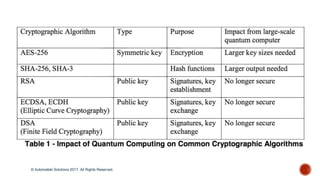
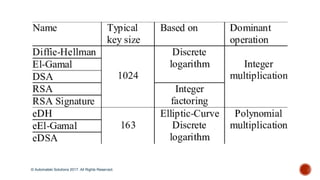
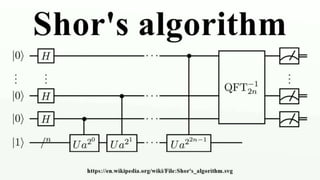
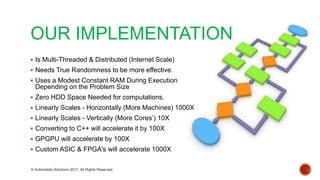
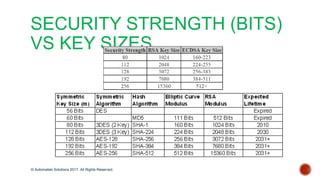
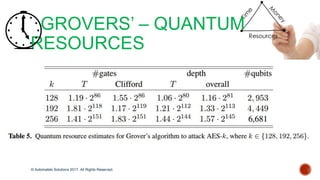
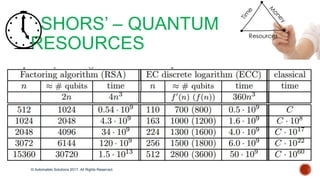
The document discusses the breakthrough of automatski solutions in quantum computing, specifically their ability to crack RSA-2048 using Shor's algorithm, which can theoretically break all modern cryptography. It highlights over 25 years of research, problem-solving achievements, and provides technical insights into quantum computing's capabilities. It emphasizes the urgency for industries to be aware of the potential implications of quantum computing on security and encryption.




















![PROGRESS SO FAR
(CLASSICAL METHODS)
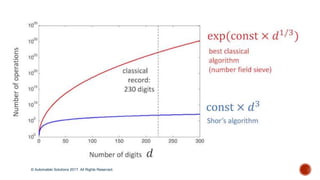
1. RSA-768 has 232 decimal digits (768 bits), and was factored on December 12, 2009
over the span of two years, by Thorsten Kleinjung, Kazumaro Aoki, Jens Franke, Arjen
K. Lenstra, Emmanuel Thomé, Pierrick Gaudry, Alexander Kruppa, Peter Montgomery,
Joppe W. Bos, Dag Arne Osvik, Herman te Riele, Andrey Timofeev, and Paul
Zimmermann.
The CPU time spent on finding these factors by a collection of parallel computers amounted approximately
to the equivalent of almost 2000 years of computing on a single-core 2.2 GHz AMD Opteron-based
computer.
2. RSA-230 has 230 decimal digits (762 bits), and was factored by Samuel S. Gross at
Noblis, Inc. on August 15, 2018.
In 2017, an analysis by a theory group led by Nike Dattani and experimental group led by Xinhua Peng and
Jiangfeng Du[35] determined that RSA-230 could be factored by a D-Wave quantum annealer if it had 687.5
MQB (mega-qubytes) or 5.5 billion qubits, much more than the 2048 qubits currently available on the largest
quantum annealer built to date. However, in the same paper they note that RSA-230 could simply be
factored by minimizing a 5893-variable quartic polynomial that takes in binary (0 or 1) input. Therefore a
quantum annealer with 5893 qubits that can be coupled together arbitrarily with each qubit coupled
simultaneously to at most three other qubits, would be able to factor RSA-230. The amount of time this
annealing would take is still an open question.
© Automatski Solutions 2017. All Rights Reserved.](https://image.slidesharecdn.com/automatski-crackingrsa-2048usingshorsalgorithmonaquantumcomputer-181225060629/85/Automatski-RSA-2048-Cryptography-Cracked-using-Shor-s-Algorithm-on-a-Quantum-Computer-29-320.jpg)



























![REFERENCES
G. H. Hardy and E. M. Wright (1979), An Introduction to the Theory of Numbers, Fifth ed., Oxford University Press, New York.
J. Hartmanis and J. Simon (1974), On the power of multiplication in random access machines, in Proceedings of the 15th Annual Symposium on
Switching and Automata Theory, IEEE Computer Society, Long Beach, CA, pp. 13–23.
A. Karatsuba and Yu. Ofman (1962), Multiplication of multidigit numbers on automata, Dokl. Akad. Nauk SSSR, 145, pp. 293–294 (in Russian). English
translation in Sov. Phys. Dokl., 7 (1963), pp. 595–596.
D. E. Knuth (1981), The Art of Computer Programming, Vol. 2: Seminumerical Algorithms, Second ed., Addison-Wesley.
E. Knill (1995), personal communication.
R. Landauer (1995a), Is quantum mechanics useful ? Philos. Trans. Roy. Soc. London Ser. A, to appear.
(1995b), Is quantum mechanically coherent computation useful ? in Proceedings of the Drexel-4 Symposium on Quantum Nonintegrability—Quantum Classical
Correspondence, D. H. Feng and B-L. Hu, eds., International Press, to appear.
Y. Lecerf (1963), Machines de Turing r´eversibles. R´ecursive insolubilit´e en n ∈ N de l’´equation u = θnu, ou` θ est un isomorphisme de codes,
C. R. Acad. Franc¸aise Sci., 257, pp. 2597–2600.
A. K. Lenstra and H. W. Lenstra, Jr., eds. (1993), The Development of the Number Field Sieve,
Lecture Notes in Mathematics, Vol. 1554, Springer.
A. K. Lenstra, H. W. Lenstra, Jr., M. S. Manasse, and J. M. Pollard (1990), The number field sieve, in Proceedings of the 22nd Annual ACM Symposium on
Theory of Computing, ACM, New York, pp. 564–572. An expanded version appeared in Lenstra and Lenstra [1993], pp. 11–42.
R. Y. Levine and A. T. Sherman (1990), A note on Bennett’s time-space tradeoff for reversible computation, SIAM J. Comput., 19, pp. 673–677.
© Automatski Solutions 2017. All Rights Reserved.](https://image.slidesharecdn.com/automatski-crackingrsa-2048usingshorsalgorithmonaquantumcomputer-181225060629/85/Automatski-RSA-2048-Cryptography-Cracked-using-Shor-s-Algorithm-on-a-Quantum-Computer-62-320.jpg)


