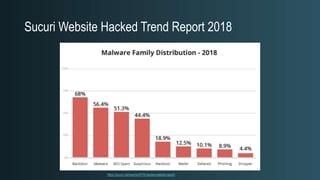
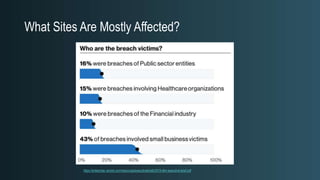
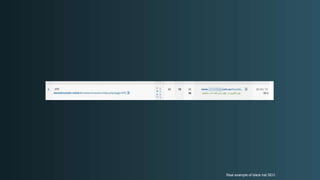
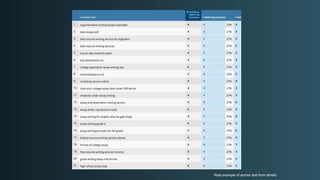
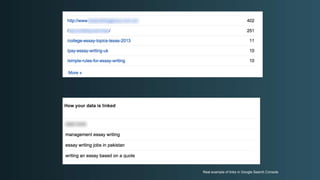
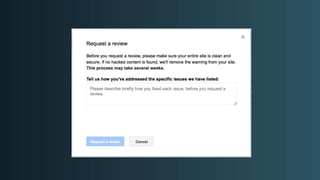
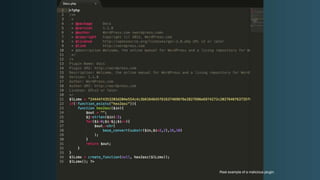
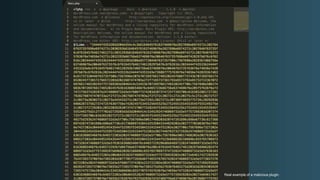
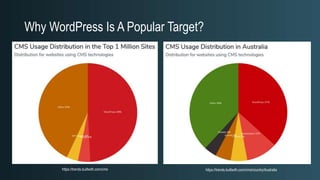
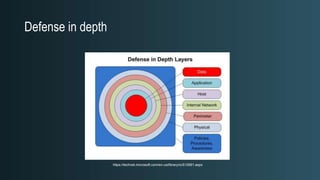
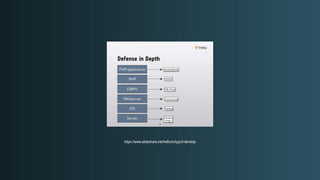
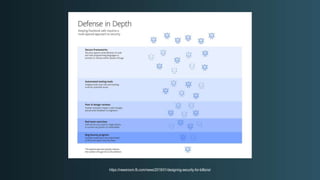
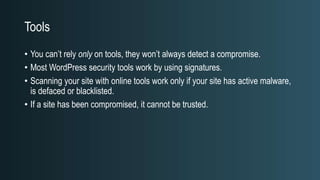
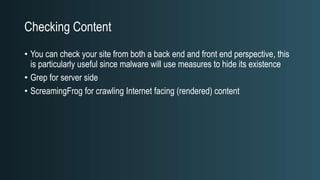
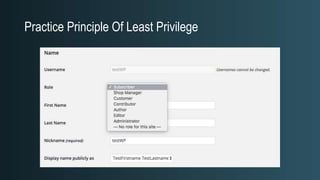
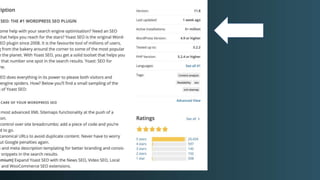
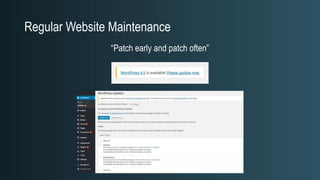
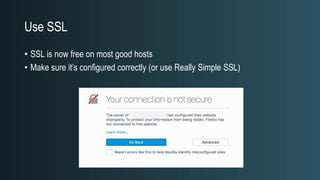
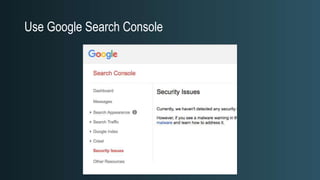
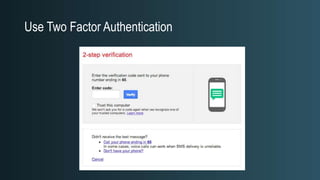
The document discusses WordPress security beyond just using security plugins. It emphasizes that WordPress security is often neglected but important, especially for business sites. While security plugins are helpful, a defense-in-depth approach with additional layers of security is recommended. The presentation provides practical advice on prevention, detection of compromises, and steps users can take including regular backups, choosing quality plugins, strong passwords, monitoring, and maintenance. WordPress is a common target because of its popularity and past vulnerabilities. The impacts of breaches on businesses can be significant.