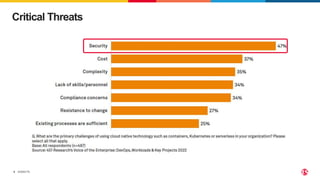
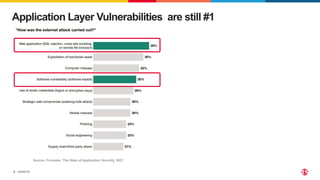
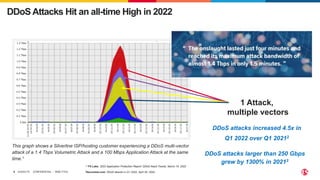
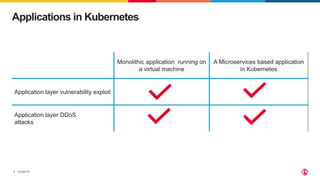
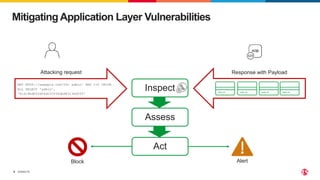
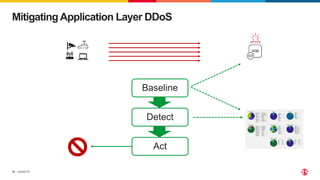
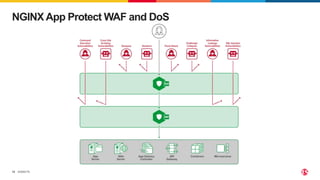
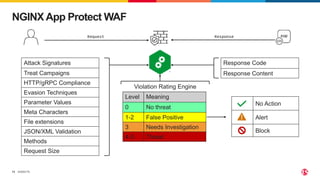
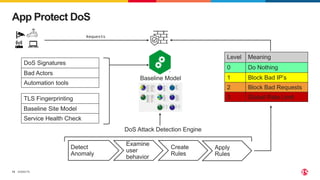
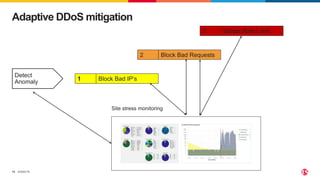
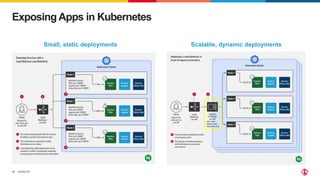
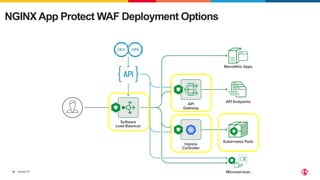
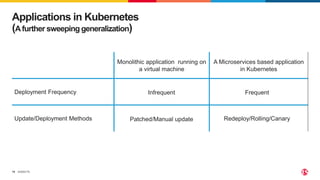
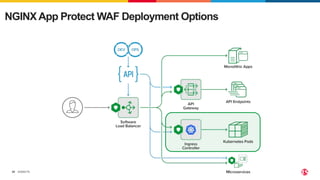
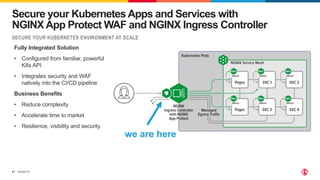
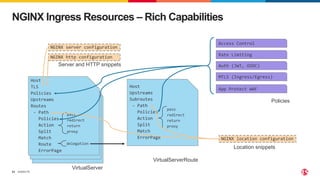
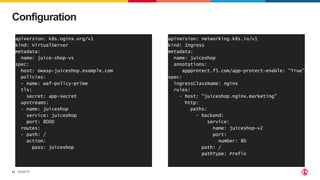
The document discusses protecting applications in Kubernetes from various hacks and DDoS attacks using NGINX solutions. It highlights critical threats such as application layer vulnerabilities and the significant rise in DDoS attacks experienced in 2022. Additionally, it details the integration of security measures into the CI/CD pipeline and offers deployment options for effective application protection.