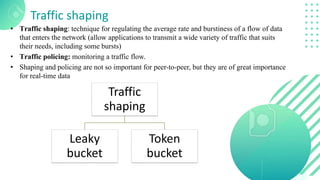
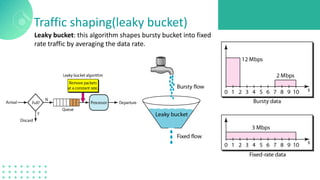
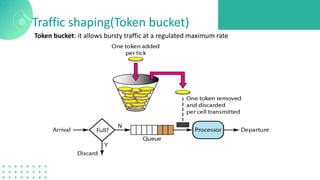
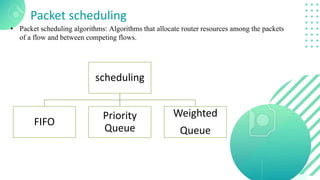
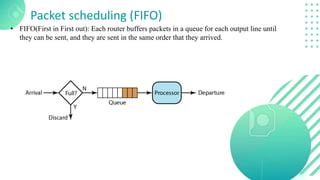
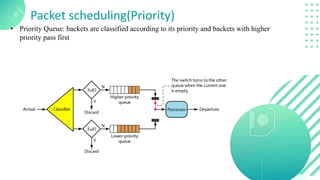
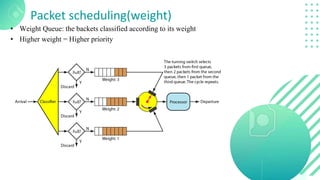
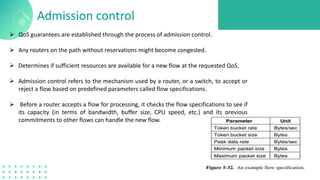
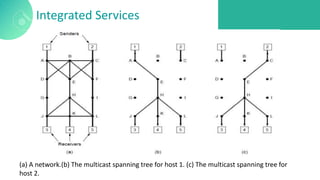
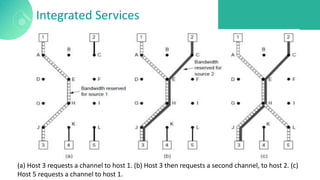
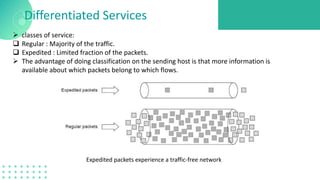
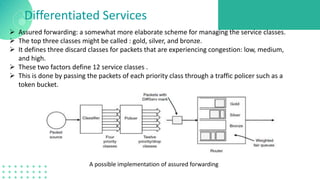
The document discusses quality of service (QoS) in computer networks, focusing on mechanisms to meet application requirements, including traffic shaping, packet scheduling, and admission control. It outlines different QoS models such as integrated services and differentiated services, detailing aspects like bandwidth, delay, loss, and jitter. Key techniques such as leaky bucket and token bucket for traffic shaping, along with various packet scheduling algorithms, are also highlighted to manage network performance effectively.