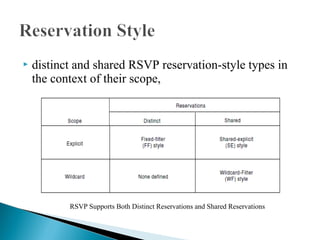
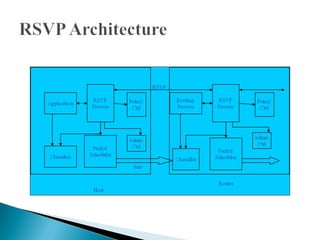
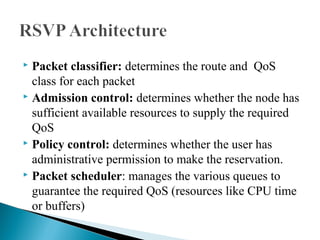
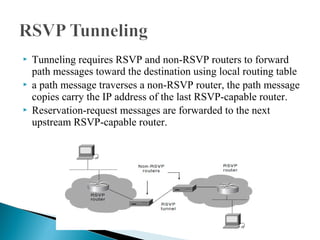
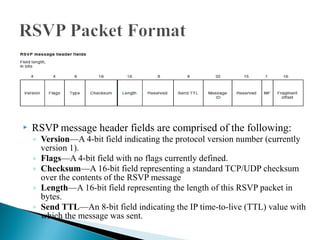
RSVP is a network control protocol that allows applications to request different qualities of service for their data flows. It works with routing protocols to implement reservations across a network without requiring migration to a new routing protocol. RSVP supports both unicast and multicast sessions, with three service levels - best effort, rate sensitive, and delay sensitive. It uses soft state to dynamically maintain reservations in response to changes in network conditions or routing.