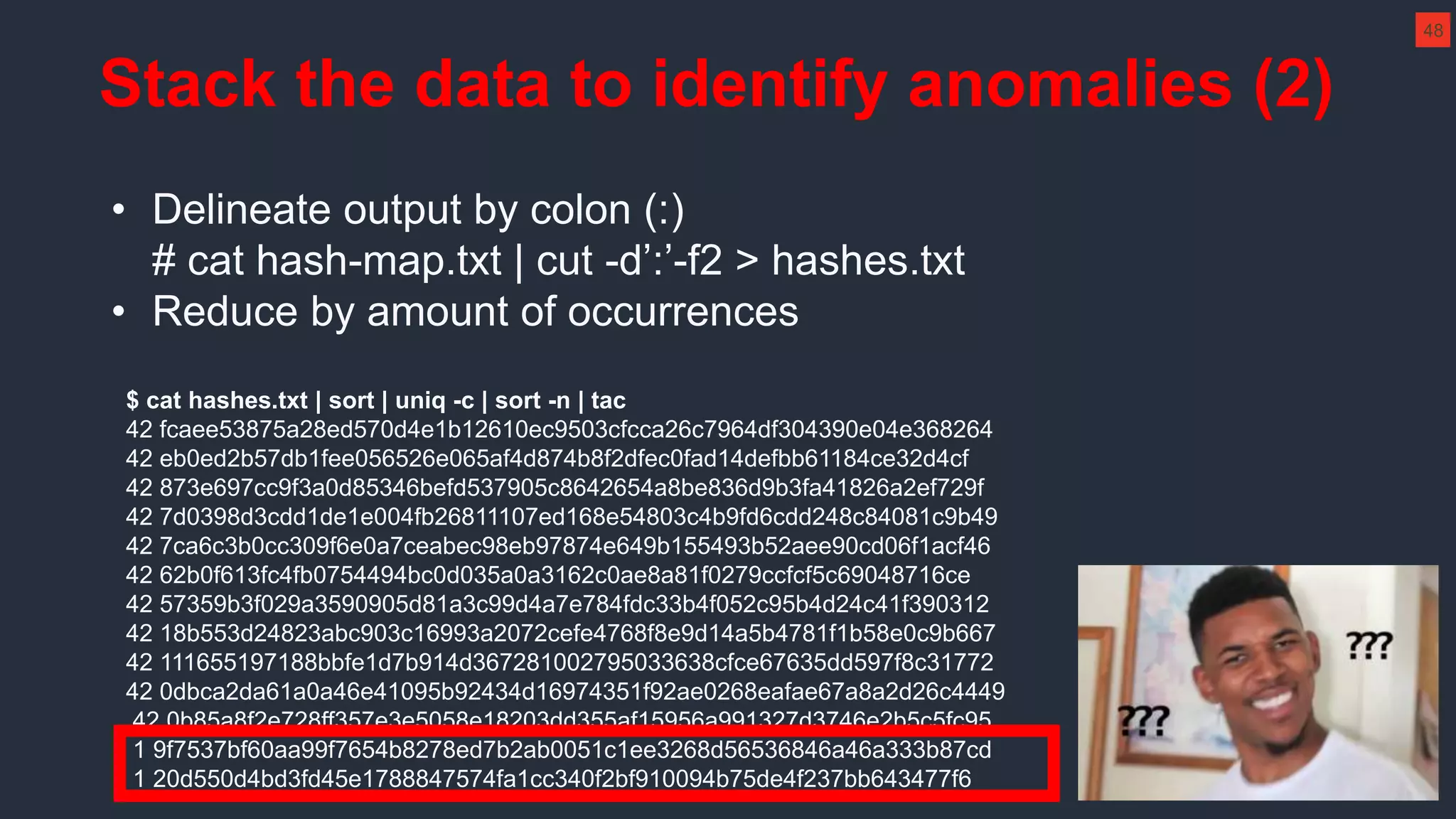
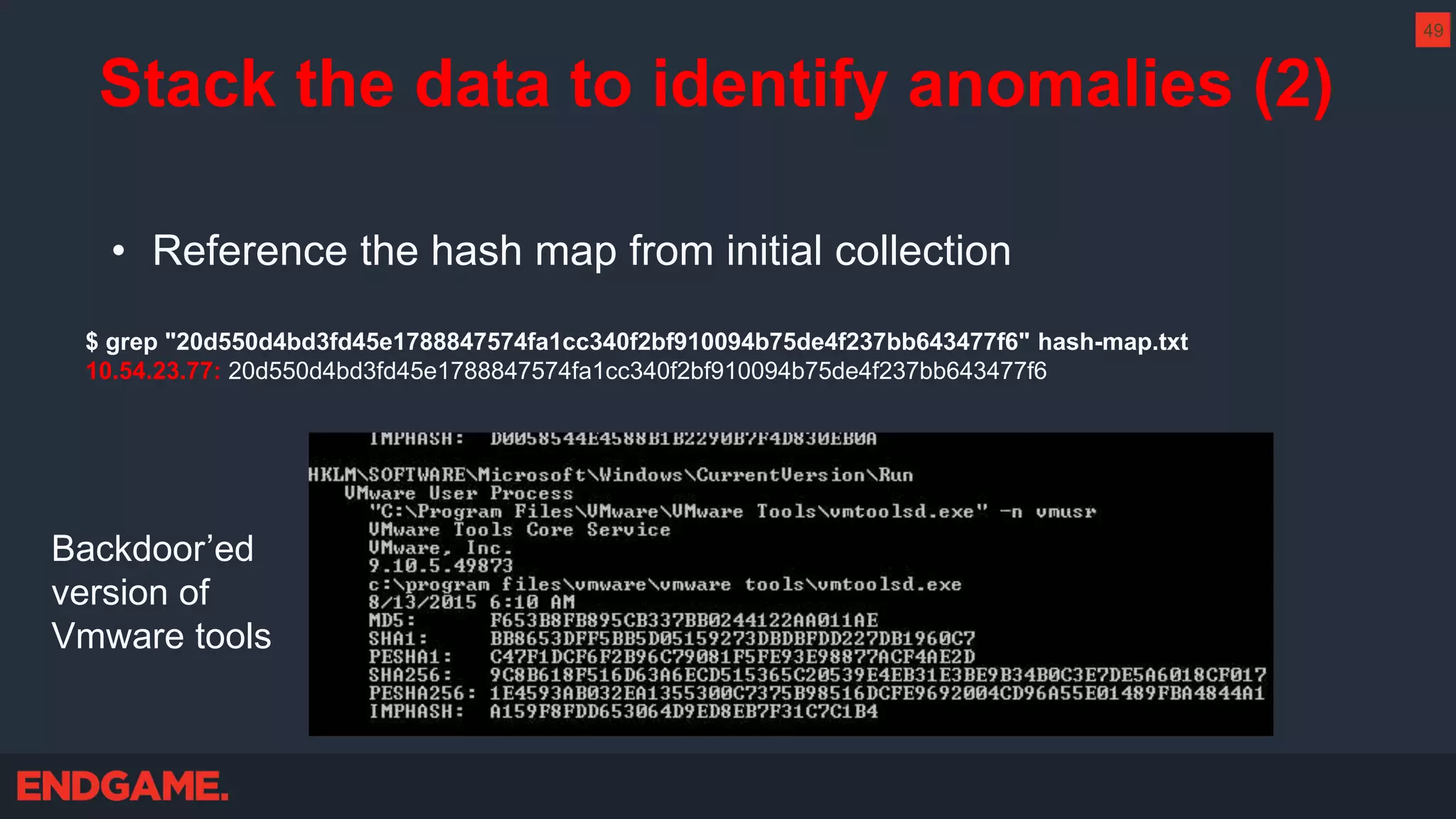
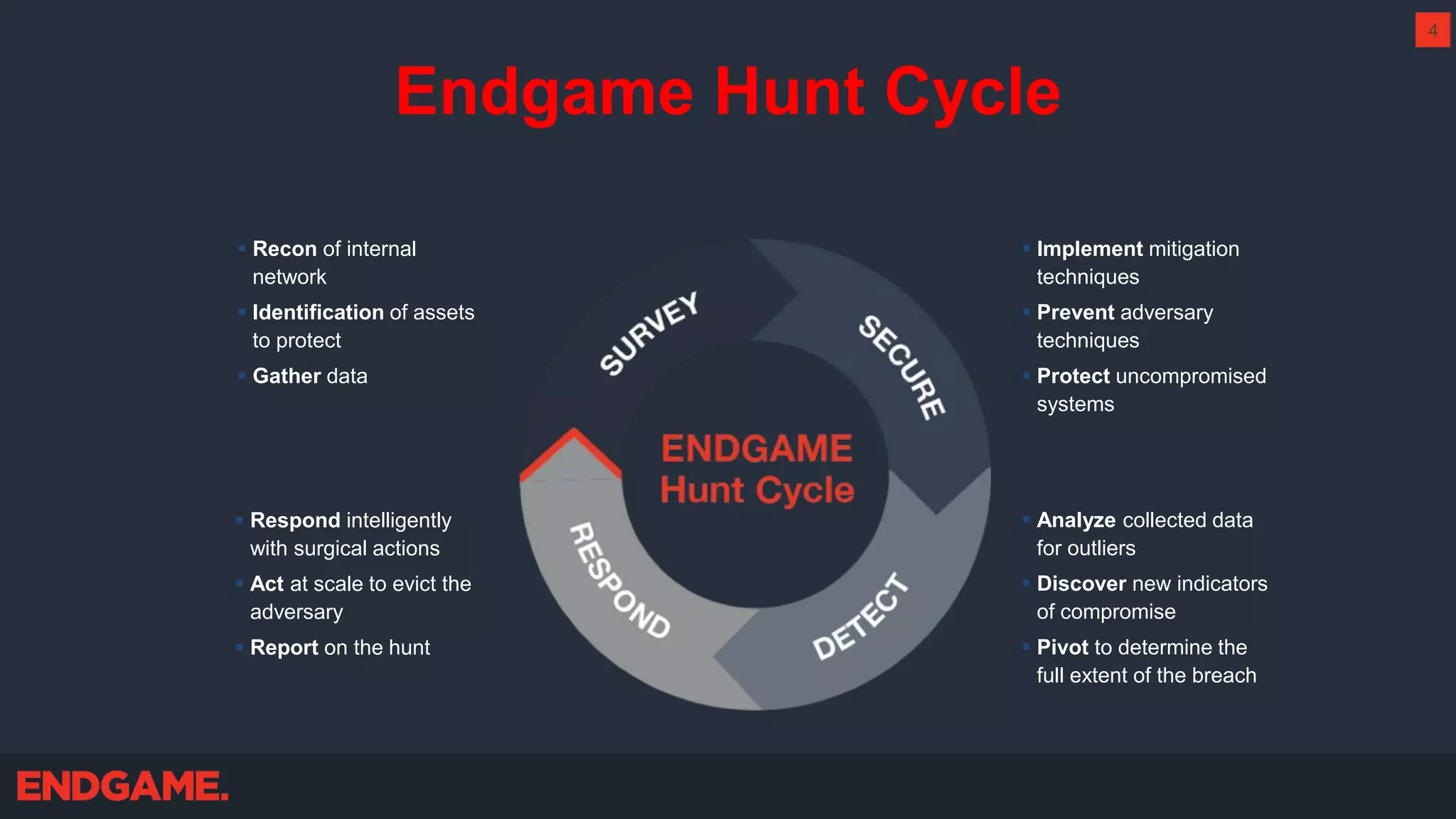
The document outlines strategies for effective threat hunting on a budget, targeting techniques and methodologies that leverage free tools and open-source intelligence. It emphasizes the importance of understanding one's network environment to identify anomalies, such as unusual processes or network connections, and provides practical guidance for investigating these outliers. Key methods discussed include utilizing passive DNS, detecting domain generation algorithms, and analyzing autorun entries to uncover potential malware presence.