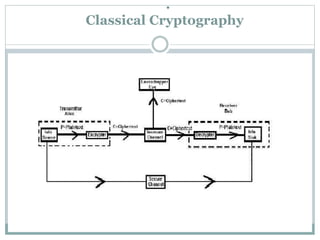
This document discusses quantum cryptography and its advantages over classical cryptography. It introduces the key distribution problem in classical cryptography. Quantum cryptography uses principles of quantum mechanics like quantum bits that cannot be copied and photon polarization to securely distribute keys. The document describes the BB84 protocol for quantum key distribution where Alice and Bob use different polarization bases to generate a random key and detect eavesdropping. While promising, challenges remain in scaling the technology to longer distances and developing affordable devices.