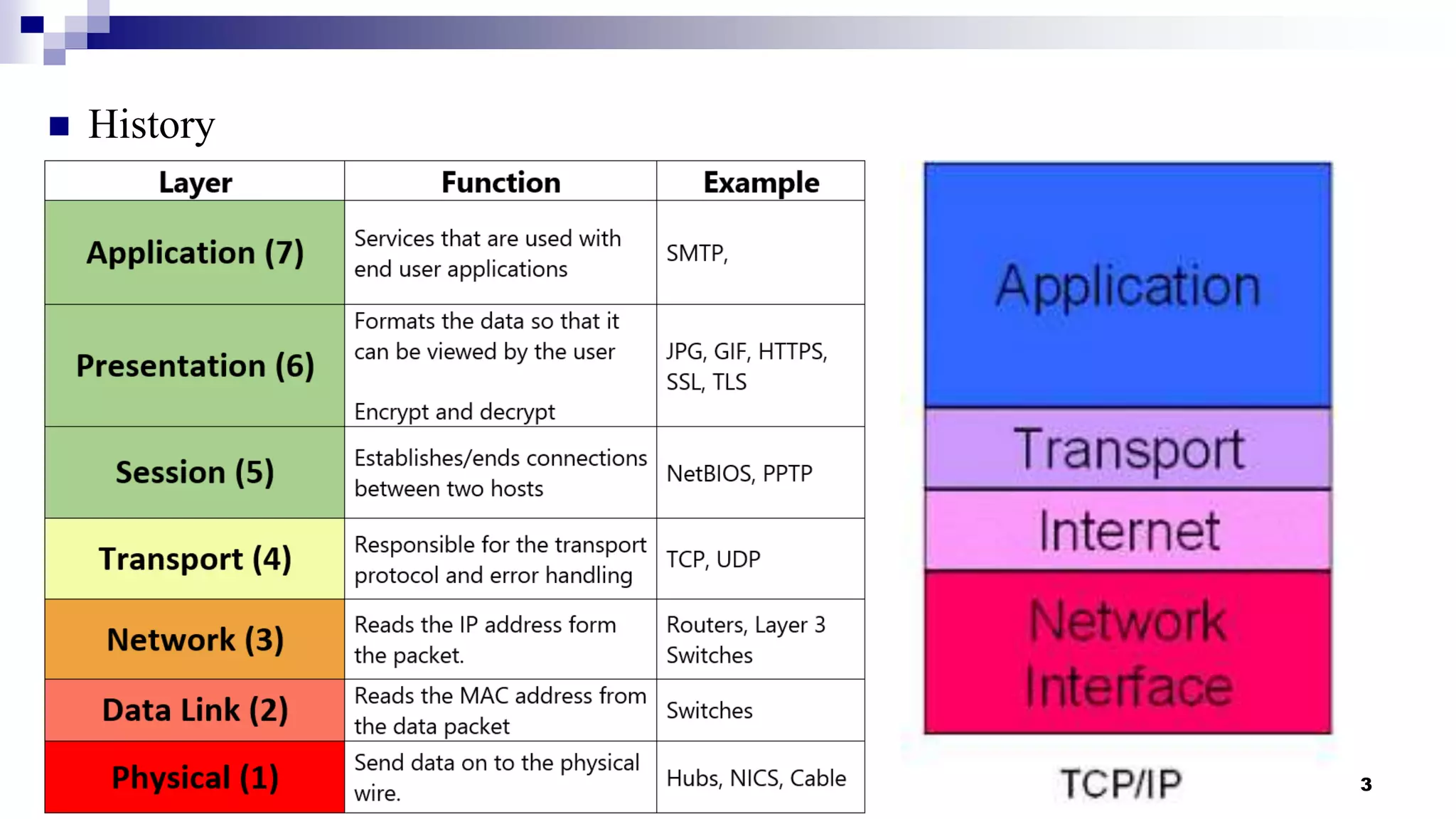
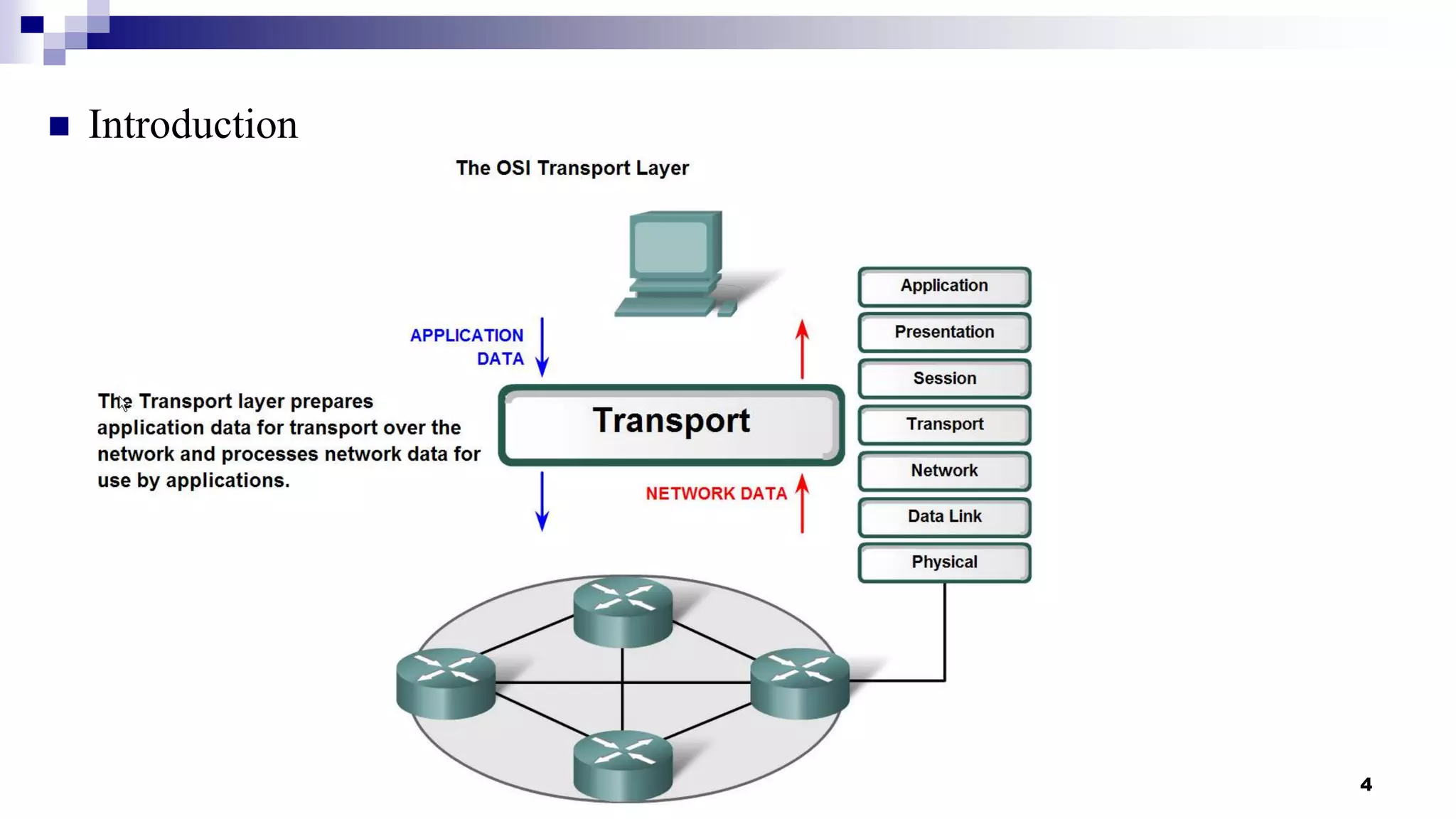
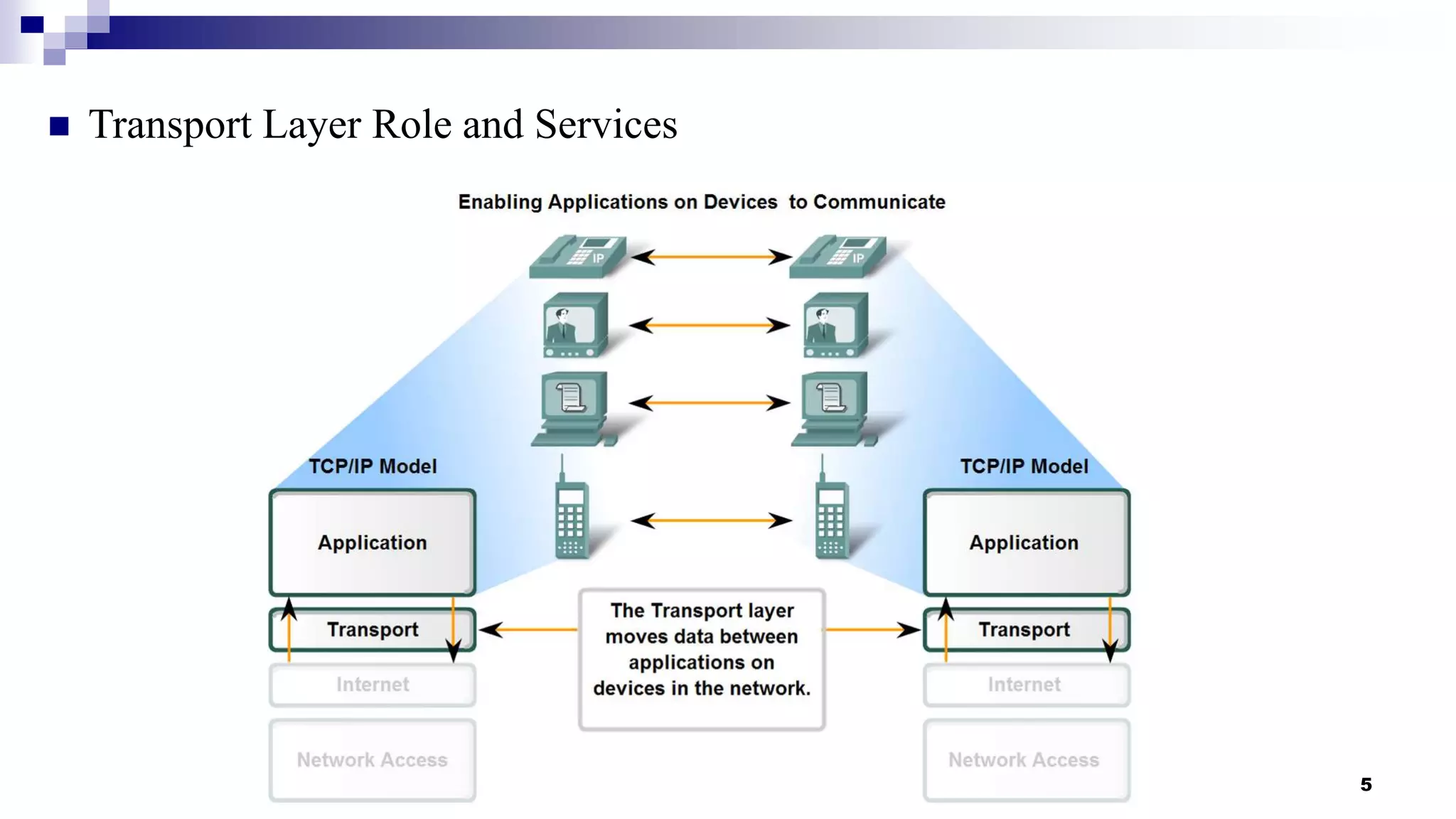
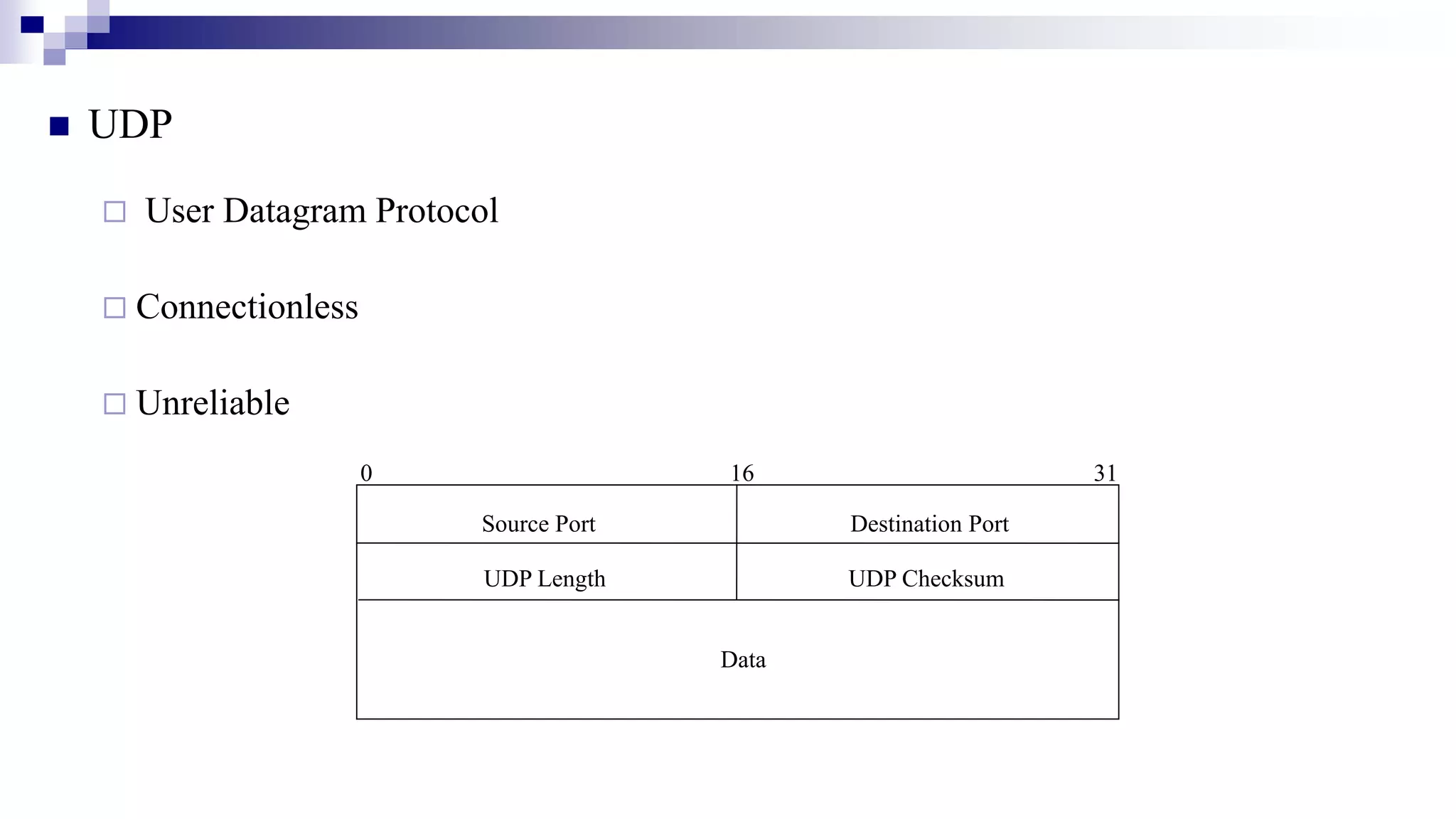
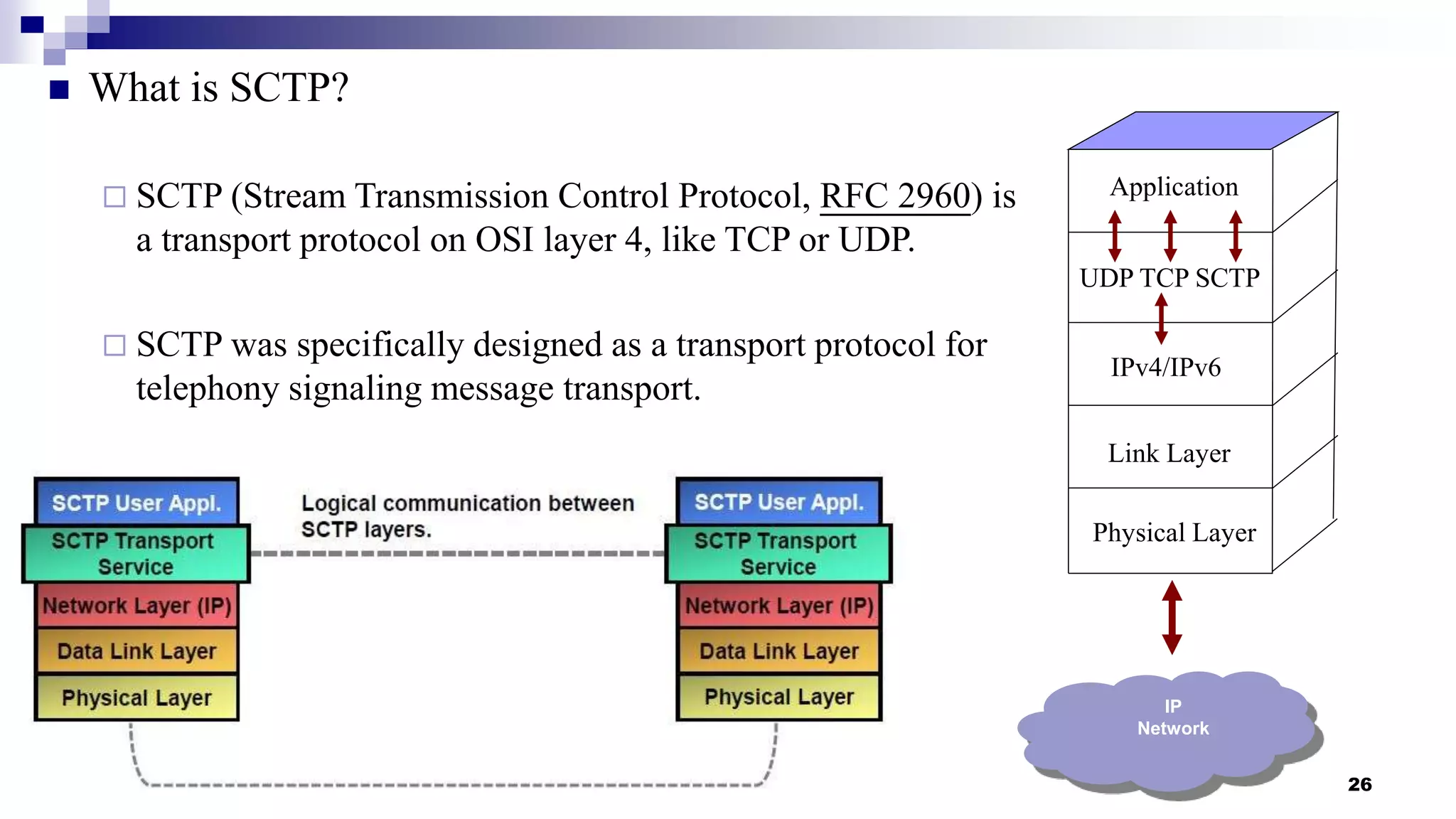
This document provides an overview of transport layer protocols TCP, UDP, and SCTP. It discusses the history and evolution of TCP, including key developments like congestion control algorithms. UDP is described as a connectionless and unreliable protocol. SCTP is introduced as a protocol developed to transport telephony signaling over IP networks. It addresses limitations of TCP like head-of-line blocking and provides features like multi-homing and message orientation. The document defines SCTP terminology and describes its chunks, states, congestion control approach, and similarities to TCP. In summary, it serves as a high-level introduction to transport protocols with a focus on motivations and capabilities of SCTP.