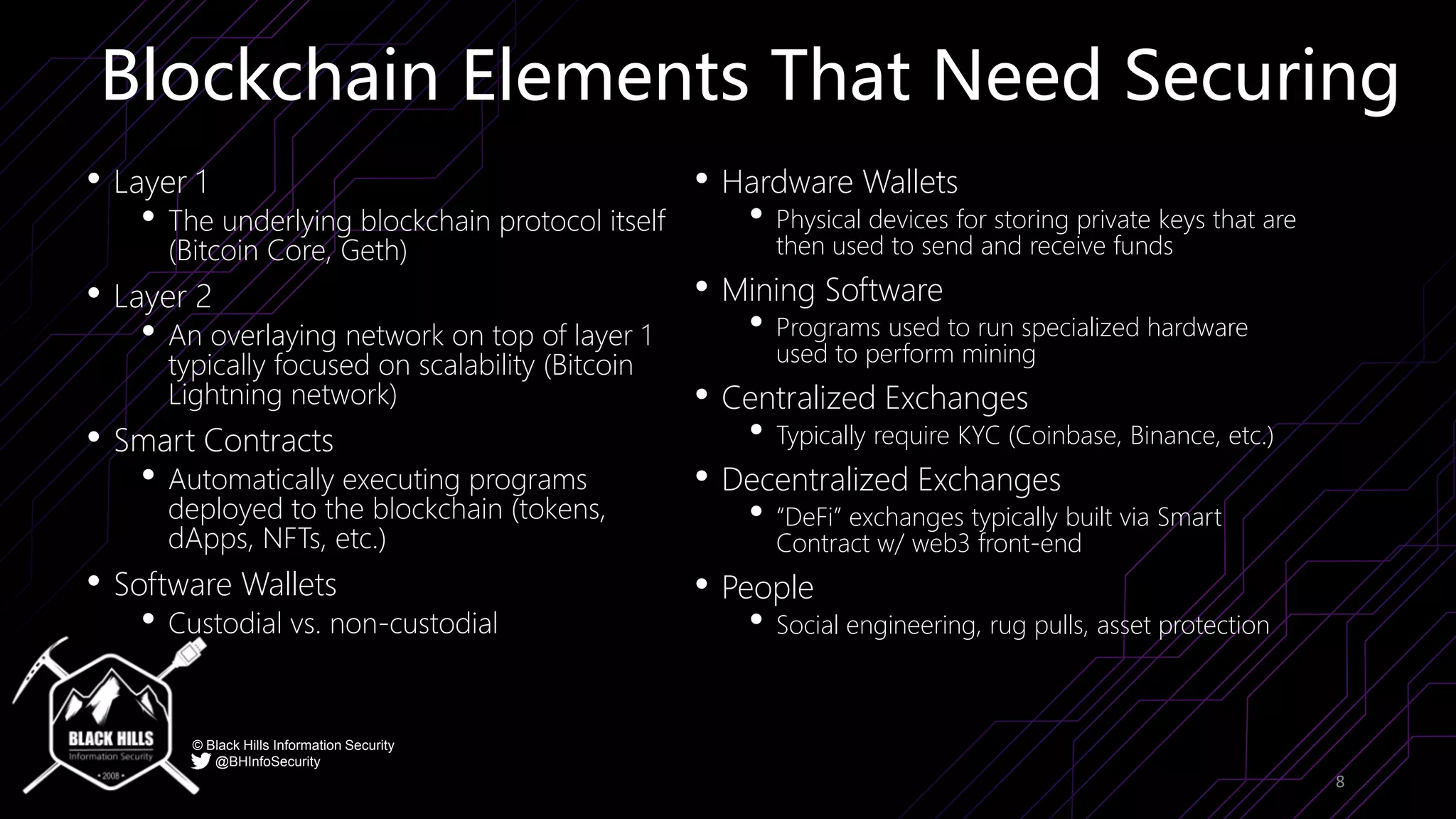
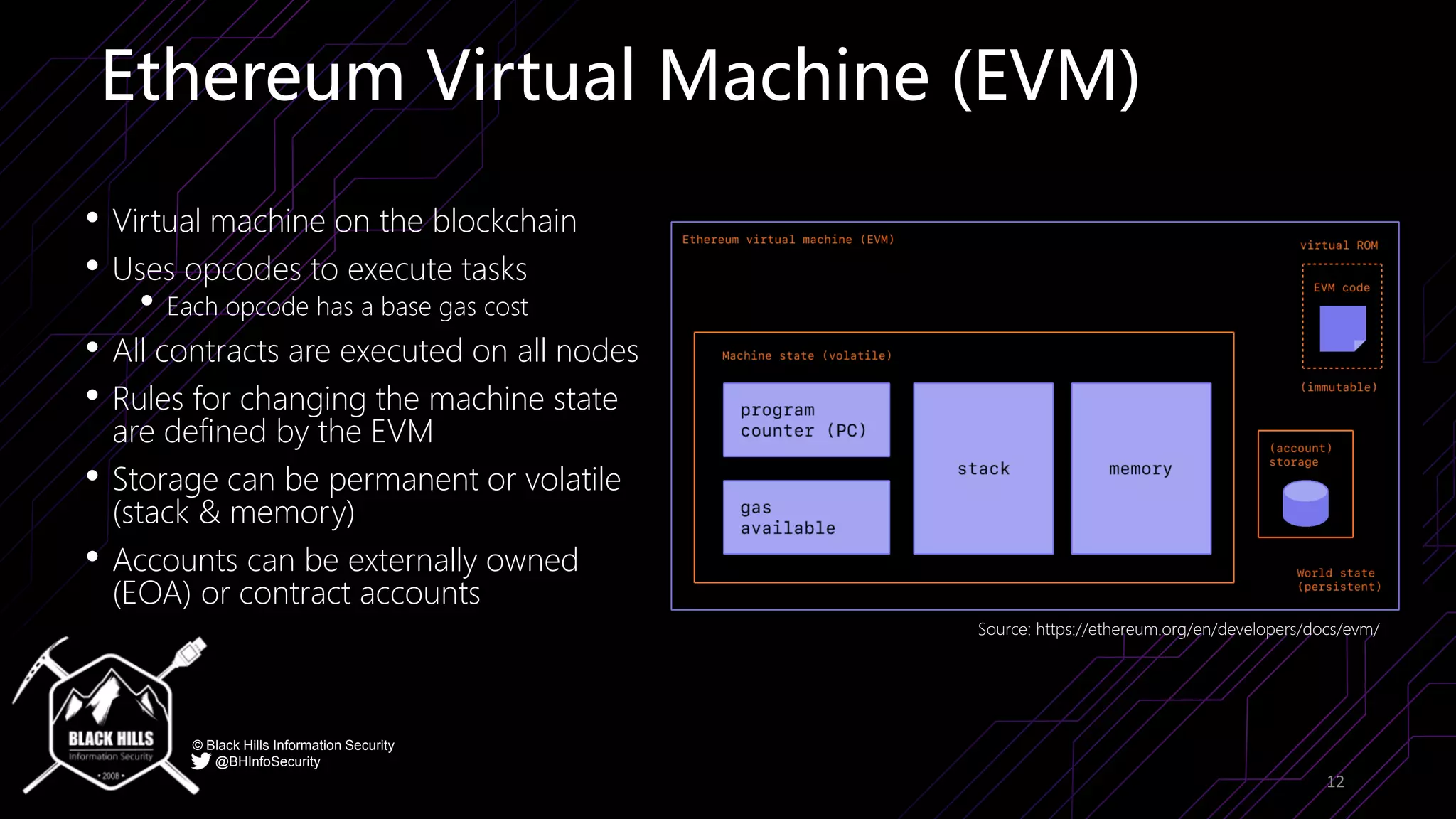
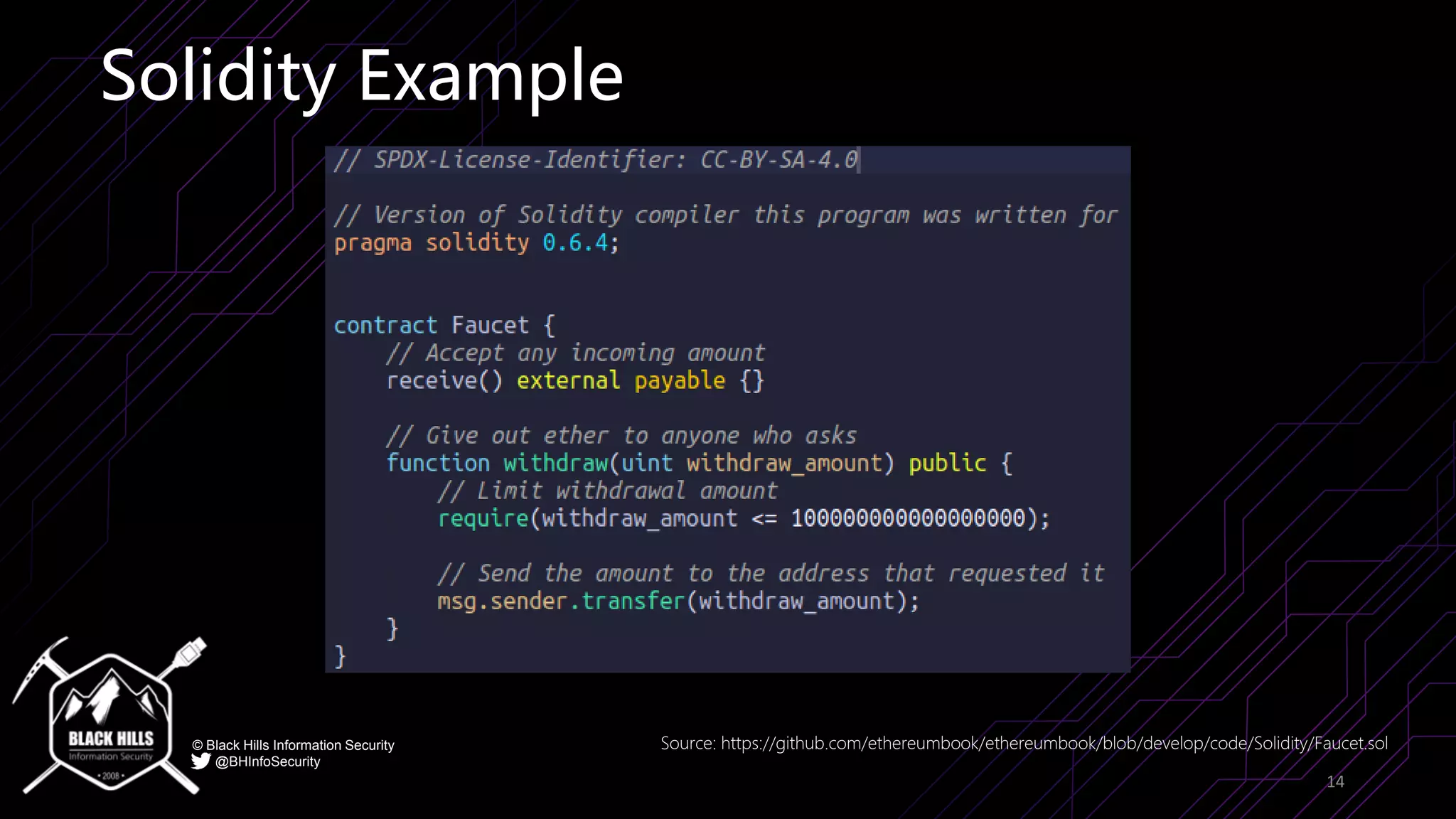
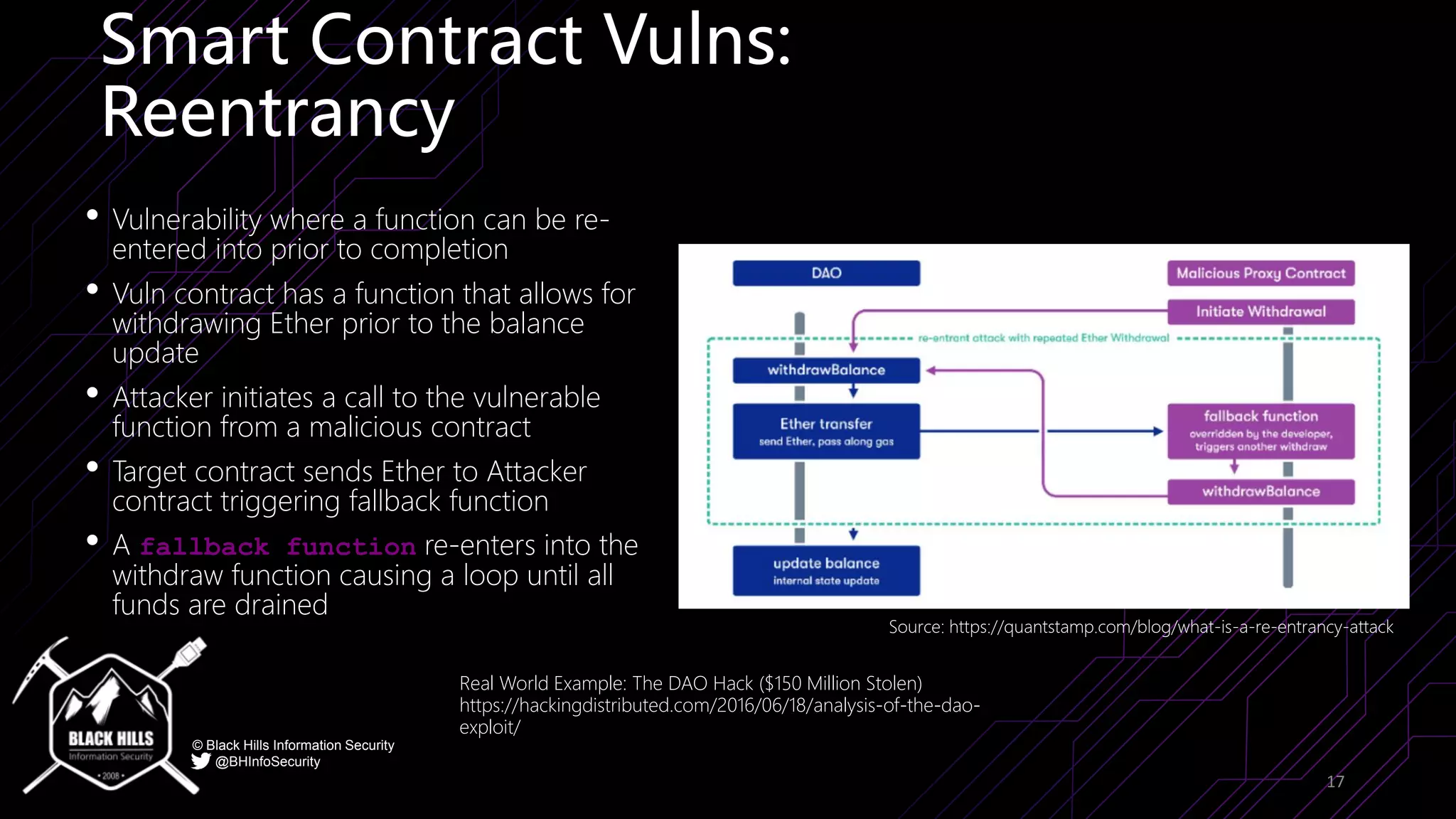
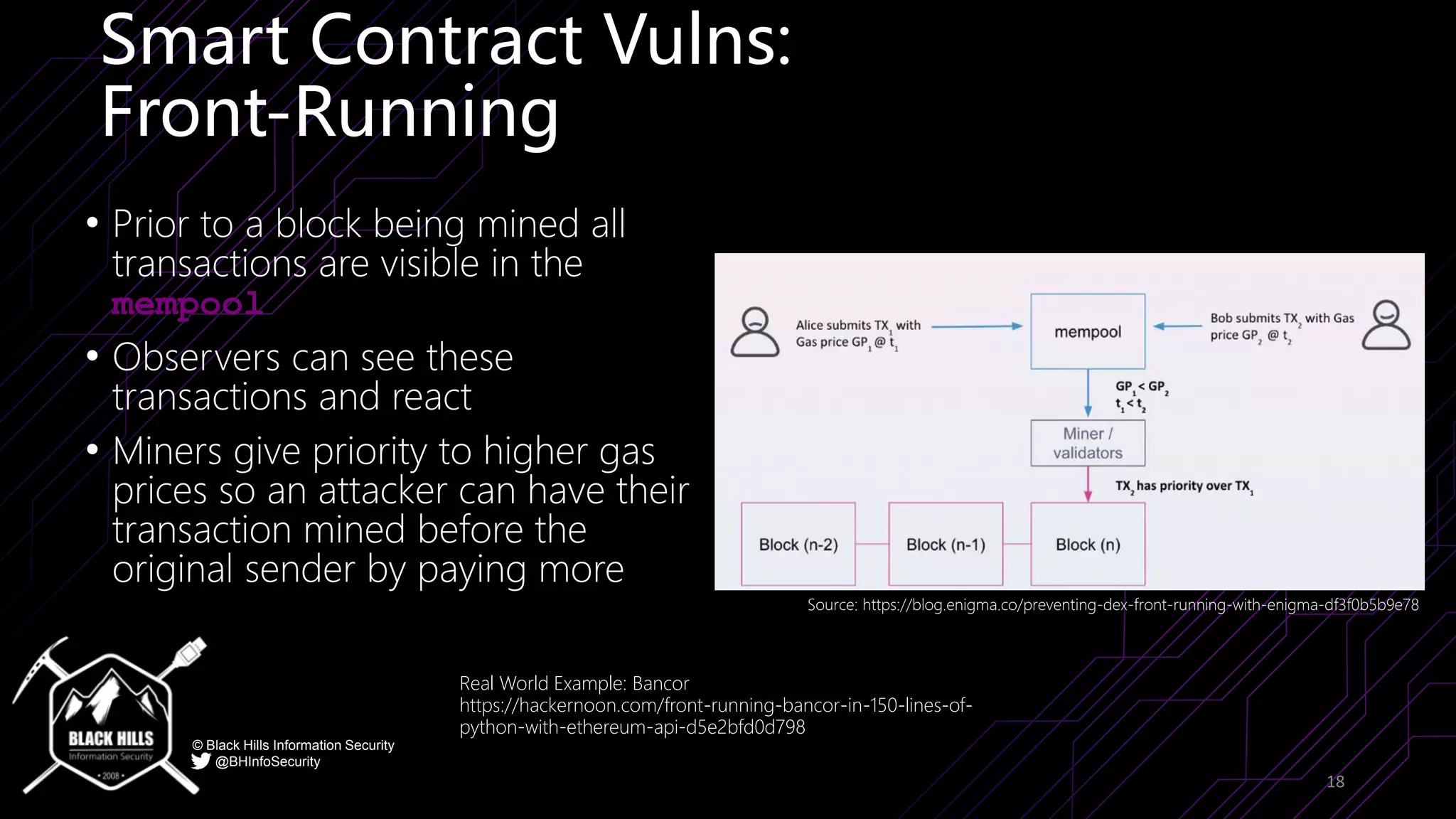
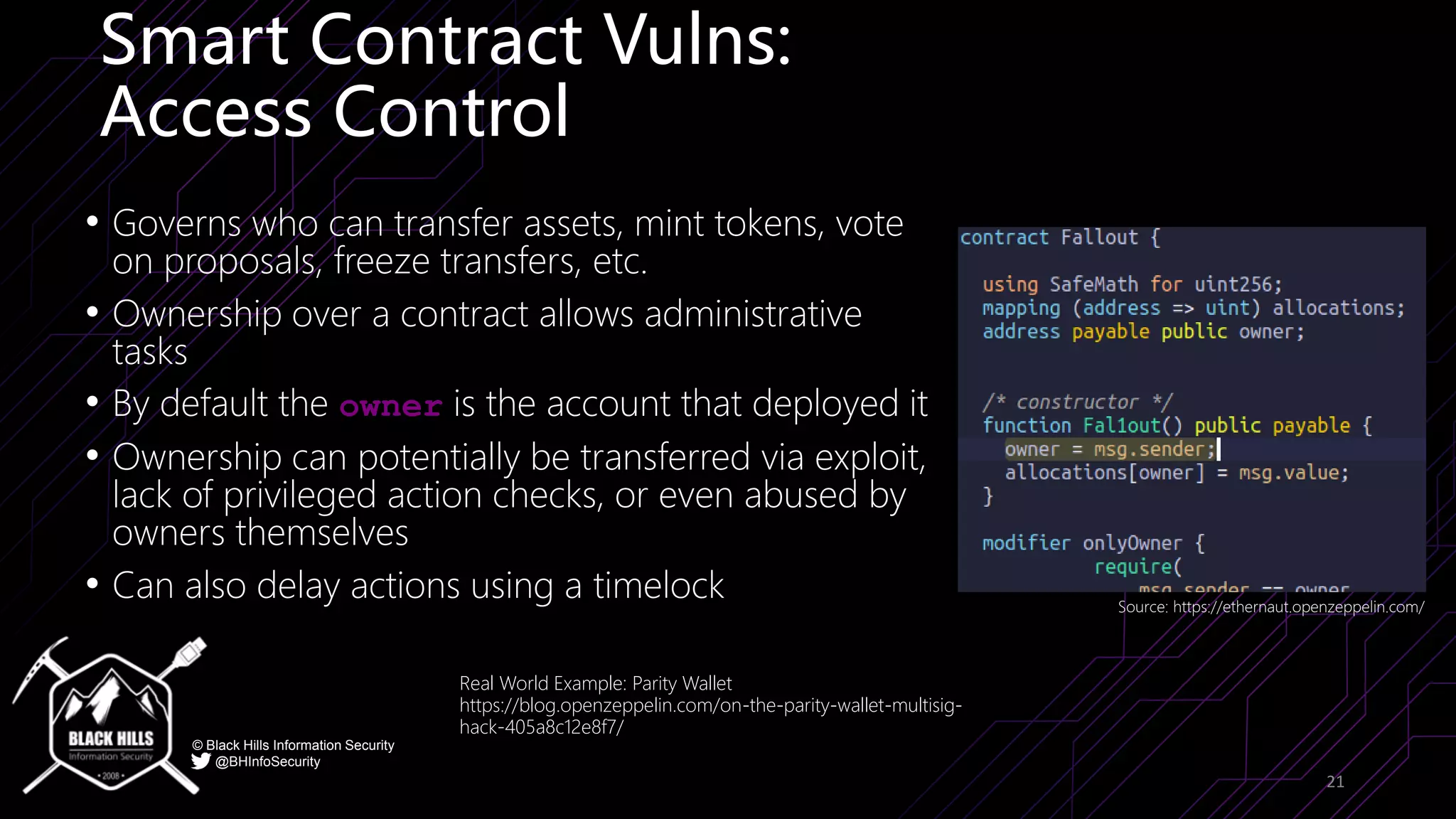
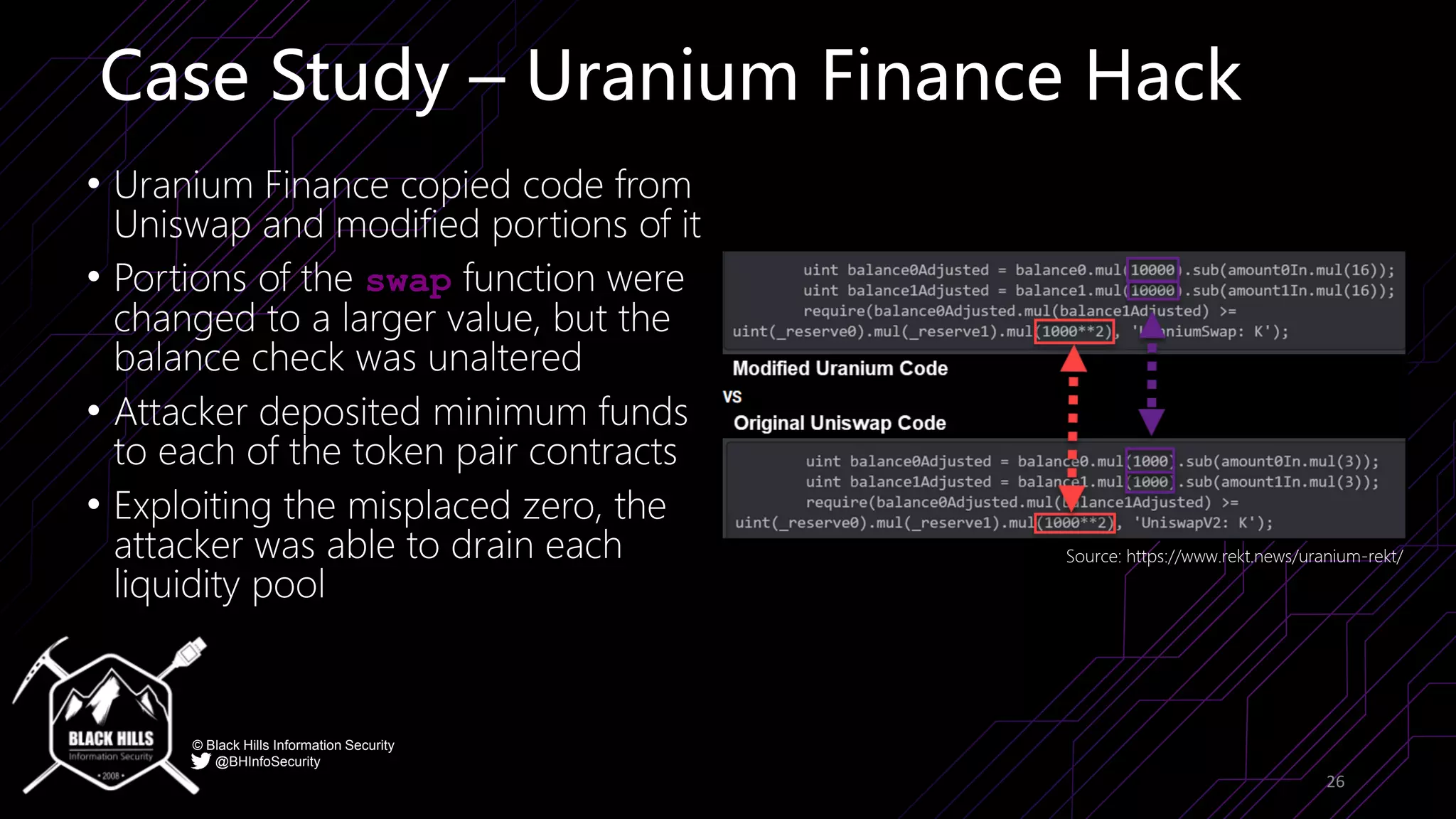
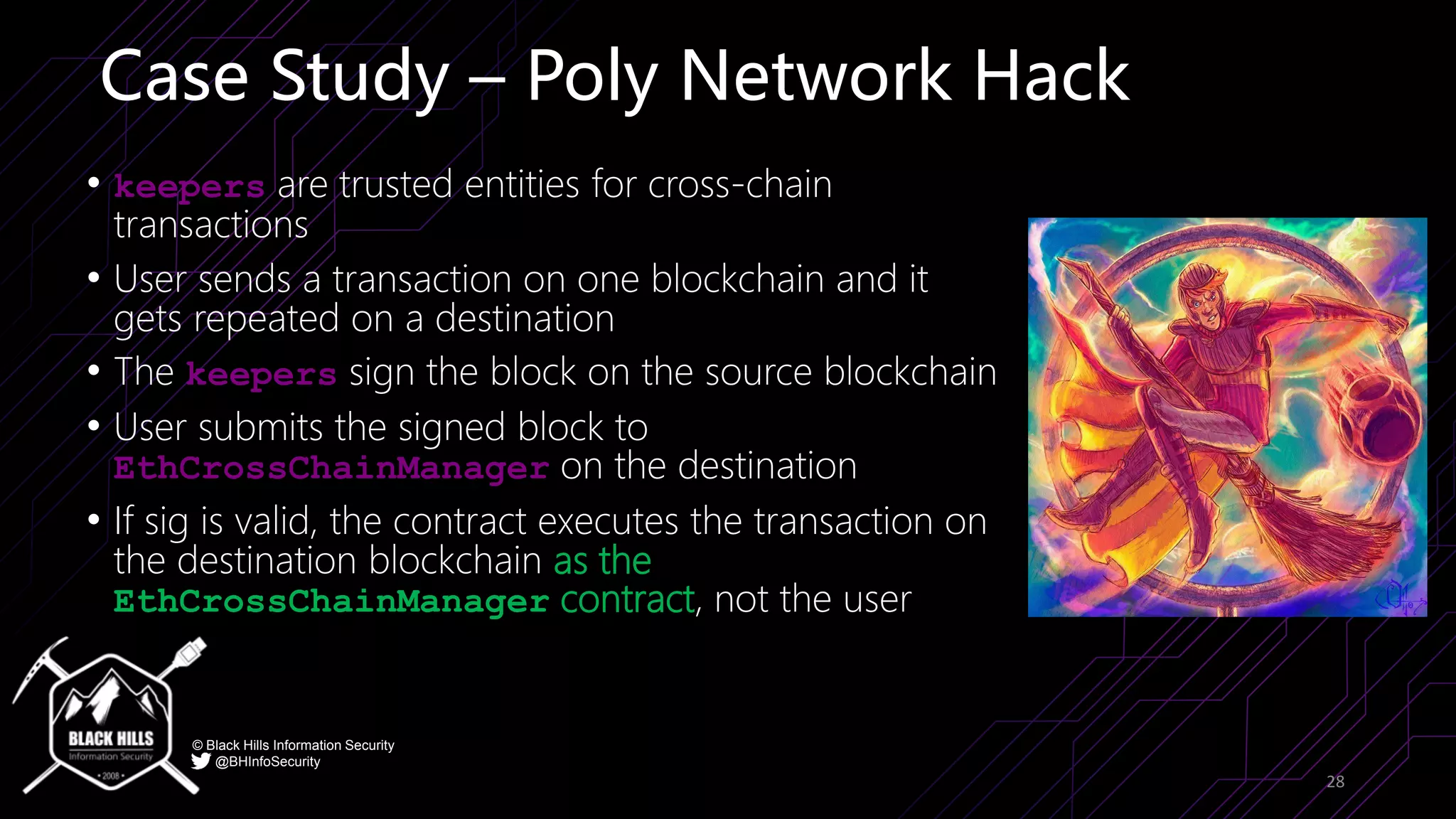
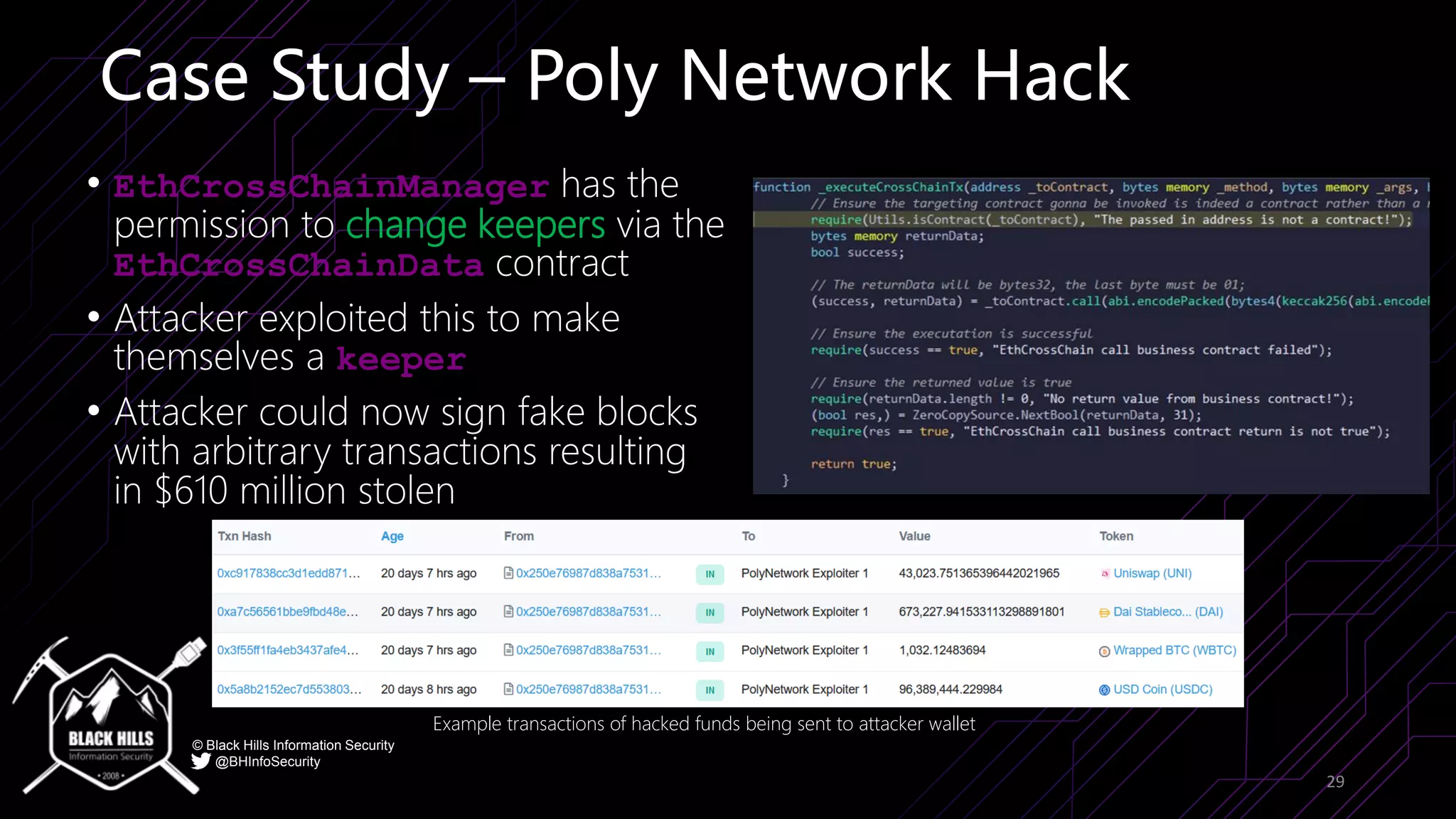
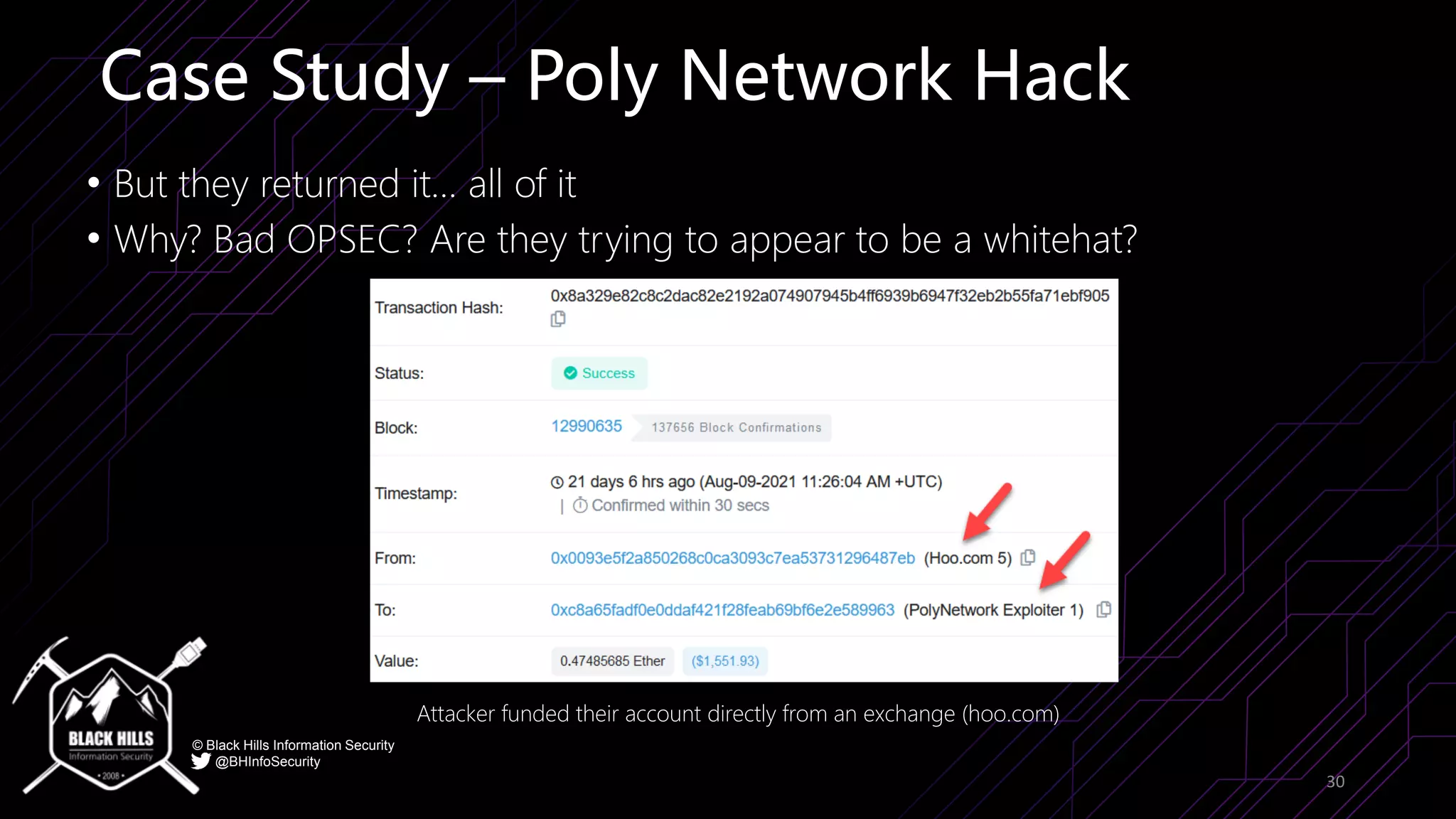
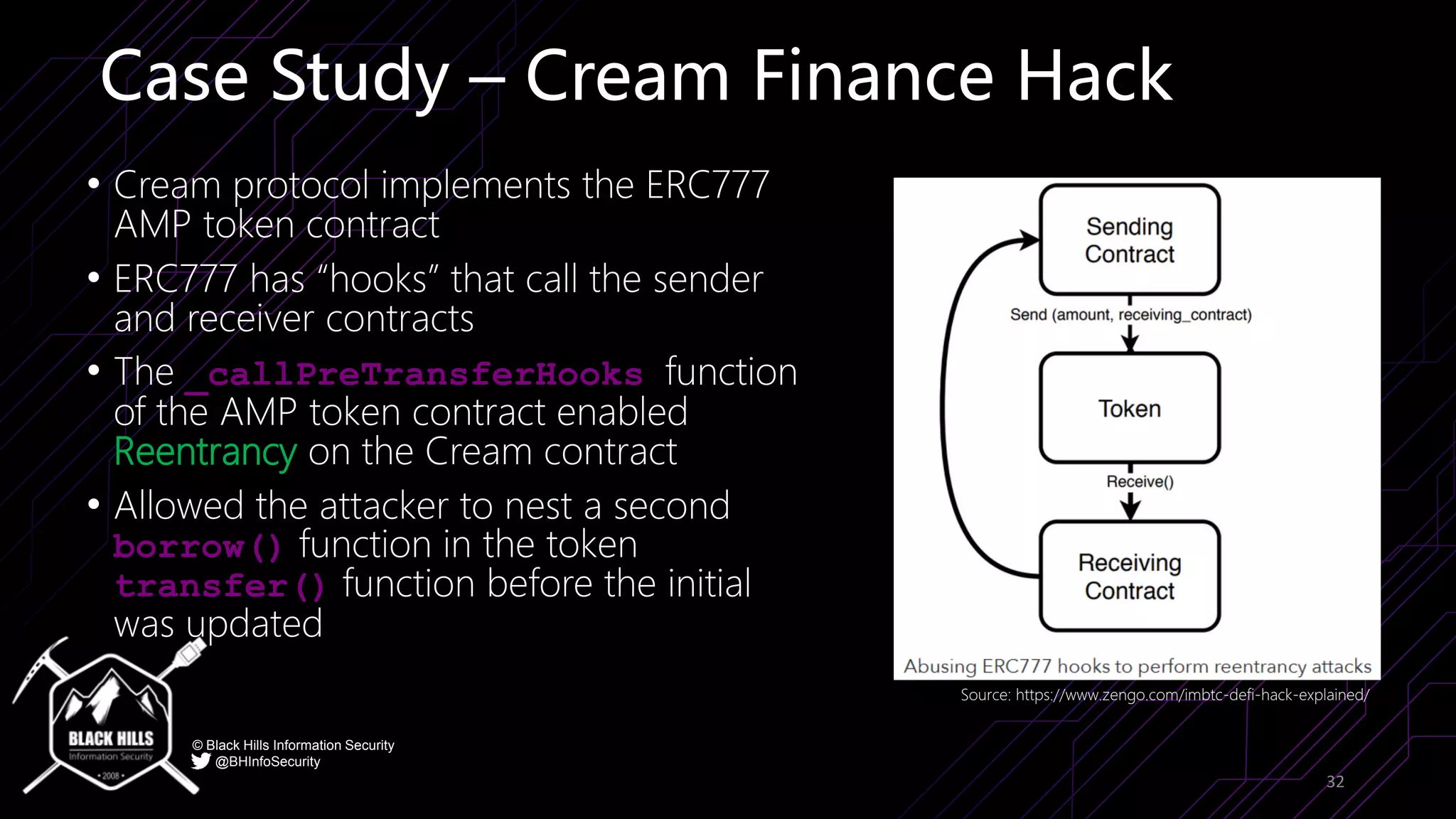
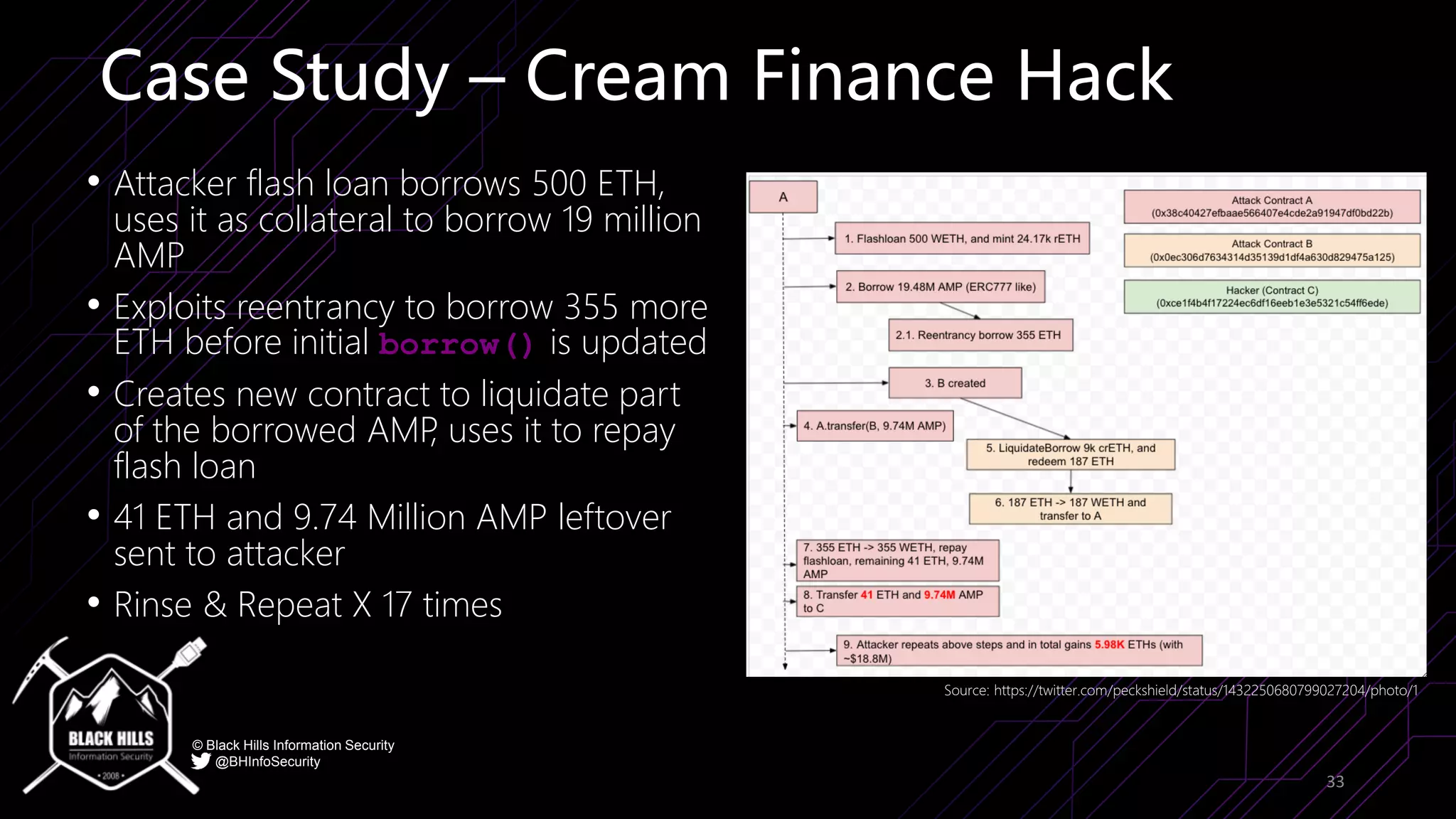
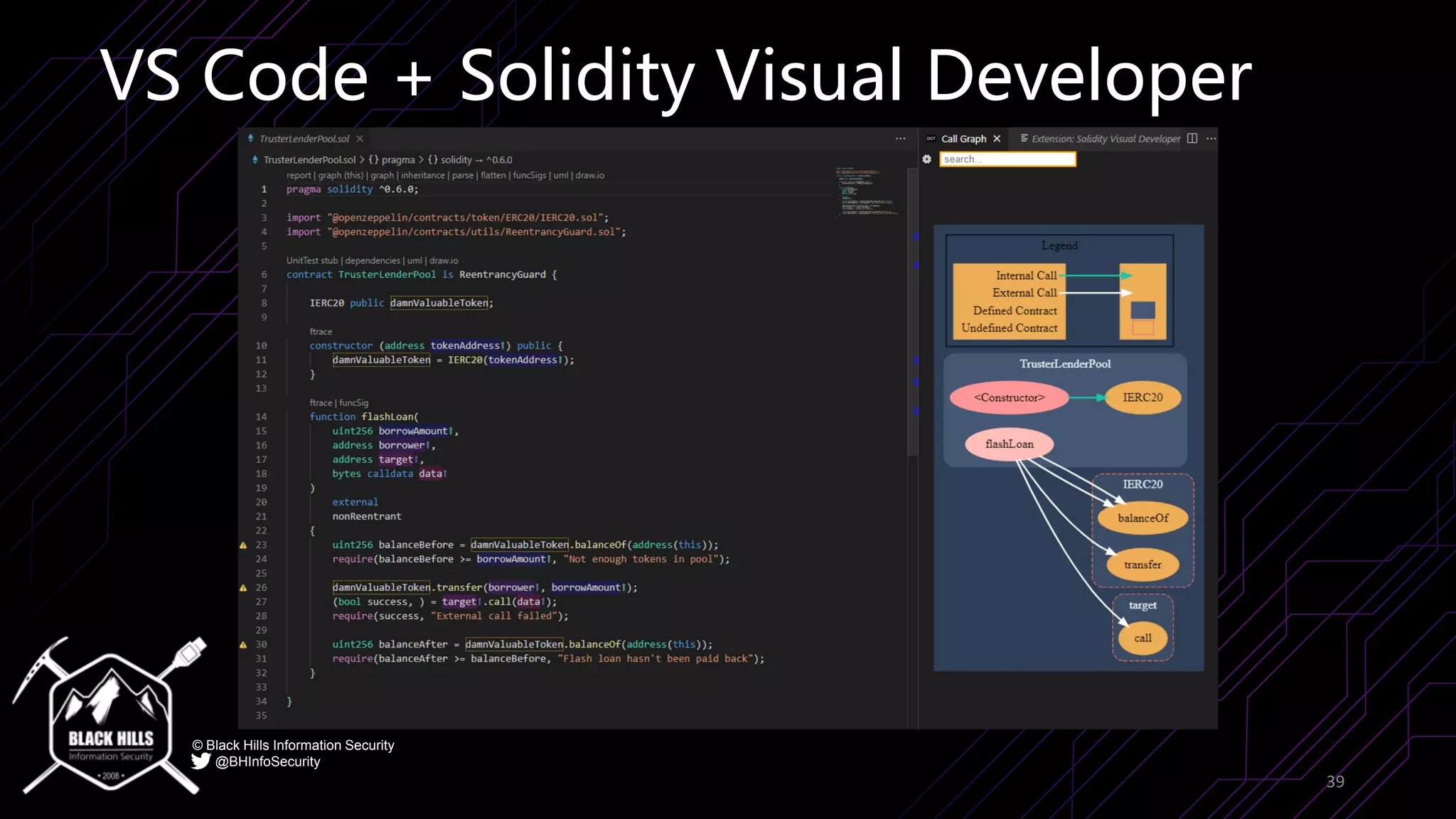
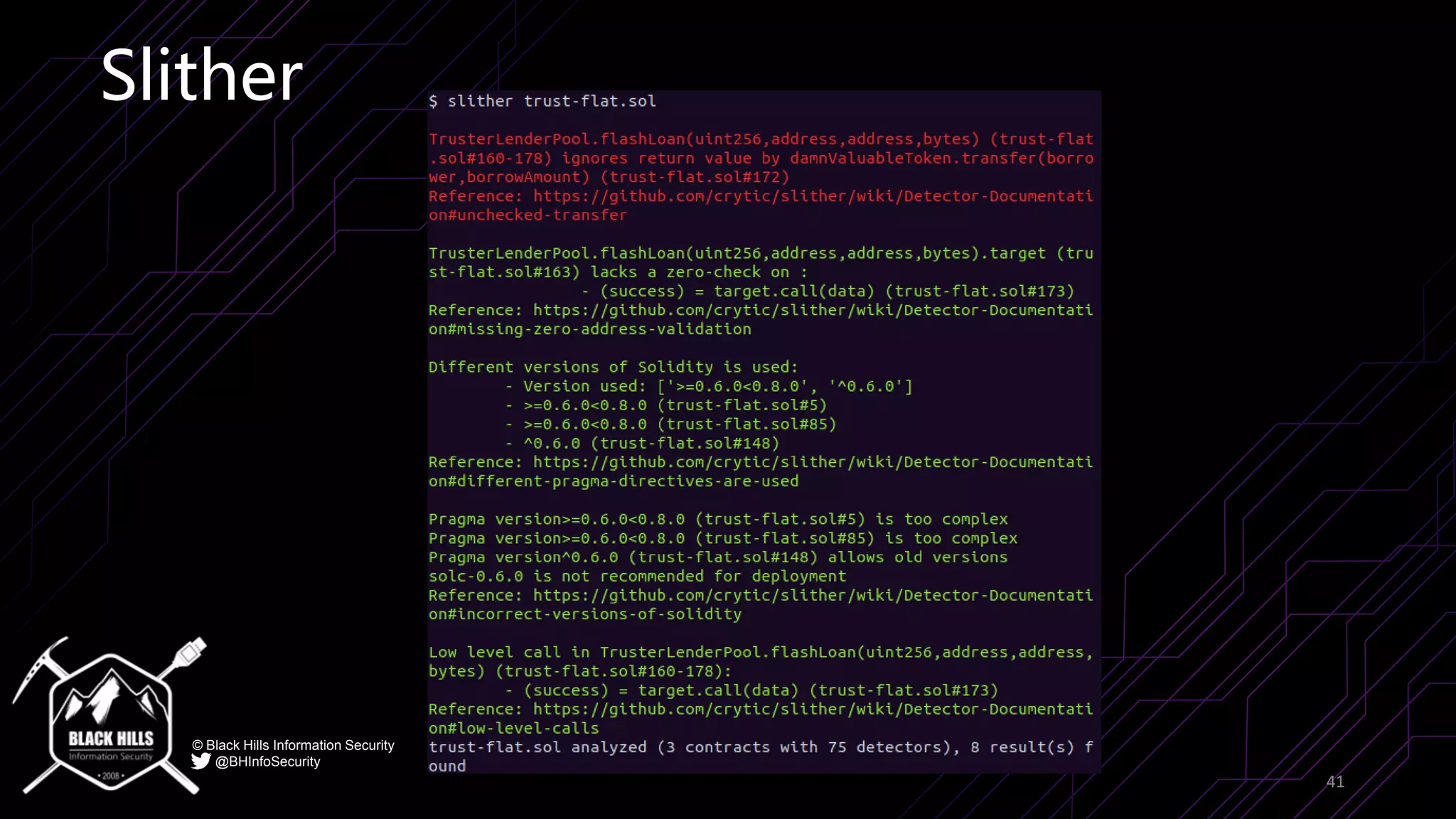
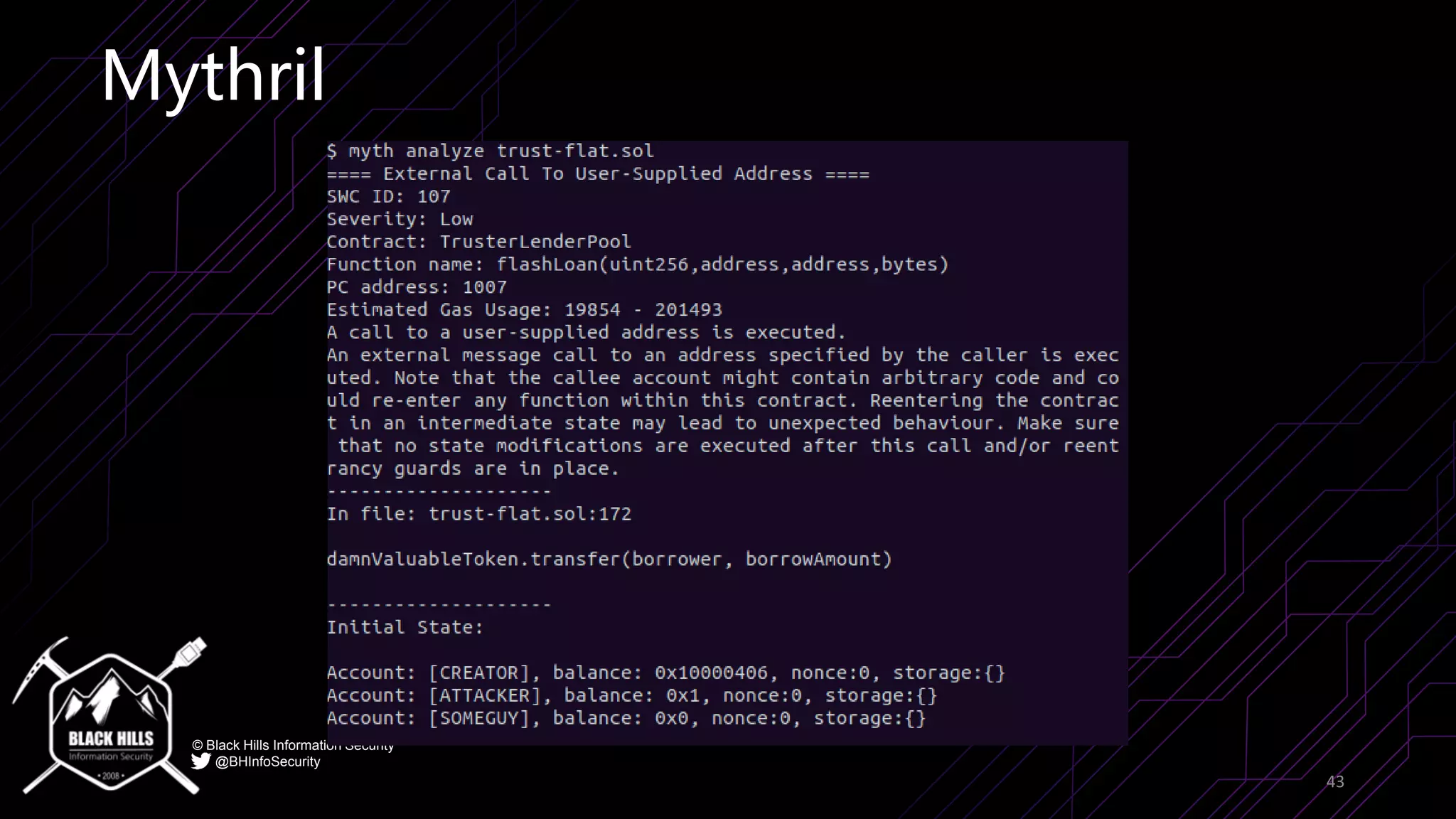
The document discusses the importance of blockchain security and smart contract auditing, highlighting significant hacks in decentralized finance (DeFi) and the vulnerabilities of smart contracts. It emphasizes the need for rigorous programming practices in smart contract development due to inherent risks like reentrancy and front-running attacks. Additionally, it outlines various blockchain use cases and the foundational elements that require security measures.