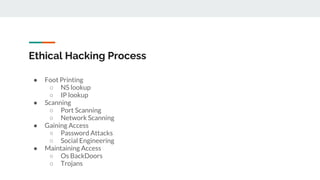
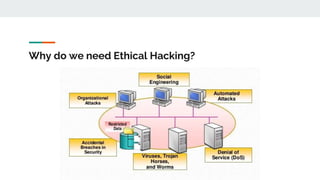
The document discusses ethical hacking, describing it as legal penetration testing aimed at identifying and fixing vulnerabilities in computer systems. It outlines the role of ethical hackers, the processes they use, necessary skills, and the advantages and disadvantages associated with the practice. Additionally, it highlights the increasing demand for ethical hackers due to the growing technology landscape and rising cyber threats.