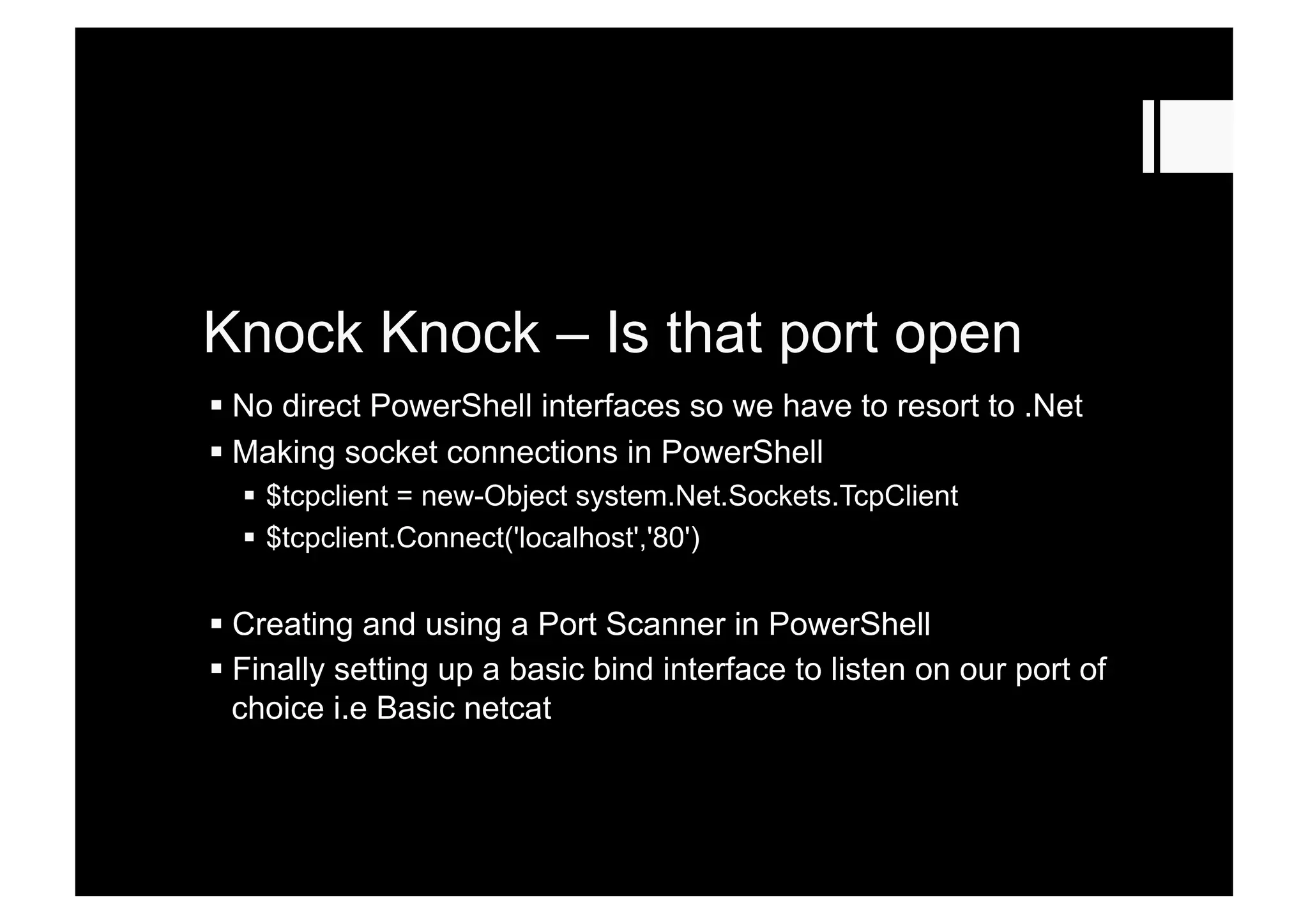
This document introduces PowerShell and explains why hackers should learn it. PowerShell can be used for tasks like port scanning, brute forcing RDP/SQL, dumping password hashes, and quickly setting up backdoors. It comes preinstalled on many modern Windows systems and provides an unchecked environment for accessing and controlling the operating system through commands and scripting. The document demonstrates various hacking techniques that can be accomplished using PowerShell, such as poking the system, checking for open ports, and gaining complete control over servers after initial access.