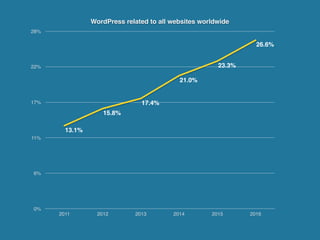
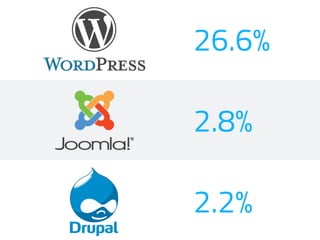
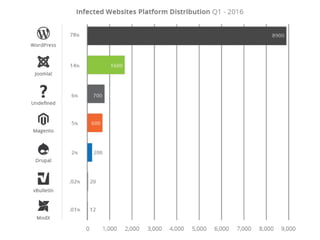
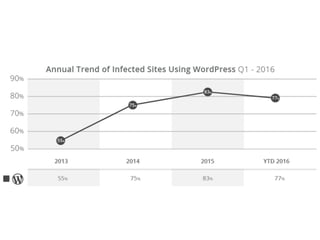
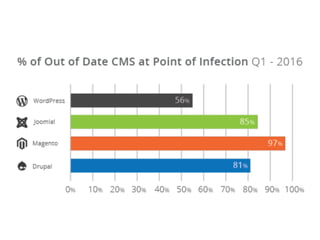
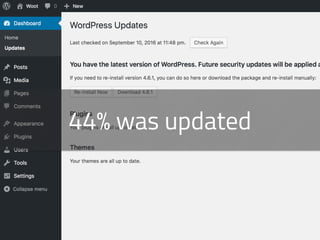
- WordPress is used on 26.6% of all websites worldwide as of 2016, showing steady growth each year.
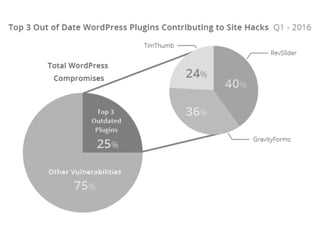
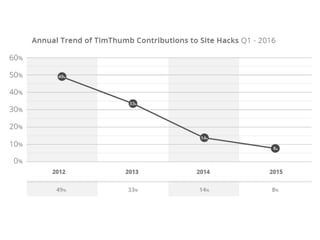
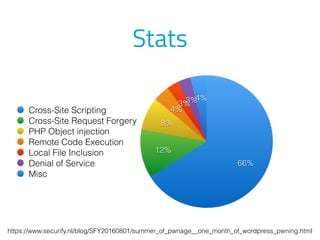
- A security audit of popular WordPress plugins found 118 instances of vulnerabilities across 58 plugins, demonstrating the ongoing need to improve WordPress security.
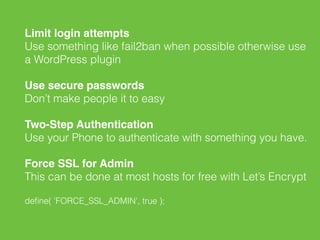
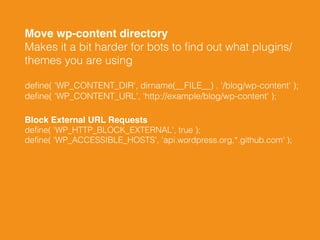
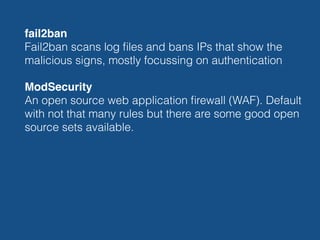
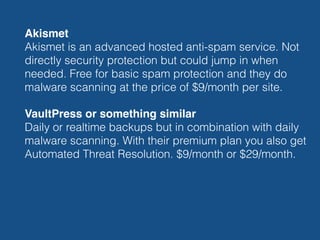
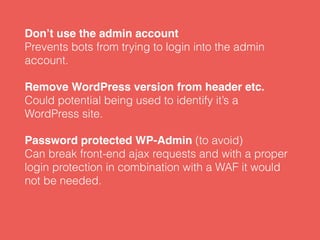
- There are several steps site owners can take to harden WordPress security, such as limiting login attempts, enforcing SSL, moving files like wp-config.php, and using server-level protections including fail2ban, Nginx configurations, and a web application firewall. External services like Cloudflare and Sucuri can also help monitor and protect sites.