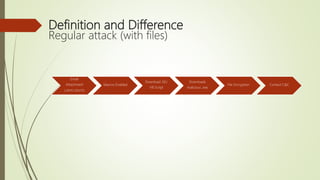
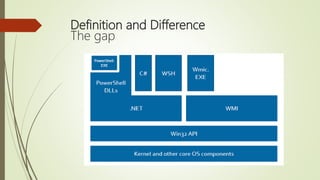
This document discusses fileless attacks, which use existing software and authorized protocols to carry out malicious activities without downloading files. Fileless attacks can use things like PowerShell, WMI, browsers, and Office applications to connect to command and control servers and execute malicious scripts in memory only. Some behaviors and evidence of fileless attacks include unusual child processes starting, legitimate DLLs loading from unexpected parents, and applications like Word or Excel invoking PowerShell or making network connections. The document demonstrates detecting fileless attacks using Event IDs in Windows logs related to process creation and PowerShell pipeline execution details.