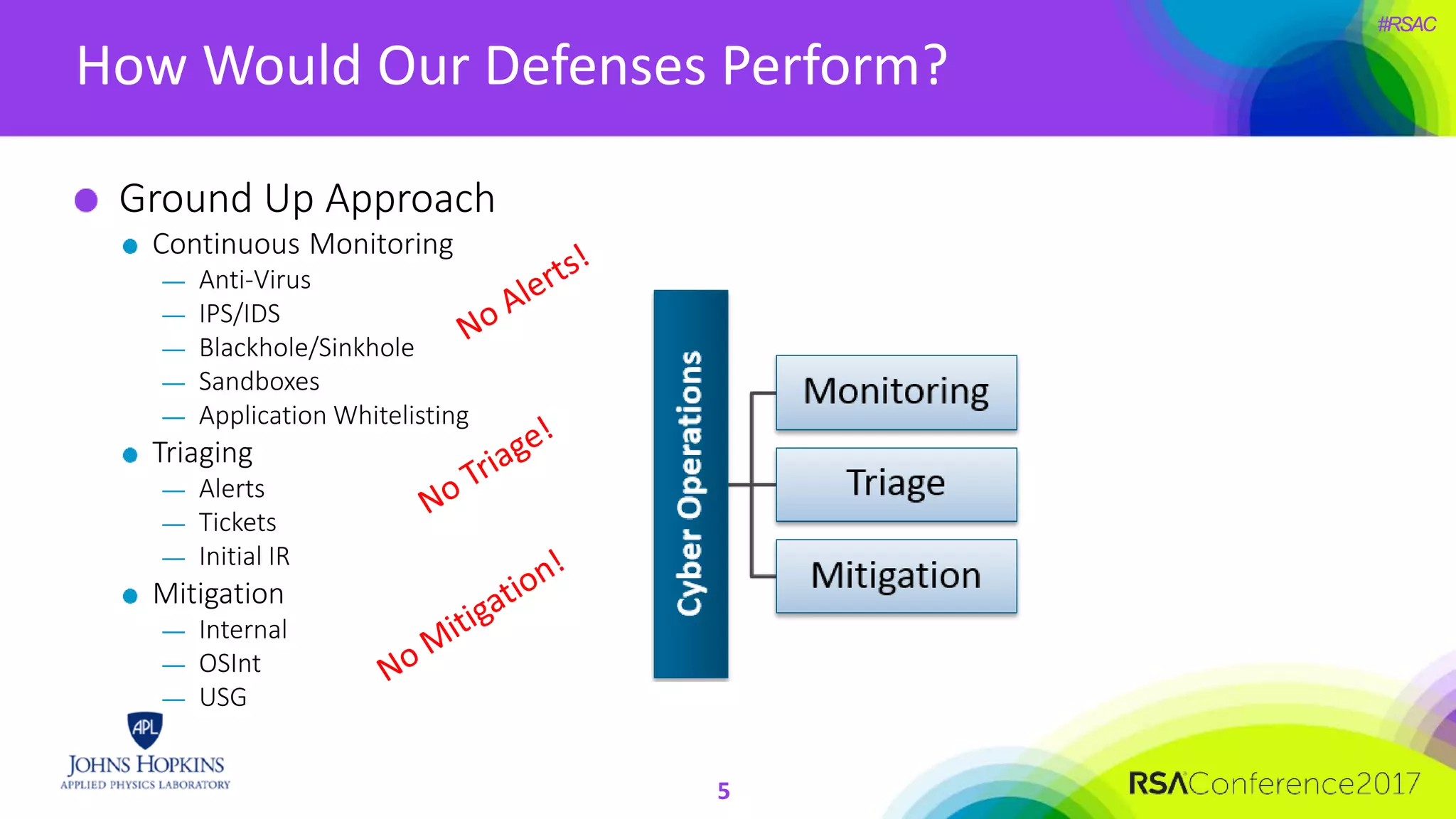
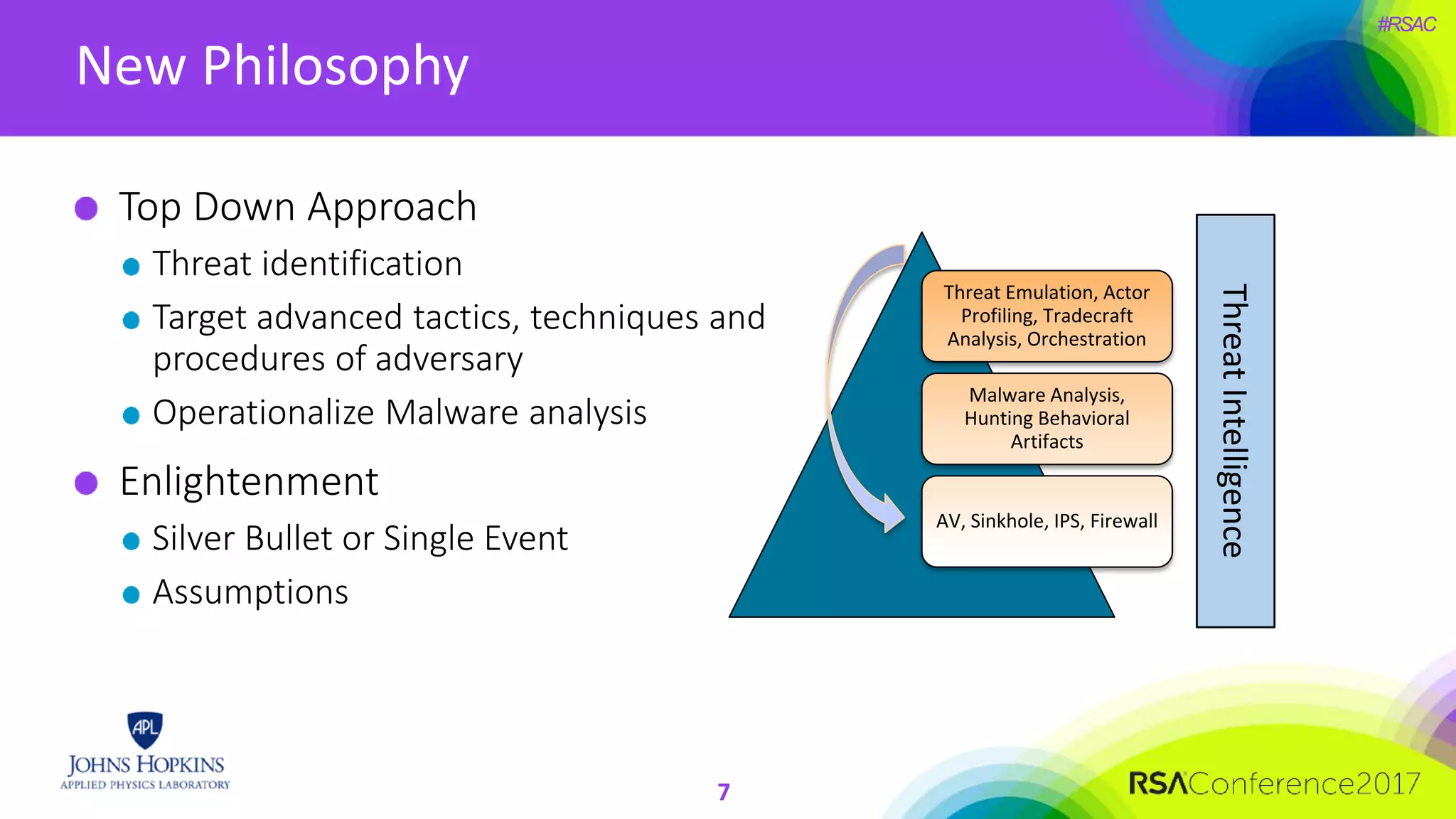
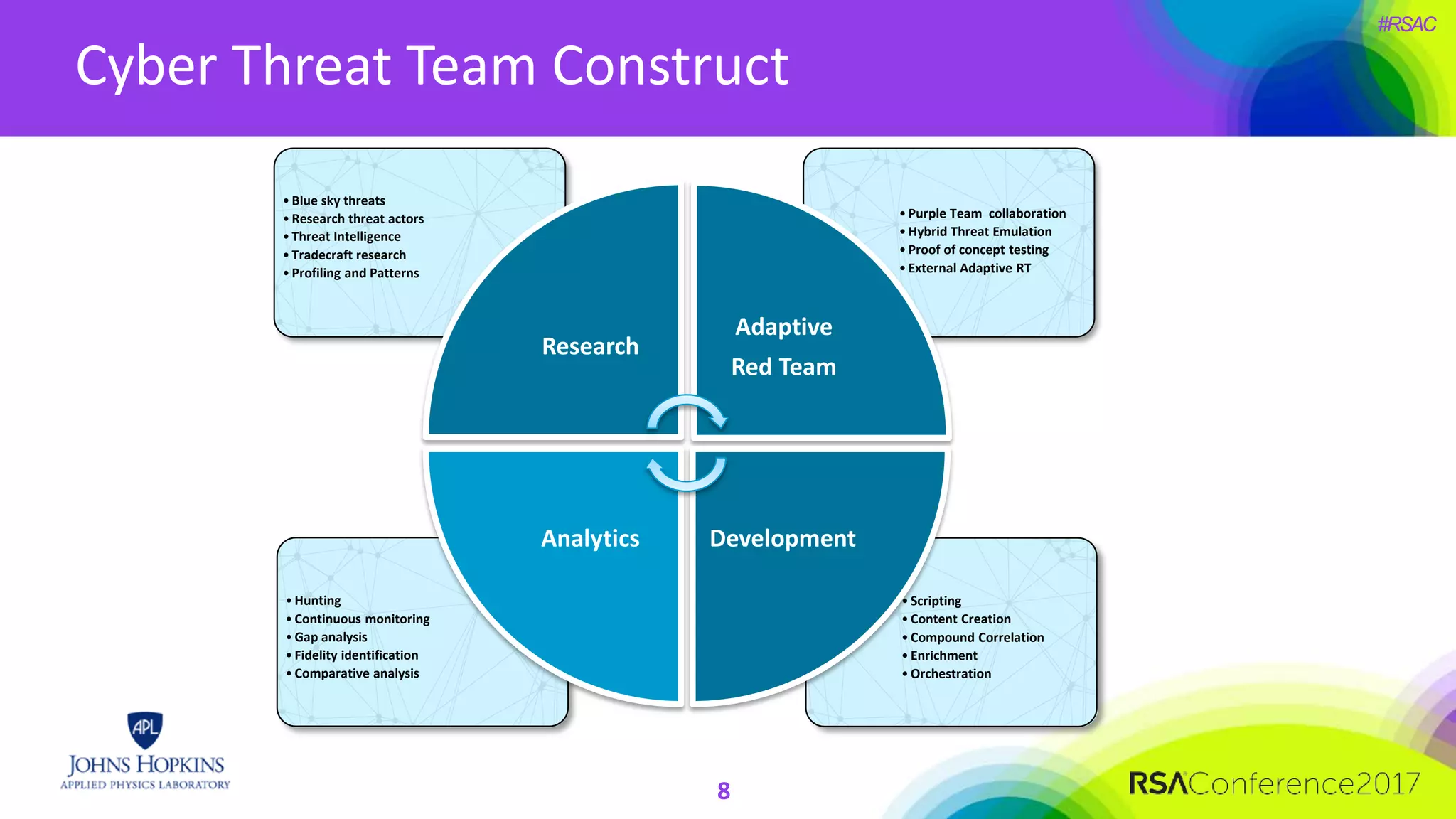
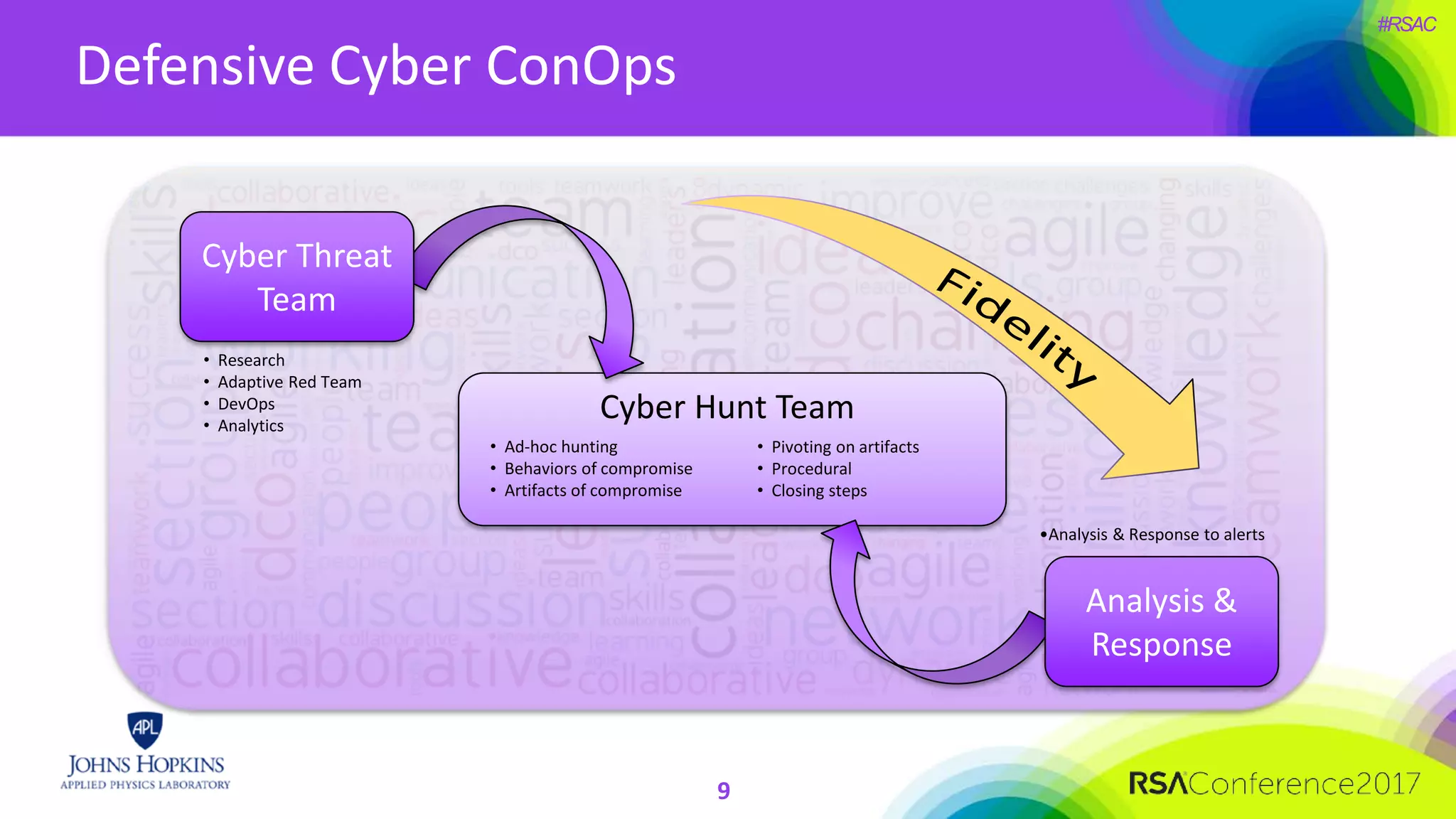
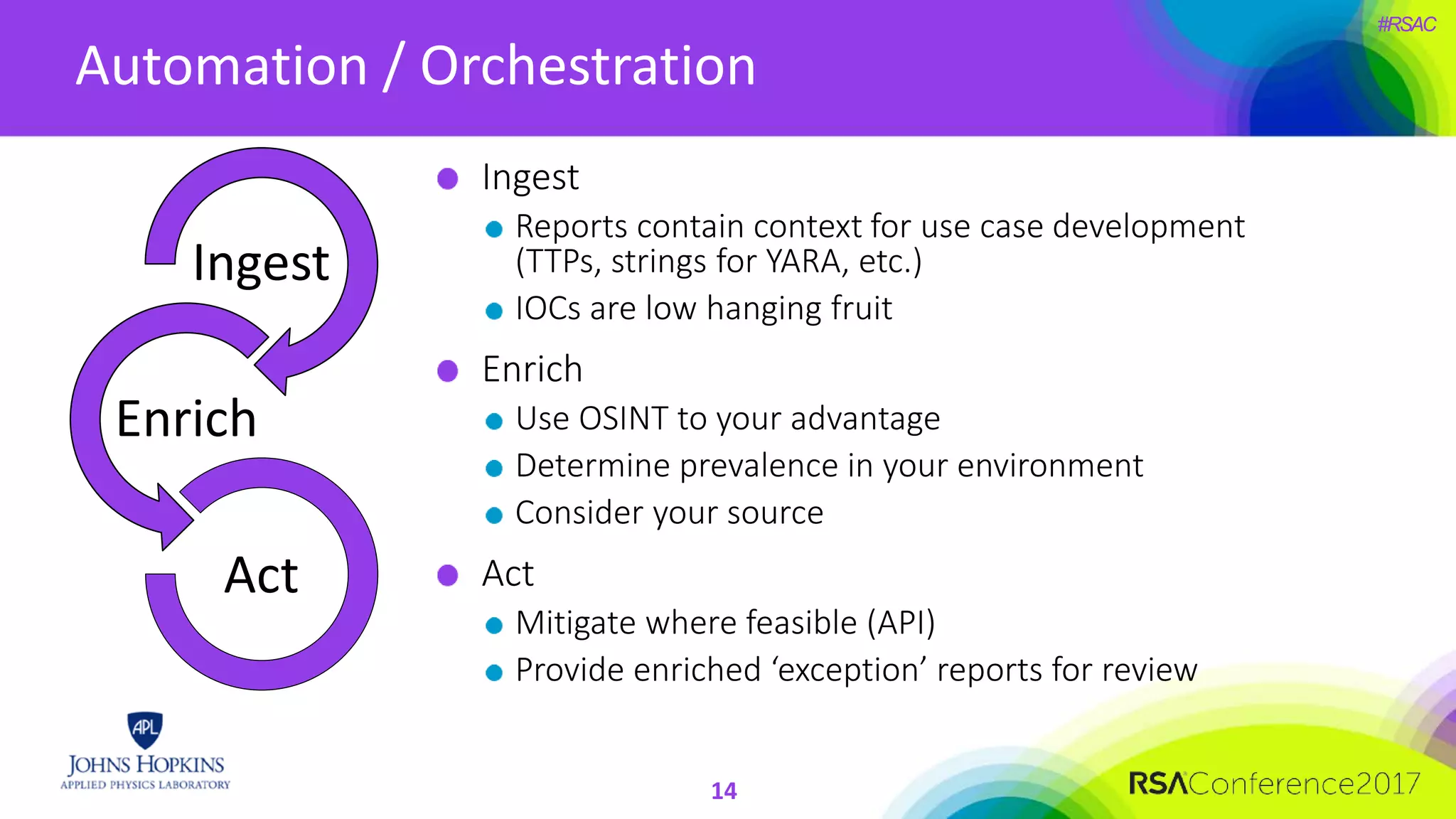
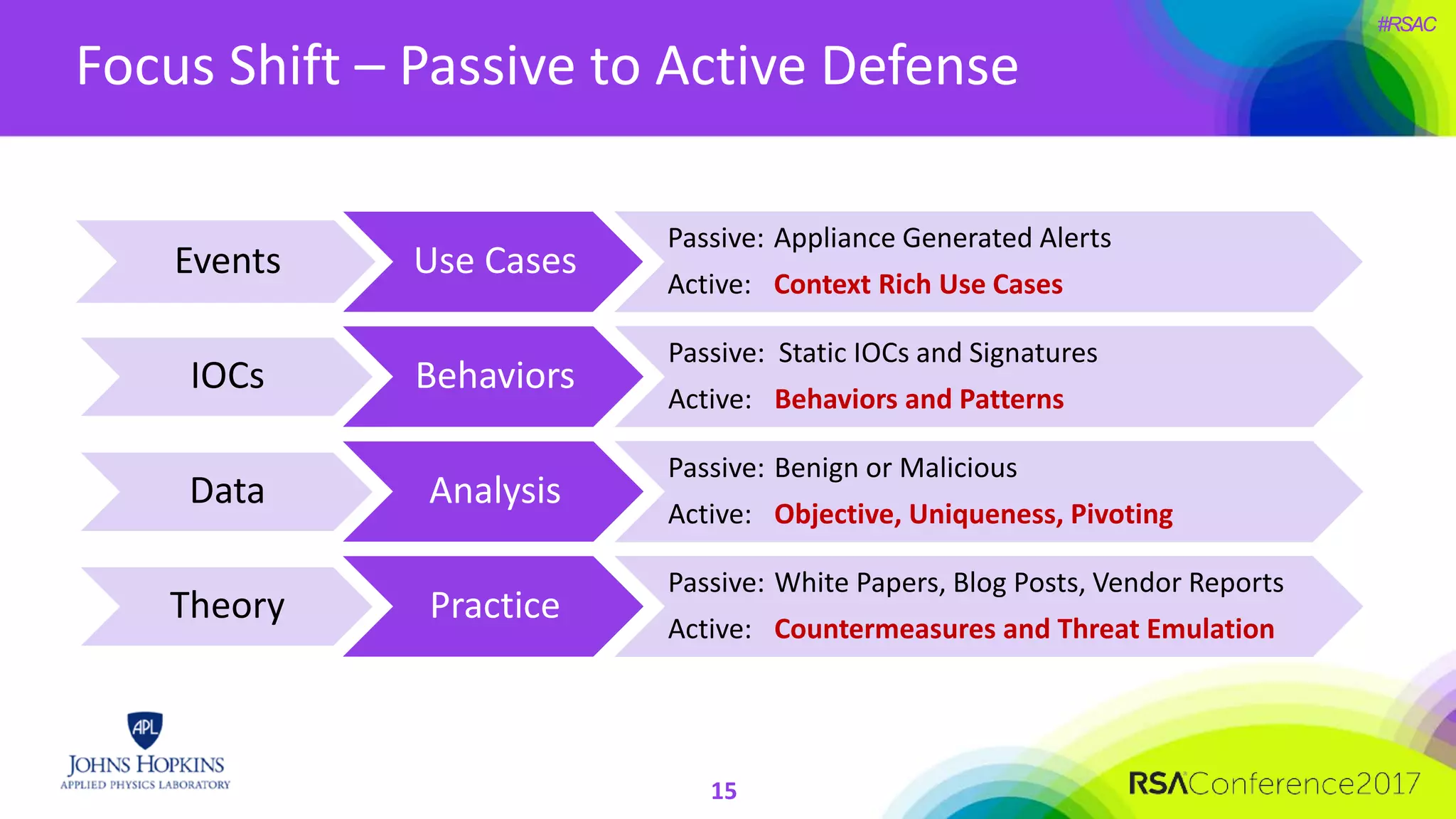
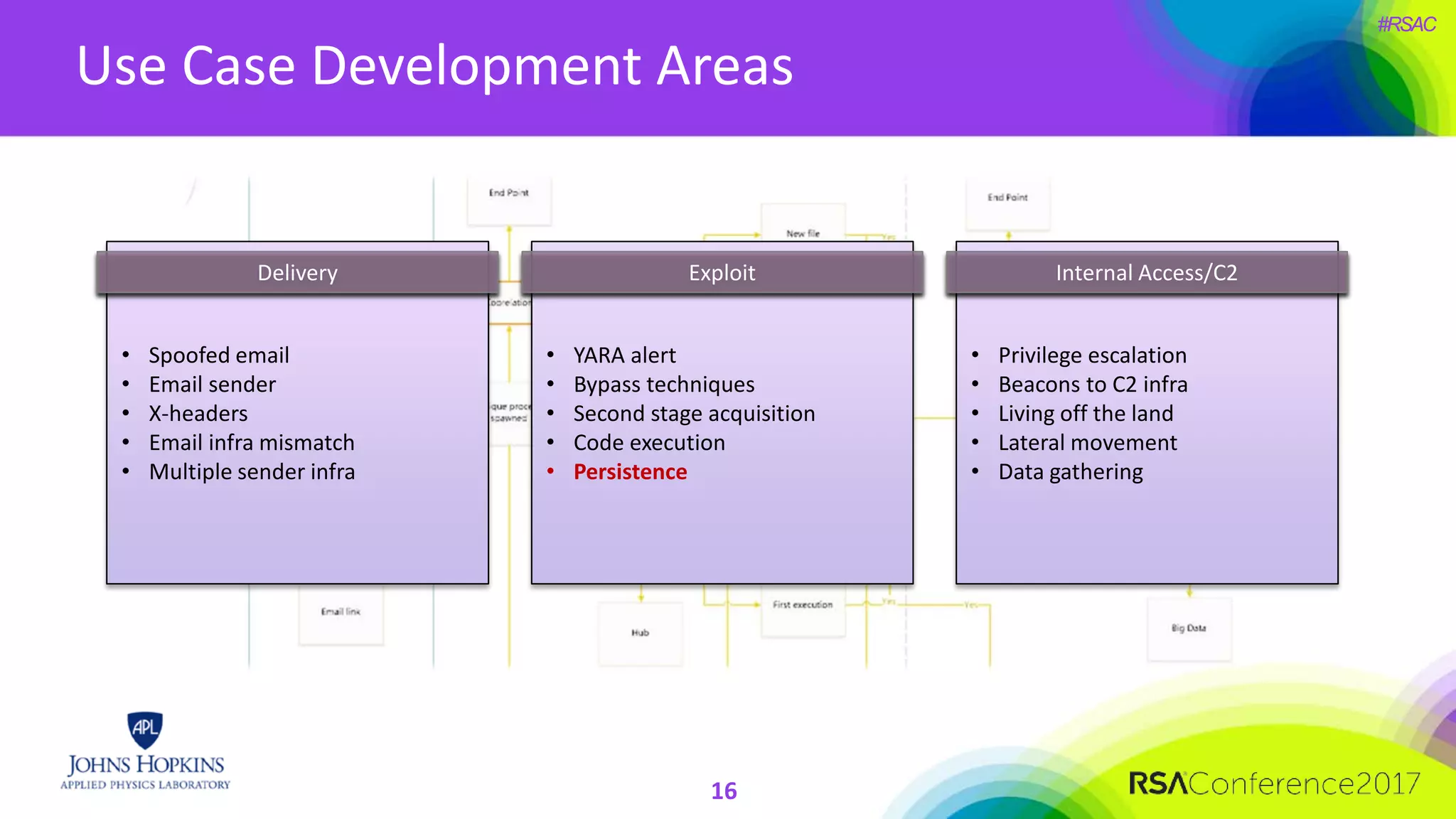
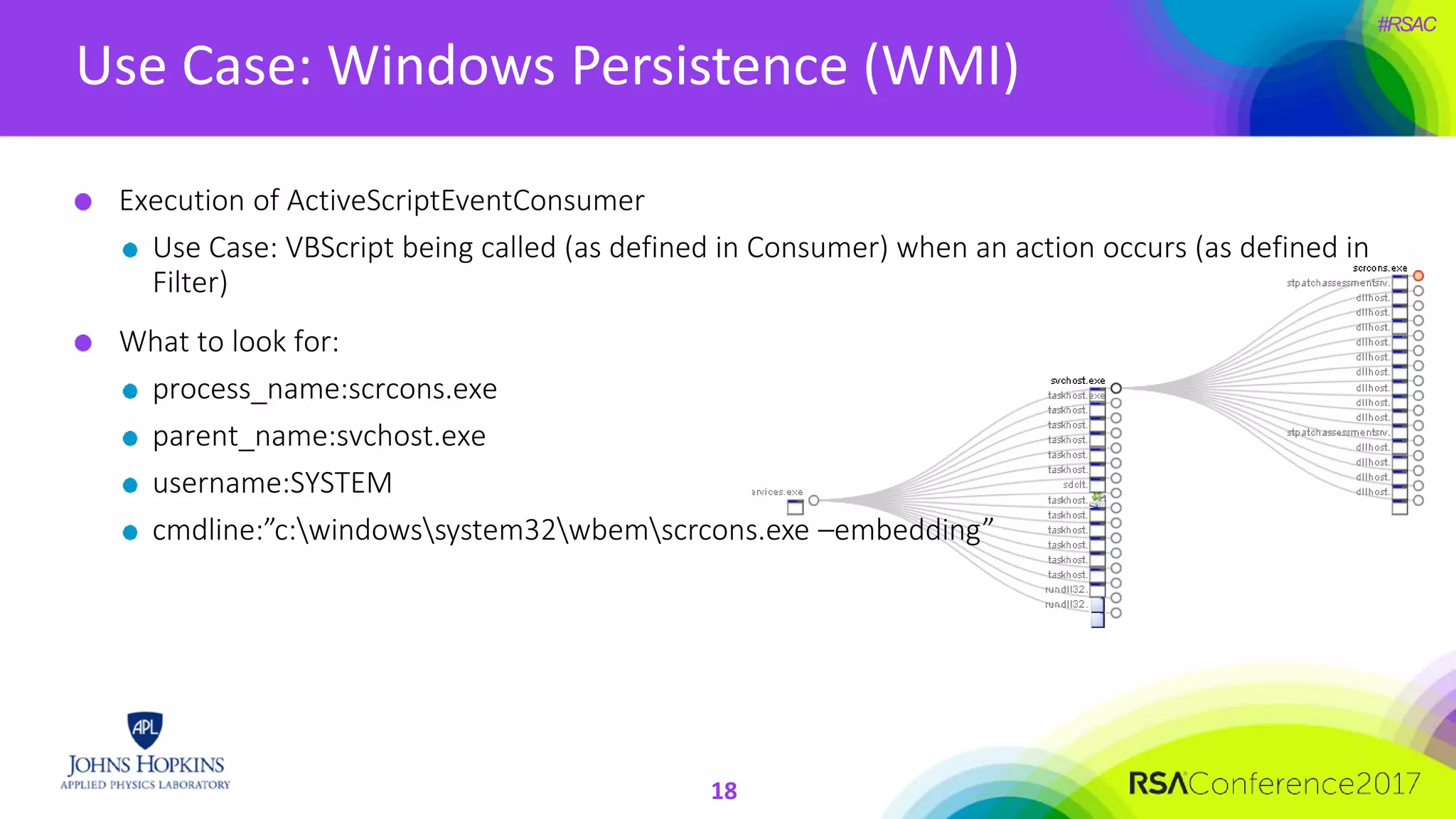
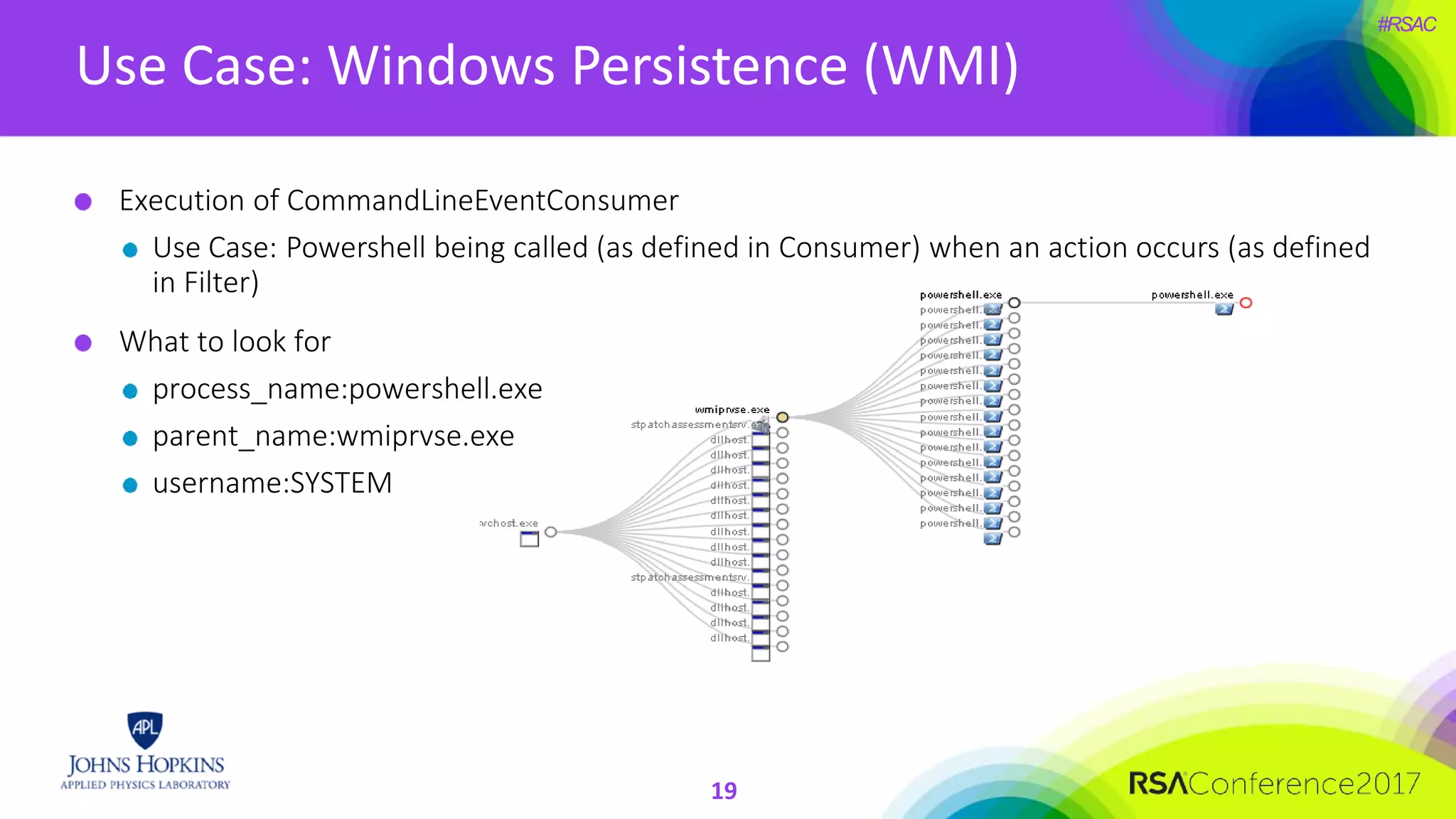
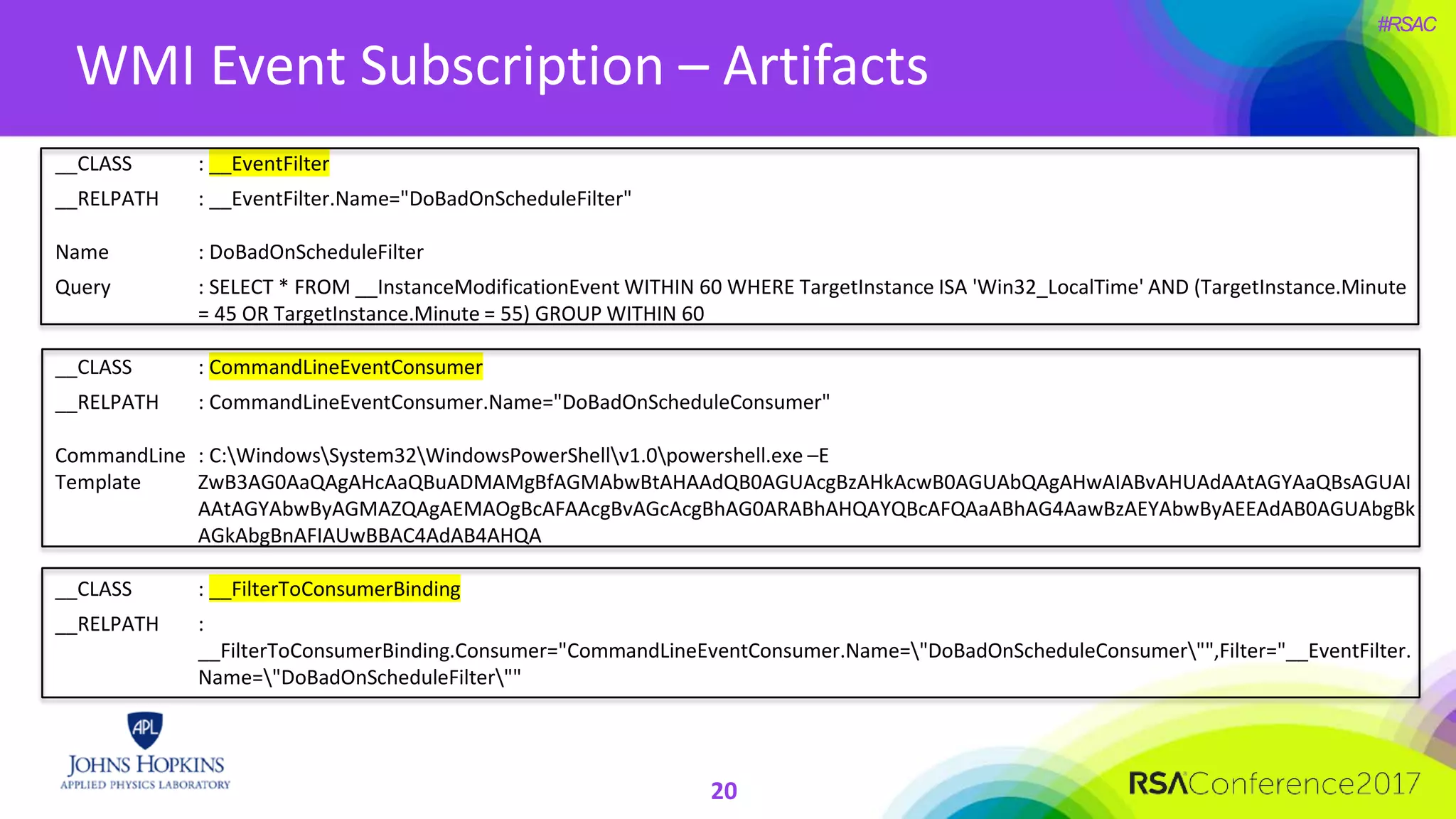
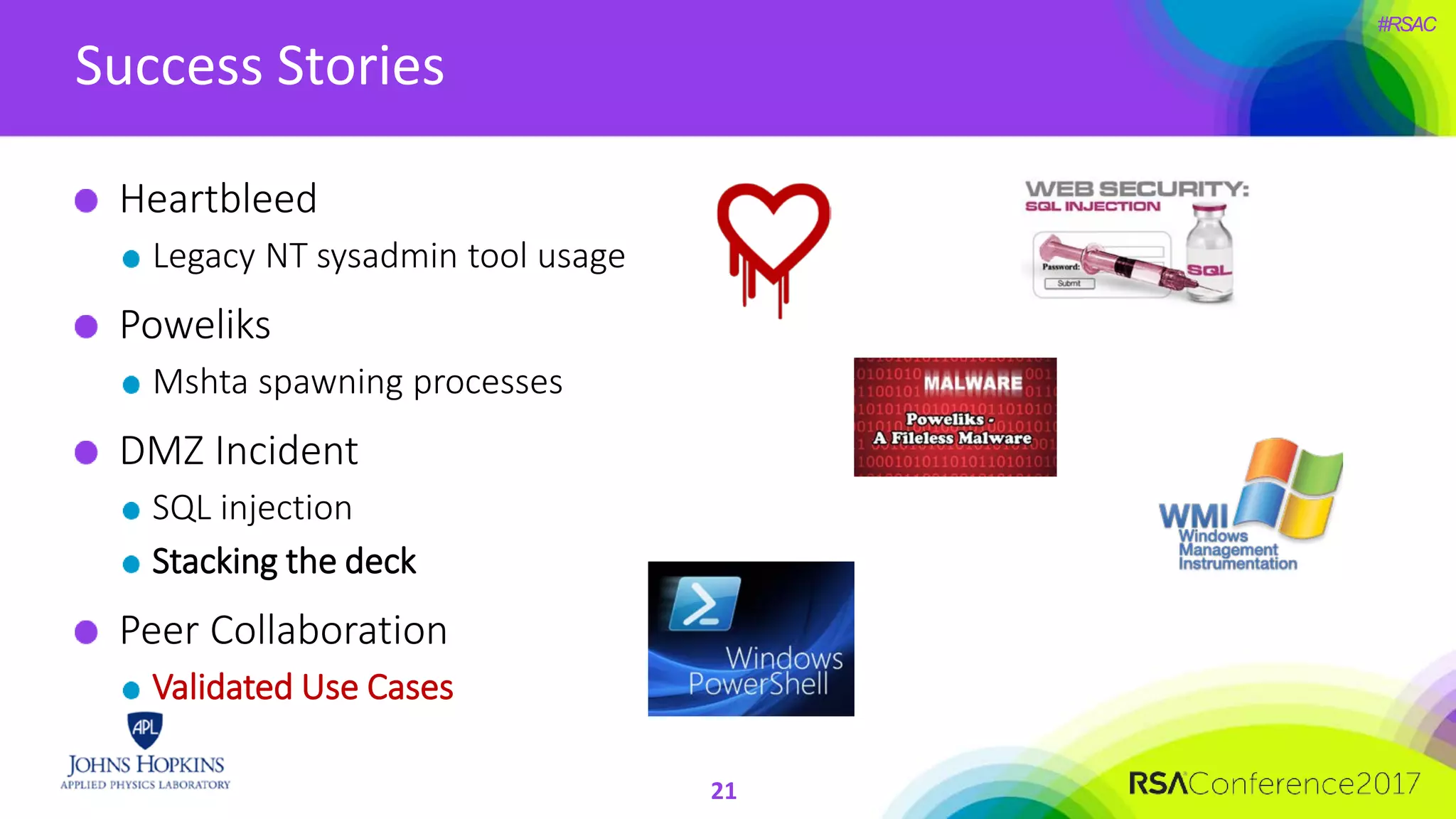
The document discusses the importance of evolving cyber defense strategies to combat increasingly sophisticated adversaries, outlining the necessity for continuous monitoring and a proactive approach to threat identification and management. It emphasizes the value of building a skilled cyber threat team capable of adaptive response and collaboration, as well as the role of behavioral analysis and use case development. Additionally, it highlights key challenges in management, philosophy, and technical areas that need to be addressed for effective cyber operations.