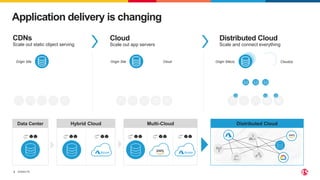
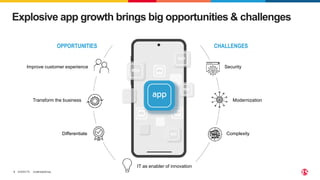
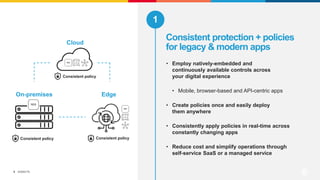
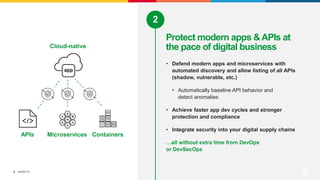
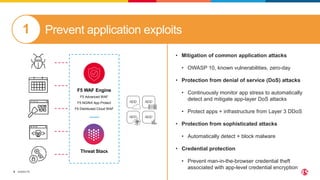
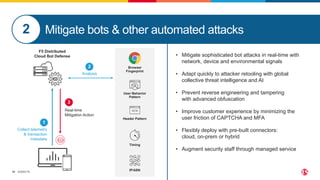
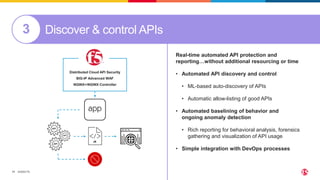
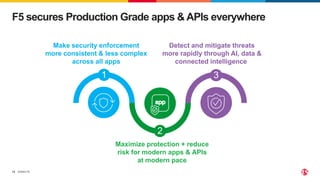
This document discusses F5's cloud security and application delivery solutions. It provides 5 key capabilities: 1) Preventing application exploits, 2) Mitigating bots and automated attacks, 3) Discovering and controlling APIs, 4) Protecting application infrastructure, and 5) Stopping fraud and account takeover. The solutions aim to make security more consistent across applications, maximize protection for modern apps and APIs, and help detect and mitigate threats more rapidly through artificial intelligence and connected intelligence.