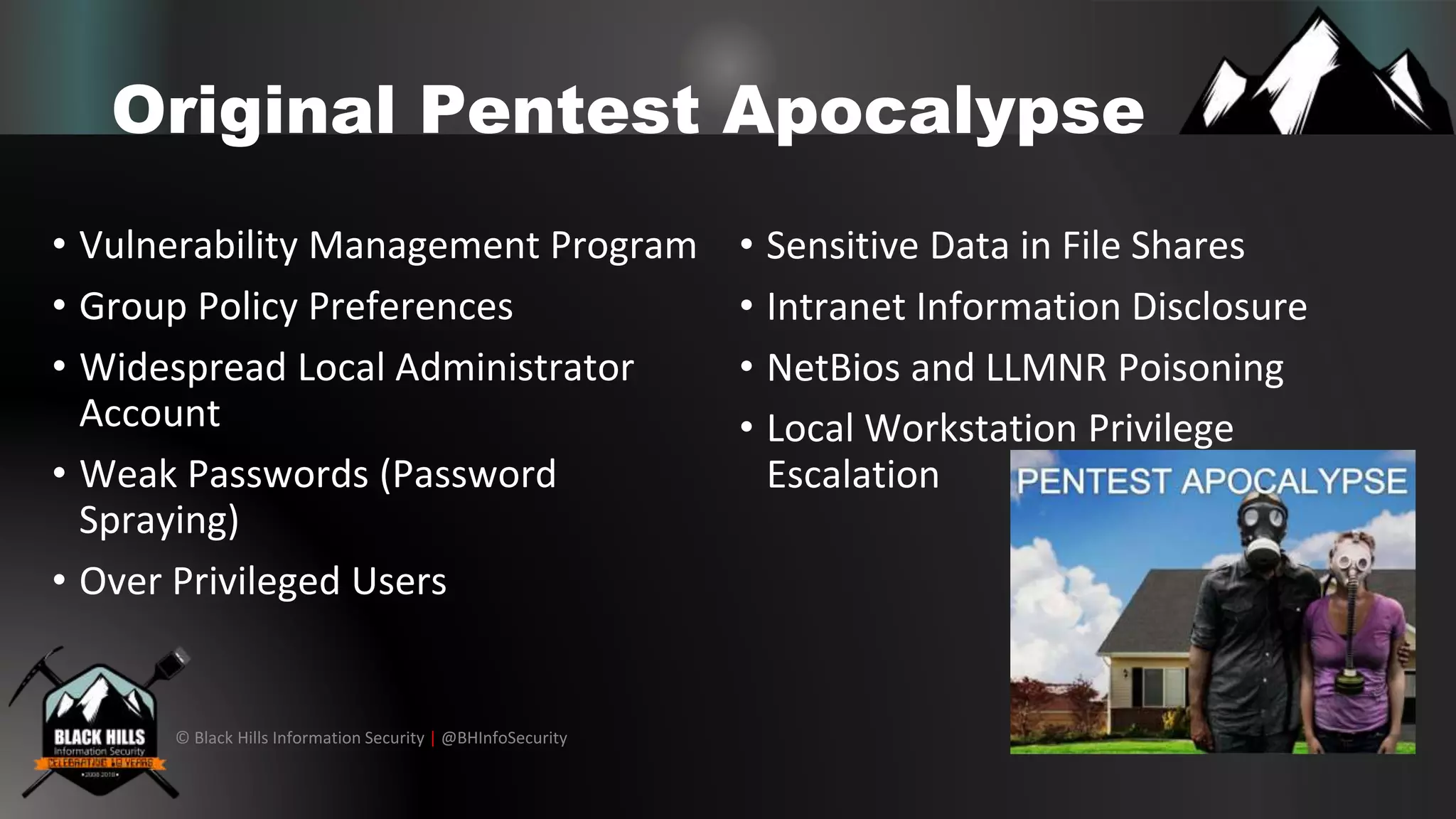
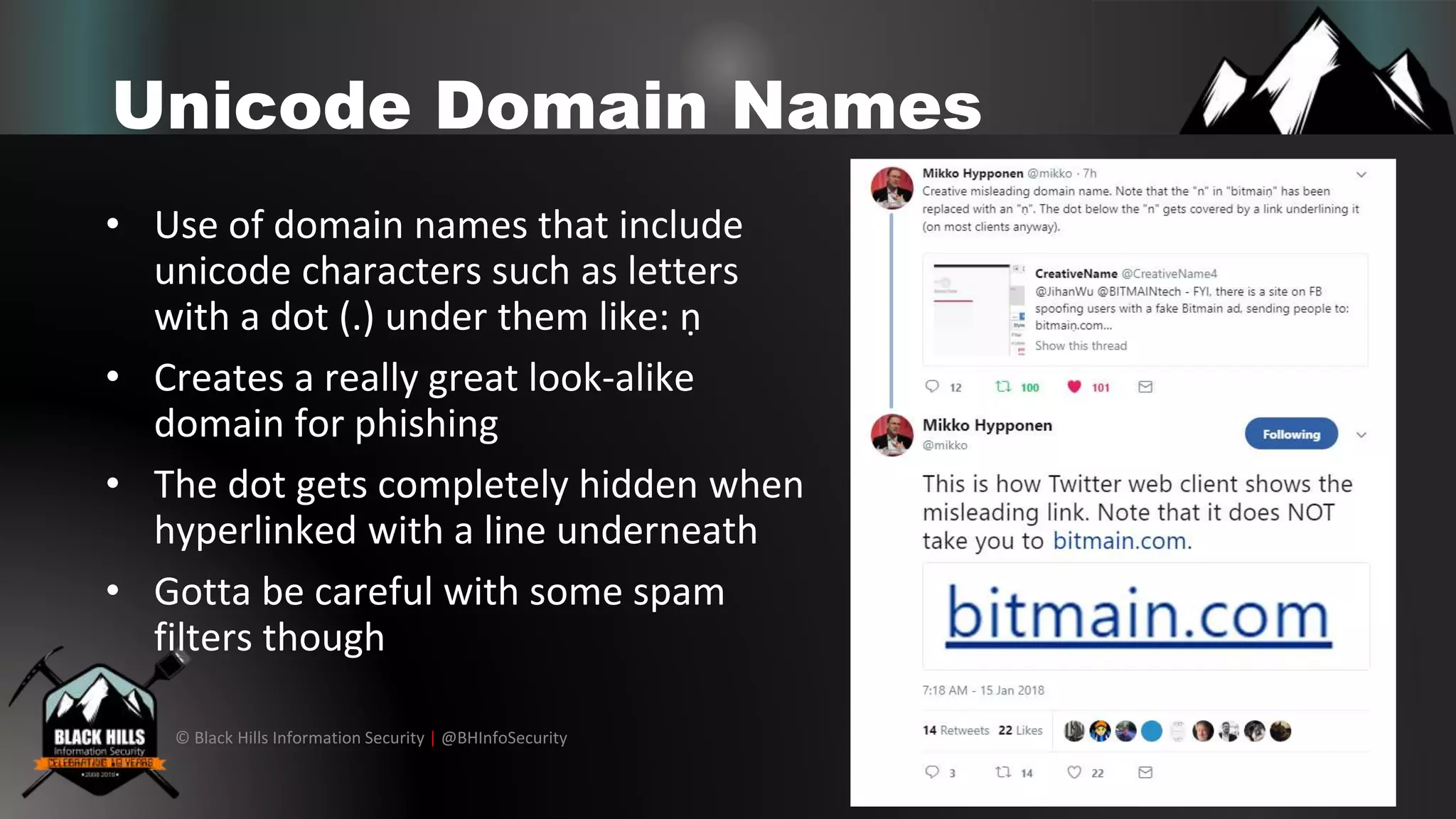
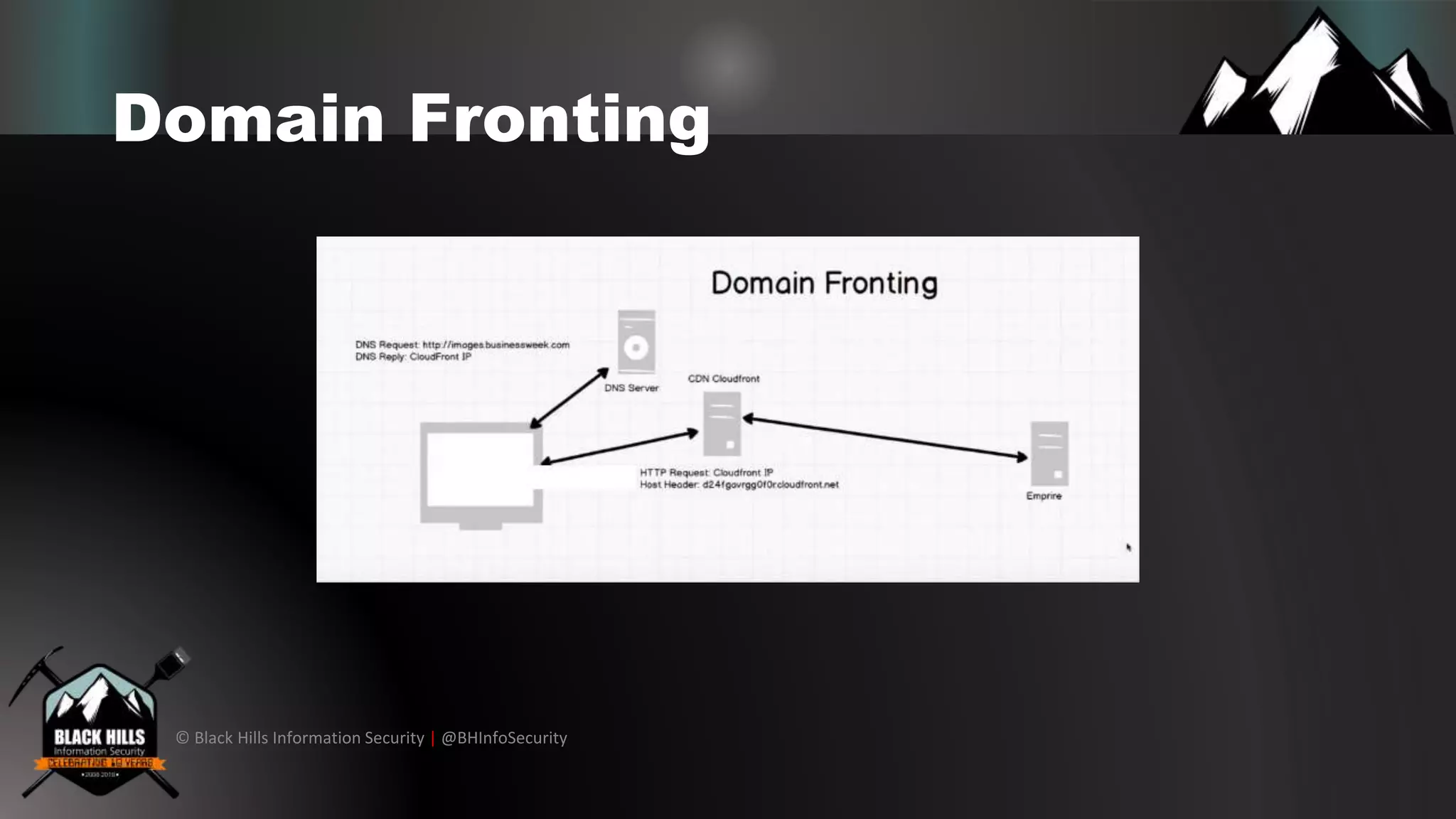
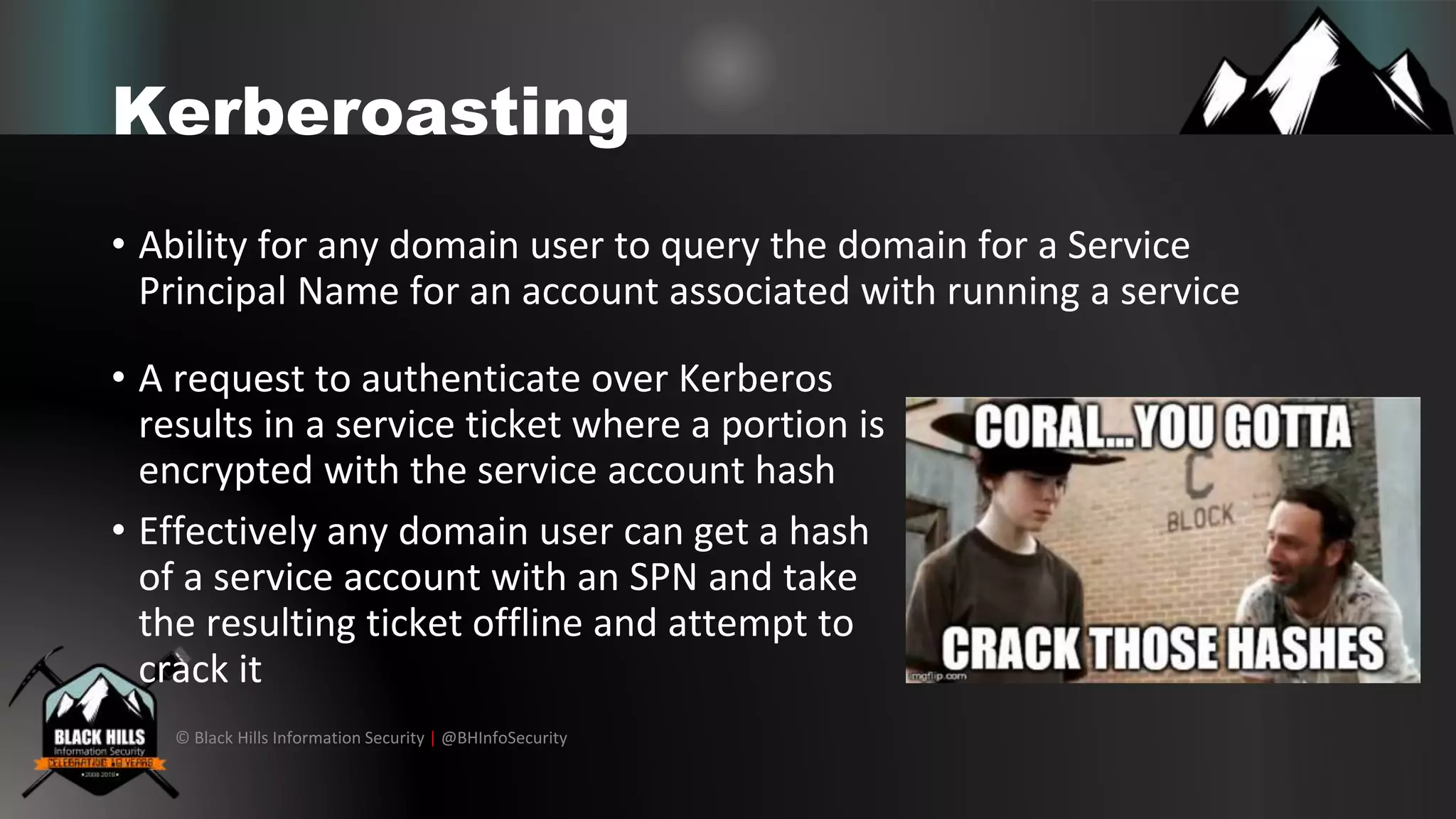
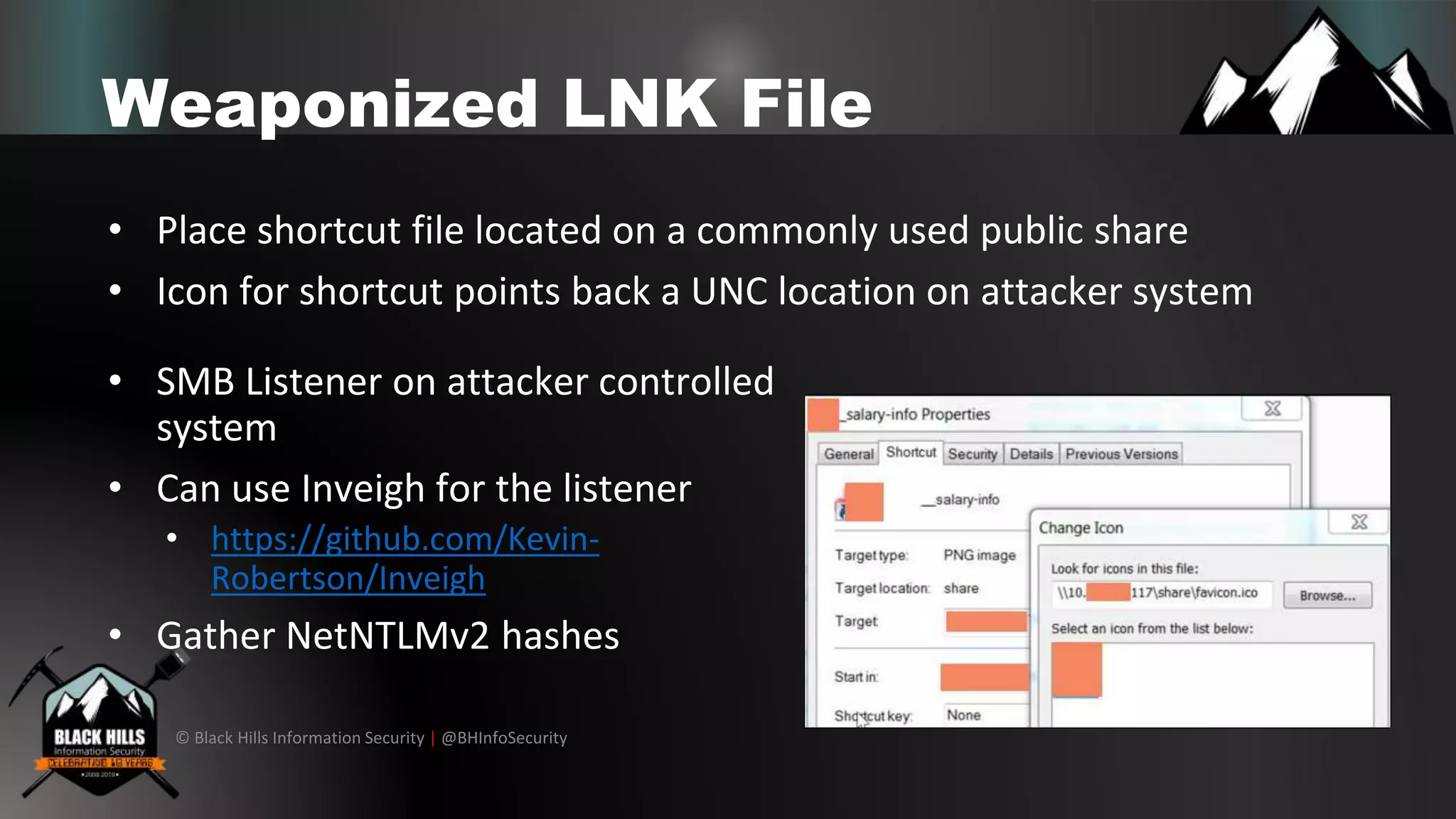
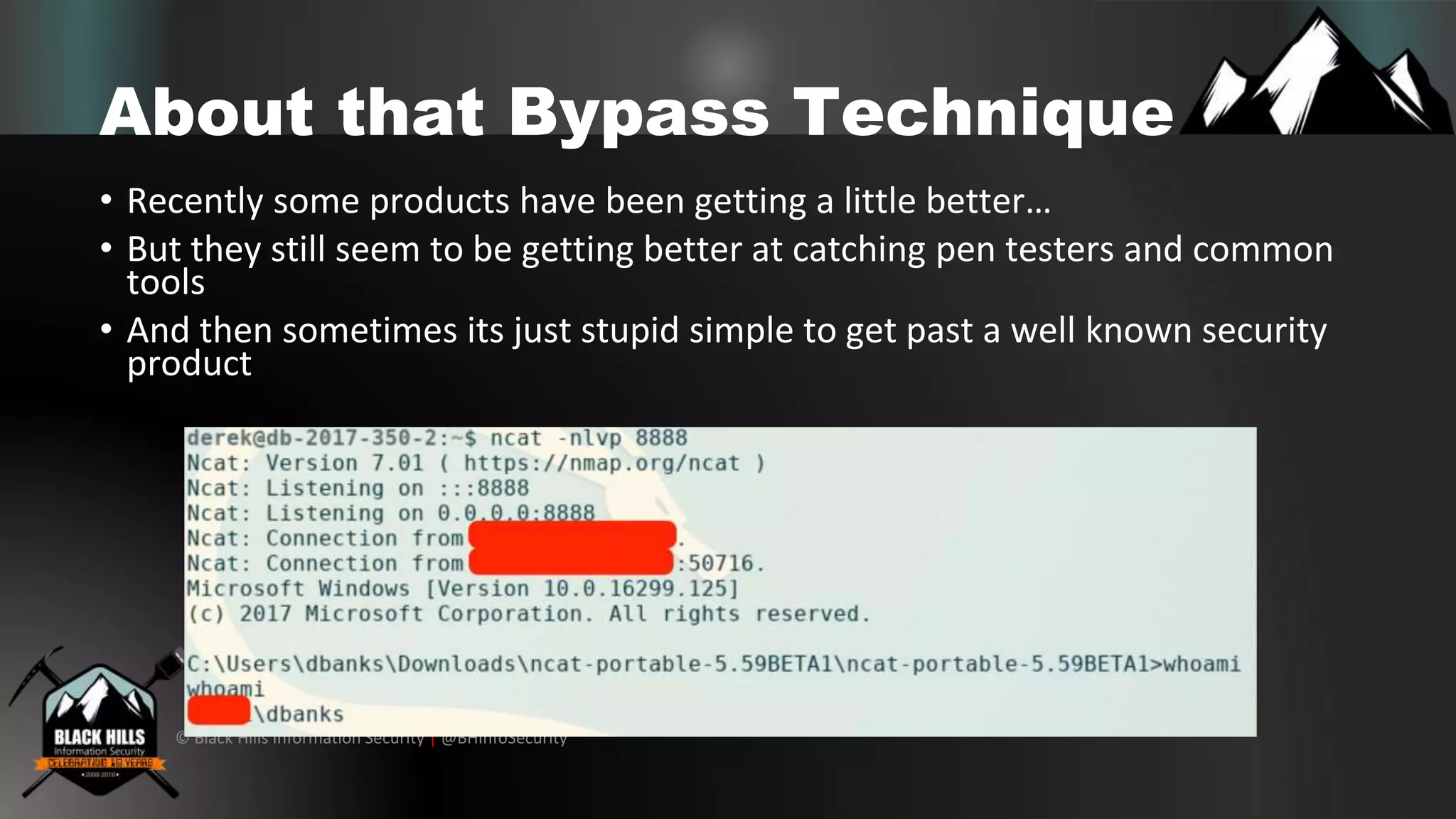
The document discusses various cybersecurity vulnerabilities and attack techniques, highlighting the importance of a robust vulnerability management program and the potential oversights in email systems and other areas. It contrasts red team engagements with traditional penetration tests and introduces several malicious tactics, including Google Calendar event injections and domain fronting. Recommendations for improving detection and prevention measures are provided, emphasizing user behavior enforcement and central log consolidation.