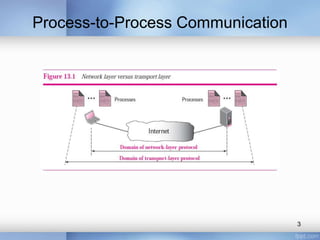
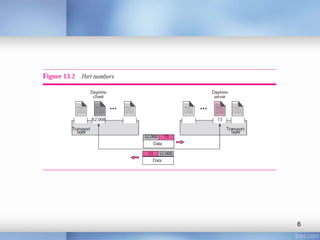
This document discusses various aspects of transport layer protocols in computer networks, including:
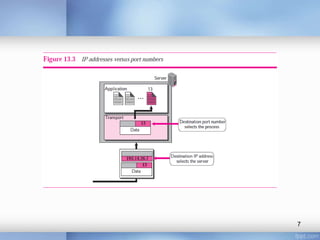
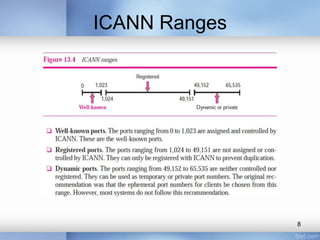
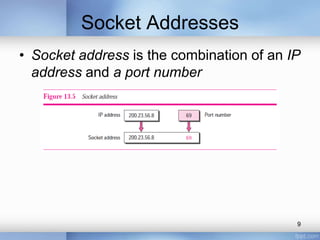
- Addressing processes using port numbers between 0-65,535
- The client-server model where clients use ephemeral ports over 1023 and servers use well-known ports
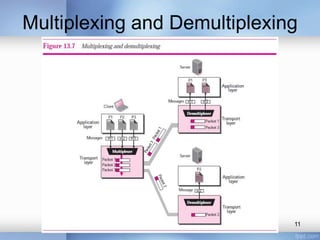
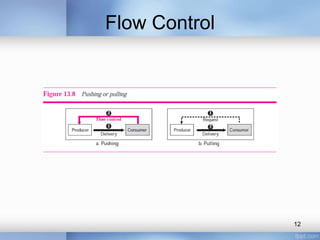
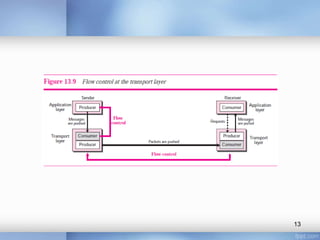
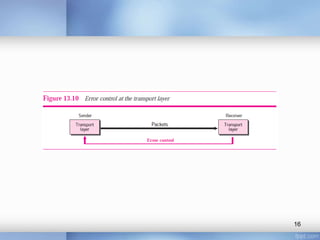
- Transport layer services like multiplexing, demultiplexing, flow control using buffers, error control using sequence numbers and acknowledgments, and congestion control
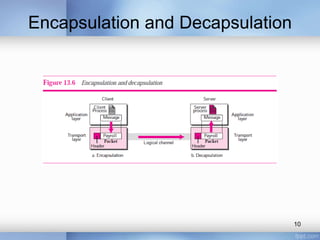
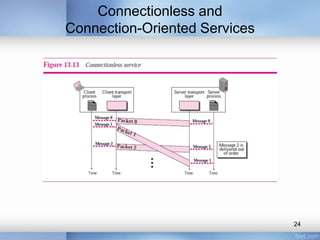
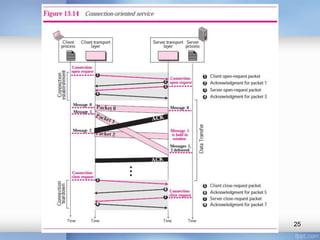
- Connection-oriented protocols like TCP provide reliable data delivery compared to connectionless protocols like UDP.
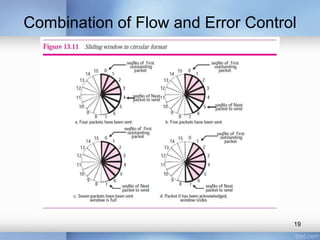
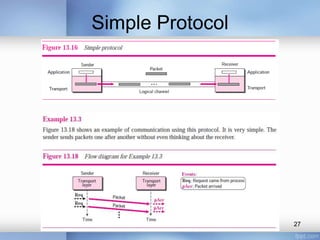
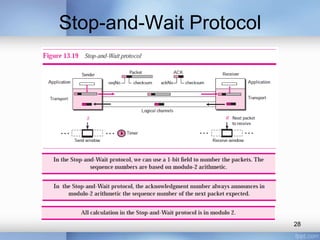
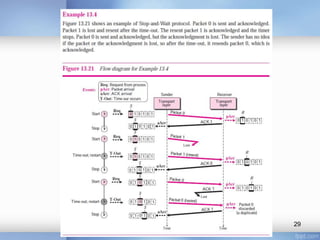
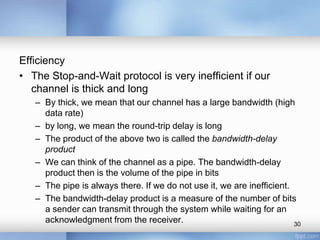
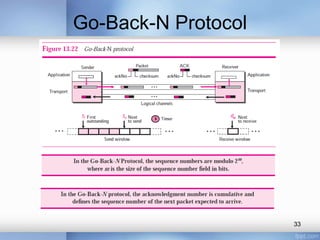
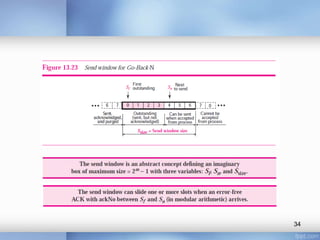
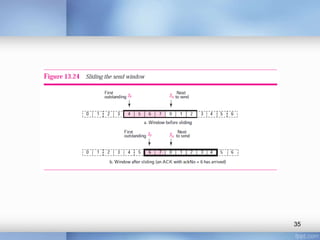
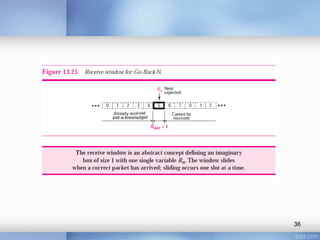
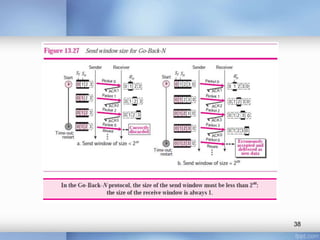
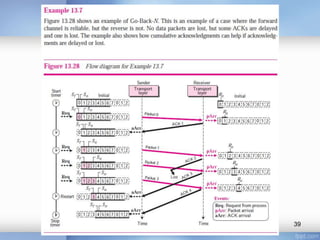
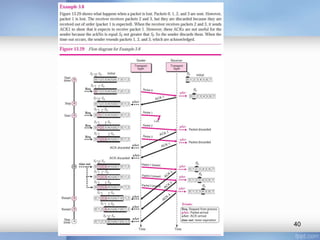
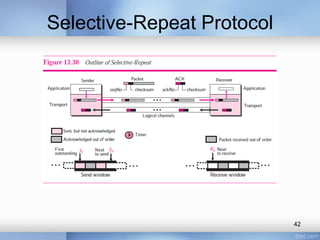
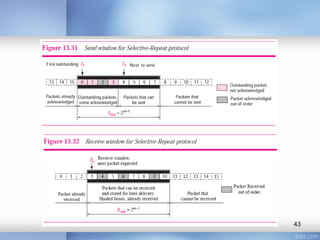
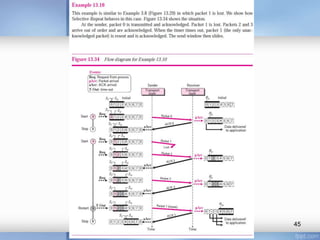
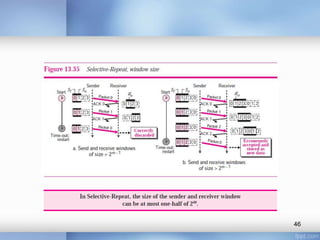
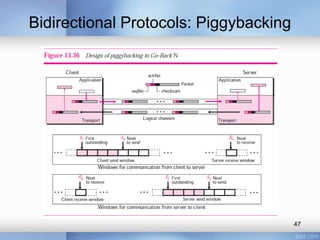
- Stop-and-wait, go-back-N, and selective-repeat protocols aim to increase efficiency over simple retransmission by allowing multiple outstanding packets.