This document summarizes a presentation given by Mike Felch and Beau Bullock of Black Hills Information Security. It discusses four novel techniques for exploiting Microsoft "features":
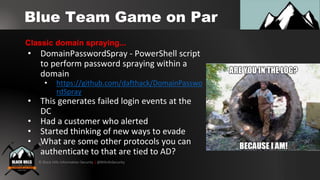
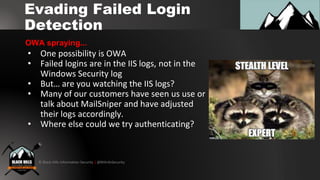
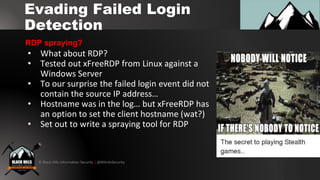
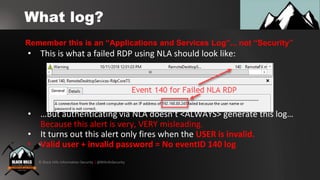
1. Using RDP with NLA enabled to perform password spraying without generating failed login events in the security log.
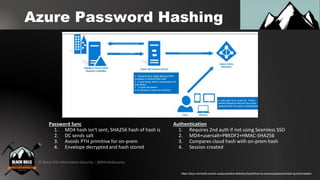
2. Leveraging Azure Active Directory synchronization to query information about users, groups, devices and applications with only a low-privileged set of credentials externally.
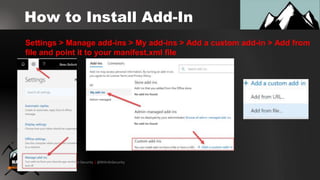
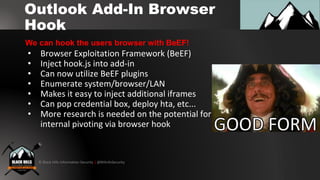
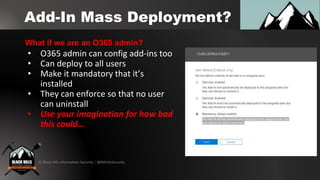
3. Creating malicious Outlook web add-ins that can steal email contents, deploy browser hooks, and run crypto-miners after being installed via compromised user credentials.
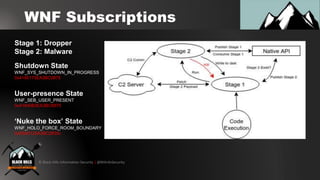
4. Weaponizing the undocumented Windows Notification Facility (WNF) to persist malware payloads