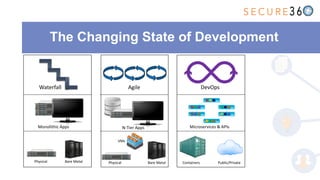
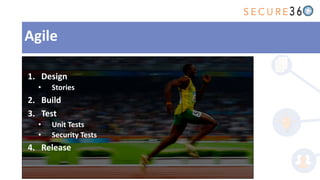
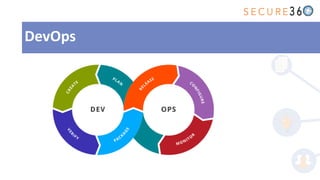
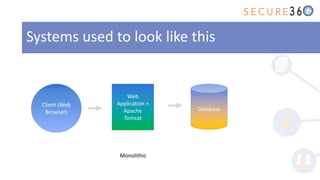
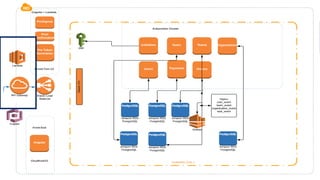
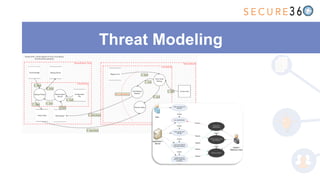
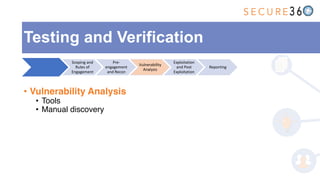
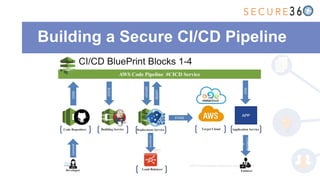
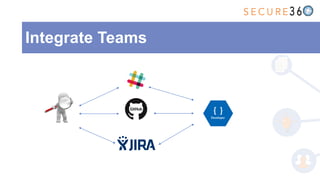
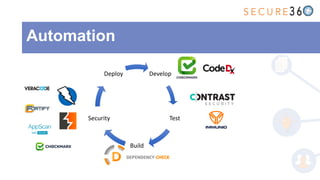
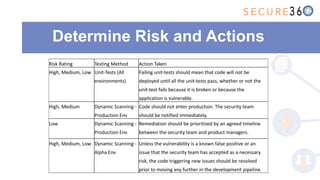
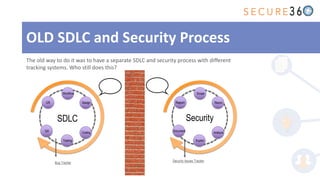
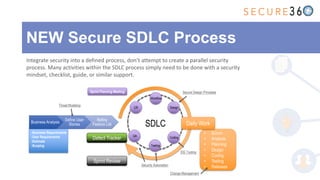
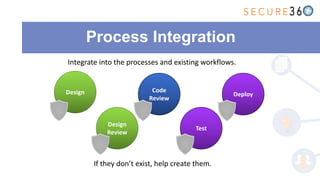
The document discusses the integration of application security (AppSec) within Agile and DevOps methodologies, emphasizing the need for executive support, governance, and collaboration among teams. It outlines the transition from traditional waterfall development to Agile practices and highlights the importance of security tools and processes throughout the software development lifecycle. Key points include the necessity of threat modeling, secure design principles, and continuous security integration into development and deployment processes.

![Who is this guy?
class Speaker {
let name = “David Lindner”
let title = “Chief Strategy Officer”
let company = ”nVisium"
let twitter = “@golfhackerdave”
var hobbies = [“Dadding”, ”Golf”,
“IoT/Mobile”, “Fishing”]
}](https://image.slidesharecdn.com/appsecagile-180516193527/85/AppSec-in-an-Agile-World-2-320.jpg)