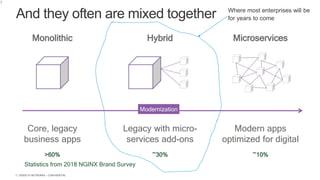
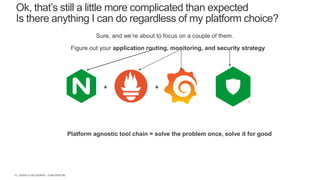
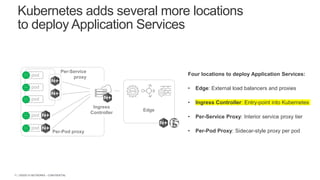
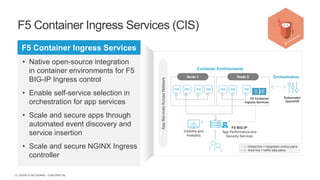
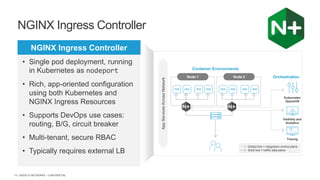
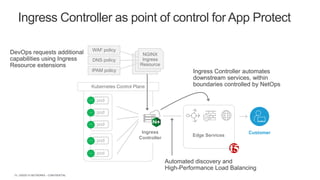
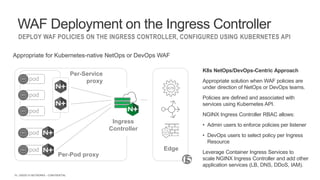
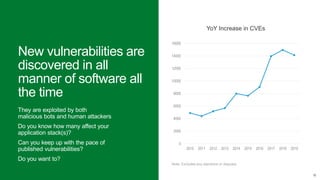
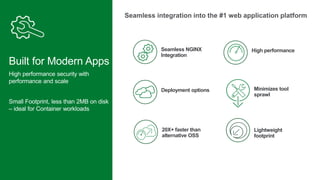
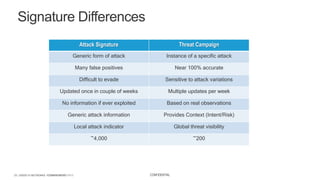
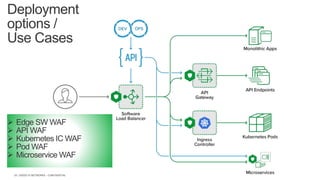
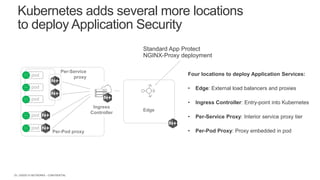
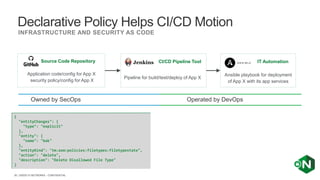
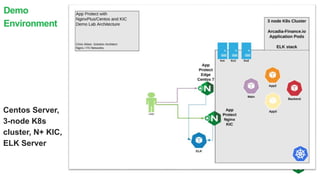
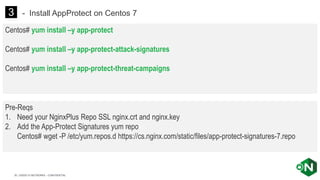
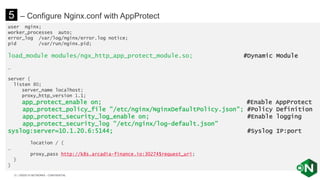
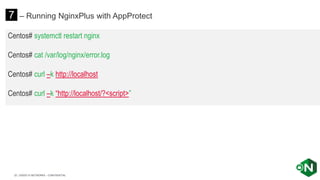
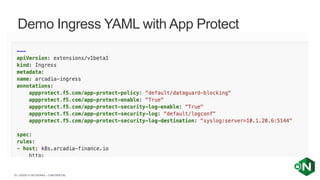
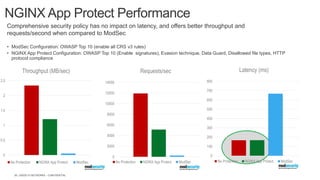
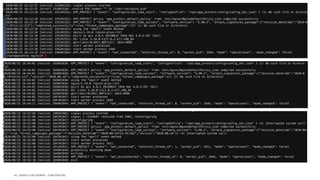
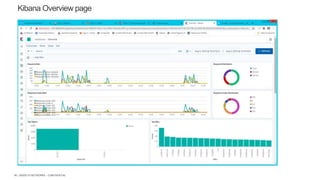
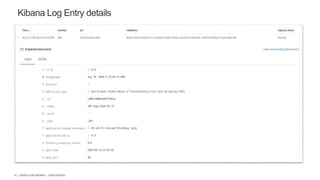
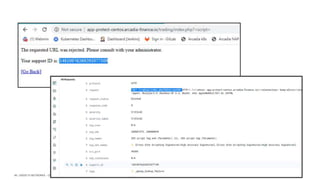
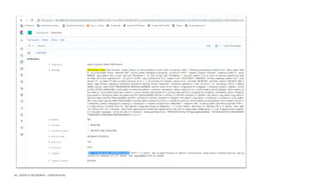
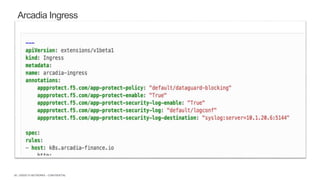
The document discusses securing applications and APIs in Kubernetes, focusing on deployment strategies, ingress control, and application security best practices. It highlights the importance of differentiating between greenfield and brownfield apps and outlines the criteria for deploying services efficiently. Additionally, it covers how to leverage F5's App Protect and NGINX technologies for robust application security within Kubernetes environments.