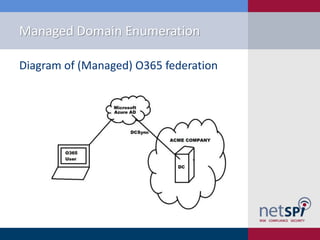
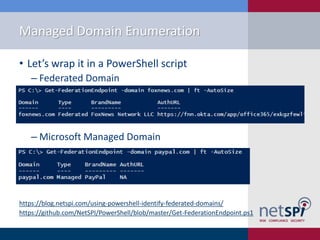
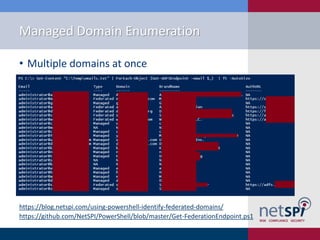
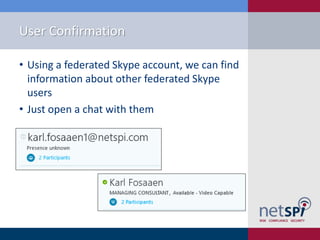
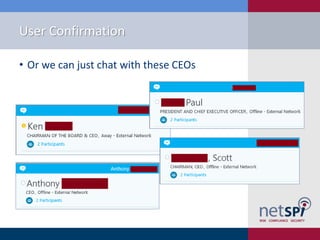
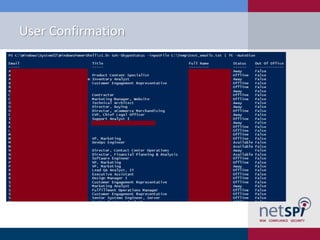
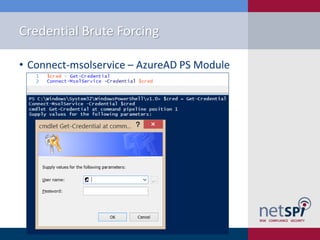
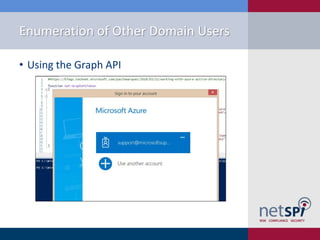
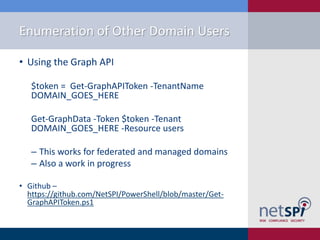
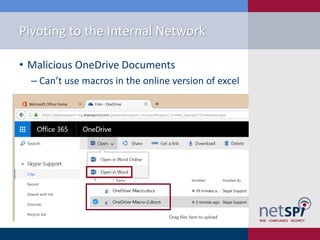
The document discusses methods for automating attacks on Office 365, including techniques for domain enumeration, user enumeration, credential brute forcing, and internal network pivoting. It also highlights various PowerShell scripts and tools that facilitate these attacks and outlines mitigations such as enabling dual-factor authentication and limiting federation to trusted domains. The presentation emphasizes the importance of monitoring endpoints and enforcing strong password requirements to reduce vulnerabilities.