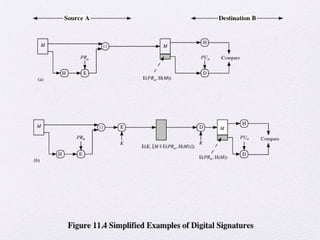
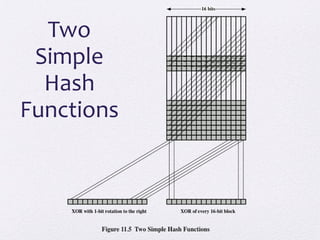
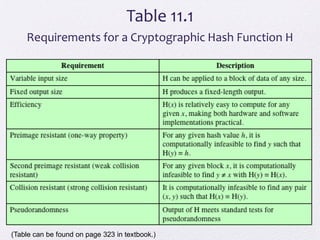
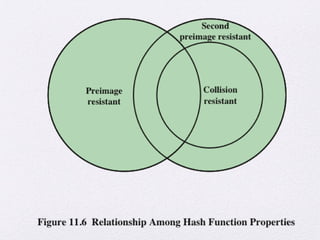
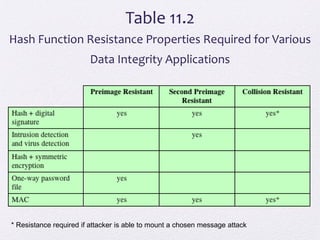
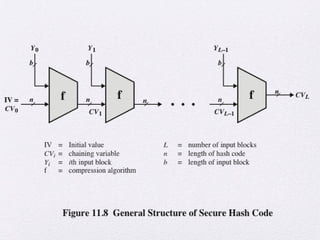
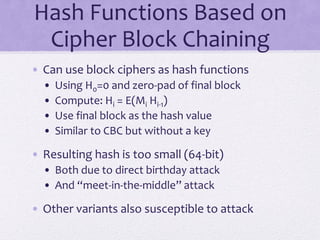
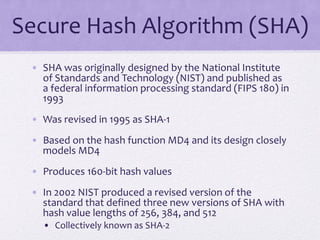
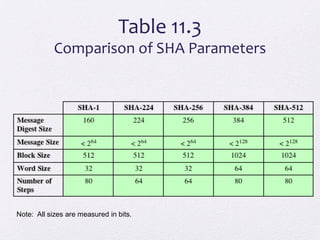
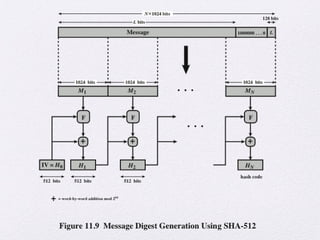
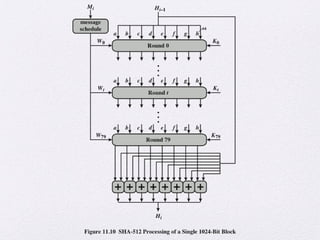
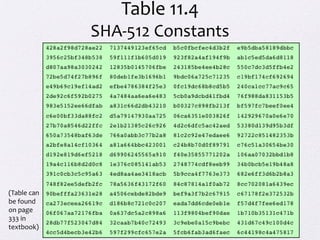
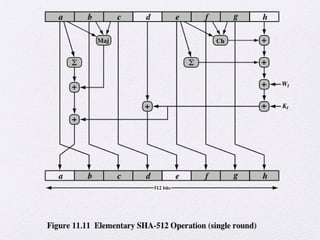
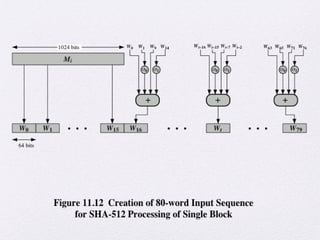
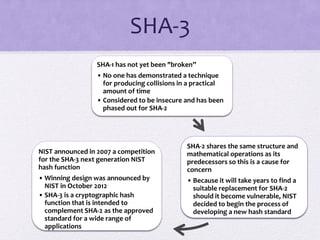
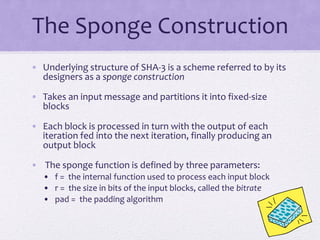
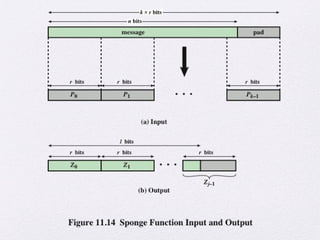
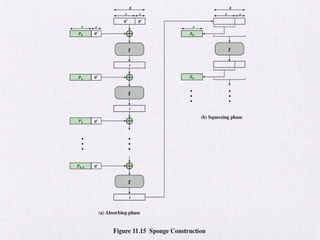
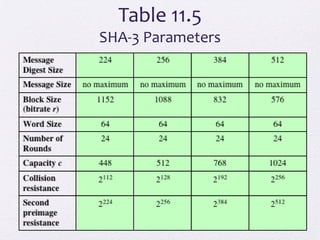
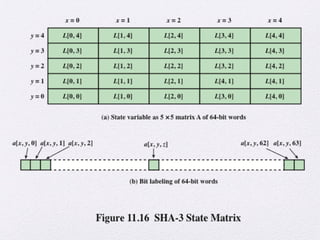
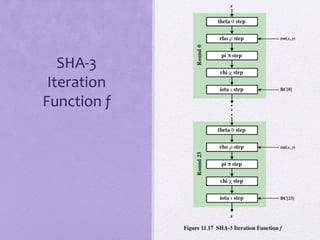
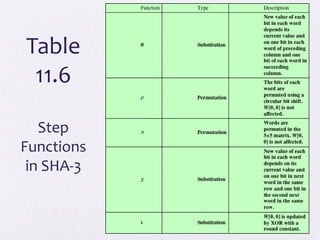
The document discusses public key encryption and hash functions, explaining that public key encryption involves a public and a private key for secure communication, while hash functions are used to ensure data integrity. Additionally, it covers various cryptographic techniques such as message authentication codes and digital signatures, highlighting their functions and applications. The text concludes with an overview of secure hash algorithms (SHA), including SHA-2 and SHA-3, detailing their structures and security considerations.