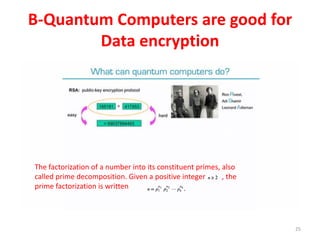
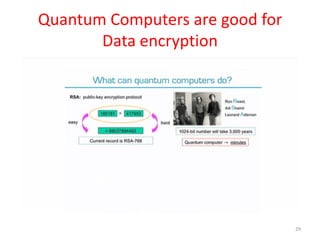
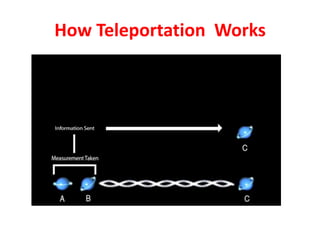
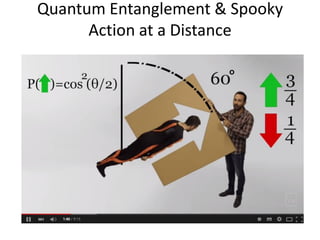
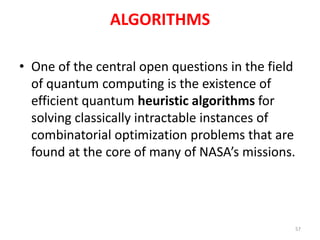
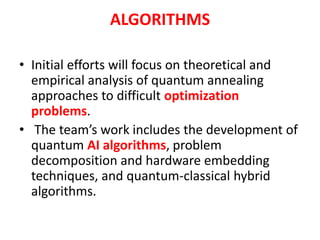
The document discusses quantum algorithms, highlighting key concepts such as Shor's algorithm for factoring and Grover's algorithm for searching. It emphasizes the potential of quantum computers to outperform classical computers in certain tasks and their implications for cryptography, particularly in breaking public-key systems like RSA. Additionally, it explores properties of quantum mechanics, including entanglement and quantum teleportation, and the development of algorithms for tackling complex problems in various fields.