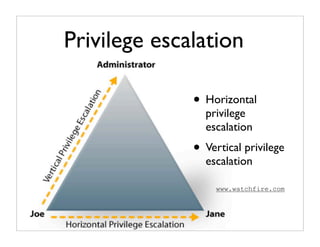
The document highlights common vulnerabilities and attacks in computer security, particularly through SQL injection and poor coding practices. It emphasizes the importance of building security into code from the start and advocates for good design principles to minimize vulnerabilities. The text also discusses various attack methods, defenses, and the significance of keeping security measures updated and maintaining logs for compliance.





![UN's website breached by hackers
The United Nations web site has been
defaced this morning.
The speeches of the Secretary-General Ban
Ki-Moon [2] have been replaced with the
following lines:
Hacked By kerem125 M0sted and Gsy
That is CyberProtest Hey Ýsrail and Usa
dont kill children and other people
Peace for ever
No war
screenshot
http://news.bbc.co.uk/2/hi/technology/6943385.stm](https://image.slidesharecdn.com/how-to-destroy-a-database-120521190454-phpapp02/85/How-to-Destroy-a-Database-8-320.jpg)
![http://hackademix.net/2007/08/12/united-nations-vs-sql-injections/
As you can easily verify by opening this URL, the site is
vulnerable to an attack called SQL Injection.
This is a very well known kind of vulnerability, fairly easy
to avoid and very surprising to find in such a high profile
web site. [3]
http://www.un.org/apps/news/infocus/sgspeeches/statments_full.asp?statID=105'
ADODB.Recordset.1 error '80004005'
SQLState: 37000
Native Error Code: 8180
SQLState: 37000
Native Error Code: 105
[MERANT][ODBC SQL Server Driver][SQL Server]Unclosed quotation
mark before the character string ''.
[MERANT][ODBC SQL Server Driver][SQL Server]Statement(s) could
not be prepared.
/apps/news/infocus/sgspeeches/statments_full.asp, line 26](https://image.slidesharecdn.com/how-to-destroy-a-database-120521190454-phpapp02/85/How-to-Destroy-a-Database-9-320.jpg)