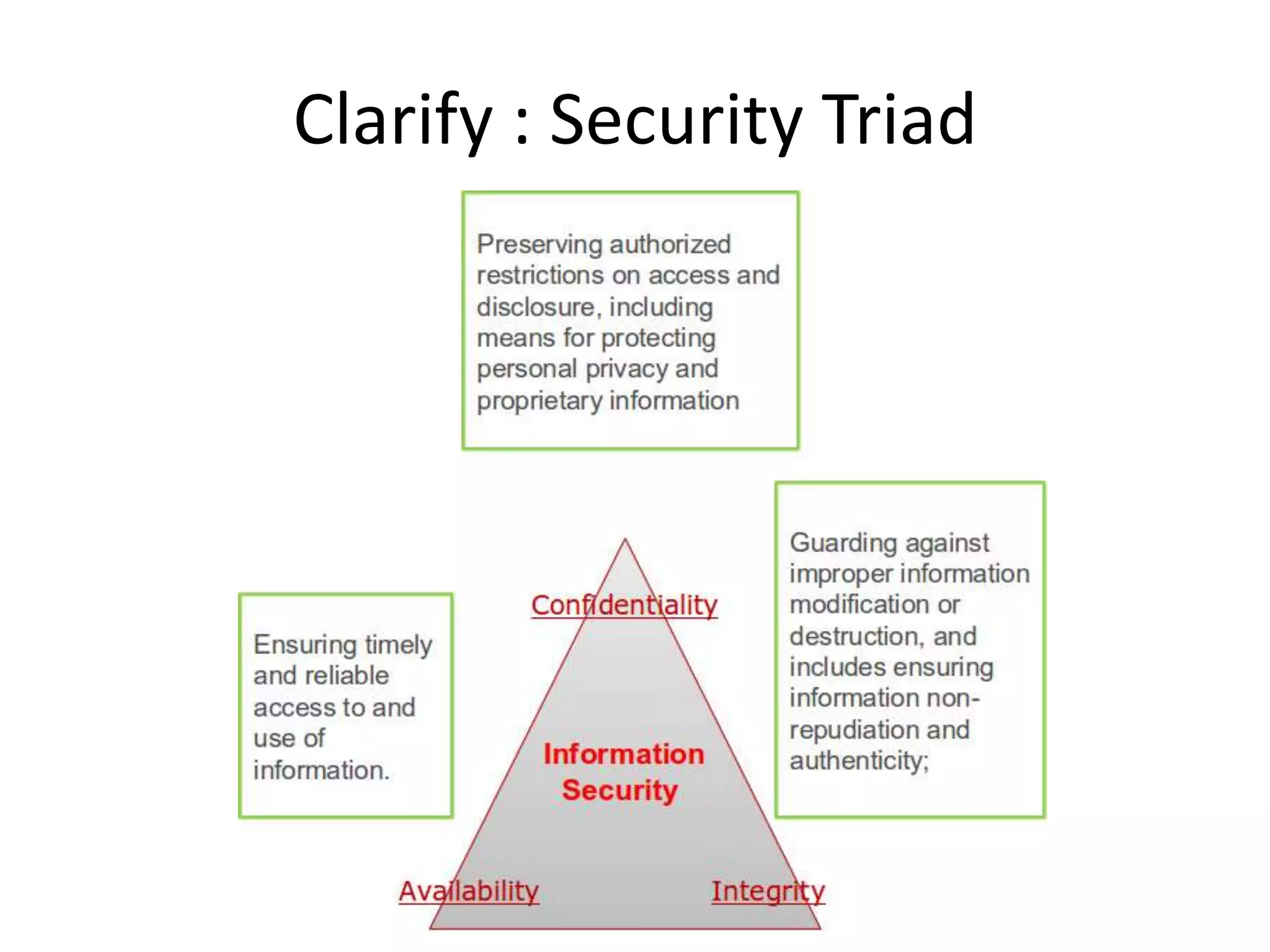
The document discusses the field of information security, outlining its significance due to increasing threats and regulatory compliance. It covers various job roles, essential certifications, skills required for success, and tips for building a career in this domain. Key aspects include understanding core security concepts, gaining practical experience, and maintaining continuous learning and networking.