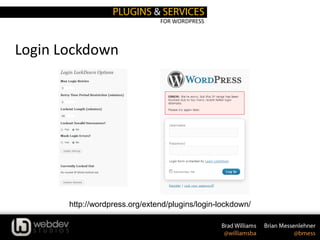
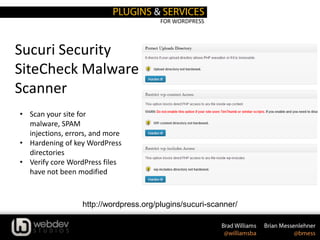
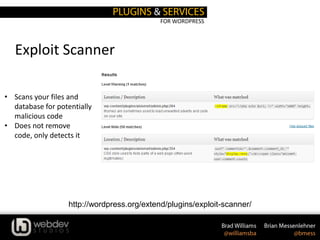
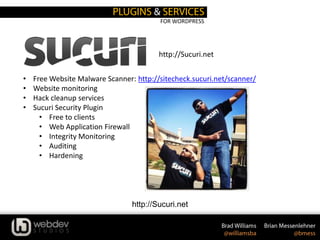
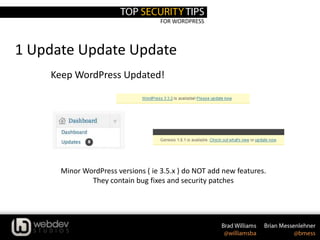
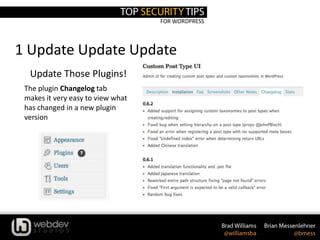
The document discusses WordPress security, providing statistics on website and malware growth, and emphasizes the importance of keeping WordPress and plugins updated, using secret keys, and choosing strong passwords. It outlines several security practices such as adjusting file permissions, moving the wp-config.php file, and using trusted sources for themes and plugins. Additionally, it includes recommendations for using specific plugins and services to enhance WordPress security.









![FOR WORDPRESS
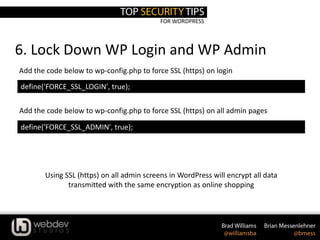
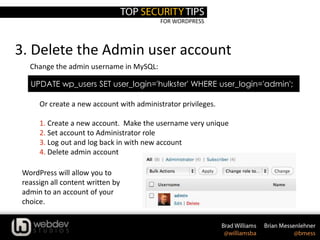
2. Use Secret Keys
define('AUTH_KEY', 'put your unique phrase here');
define('SECURE_AUTH_KEY', 'put your unique phrase here');
define('LOGGED_IN_KEY', 'put your unique phrase here');
define('NONCE_KEY', 'put your unique phrase here');
define('AUTH_SALT', 'put your unique phrase here');
define('SECURE_AUTH_SALT', 'put your unique phrase here');
define('LOGGED_IN_SALT', 'put your unique phrase here');
define('NONCE_SALT', 'put your unique phrase here');
1. Edit wp-config.php
A secret key is a hashing salt which makes your site harder to hack by adding random
elements to the password.
2. Visit this URL to get your secret keys: https://api.wordpress.org/secret-key/1.1/salt
BEFORE
define('AUTH_KEY', '*8`:Balq!`,-j.JTl~sP%&>@ON,t(}S6)IG|nG1JIfY(,y=][-3$!N6be]-af|BD');
define('SECURE_AUTH_KEY', 'q+i-|3S~d?];6$[$!ZOXbw6c]0 !k/,UxOod>fqV!sWCkvBihF2#hI=CDt_}WaH1');
define('LOGGED_IN_KEY', 'D/QoRf{=&OC=CrT/^Zq}M9MPT&49^O}G+m2L{ItpX_jh(-I&-?pkeC_SaF0nw;m+');
define('NONCE_KEY', 'oJo8C&sc+ C7Yc,W1v o5}.FR,Zk!J<]vaCa%2D9nj8otj5z8UnJ_q.Q!hgpQ*-H');
define('AUTH_SALT', 'r>O/;U|xg~I5v.u(Nq+JMfYHk.*[p8!baAsb1DKa8.0}q/@V5snU1hV2eR!|whmt');
define('SECURE_AUTH_SALT', '3s1|cIj d7y<?]Z1n# i1^FQ *L(Kax)Y%r(mp[DUX.1a3!jv(;P_H6Q7|y.!7|-');
define('LOGGED_IN_SALT', '`@>+QdZhD!|AKk09*mr~-F]/F39Sxjl31FX8uw+wxUYI;U{NWx|y|+bKJ*4`uF`*');
define('NONCE_SALT', 'O+#iqcPw#]O4TcC%Kz_DAf:mK!Zy@Zt*Kmm^C25U|T!|?ldOf/l1TZ6Tw$9y[M/6');
AFTER](https://image.slidesharecdn.com/wordpress-security-130927051446-phpapp01/85/Protect-Your-WordPress-From-The-Inside-Out-21-320.jpg)
![FOR WORDPRESS
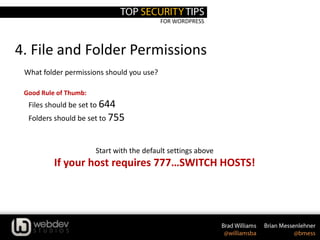
4. File and Folder Permissions
find [your path here] -type d -exec chmod 755 {} ;
find [your path here] -type f -exec chmod 644 {} ;
Or via SSH with the following commands](https://image.slidesharecdn.com/wordpress-security-130927051446-phpapp01/85/Protect-Your-WordPress-From-The-Inside-Out-28-320.jpg)