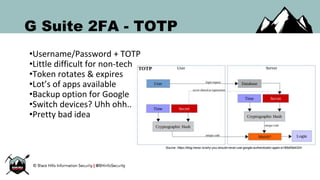
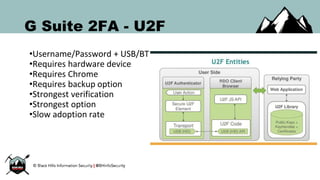
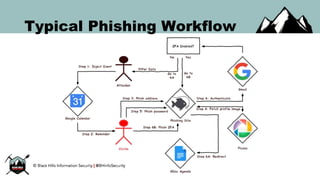
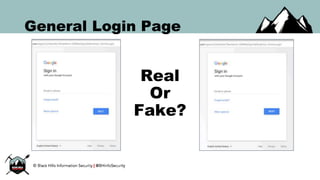
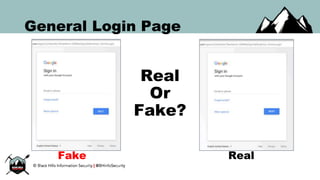
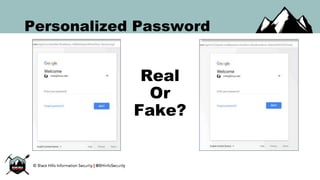
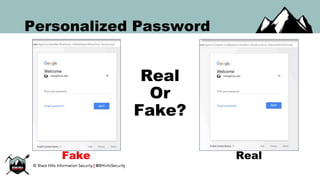
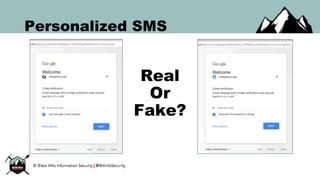
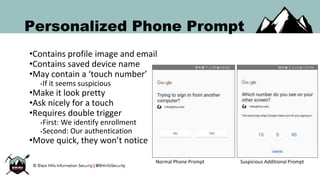
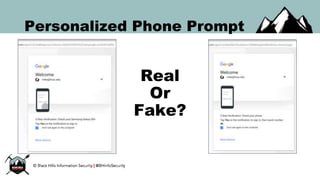
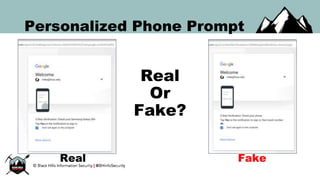
The document discusses the security vulnerabilities of Google Suite, focusing on real-world attack paths, including event injection and personalized phishing tactics. It highlights various two-factor authentication methods, their drawbacks, and the necessity of user awareness and vigilance. The presentation ends with a strong warning about the ease of event injection into Google calendars and calls for improved security measures from Google.