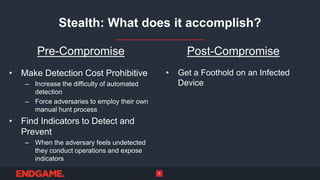
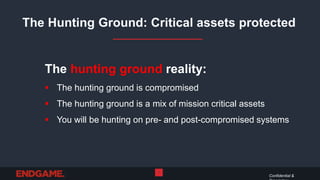
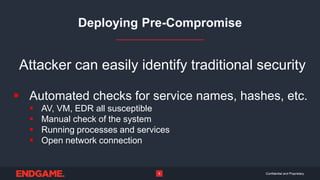
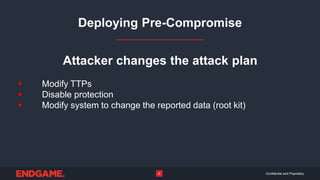
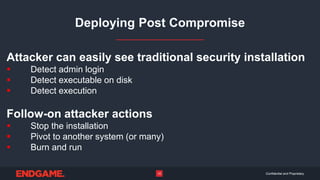
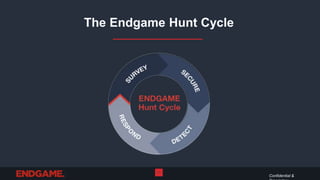
The document discusses the importance of stealth in cybersecurity, detailing strategies to avoid detection by adversaries. It highlights the hunting ground concept, emphasizing that systems can be both pre- and post-compromised, and offers insights into modifying attacks to evade traditional security measures. Overall, the key message is to maintain stealth to protect critical assets and avoid adversarial detection.